
Anatomy of a Data Exfiltration Investigation
In the United States, 62% of Insider Threats are data exfiltration. This is, by far, the most common type of Insider Threat, with three times more frequency than the second most common Insider Threat: privileged misuse.
Data exfiltration or IP theft, is simply when data walks out the door of your business. These types of security events can be carried out by an external threat actor or from a maliciously-acting insider such as an employee or third-party contractor. Often, an employee inadvertently leaks data. According to the AT&T Insider Threat Report, inadvertent data breaches or negligent employees are more worrisome than malicious data breaches.
And unfortunately for businesses, they aren’t aware that data has been exfiltrated—or is being exfiltrated—from their organization until it’s too late. This often causes monetary loss and damage that is unquantifiable. It’s the job of the digital forensics examiner to find out who exfiltrated the data, how, and where it went. They need to try to recover as much of it as possible or mitigate the damage caused by the data once it’s out in the wild.
An “Unlikely” Case of Data Exfiltration
The case described in this blog post is a real-world case (names and references to companies have been fictionalized) worked by Magnet Forensics’ Steve Gemperle who is a Forensics Consultant. At the time, Steve was a Senior Special Agent, specializing in cybercrime, working with the United States Secret Service. Although no two data exfiltration cases are the same, we’ve tried to highlight an approach that you can take to investigating data exfiltration and apply it to your own practice.
Phase One: Get Notification That Data Exfiltration Has Occurred
Our data exfiltration scenario case begins in one of the most unlikely ways: with a traffic violation. Jimmy Lowry is pulled over for running a red light. Upon inspection of Jimmy’s vehicle, officers find weapons, multiple forms of ID, narcotics, and a computer.
Turns out Jimmy had a previous record. Due to contents of his vehicle, the case was referred to Special Agent Steve Gemperle at the United States Secret Service, who had the task of performing a digital forensics examination on the computer discovered in Jimmy’s vehicle in addition to his mobile phone.
At this point in time, Steve is unaware that he’s in fact working a data exfiltration case. Rather, he’s under the impression it’s a weapons or drug trafficking case, or even a case related to the multiple fake IDs discovered in Jimmy’s vehicle.
Steve acquired data from the computer and mobile device and analyzed them together. It’s important when analyzing evidence from multiple data sources that you’re analyzing the data all together in one tool. This ensures that there is data consistency and that you can follow items of evidence as it moves from one data source to another. Magnet AXIOM Cyber is an excellent tool for analyzing data from computers (Windows, Mac, and Linux are all supported), mobile devices, and cloud-based data.
Upon his exam, he noticed something interesting: thousands of records of personally identifiable information (PII) including names, dates of birth, social security numbers, banking information, and more. And they were all military personnel.
Through some digging, Steve eventually discovered where the thousands of names had been exfiltrated from and he ended up at the door RUSH Data Consulting: a third-party government contractor.
It’s at this point that RUSH was notified that they’d fallen victim to data exfiltration.
Being notified by the United States Secret Service that data has been exfiltrated from your company is definitely one way to find out. However, there are other ways that your company may discover data exfiltration:
- You’re actually notified by a threat actor that your data has been stolen and it’s being ransomed
- It’s discovered for sale on the dark web
- Banks identify your business as a common point of compromise for PII and/or credit card information.
- You may hear complaints from customers
If you get lucky and are tipped off to data exfiltration from your own internal systems or teams, you may have a chance to get ahead of it and potentially prevent data exfiltration from happening. Those notifications could look like the following:
- IT reports of misconfigured databases that reveal customer information
- IT sees large amounts of encrypted traffic outbound
- IT reports download or uploads to external devices or non-company approved cloud storage (OneDrive, Dropbox, etc.)
Regardless of how you find out about the instance of data exfiltration, what you as the examiner do next is most likely the same: you gather your evidence wherever it is.
Phase Two: Gather and Connect Evidence
When Special Agent Steve Gemperle and his team met the executive team and the Director of IT, Rhonda Leonard, they explained the situation operating under the premise that RUSH’s network had been breached and PII was stolen.
