
Automating Root Cause Analysis With EDR Integration in Magnet AUTOMATE
Root cause analysis is essential. Especially for critical and high-impact security incidents. By resolving only the symptoms of a security incident, instead of the actual core issue, organizations can open themselves up to similar attacks in the future.
Performing root cause analysis helps ensure you’ve eliminated attackers from lurking in your network minimizing damages and costs. In fact, breaches identified and contained in under 200 days had an average cost savings of 26.5%, or 1.12 million dollars, according to the 2022 IBM Cost of a Data Breach report. This doesn’t include the average dwell time of 79 days, as reported by Crowdstrike, meaning attackers already spend around two to three months in a network before discovery. EDR solutions will alert security analysts to a potential incident but often the work of completing root cause analysis can be unnecessarily tedious–that’s why automating workflows and connecting the SOC to the digital forensic team can save time by increasing efficiency and productivity.
What is Root Cause Analysis?
Root cause analysis is a method of problem-solving used to investigate a problem to identify where it originated.
While SOC tools, such as endpoint detection and response (EDR) and security information and event management (SIEM), provide a good start to an investigation, they’re often not able to provide the depth and breadth of artifacts required to identify the root cause. While EDR tools excel at providing real-time, continuous monitoring of endpoints, this becomes a limitation when performing root cause analysis as there are far more pieces to the puzzle than endpoint telemetry.
Artifacts processed from memory using Magnet AXIOM Cyber—such as active network info, hidden processes (psxview) hidden terminated processes, malware finder (_malfind) to name a few—can help identify the root cause in incidents such as malware and ransomware investigations.
For a full-scale investigation, a collaborative team of experts including the digital forensic analyst and incident responder s will present the results of their analysis in a detailed “lessons learned” report. This usually includes, among other things, the events that occurred before, during and after the incident, as well as the impact (financial, regulatory compliance, privacy) and corrective actions to remediate the vulnerability. It is highly unlikely that an incident will be caused by a single gap in security.
Automation for Consistent, Repeatable and Efficient Workflows
A forensically sound investigation relies on a consistent, repeatable, and reproducible process. Introducing automation helps you achieve this goal while also creating efficiencies.
With Magnet AUTOMATE, a digital forensic platform that automates your forensic tools and tasks, you can create streamlined customized workflows that ensure consistency while removing manual tasks so your forensic analysts can focus on deep dive analysis, review, and reporting.
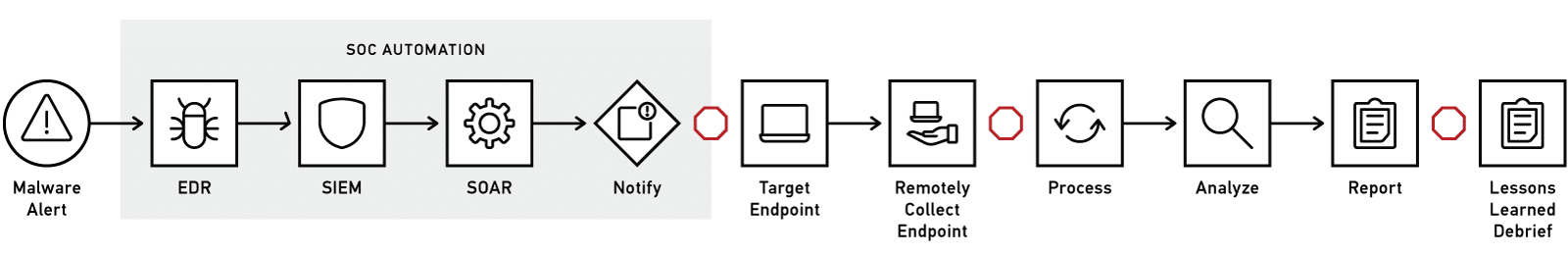
Current Manual Digital Forensic Workflow
In this example, the EDR solution (such as CrowdStrike Falcon or Cortex XDR) has detected potential malware on an endpoint. An event is created in the SIEM tool, which has triggered a specific malware playbook in the SOAR. A basic triage was conducted and determined that forensics is required.
If this occurs outside of working hours, then the collection may be delayed to when the forensic analyst starts their day. For every manual task, such as setting up and executing a remote collection, and subsequently the processing of that data, there is the potential for hours or days of delay, resulting in more time attackers have to spend in your network causing damage.
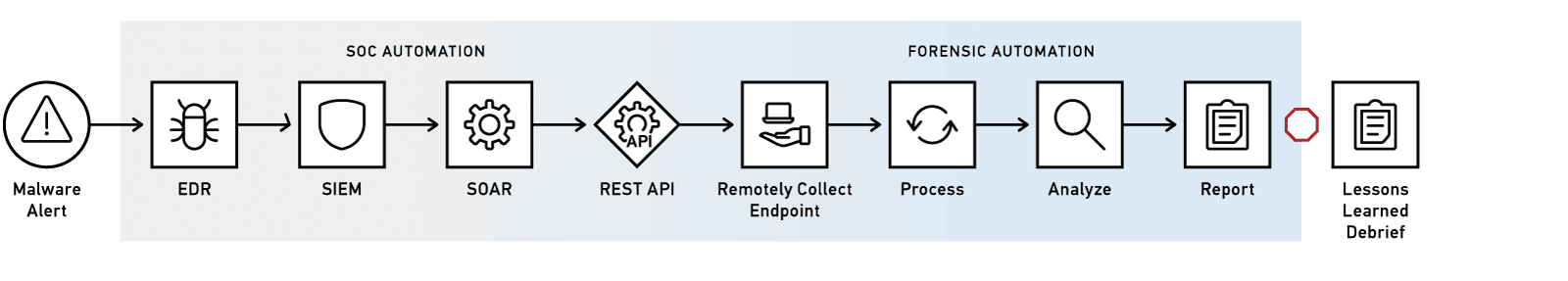
New Workflow With AUTOMATE
Now, with AUTOMATE, the workflow is fully automated from the SOC to the digital forensics team. Within minutes, AUTOMATE can immediately execute on a collection from the endpoint and the delay from collection to processing is entirely removed as the data automatically moves from one step in the workflow to the next.
In this example, a remote targeted collection over the network returned Windows event logs, and browser history to explore where the malware may have been downloaded from, as well as memory artifacts to see what was executed (such as MUI Cache, ShimCache, and $MFT).
As with most workflows, there is still a human element required. Not everything should or can be automated!
In this case, the forensic analyst receives an email notification from AUTOMATE letting them know that they have a case ready for their review. They can then conduct their analysis and ultimately prepare their findings for a Lessons Learned report which is provided to cross-functional stakeholders for remediation.
The new automated workflow may follow this sequence:
- The EDR tool detects potential malware, and the event is ingested into the SIEM which triggers a specific malware playbook in the SOAR
- The SOAR, via the REST API, invokes AUTOMATE and provides the collection details
- AUTOMATE initiates automatic collection from the target remote endpoint
- Upon completion of data collection, AUTOMATE orchestrates the processing of evidence after which an alert is sent to the forensic analyst to notify them that the incident is ready for review
Learn More About Automating Your DFIR Workflows
Check out other common digital forensic workflows that can benefit from automation in our “Automating DFIR Workflows” blog series:
- Automating Insider Threat Investigations with SIEM Integration in Magnet AUTOMATE
- Automating Legal Hold Requests With Remote Collections in Magnet AUTOMATE
Also, download the “Modernizing Digital Forensics Workflows with Magnet AUTOMATE” guide to explore how automation transforms other common DFIR workflows, such as DLP, inter-department handoffs, and malware investigations.