
AXIOM Cyber 6.5: Decrypting DDPE Files and Continued Improvements for Incident Response Investigations
AXIOM Cyber 6.5 introduces several new and exciting features including:
- Support for Dell Data Protection Encryption (DDPE)
- New remote volatile artifacts
- Added evidence sources and features for Email Explorer
- Additional artifact details in Timeline view
In addition to these feature developments, we’ve also added and updated a number of artifacts to ensure your evidence sources stay current with the latest apps and services.
You can upgrade to the latest version within AXIOM Cyber or over at the Customer Portal. If you haven’t tried AXIOM Cyber yet, request a free trial here.
Support for Dell Data Protection Encryption (DDPE)
This release introduces the first file-based encryption system for AXIOM Cyber, with support for Dell Data Protection Encryption (DDPE). You can now decrypt DDPE files right in AXIOM Cyber, streamlining the decryption process as well as maintaining the forensic integrity of the evidence and avoid delays and roadblocks in the preservation and review of encrypted evidence.
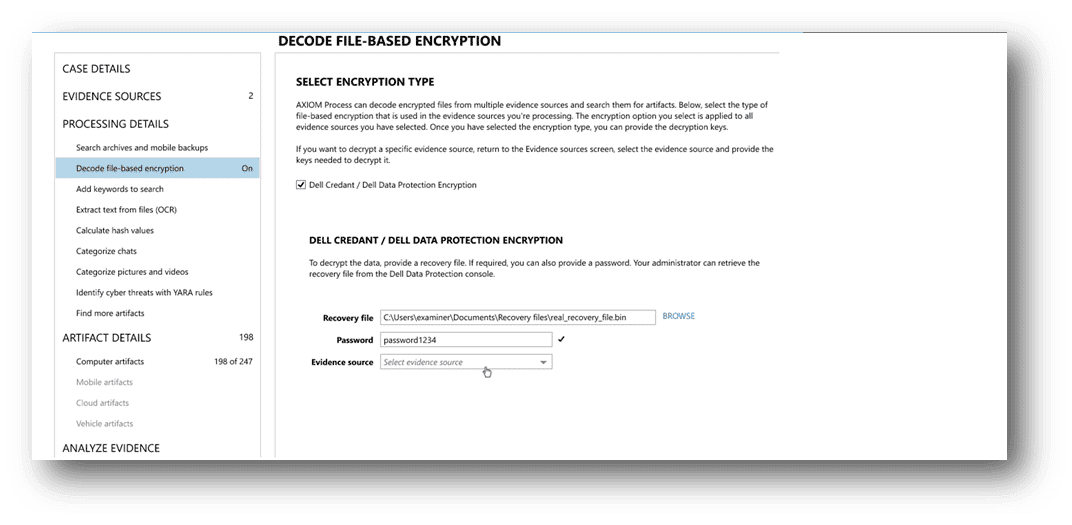
To see more about Dell Data Protection Encryption in AXIOM Cyber, check out our recent blog post.
New Remote Volatile Artifacts
Earlier this year we introduced a new artifact category, volatile artifacts, which allow you to remotely collect live system information. In this release, we have continued to expand on the range of the remote volatile system artifacts to include prefetch lists.
Prefetch lists store information regarding the activity of a program, including how often it has been run on a system and when, as well as the files and directories referenced, which can provide important insight into applications and tactics of a cyberattack.
Volatile artifacts are a great asset to incident response investigations as they can provide unique insights into malware behavior, anti-forensics software or other malicious activities that don’t leave easily detectable evidence trails.
Added Evidence Sources and Features for Email Explorer
Continuing to build on Email Explorer, this release adds support for cloud-acquired Apple Mail and MBOX artifacts, rounding out the cloud acquired email sources. To facilitate building user specific evidence from previous collections, this release also introduces a new feature which organizes acquired mailboxes and emails by the source.
Email Explorer presents messages similarly to how the sender and recipient would have originally viewed them, providing important context that may otherwise be missed. Much like a native email platform, Email Explorer provides several filters and search capabilities to narrow in on specific message times or themes to help manage the volume of data.
To see Email Explorer in action, check out our recently updated blog post.
Additional Artifact Details in Timeline View
We have also made some improvements to the artifact details in Timeline view to present more information—enabling a faster review of artifacts with less clicks. The artifact details shown on the Timeline view has been tripled to include key, supporting, and additional details, which will vary based on the type of artifact selected, providing key context on the evidence to help streamline your review.
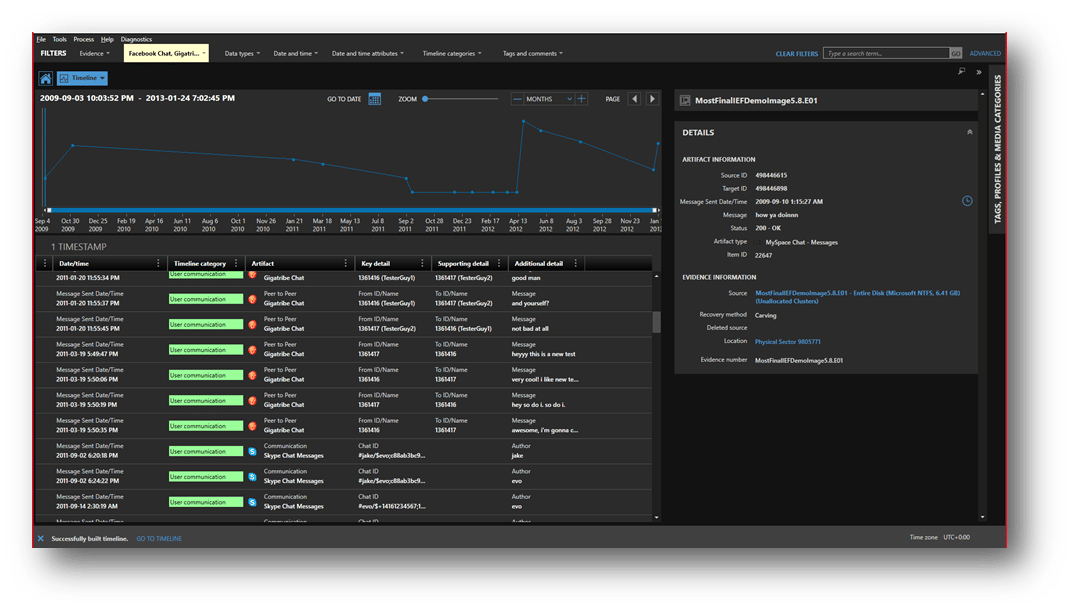
To learn more about this development, check out blog post about it.
New and Updated Artifacts
As with all releases of AXIOM Cyber, there is also support for several new and updated artifacts to help keep your investigations current with the latest corporate apps and services developments, including:
New Artifacts
- Google Keep
- Samsung Notes
- Prefetch List
Updated Artifacts
- AirDrop Transactions
- Apple Mail
- Bluetooth Devices
- Facebook Contacts
- Facebook Messengers
- Google Location History
- iOS Backups
- LINE Chat
- Signal Users
- Skype Activity
- Skype Messages
- Snapchat Messages
- Telegram Messages
- Twitter Users
- WeChat Friends
- WeChat Messages
- WhatsApp Messages