Steve worked with Rhonda Leonard who was very cooperative and got access to RUSH’s network and began trying to find indicators of compromise or evidence that the network had been breached—read Anatomy of a Data Breach to find out more about how to work a data breach investigation. However, upon looking at the network every which way, the network was clean.
Time to try a new approach! An as a digital forensics examiner, technical skills are extremely important, but the investigative skills that you hone are also important to get you going in the right direction.
Steve also had other evidence at his disposal from Jimmy’s laptop and mobile device. Now that a data breach was ruled out, he started to look at the data through a new lens. Going back to the thousands of names on the laptop, Steve discovered they originated from a personal OneDrive account that Jimmy had created. Oddly, the thousands of names didn’t originate from the laptop Steve had in his possession but were actually downloaded from the OneDrive account.
Magnet AXIOM Cyber has a feature called Connections that is useful for tracking an item of evidence, for example, a user account, a device, or a file. Using Connections, Steve was able to focus on the OneDrive account and connect it to another device connected to Jimmy’s OneDrive account.
As you could imagine, Jimmy was not cooperative. So, through execution of a search warrant, Steve and his team were able to gain access to Jimmy’s residence and search for the device that originally had the thousands of names on them. The search did come up successful and another laptop was found, that appeared to be the property of RUSH Data Consulting.

Phase Three: Put Your Suspect Behind the Keyboard
Steve validated that the newly found laptop from Jimmy’s apartment was the original source of the thousands of names and associated PII and that the names had been uploaded to Jimmy’s OneDrive account.
It’s important to note that to prove your suspect was the one who was actually doing all of this, you’ll need supporting evidence to show put your suspect behind the keyboard—because you know the claim will inevitably be “it wasn’t me”. In Steve’s case, he looked at a few artifacts to identify Jimmy as indeed being the individual behind the keyboard when records were uploaded.
Using the Relative Time filter in AXIOM Cyber, you can pick a specific time when you know an event occurred and then discover what happened on the device before and/or after that specific time. Watch this video to see how you can search for evidence using the Relative Time filter:
Steve knew that the records had been uploaded to OneDrive at 2:43AM. Setting a relative time filter for to search for activity from 2:13AM to 3:13AM revealed what Steve characterized as the smoking gun to put Jimmy behind the keyboard.
Using Web Related artifacts, he was able to see that Jimmy had logged into his online banking portal at 2:39AM — only minutes before the upload to OneDrive began.
Using a digital forensics platform like AXIOM Cyber, one that has an artifacts-first approach, will help you through your investigation with speed and insight. Here are some useful artifacts that you can look at to try to put your suspect behind the keyboard and disprove the “it wasn’t me” excuse:
- Browser History – web browser history can give you granular and very personalized insight (e.g., logging into online accounts) into what a user is doing and when
- Cloud Artifacts – cloud-based file sharing applications (e.g. OneDrive, Dropbox, even email services like Gmail) are commonly used to move information from one spot to another. Using this artifact as the anchor of an event will help put other items of evidence in contextArtifact2 – explanation
- Recently Used Applications – Having a view of different applications and the times that they were used will help guide you down the right path and dig deeper into specific items of evidence
Now back to RUSH: Steve connected with Rhonda Leonard to now identify the laptop belonged to RUSH. He asked for device inventory records from Rhonda, but strangely the device that he had obtained from Jimmy’s residence wasn’t listed on the inventory…odd. It was at this point that Rhonda started missing meetings with Steve and became less and less cooperative…also odd.
Time to try a new approach: since Rhonda’s behavior is suspicious, Steve began to exclude her from activities and instead worked with RUSH’s Finance team to get an inventory of all devices purchased. It was on this list that the laptop in Jimmy’s residence appeared and proved that it had in fact belonged to RUSH.
This is where things begin to get interesting.
By examining document versions of inventory records, Steve discovered that Rhonda had intentionally altered records of RUSH’s device inventory to remove the laptop in question. Rhonda has now gone from a cooperative ally to a suspect.
But why?
In an interesting twist, it turns out that Rhonda Leonard is Jimmy Lowry’s mother and she had given him the laptop. And before she gave Jimmy the laptop, she didn’t wipe it and didn’t keep a record that she had disposed of the device.
