
Anatomy of a Workplace Harassment Investigation
A main focus for many digital forensics examiners working for corporations around the globe are investigations that center around Human Resources (HR) issues such as employee misconduct, misuse of corporate assets, policy violation, and workplace or sexual harassment among others.
Whereas the effects of a malware attack, for example, can be quite concrete and quantified, it’s often more difficult to grasp the long-term effects of employee misconduct. The effects however are quite real and serious; take these stats into consideration:
Harassment is rarely a one-time event, rather it is a prolonged behavior that can last years and affect multiple victims. 70% of people who are harassed in the workplace end up leaving their employer resulting in a high staff turnover, retraining, and potential wrongful termination lawsuits.
When it comes to HR-related investigations, many times it’s a simple matter of confirming alerts from the Security Operations Center or completing a review of an endpoint after a manager initiates a request via HR for an employee to be investigated. But due to the sensitivity of some of these investigations, it’s important to ensure you stay within the scope of your investigation when it comes to what data you can and cannot access. Likewise, you’ll want to make sure you’re getting the most complete picture possible to make sure you’re getting every side of the story.
In this post we’ll break down the timeline for a typical workplace harassment investigation, reviewing both different strategies to employ based on your case as well as artifacts to keep an eye on. We’ll also discuss how to effectively collaborate with your stakeholders such as Legal or HR, who oftentimes for these types of investigations are non-technical.
A Fictional Real-World Case: Audrey and Zach
To give this investigation a little bit of color, we’ll walk through a fictional yet real-world scenario: two employees, let’s call them Audrey and Zach, are quite friendly with each other. However, Zach files a formal complaint with HR that he has been receiving inappropriately romantic emails from Audrey and likewise has been receiving unwanted and inappropriate images via social media from Audrey. Audrey is now under investigation for workplace harassment.
This article has been authored by experts at Magnet Forensics who have worked HR investigations in their roles as examiners in the past. As much as possible, we’ll provide a sequential chronicle of events.

Phase 1: Receive Email Request from HR to Investigate Report of Workplace Harassment
Workplace harassment investigations are typically initiated by an HR representative who’s been assigned the case, although depending on size and structure of the company, it could come from a manager or people leader.
Many times, forensic teams have either an intake form for HR to complete or an email inbox that the team monitors for incoming requests.
Going back to our fictional scenario: you’ve received an email request from HR to investigate Zach’s claims of harassment from Audrey and report your findings. It’s important to note that the investigation is to be covert, meaning Audrey should not be tipped off that she is under investigation.

Phase 2: Acquire Evidence from Cloud, Mobile, and Computer Data Sources
As forensic examiners our job is to interrupt the evidence for our stakeholders, and with that we need to identify the parameters of each case. What are the pieces of evidence we need, do we have the necessary access, and does our forensic software have the capabilities we need to investigate the evidence we’ve identified?
Corporate data can live in so many different places now. It’s not just limited to computer data or PST files, mobile data is primary source of data for corporate examiners, and so is data from the cloud. According to research that we conducted last year in our 2021 State of DFIR report, mobile data is the most frequent data source that DFIR professionals are examining with cloud data—in addition to computer data—factoring heavily into the mix as well.
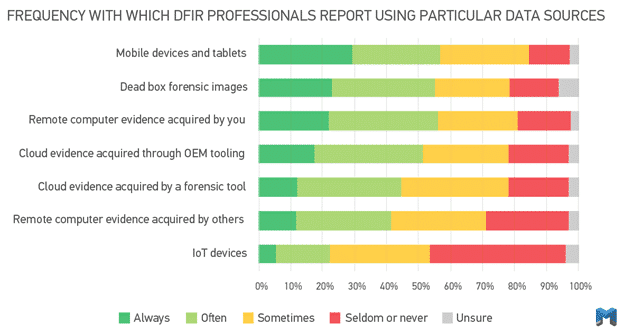
In our fictional example, there are several data sources that the examiner would acquire. Since Zach is a willing participant in the investigation, he can provide a “Download Your Data” package from Google as well as Facebook, both of which can be ingested in Magnet AXIOM Cyber for analysis.
Likewise in this scenario, you may choose to remotely and covertly acquire data from Audrey’s Mac endpoint while she is under investigation. Watch this video, Remotely (& Covertly) Acquire Mac with Magnet AXIOM Cyber, to see exactly how this can be done using Magnet AXIOM Cyber.
Now that you have some evidence, it’s time to begin analyzing it!
Phase 3: Narrow the Scope of Your Investigation
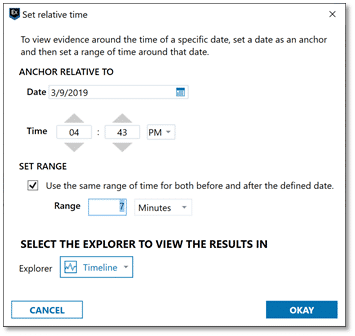
Narrowing down your timeline for the investigation can help remove noise from all of your evidence. Utilizing features such as a Relative Time Filter to identify everything that happened before and after an event based on a timeframe an examiner picks can be helpful, as we see in the image below.
In the Audrey-Zach scenario, Zach pinpointed a time of 4:43pm on September 3 where he received an image that led to his complaint of workplace harassment. As shown in the diagram below, the examiner is searching for that time provided by Zach and they’ve also set a time range of 7 minutes before and after that time, this way you can get a sense of what was happening before and after that time to help provide more context.
In our scenario, the examiner may be interested in Audrey’s Office 365 or Google Workspace account for evidence of any potentially inappropriate emails sent to Zach. Admin logs associated with user’s accounts can also offer insight into their routine.
Magnet offers easy access to both Office 365 and Google Workspace data, whether you want to acquire from within AXIOM Cyber or load manually collected files that you’ve already collected from the platforms.
Windows Event Logs are also a great source of data for workplace harassment investigations. A few Event IDs that might be worth reviewing are:
- Logon ID 4624
- Log Off ID 4634
- User Initiated Logoff 4647

