Simplify your investigations
Magnet Axiom Cyber is your comprehensive digital investigative solution for today's complex challenges. Remotely collect data from computers and the cloud reliably, and analyze it alongside mobile, IoT, and third-party data for a complete picture of your case.

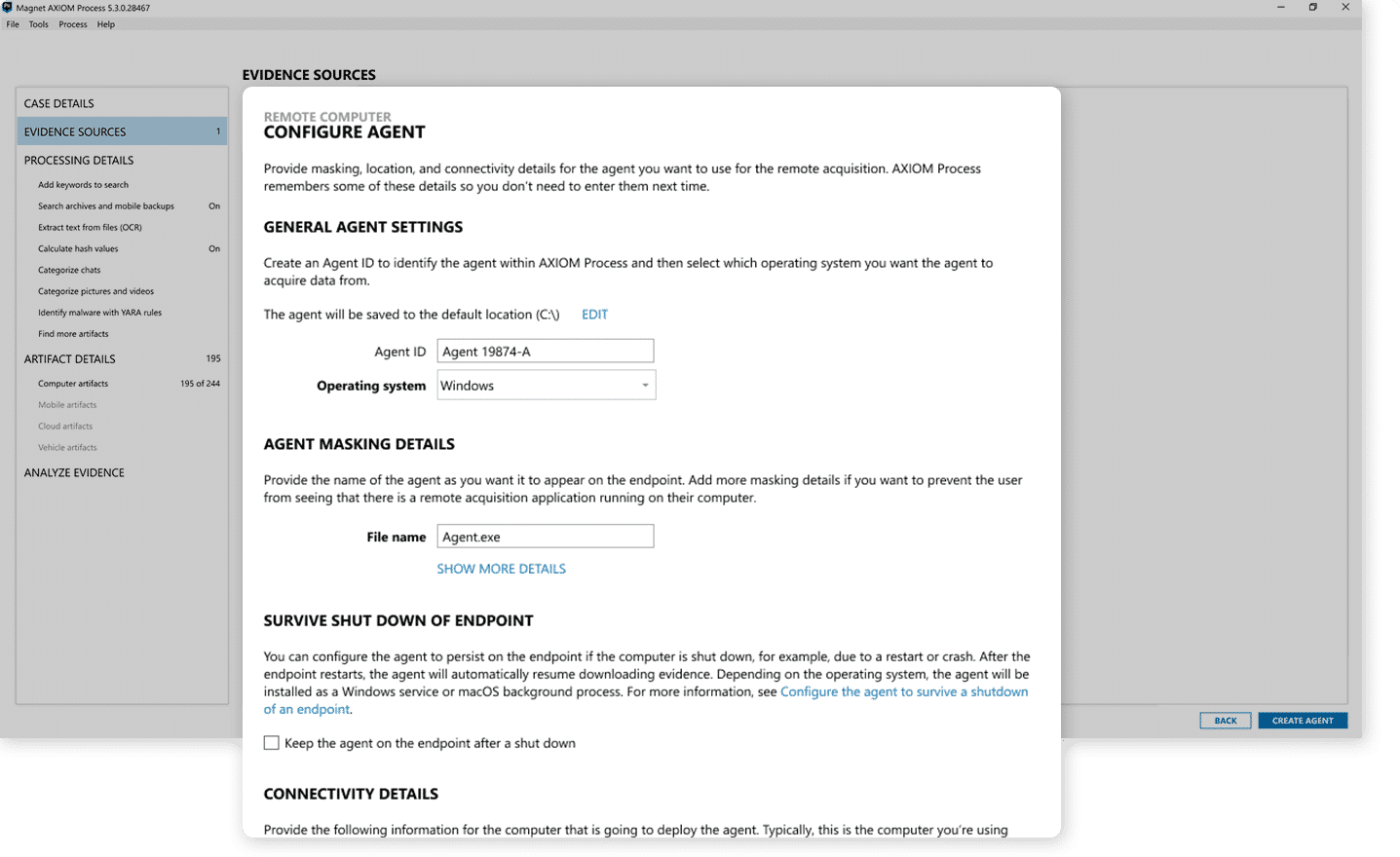
Advanced remote collections
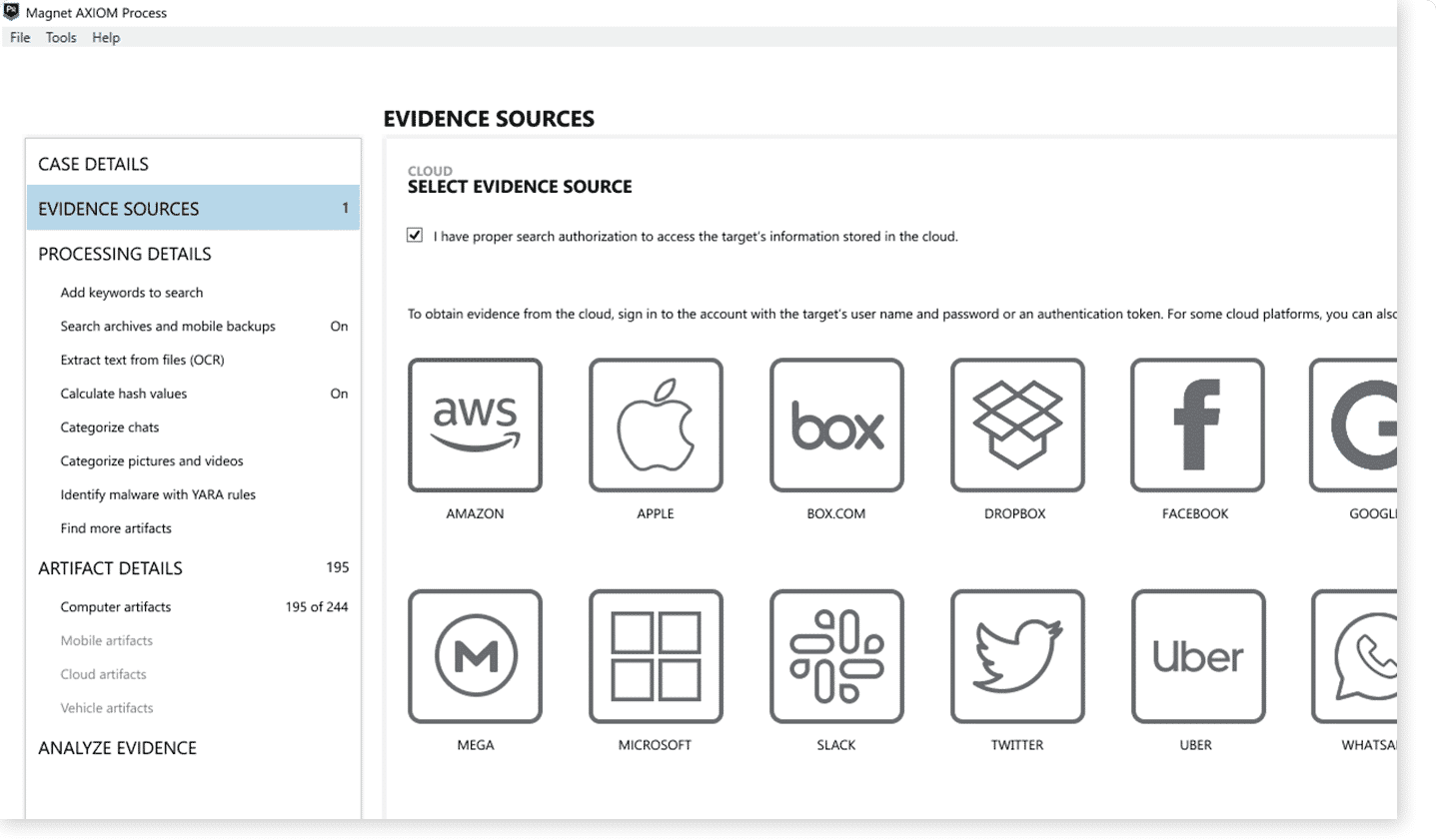
Conduct thorough and reliable investigations with targeted remote and off-network collections from Mac, Windows, and Linux endpoints. Acquire and analyze artifacts from single physical drives and volatile memory to see the full picture.
Key takeaways
- Use targeted locations to acquire only the data that is relevant.
- Collections automatically resume if a target goes offline and reconnects.
- Data is written to an AFF4-L forensically sound container.
