
Anatomy of a Business Email Compromise Investigation
While ransomware and phishing attacks seem to dominate cybersecurity headlines and mindshare, there is another threat, one that is arguably stealthier and more dangerous: business email compromise (BEC) or also sometimes called CEO fraud.
A business email compromise attack uses the principles of social engineering where a threat actor will send a well-crafted email that’s tailored to an individual or a small group of people — usually in the finance department or sometimes human resources. The email is typically sent from a spoofed email address of the CEO (hence the name CEO fraud) or another senior leader and will express an urgent and often clandestine need to transfer money.
There are obviously many different variations of a business email compromise attack. To get a sense of how they vary, Tessian, an email security provider, has a good overview of 8 Real-World Examples of Business Email Compromise Attacks. Regardless of how they vary, the ultimate goal of the email is to convince the recipient to transfer money via wire transfer or send sensitive information.
Here are a few stats that speak to the severity of BEC and the damage that it has wreaked as of late:
- Based on complaints received from the FBI’s Internet Crime Report, BEC schemes were the costliest in 2020 with losses reported at 1.8 billion dollars.1 From the same report, the FBI says that BEC attacks are 64 times worse than ransomware.
- The APWG Phishing Activity Trends Report states that the average amount requested in wire transfer BEC attacks in Q2 2021 was $106,000, up from $75,000 in Q4 2020. Threat actors are becoming greedier and more sophisticated at the same time.2
This doesn’t even take into account those BEC attacks which were executed so flawlessly that the target organization didn’t even know they had been scammed!
This post will outline a fictional, yet real-world example of a BEC attack. Our example scenario begins with Sven Jansen, an Accounts Payable Clerk, getting an urgent email from his CEO telling him to transfer money to an account.
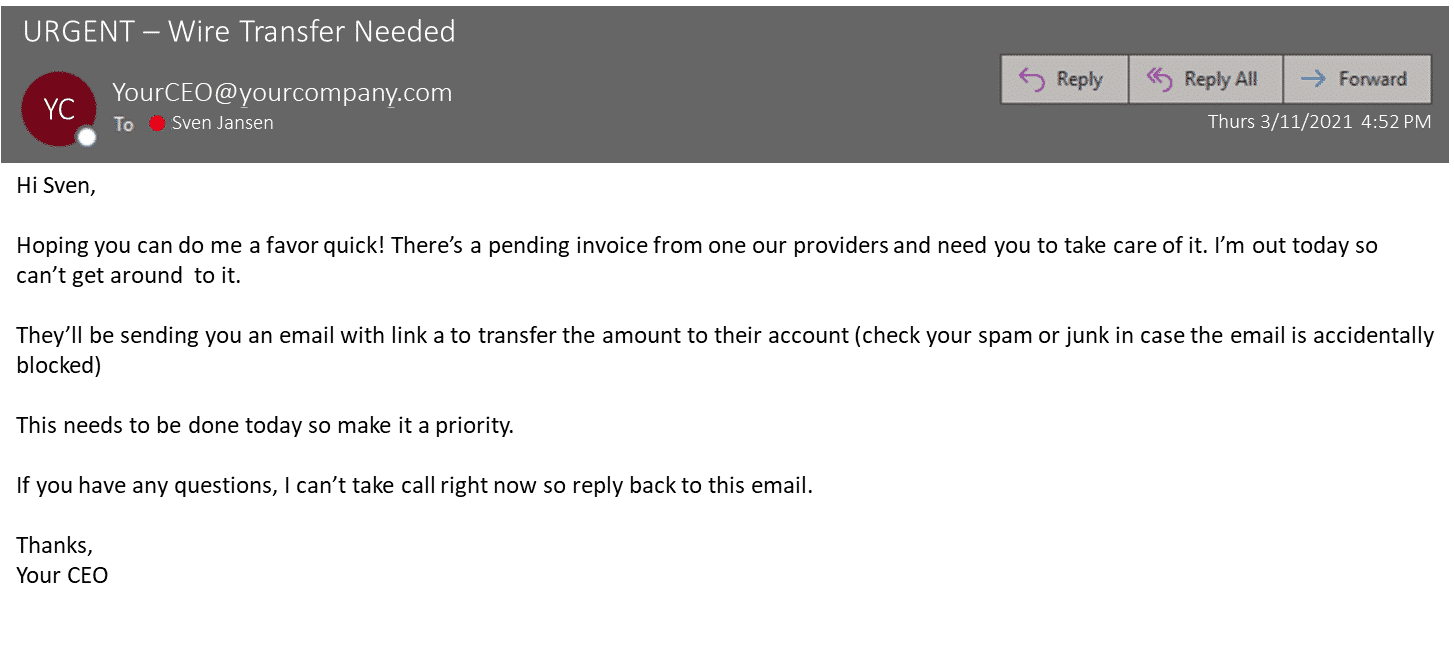
The email, while looking legit, has a couple of tell-tale signs of a well-crafted, socially engineered, BEC attack:
- It’s in a natural and casual tone with no spelling errors and it’s grammatically correct.
- Urgency is expressed several times, it’s in the email subject line itself and throughout the body of the email too.
- The email was sent late in the day, it was sent at 4.52 PM. It’s typical for BEC scam emails to be sent late in the day and often on a Thursday or Friday or before a statutory holiday.
- The instruction is not to call the CEO since they’re out. Rather the instruction is to reply to the email which will obviously be received by the threat actor.
- Another common tactic used in emails like this—which wasn’t used in the email to Sven—is to keep the wire transfer a secret or not to tell anyone else.
