
Anatomy of A Data Breach Investigation
The effects of a data breach on an organization can have long term, lasting effects. Erosion of customer confidence, loss of established goodwill, costs associated with remediation, and legal ramifications may linger for years.
Data breaches can occur multiple ways:
- A company’s network could be breached
- Malware could be installed that gives an attacker access to the system
- Unsecured webservers/websites can be scraped for data
- And there is always the threat of an insider—an employee or a contractor for example—leaking information
In September 2021, Upguard.com listed the 57 biggest Data Breaches by Impact; the largest data breach they reported contained 10.88 BILLION records. And that is just one of the breaches!
There is also an emerging data breach trend: double extortion.
Double extortion occurs when a victim suffers both a ransomware attack and a data breach in quick succession. Cybercriminals are anticipating that the victim organization is going to direct all of its attention to the ransomware attack and very little to no attention to the data breach. The ransomware effectively ends up being a distraction to the real attack: the data breach.
There are two scenarios that typically play out in a double extortion data breach attack:
- If you’re able to restore back-ups, you can possibly recover from the ransomware event without paying the cybercriminals for the decryption key. In this instance, they will contact you, even congratulate you, and then demand a fee not to publish the data that was exfiltrated.
- If you are not able to restore backups and pay the cybercriminal for the decryption key, they know that you have money. After the ransomware transaction is completed, you will get hit with extortion for the data which was breached.
Incidents like this are becoming much more common. Regrettably, if the cybercriminal feels mistreated during the first exchange, the second extortion amount may be greatly increased and you could end up having to “play nice” with the criminal that stole your data.
Decisions will have to be made regarding payment to keep the stolen data from being revealed. What is the cost of paying the extortion versus the cost of having the data published? Remember, there is no guarantee that if you pay, that the bad guy won’t come back and ask for more money, sell the data to another criminal group or publish it after you pay.
In this post, we will work through what the timeline of a data breach investigation might look like. Magnet Forensics has a team of experts who have worked data breach investigations, they have lent their perspectives to the creation of this article.

Notification of a Potential Breach
There are so many alerts that can occur every day, it is easy to become complacent. SOCs receive a variety of alerts on any given day. These alerts can range from endpoints attempting to connect to URLs that are blacklisted, to potentially unwanted programs (PUPs) being downloaded and installed, to EDR tool alerts on potential malware and quarantine events.
While it’s important for analysts and investigators to review each and every alert the SOC receives, it’s just as critical not to get tunnel vision when working alerts. Cybercriminals may have a multi-pronged attack that is used to cover up the actual mission they are trying to accomplish. This could be releasing ransomware within the environment, while copying endless amounts of your company’s data off for distribution on the web. Bear in mind, attackers want to maintain persistence in a system.
If a valid attack is identified, be on the lookout for other indicators of compromise (IOCs). Some attacks are false flags designed to obfuscate another attack. (e.g. a DDoS attack after a Business Email Compromise). Other times, attacks are used to cover the tracks of the cybercriminals. Ransomware is a great example of this; ransomware can be like throwing a grenade in a room to cover the evidence of another crime.
In some cases, the evidence of a data breach is discovered only after the data has been posted for sale on a criminal forum or the data is being exploited.
Forensics and forensic tools have become a necessity to examine endpoints for IOCs. Cybercriminals have dramatically increased the technicality of their attack vectors. The malware available today on criminal forums ranges from Ransomware-as-a-Service (RaaS), file-less malware which only runs in memory, custom written malware and, on the extreme, the constant battle against new zero-day exploits. The forensic tools that you use must be fast, and they must be accurate.
When validating security alerts a forensic investigations team may want to quickly triage an endpoint before completing a full in-depth analysis of what caused the alert. In cases where triage is a first step, tools like Magnet IGNITE can be configured for a variety of case work based on the needs for the investigation. It’s also worth noting IGINITE can easily be deployed to multiple endpoints simultaneously in the case multiple alerts from different devices have been received.
In cases where the data has been exposed or exploited, digital forensics can help to point you quickly to the files which contain the exposed data. Once the relevant files have been identified, products such as AXIOM Cyber can be used to determine the telemetry of the associated file.

A Set of Alerts Have Been Confirmed, It’s Time to Act
After you have confirmed an incident, follow your incident response plan. The who, what, where, and how will be answered soon but the immediate problem is notification and gathering teams to address the incident and subsequent investigation.
Things to keep in mind:
- Communication is vital but be aware! If an attacker has a foothold in your network, they may be monitoring your emails as well as actions you take to secure your network.
- Internal communication and strategies need to be communicated but keep the messaging straightforward – articulate deliverable steps to personnel.
- Your plans will change during the event. It is almost impossible to preplan for all the variables of an incident. Document deviations from the plan, why the deviation occurred and the steps that were taken to address the situation.