Phase 4: Dive Deeper with Analytics
Once the Relative Time Filter is set, in this case to show events happening 7 minutes before and after the date that was selected, now it’s time to dive a little bit deeper and start piecing together the pieces of evidence. A great way to quickly surface insights is by using the Timeline feature in Magnet AXIOM Cyber.
By combining keyword searching within Timeline, you can now build a sequence of events. And start to put all the pieces of the puzzle together.
Another Analytics feature in AXIOM Cyber that can help speed things up is Magnet.AI. Originally developed for application in law enforcement investigations such as child abuse or human trafficking, Magnet AI is a machine learning algorithm built into AXIOM Cyber that, when turned on, will automatically identify sexual conversations as well as pictures that contain nudity, weapons, drugs, and more. This feature is extremely helpful specifically for sexual harassment investigations in a corporate setting.
Watch this video, AXIOM at Work: Magnet.AI in Harassment Investigations, to see how you can use Magnet.AI for workplace harassment cases.
Going back to Audrey and Zach, the examiner working the case was using AXIOM Cyber and had recently watched the video above. They ran Magnet.AI and discovered something interesting in both the chats and pictures from Zach’s data. Zach’s claim that Audrey had sent “inappropriate” pictures to him was indeed validated, however the examiner also discovered that Zach had also been sending “inappropriate” pictures to Audrey and the chats revealed that the romantic relationship they had was consensual.
Without these key pieces of data, the story is one sided. AXIOM Cyber can be instrumental to presenting both sides of the story.

Phase 5: Share Findings with Key Stakeholders
At this point in the investigation, you’ve reviewed the evidence in question, you have validation of the claim, but also some supplemental evidence which may affect how HR deals with the situation. It’s now that you’ll want to begin preparing your report and findings that will be shared with HR and perhaps Legal or others.
Many times, organizations have standard reports they often use for case work ranging from HTML to PDF and text documents, but with each often come with pros and cons. For investigations that include large amounts of email, you may be asked to export a .PST of the email for the stakeholder to then review within their own environment. Often this is simply loaded into their Outlook, so it’s a tool they are familiar with. However, creating a Portable Case can often be beneficial as well as it requires little training and allows the stakeholders to review the evidence similarly to how the examiner originally did.
In cases that deal with sexual material or nudity, it’s not always necessary to include explicit material since those reviewing do not have to be exposed to the material. It’s best to consult with HR or others as to the extent of what is needed. Reference to the material may be all that’s needed in some cases so long as the evidence exists and is documented appropriately; other times a blurred image is sufficient or depending on the case, everything may be needed.
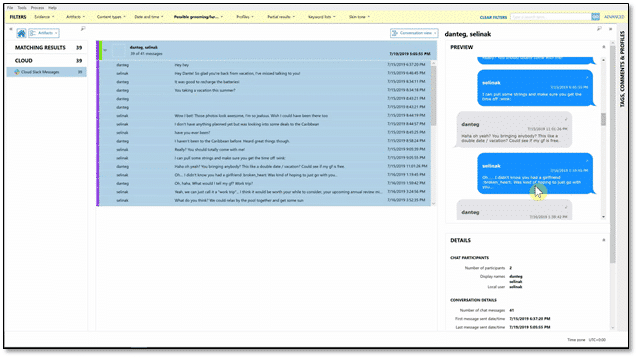
Also, when it comes to chat conversations, look for tools that present conversations in an easy to read and familiar format. AXIOM Cyber does a great job of this so non-technical stakeholders can easily understand what has happened. The screenshot below shows a familiar chat layout that is great for reporting.
Conclusion: Get the Whole Story with AXIOM Cyber
Workplace harassment can have immediate effects on productivity, it has lasting effects on employee morale and the reputation of a company which can affect recruiting efforts and even how customers view a company’s brand and product.
Not to mention the effects it has on individuals; think of Audrey for example: without the extra evidence from AXIOM Cyber, the investigation conducted on her could have gone very differently. At the end of the day, you’re dealing with people and their livelihoods and it’s important to get all sides of the story. It’s important to get the truth.
Learn more about Magnet AXIOM Cyber and request a free trial to see how it can help you get the whole story when it comes to workplace harassment investigations.
Technical Advice Disclaimer
Magnet Forensics is dedicated to engaging with the DFIR community through our blogs and whitepapers. However, properly addressing technological issues often includes numerous variables that require independent assessment and strategies designed for each specific circumstance. Since Magnet Forensics cannot have complete insight into all variables involved in a specific situation, this blog/whitepaper is for informational purposes and should not be read as professional advice recommending techniques or technologies to address your specific situation. We do not accept responsibility for any omission, error, or inaccuracy in this blog/whitepaper or any action taken in reliance thereon.