Actionable case intelligence
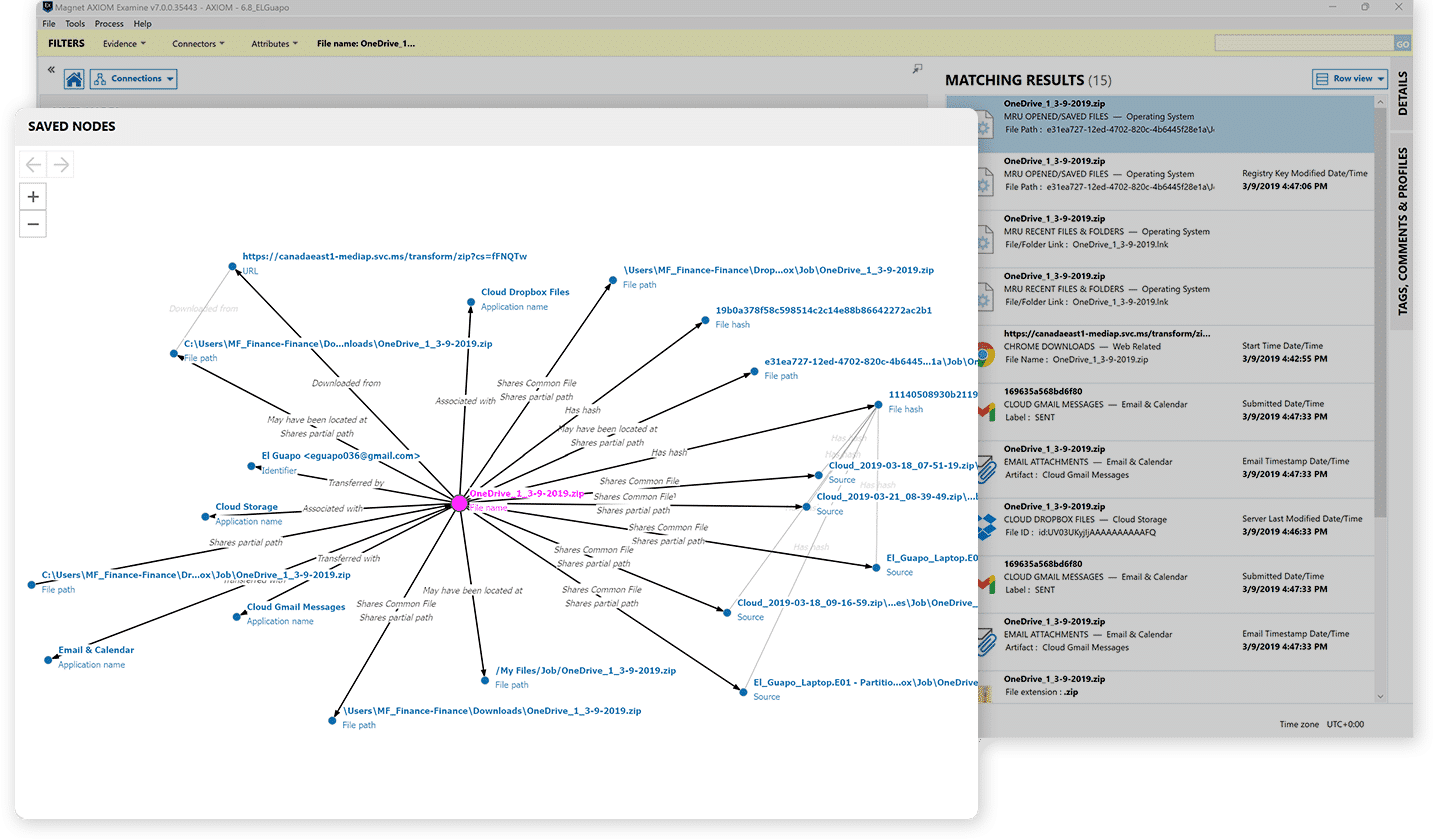
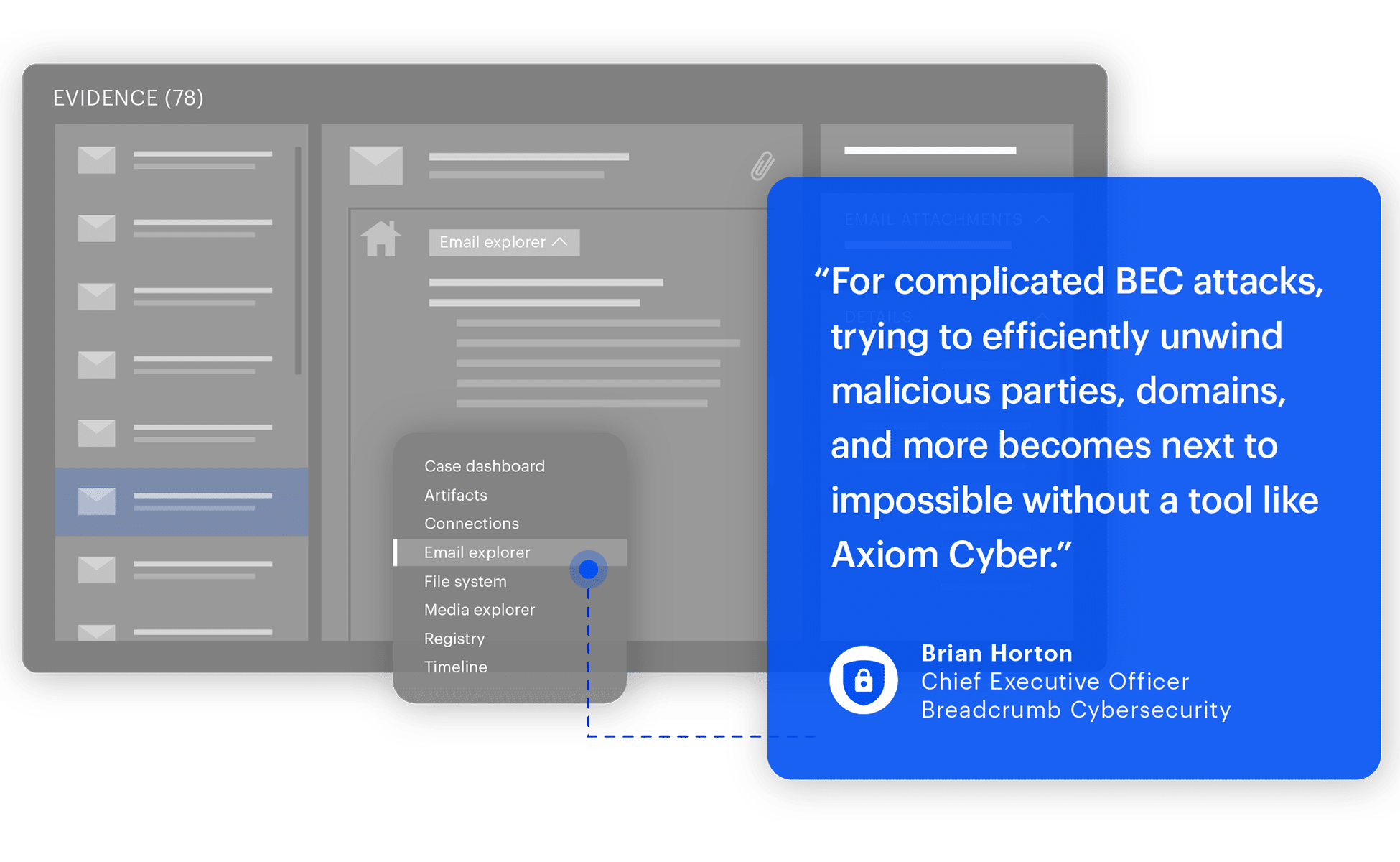
Axiom Cyber’s artifacts-first approach immediately presents the data needed to work through your case efficiently. Powerful analytics features like Timeline, Connections, identify TTPs with MITRE ATT&CK®️ framework, YARA rules, MFT parsing, Magnet Copilot, and Magnet.AI create actionable intelligence.
Data visualizations help you to quickly connect the dots between all the artifacts in your case.
Key takeaways
- Multiple views for data, like Email Explorer, provide the needed context to build a complete picture of an incident.
- Establish connections and relationships between evidence from different sources.
- Data visualizations help you to quickly connect the dots between all the artifacts in your case.
Deploy in the cloud
Get the flexibility your team needs by hosting Axiom Cyber on AWS or Azure. Hosting Axiom Cyber in the cloud reduces the cost and maintenance of your lab and provides the ability to perform collections from off-network endpoints.
Key takeaways
- Any workstation can access and connect to available cloud license.
- Minimize reliance on lab hardware and maintenance.
- Increased speed and availability for critical DFIR tools.
