
Custom Targeted Locations with Magnet AXIOM Cyber
In this blog we’ll discuss how examiners can now create their own custom Targeted Locations with AXIOM Cyber, saving you time by eliminating the need to navigate the file tree for artifacts that are frequently needed in casework.
If you haven’t had the opportunity to try AXIOM Cyber yet, make sure to request a free trial here. And for those who already have AXIOM Cyber, make sure to head over to the Magnet Customer Portal to update today!
When we decided it was time to make a dedicated corporate product, our main objective in doing so was to rethink the common complaints we heard from examiners working cases day in and day out. We took a different approach with AXIOM Cyber, enabling examiners to deploy agents to both Windows and Mac endpoints as needed with an ad hoc approach versus the traditional approach of having agents preinstalled on every endpoint. Speaking from personal experience, reconfiguring and updating mass-deployed agents can be a challenging endeavor in corporate environments when coordinating with multiple teams from across the organization.
We also wanted to incorporate our artifact-first approach into the remote acquisition phase of the investigation by providing examiners an already curated list of Targeted Locations they could quickly select to collect from for both Windows and Mac. The list below includes what comes preconfigured with AXIOM Cyber.
Preconfigured Targeted Locations
| Item | Operating system | Description |
| All users – Folders | Windows, macOS | Download items from the default User folder location (C:\Users\username\*.*, /Users/username/*.*) for all users. |
| All users – Desktop items | Windows, macOS | Download items from the default Desktop folder location (C:\Users\username\Desktop\*.*, /Users/username/Desktop/*.*) for all users. |
| All users – Documents | Windows, macOS | Download items from the default Documents folder location (C:\Users\username\Documents\*.*, /Users/username/Documents/*.*) for all users. |
| All users – Downloaded items | Windows, macOS | Download items from the default Downloads folder location (C:\Users\username\Downloads\*.*, /Users/username/Downloads/*.*) for all users. |
| Web browsing activity | Windows, macOS | Download web browsing activity such as history, temporary internet files, download history, cookies, and more for Chrome, Firefox, Internet Explorer, 360 Safe Browser, and Opera. |
| Registry files | Windows | Download registry files from the target computer. For example, registry files located at C:\Windows\System32\config\*.dat and C:\Users\username\NTUSER.dat. |
| Event logs | Windows | Download event logs from the target computer. For example, event logs located at C:\Windows\System32\config\ and C:\Windows\System32\winevt\Logs. |
| Pagefile.sys | Windows | Download the pagefile.sys file from the target computer. |
| Swapfile.sys | Windows | Download the swapfile.sys file from the target computer. |
| $MFT | Windows | Download the Master Table File ($MFT) from the target computer. |
| iOS backups | macOS | Download iOS backups for all users. |
| iCloud data | macOS | Download iCloud data for all users. |
| Unified logs | macOS | Download unified logs from the target computer. |
| Quarantine files | macOS | Download files with a quarantine flag from the target computer. |
| Bash | macOS | Download bash sessions for all users. |
| Spotlight shortcuts | macOS | Download Spotlight shortcuts for all users. |
| Daily.out | macOS | Download the Daily.out file from the target computer. |
| Finder MRU | macOS | Download information about recently accessed paths in the Finder application for all users. |
| App Store downloads | macOS | Download a history of App Store downloads from the target computer. |
Custom Targeted Locations
Adding new Targeted Locations so you only remotely collect exactly what it is that you need is a breeze with AXIOM Cyber 4.2!

- Navigate to the Targeted Locations section within AXIOM Process
- Select “Add New Targeted Location”
- Name your new location and complete the path you want AXIOM Cyber to collect from
In the example below, I’ve created a new Targeted Location with a description of Company Information_All Users. In the path information section, I’ve designated AXIOM to recursively acquire all the contents of the folder “Company Information” from every user found on the endpoint.
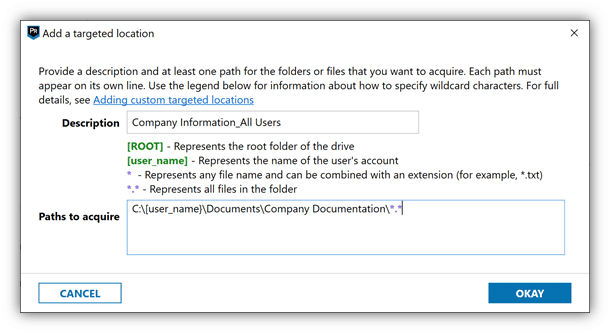
A few important things worth noting when building new Targeted Locations:
- Using [user_name] in the path will search all user folders on the endpoint
- Examiners acquiring a folder via star-dot-star (*.*), will be recursive, in that it will grab all folders therein
- filename extensions (*.txt, for example) are not recursive
If you have any questions or have ideas on new artifacts you’d like to see supported with AXIOM Cyber, don’t hesitate to reach out at trey.amick@magnetforensics.com