There are some immediate questions that may need to be answered:
Determine the Extent of the Damage While Preserving Evidence
- How long has our data been vulnerable?
- How much data has been exposed?
- Is data leakage still occurring?
- Are there regulatory implications regarding the breach of data?
- Was customer data or Personal Identifiable Information (PII) taken? How much?
Identifying what was taken in a breach is one of the first steps needed to correct the problem. If the data was scraped from websites, this will lead us down one path. If the data was exfiltrated due to malware, we are in a slightly different direction. Or, third, it could have been stolen by an insider. Each scenario warrants a different forensic response.
You are going to want to examine data from a variety of sources including:
- Firewall logs and rules: Was the firewall set up to monitor outbound traffic? Outbound SSH traffic?
- System logs from web servers: Is there evidence of increased traffic that is out of the normal parameters for that system? Is there evidence of URL or credential stuffing?
- Individual endpoint systems: Windows logs, RAM, Process capture, and full disk images may all be needed to show user attribution to a file or files.
- Antivirus logs: Has malware been detected in the environment? What are the characteristics of this malware family?
And keep in mind, if you have a possible insider threat, how will you image that employee’s issued computer if they are remote?
The forensic tool at your fingertips should be nimble, powerful, and easy to use. These characteristics will enable you to act with both speed and precision. We believe Magnet AXIOM Cyber fits the bill very well to perform root cause analysis when investigating a data breach.
Here are a number of ways that AXIOM Cyber specifically can help with your data breach investigation:
- Powerful analytics features can reduce your time to evidence:
- Connections will visually show you how a file, a malicious payload for example, originated and where it and how.
- Relative Time Filters within AXIOM Cyber will allow you to quickly narrow your window of artifacts that need to be examined.
- You can analyze Linux artifacts coming from servers or other devices within your network that will help identify network traffic going to and from the infected device giving you clues as to how the attacker moved through your network and possible what other endpoints may be infected.
- Remote acquisition of target endpoints can be performed, even when they’re not connected to your corporate network via VPN. Watch this video to see how you can perform remote acquisition of an off-network endpoint with AXIOM Cyber.
- Capturing and analyzing RAM/memory and disk images from a remote computer may indicate that an insider had a role in the breach.
While taking these steps, it is also vitally important to maintain copies of “original evidence” (the data that you collect before it is analyzed) for regulators or for possible prosecution.

Ensure Your Systems Are Secure
Once the source of the breach is confirmed, make sure that any vulnerabilities are addressed. Indicators of Compromise found during previous steps can be used to assist in securing systems and networks within the environment.
Customer data and specifically customer PII being released can have dire consequences. If it happens, it needs to be vigorously addressed but if it happens a second time, the significance is exponentially multiplied. Unlike some attacks which can be kept quiet and in house, data breaches with external leakage will garner news. Being forthcoming with remediations to ensure that this does not happen again may want to be included in your external communication plans.

