
Automating Insider Threat Investigations with SIEM Integration in Magnet AUTOMATE
Insider threats, whether due to malicious action, inadvertent breaches, or negligence, put your company at risk of potentially significant financial and reputational consequences. Costs can add up in both direct and indirect ways. They can include the theft of intellectual property, legal and regulatory costs, and brand deterioration, to name a few. According to the 2020 IBM Cost of Insider Threats: Global Report, the total average cost of insider-related incidents for an organization reached $11.45M over a 12-month period.
Identifying Insider Threats
Each company has in place their own policies and procedures for investigating insider threats. Alerts can be triggered via monitoring solutions configured to detect suspicious behavior. For example, a SIEM can be set up to detect and alert when an employee downloads several high-value CAD files onto a USB drive in the middle of the night. Or the HR department may request an investigation based on information passed to them about a frustrated employee threatening to take confidential assets with them when they leave.
Investigation Delays Can Be Costly
Regardless of the scenario or motive, investigating with speed and discretion is crucial to contain the threat and minimize damage and costs. Delays occur when cross-functional teams need to manually handoff information and requests to one other. SOC Analysts rely on solutions such as SIEM (Security Information & Event Management) to detect and alert when a threat occurs, as well as for remediation. However, these solutions are not designed to covertly and remotely collect evidence from endpoints or process it for forensic investigation. That’s why incorporating an automation solution like Magnet AUTOMATE into your lab ensures your team’s resources can respond just as quickly as those used in the SOC.
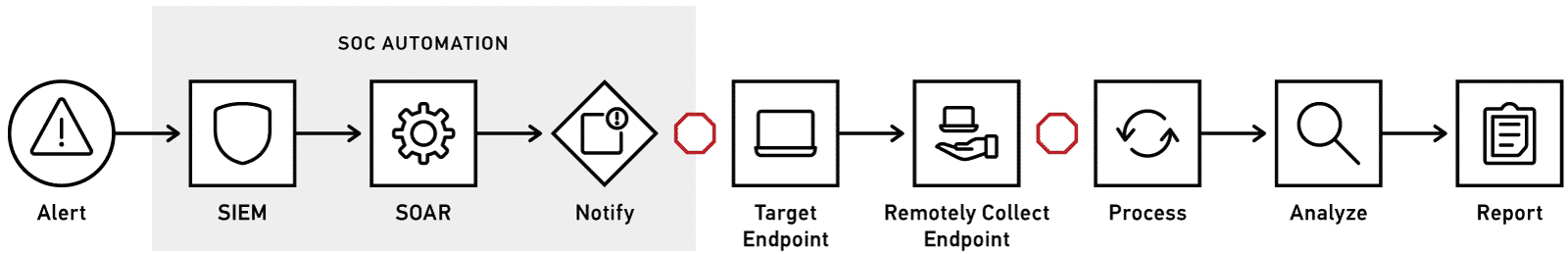
Current Manual Digital Forensic Workflow
In this example, the SIEM (for example, Splunk Enterprise, LogRhythm) detects suspicious employee behavior creating an alert and kicking off one of the organizations appropriate insider threat playbooks. This playbook requires a deep dive by the digital forensics team which introduces a potential delay. The case needs to be manually handed off to the forensics team who then need to perform the remote collection. Then, once the collection is complete, there is usually another manual intervention required to process and create reports such as a timeline report or internet history report.
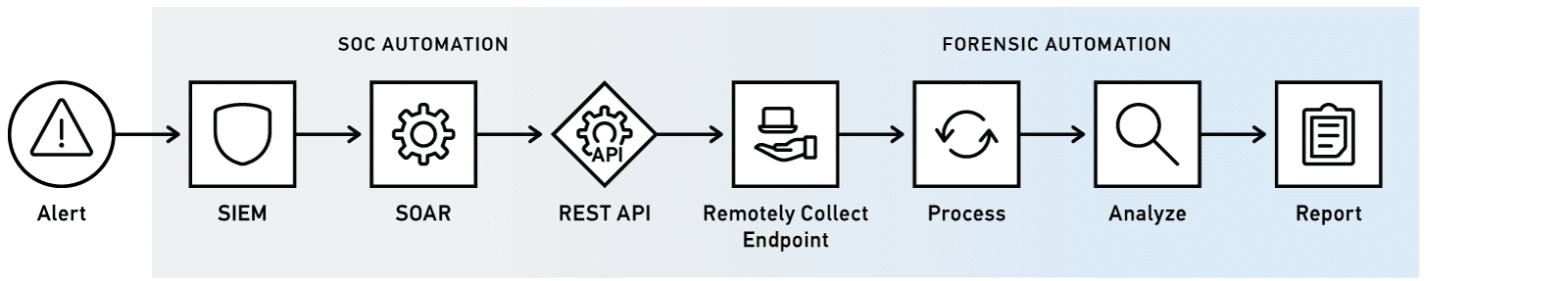
New Workflow with Magnet AUTOMATE
Now, with AUTOMATE, the entire workflow can be automated from the time the SIEM detects malicious activity through to completing all the steps within the forensic workflow.
With AUTOMATE coordinating the forensic response, instead of delays and manual task execution, there’s an automated sequence of events:
• The SOAR, via the REST API, invokes AUTOMATE and provides the collection details
• AUTOMATE initiates automatic collection from the target remote endpoint
• Upon completion of data collection, AUTOMATE orchestrates processing of evidence
Learn More About Automating Your DFIR Workflows
Check out other common digital forensic workflows that can benefit from automation in our “Automating DFIR Workflows” blog series:
- Automating Legal Hold Requests With Remote Collections in Magnet AUTOMATE
- Automating Root Cause Analysis With EDR Integration in Magnet AUTOMATE
Download the “Modernizing Digital Forensics Workflows with Magnet AUTOMATE” guide to explore how automation transforms other common DFIR workflows, such as DLP, inter-department handoffs, and malware investigations.