
Anatomy of an eDiscovery Investigation
If you’re not familiar with eDiscovery, here’s a brief overview: “eDiscovery refers to discovery in legal proceedings such as litigation, government investigations, or Freedom of Information Act requests, where the information sought is in electronic format (often referred to as electronically stored information or ESI).”
Oftentimes this work is carried out by law firms or consultancy organizations—including the collection of digital evidence from various data sources such as email or social media. However, more businesses are finding that they can perform eDiscovery more cost effectively by using the resources they have in-house.
According to research that we gathered and presented in our 2021 State of DFIR report: more than 1 in 5 DFIR professionals report always having to work on cases that support eDiscovery.
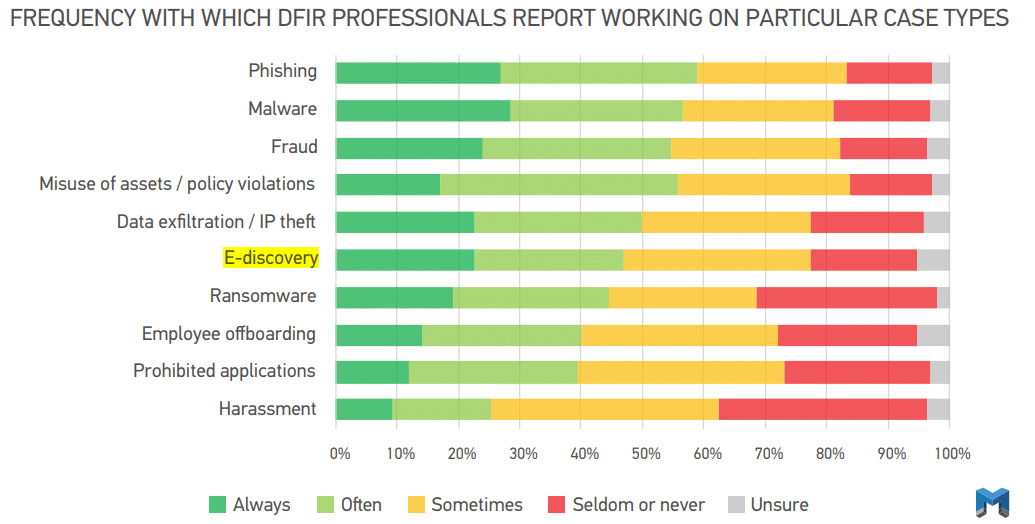
However, you never know when a case that you’re working may end up taking a turn you didn’t expect. You may find yourself in a situation where you are unexpectedly gathering and analyzing digital evidence that will make its way to an eDiscovery team or analyst.
We’ll use a fictional, yet real-world inspired example, based on a case that one of our Forensic Consultants worked a few years ago, to illustrate what you could experience throughout the course of your eDiscovery investigation. This includes the unexpected twists and turns that may arise and how you can take measures to quickly adapt.

Phase One
Receive Request from SOC to Validate Alert from a Remote Endpoint
You can expect your work to begin from any number of different stakeholder groups. However, some of the more common ones for eDiscovery tend to be HR or Corporate Investigations, Forensic Accounting and Finance, or even the Security Operations Center or SOC for short.
Our real-world example begins with an alert from the SOC. The alert is triggered by an employee downloading Dropbox, which is not an approved IT tool for employees at the company in our example. Your first task will be to validate the alert and determine the scope of your investigation. From there, you’ll decide on the most effective data collection method.
Consider two different options offered by Magnet Forensics products:
Triage with Magnet IGNITE
Magnet IGNITE is a web-based, early case assessment triage tool that can be used to quickly scan remote endpoints. It can perform an initial analysis of artifacts and files and apply keyword searches and time filters.
In our example, you could simply keyword search “Dropbox” while searching in the Installed Applications artifact and you’d have hits returned if there was activity.
The benefit of IGNITE is that you can get quick results and have the information you need so you can know whether or not to move forward with a targeted or full collection and then deeper forensic analysis.