Reporting Internally and Externally
You should expect to create internal reports but depending on your industry and the amount of data exfiltrated, external reports may also need to be written. These external reports may have to address customers, regulators or even stockholders.
Communicate the valuable lessons learned and that the vulnerabilities which led to this situation have been addressed.
When putting together your report, one of the most effective ways to go about presenting your findings is by showing a relative timeline of events. AXIOM Cyber has a feature called Relative Time Filter allows you to narrow the time frame of data that is being examined and reported.
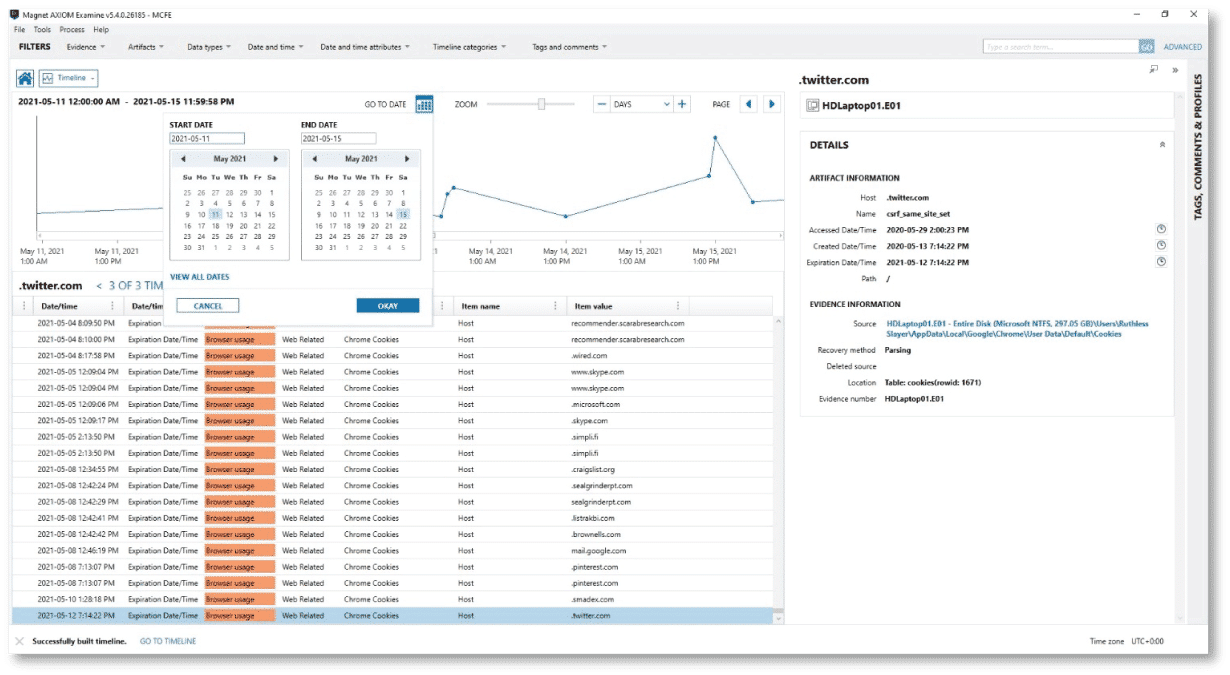
When using the relative time filter, you can then pick and choose what you want to include in your final report taking screenshots along to way to support your evidence.
Another feature of AXIOM Cyber that can help you build your report is Connections. Connections will assist you in determining actions and programs which have interacted with the file in question.
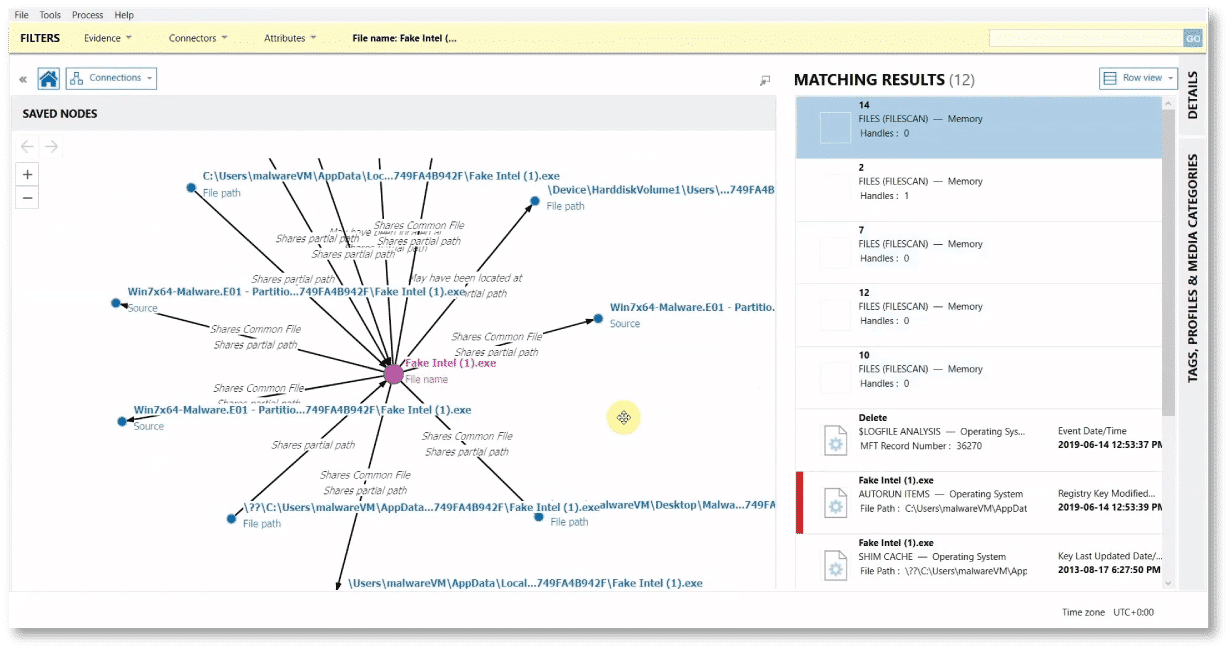
Using the information from Connections and the relative timeline features, you will be able to address the steps that were used to exfiltrate the data.
Armed with that information be able to address several of the who, what, when, where, and how the systems were breached.
Many investigations follow the same overarching patterns regarding how the analysis will unfold. It is important to have the tools to quickly address digital forensic issues such as a data breach. While there are several different tools that you’ll use throughout an entire lifecycle of a data breach investigation, AXIOM Cyber can be an integral part of your road to recovery.
Learn more about Magnet AXIOM Cyber and request a free trial to see how it can help you with all of your corporate digital forensic investigations.
Further Reading
Technical Advice Disclaimer
Magnet Forensics is dedicated to engaging with the DFIR community through our blogs and whitepapers. However, properly addressing technological issues often includes numerous variables that require independent assessment and strategies designed for each specific circumstance. Since Magnet Forensics cannot have complete insight into all variables involved in a specific situation, this blog/whitepaper is for informational purposes and should not be read as professional advice recommending techniques or technologies to address your specific situation. We do not accept responsibility for any omission, error, or inaccuracy in this blog/whitepaper or any action taken in reliance thereon.