Data was inadvertently exfiltrated from RUSH due to Rhonda’s negligence. Recall the statistics mentioned at the beginning of this post: the most worrisome Insider Threats are advertent data breaches and negligent employees. This “unlikely” case of data exfiltration is actually a very likely case of data exfiltration and has the characteristics of what businesses worry most about.
Phase Four: Report Findings Demonstrating Forensically Sound Methods
As you could imagine, there was quite a bit of fallout that resulted from this case of data exfiltration. Jimmy Lowry was charged with Fraud, Possession and Manufacturing of False Identification, Fraudulent Use of Credit Cards, among other things and was sentenced.
RUSH Data Consulting lost their contract with the US government resulting in the loss of millions of dollars of revenue.
Rhonda Leonard was terminated from RUSH and was also sued by RUSH due to the loss of their government contract. She was also charged with Making False Statements to government officials since she had tried to cover up her involvement in the case and had outrightly lied to Gemperle throughout the investigation.
A large part of the cases brought against both Jimmy and Rhonda was the digital evidence gathered by Special Agent Steve Gemperle. As he worked through his case, in addition to his forensically sound approach, he used forensically sound digital forensics tools such as Magnet AXIOM Cyber.
While it may seem arduous to go through the effort of gathering and analyzing digital proof of many things that are assumed to be true, when a case goes to court, this digital proof is invaluable.
The report Steve produced was instrumental in proving the many different aspects of his case. And the creation of the report was made easier since the forensics tool he was using had the ability to produce a report based on his examination, items of interest that he had tagged and was able to include specific artifacts of interest—such as Jimmy’s smoking gun web browsing history.
Magnet AXIOM Cyber has reporting and report building functionality included in it which is convenient to ensure that all the relevant pieces that key stakeholders need to know is included. Here’s a view of the type of flexibility that AXIOM Cyber can offer in its reporting.
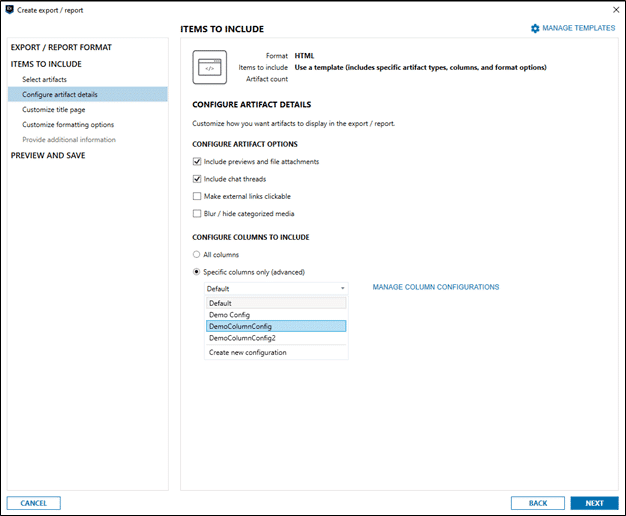
Oftentimes reports are intended for non-technical stakeholders, AXIOM Cyber makes reports that are easy to read, visual, and easily digested by folks like HR, Legal, or even a jury.
Learn more about Magnet AXIOM Cyber and request a free trial to see how it can help you with all of your corporate digital forensic investigations.
Further Reading:
- Anatomy of a Business Email Compromise Investigation
- Anatomy of an eDiscovery Investigation
- Anatomy of a Workplace Harassment Investigation
- Anatomy of a Data Breach Investigation
- Anatomy of a Ransomware Investigation
Technical Advice Disclaimer
Magnet Forensics is dedicated to engaging with the DFIR community through our blogs and whitepapers. However, properly addressing technological issues often includes numerous variables that require independent assessment and strategies designed for each specific circumstance. Since Magnet Forensics cannot have complete insight into all variables involved in a specific situation, this blog/whitepaper is for informational purposes and should not be read as professional advice recommending techniques or technologies to address your specific situation. We do not accept responsibility for any omission, error, or inaccuracy in this blog/whitepaper or any action taken in reliance thereon.