Targeted Remote Collection Using Magnet AXIOM Cyber
AXIOM Cyber performs remote collections of on- and off-network endpoints and to speed things up can do targeted collections as well. AXIOM Cyber provides a list of preconfigured targeted locations, but also allows you to define your own custom targeted locations too. Read more about targeted location options in AXIOM Cyber in this blog post.

Phase Two
Determine the Scope and Start Data Collection of Digital Evidence
The data sources that you end up collecting from are largely dependent on the type of digital evidence that you’re after.
Social media activity, for example, is primarily going to be coming from cloud-based sources in addition to computer artifacts. General activity such as downloading and installing applications will come from computer artifacts.
In our example, the examiner checked the following artifacts in AXIOM Cyber:
- Browser History for searches of Dropbox
- Internet Activity for web visits to sites related to Dropbox
- Installed Programs to see if Dropbox was installed
- Recycle Bin to see if the installer for Dropbox was removed
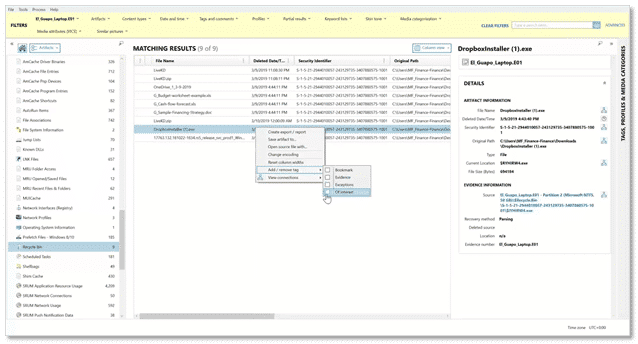
All four searches yielded results and the screenshot above shows the results from the Recycle Bin. The other thing you’ll notice is that items of interest are being tagged as the examiner is working through the case.
TIP: A great habit to get into is tagging evidence items of interest as you work through your case. Every case you work will involve some level of reporting, everything from a simple pdf to perhaps something a bit more complex such as a Portable Case or a load file may be needed. Tagging evidence as you go can save you a lot of time having to go back, re-find evidence and then apply tags.
The other thing the examiner in the example case noticed: in the Recycle Bin, aside from the Dropbox Installer, were a couple of documents that the employee under investigation should not have had access to. The files were privileged and sensitive containing information about company budget and forecasting.
This is where the investigation went from a simple “validate to see if Dropbox was installed on the endpoint” to an insider threat eDiscovery case. The Legal department was ultimately brought in since it was an insider threat. Requests were made for a report, the employee’s PST, and a load file.
If your investigations take an unexpected turn like this, it’s always a good idea to loop in your manager or leader in addition to the stakeholders who initiated the investigation, as well as any other functional groups that make sense.
In our example, HR and Legal were involved, which triggered a larger data collection of digital evidence. Depending on the situation, a covert collection may be necessary. Ensure that collection tools you have at your disposal can perform covert collections so you can perform collections without tipping employees off that they’re under investigation. And yes, AXIOM Cyber can perform covert remote collections.
From here, the scope of the investigation has dramatically increased. Now there are several other data sources that our examiner will want to collect digital evidence from including:
- RAM
- Dropbox
- Google Workspace
- Office 365
- Facebook or any other social media accounts that may be relevant
One of the benefits of AXIOM Cyber is that you can collect digital evidence from a variety of data sources—computer, mobile, and cloud-based data—and analyze it all at the same time.

Phase Three
Analyze Digital Evidence with an Artifacts-First Approach
The artifact-first approach pioneered by Magnet gives examiners an excellent starting point for their examinations and quickly surfaces the insight needed to move through casework with speed and efficiency.
The examiner’s goal is to tell a story. Answer the who, what, where, when, and how. Frame your investigation to answer these questions. When you move forward with your examination, use artifacts to highlight these points.
Below are three things you can do during your analysis of digital evidence that will give help you tell that story — quickly and comprehensively.
Use Hash Lists
As an examiner looking at the collected data, be flexible and creative. The goal is to eliminate “noise” or useless information as soon as possible in the investigation. Start by incorporating a NSRL hash list or, if applicable, a gold image hash list of the base build of the machine. This will get rid of data which is not relevant to the case.