Time-saving features and workflows
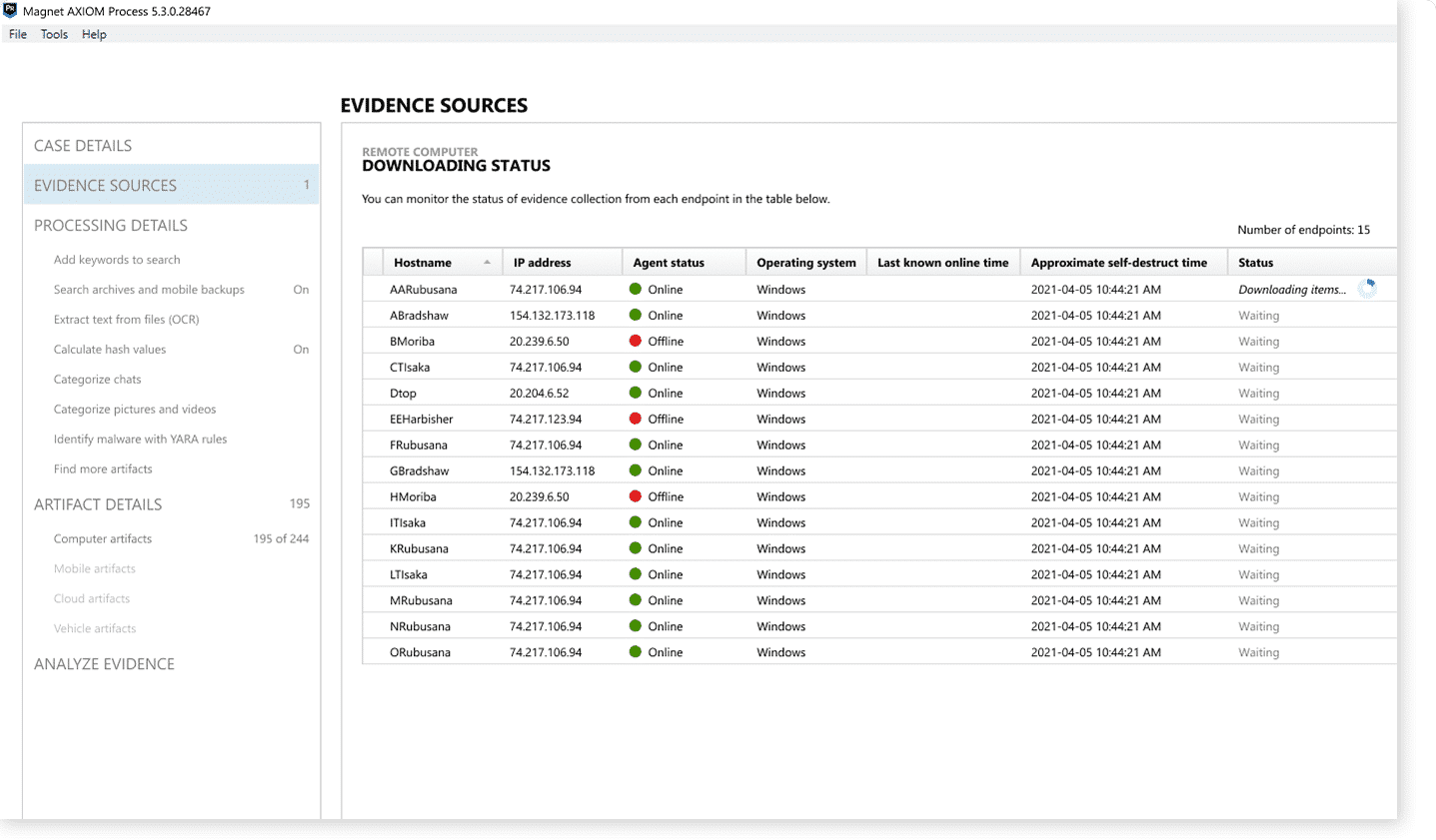
Speed up investigations with features, like queued collection and targeted location profiles, that minimize manual and repetitive tasks, allowing examiners to focus on data analysis, not configuring the tool.
Key takeaways
- Get results faster for more effective incident response, increased productivity, and happier stakeholders and clients.
- Designed to balance robust functionality with ease of use.
- Frequent functionality enhancements further refine and streamline workflows and processes.
Products for enterprise organizations

Perform and manage enterprise-wide, large-scale investigations of multiple remote endpoints with speed, scalability, and ease.