Haven’t used a gold image before to compare against in your investigation? Read this blog, AXIOM at Work: Building a Gold Build Hash-Set for Use in Magnet AXIOM Cyber, for a quick step-by-step walkthrough of how to do it.
Identify Time Frames
By limiting the time frame that you are examining, you will drastically cut down the amount of data that you have to examine.
Remember, if you need to expand your timeframe, you will be able to do this easily. Even with a reduced data set, there are temptations to go down rabbit holes. Although it might be interesting to read every email and chat on a device, seldomly is that time available. Also remember that as you find items of interest, tag them as you go. Tagging as you go is also a good idea because it may help later with organization.
Leverage Machine Learning
Magnet.AI uses machine learning to quickly comb through digital evidence and surface pictures that may be of interest. Watch this video, Magnet.AI in Insider Threat Investigations, to learn more about Magnet.AI and how it could help you.
Back to our example: by running Connections within AXIOM Cyber on these documents, the examiner can see other potential locations where a file (or files) may be located. The Connections feature also provides a visual representation regarding a file’s location. In this case, we could see that the documents were also located on the G: drive, which was identified as a USB hub.
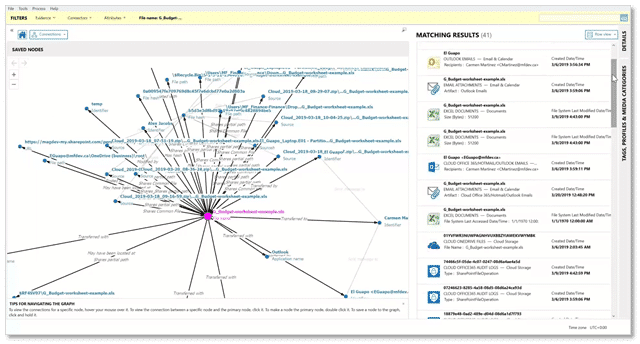
From there, digging into the USB Devices artifact, it’s plain to see that the employee had connected a USB drive to their endpoint and transferred the budget and forecasting spreadsheets to it.

Phase 4
Generate a Load File for an eDiscovery Review Platform
In addition to the normal reporting that you would do as a part of your investigation, specifically for eDiscovery, you may get asked to produce a load file.
Load files are ingested by eDiscovery review platforms such as Relativity or Concordance. eDiscovery Analysts typically on the Legal team, or sometimes an independent third-party consulting agency, will use these tools to complete their review, analysis, production, and presentation of the case.
Load files generated by AXIOM Cyber include:
- A plain text delimited file with a .dat extension in the Concordance / Relativity format containing metadata for the included artifacts
- Folders with accompanying natives and text including:
- MSG file for email
- HTML chat threads for chat messages from Slack or other chat-based communication services
- Original files for documents, media, and other file-based artifacts
Watch this video to see how easy it is to generate a load file using AXIOM Cyber.
Lastly, it’s not uncommon to get asked to debrief with your Legal department and provide your methodology or more context as you worked through the evidence.
You never know when an investigation that you’re working on may end up requiring eDiscovery collection or reporting. Aside from tagging digital evidence as you go, you want to make sure that you’re working with a digital forensics product like Magnet AXIOM Cyber that can covertly acquire from remote endpoints, analyze digital evidence from multiple data sources at once, and then lastly have a convenient way to generate a load file which can be ingested by eDiscovery review platforms like Relativity.
Learn more about Magnet AXIOM Cyber and request a free trial to see how it can help you work through your eDiscovery cases with speed and efficiency.
Technical Advice Disclaimer
Magnet Forensics is dedicated to engaging with the DFIR community through our blogs and whitepapers. However, properly addressing technological issues often includes numerous variables that require independent assessment and strategies designed for each specific circumstance. Since Magnet Forensics cannot have complete insight into all variables involved in a specific situation, this blog/whitepaper is for informational purposes and should not be read as professional advice recommending techniques or technologies to address your specific situation. We do not accept responsibility for any omission, error, or inaccuracy in this blog/whitepaper or any action taken in reliance thereon.