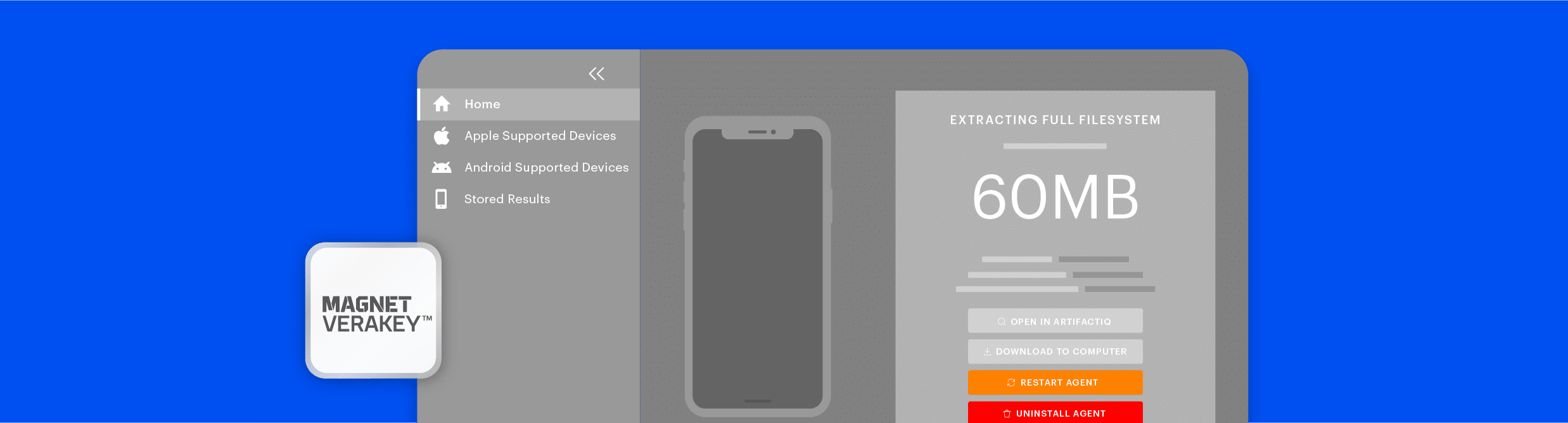
Collect the most comprehensive data extraction from iOS and leading Android devices while letting you get only the evidence you need.
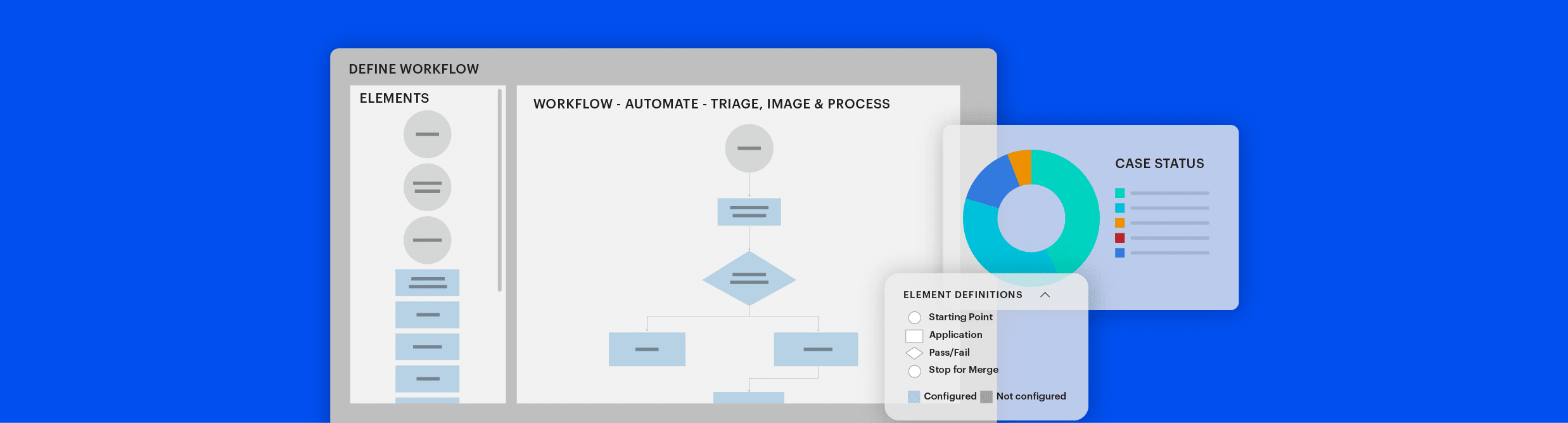
Scale up your DFIR investigations with the power of automation. Integrate your tech stack with the processing power of the Axiom Cyber Engine to create streamlined workflows.
Request your free trial today
Magnet Axiom Cyber is a digital forensics solution that will help you find the truth.
Get right to the evidence you need with a solution that keeps you a step ahead.