Unfortunately, Sven, like thousands of others, didn’t recognize that he was the target of a business email compromise attack. Before heading home on Thursday, he sent a wire transfer as he was instructed in the email his CEO mentioned. On Monday, Sven’s manager noticed something was off. They confirmed with the CEO that they didn’t send Sven an email on Thursday asking him to transfer money…
And this is where the investigation begins.
Phase One: Collect Evidence from the Business Email Compromise Target Endpoint
Although working a BEC investigation may not feel as urgent or time sensitive as a data breach or a ransomware attack, there is urgency when it comes to validating and confirming a BEC attack has occurred. The sooner you can confirm what has happened — and how — the better chance your organization has of stopping or reversing the payment.
You’ll often know exactly what it is that you’re looking for. It’s simply a matter of doing your due diligence and gathering evidence. The tool that you use for collection should allow you to be very targeted to minimize the amount of time spent acquiring that isn’t necessary to your investigation.
Magnet AXIOM Cyber gives you a high degree of flexibility when it comes to how targeted you want to be in your collection. AXIOM Cyber includes preconfigured targeted locations, such as Desktop Items, Documents, and Web Browsing Activity—all of which have high evidentiary value.
But AXIOM Cyber also give you the ability to create your own targeted locations depending on how much you need to collect or on the case type. To learn more about how custom targeted locations in AXIOM Cyber, read Custom Targeted Locations with Magnet AXIOM Cyber.
Plus AXIOM Cyber has the ability to perform remote collections of target endpoints even when they’re not connected to your corporate network either physically or via VPN.
Now that you’ve quickly collected the data that you need, it’s time to analyze it.
Phase Two: Analyze the Evidence and Validate the Business Email Compromise Attack
Thinking about our scenario with Sven, we already have the anecdotal and verbal evidence to confirm what has happened. However, it’s the forensic examiner’s job to get the digital evidence to prove what happened and tell a comprehensive story.
You’ll want a forensics tool that will allow you to work quickly and give you the best chance for a timely response. This will hopefully help you stop or reverse any payment made.
Again, AXIOM Cyber is a good choice for analysis of digital evidence due to its strong artifact support for Office 365 and Google Workspace. Items of interest that an examiner needs to be looking for include: forwarding rules, login activity, any changes to permissions, indictors of when the malicious activity started, and if any data was exfiltrated.
Unified Audit Logs and User Access Logs are two artifacts in AXIOM Cyber that can provide a great amount of insight as you are working through a BEC attack investigation.
Unified Audit Logs
Consider starting your investigation by collecting Unified Audit Logs from your email provider. Many organizations utilize Office 365 or Google Workspace for both email as well as their productivity suites. This blog post, Expanded Office 365 Unified Audit Log Capabilities with Magnet AXIOM Cyber, provides a great walkthrough on how to collect these logs and import them into AXIOM Cyber.
Some of the relevant information that can be found in the Unified Audit Logs includes Roles and Permissions, forwarding rules, login activity, permission changes, IP addresses, and data exfiltration.
User Access Logs
Depending on your network set-up, you might also want to pull User Access Logging. This artifact aggregates client usage data by role and product within Microsoft’s Windows Server application. User Access Logging includes a ton of useful data including:
User related data
- Username
- Activity count
- First Seen
- Last Seen
- Role GUID
- Role name
Device related data
- IP Address
- Activity Count
- First Seen
- Last Seen
- Role GUID
- Role Name
Dive deeper into accessing Windows User Access Logs with this on-demand webinar: No logs, no problem: Leveraging User Access Logging on Windows Server systems.

Phase Three: Attempt to Stop or Reverse Payment by Contacting Your Financial Institution or Law Enforcement
At this point, after you’ve created your brief report, your job as a forensic examiner is pretty much over. However, what happens next can take a significant amount of time: trying to stop the payment made to the BEC attacker or reverse it.
The first step is to know who to contact if your organization has fallen victim to a BEC attack. Here are a few suggestions of who to contact after you’ve confirmed a successful BEC attack.
Financial Institution
Individuals and businesses need to contact their respective financial institutions as soon as possible. The window to stop wire transfers is extremely short (often the window closes within 72 hours.) The criminals know this and will often send these compromised messages on Thursday or Fridays.
Internet Crime Complain Center IC3 or equivalent agency
In the United States, the Internet Crimes Complaint Center or IC3 is the main “clearing house” that tracks BEC attacks and other types of cybersecurity events. Keep in mind that both attempted (but unsuccessful) and successful business email attacks should be reported. Keeping track of all attacks enables law enforcement to put pieces together and go after criminal organizations.
Law Enforcement
Consider contacting law enforcement or your local United States Secret Service or FBI office as soon as possible. Law enforcement agencies may be able to assist financial institutions in the recovery of stolen funds.
One of Magnet Forensics’ amazing Forensic Consultants is Steve Gemperle: a former Senior Special Agent with the United States Secret Service who specializes in cybercrime. When it comes to contacting law enforcement if you’ve suffered a BEC attack, Steve says:
This step is extremely important. Both the Secret Service and the FBI have additional tools to assist financial institutions or legal means to stop money from being transferred through accounts if they are notified quickly. Federal law enforcement has the capability to work across state lines and they have formed close working relationships with banks to combat this type of crime.
Steve Gemperle
You may be wondering: what happened to Sven? Sven’s company ended up contacting their financial institution but weren’t successful in having the wire transfer reversed. They ended up getting in touch with federal law enforcement who served a search warrant to their financial institution to stop the payment. Over the timespan of six months and 13 days (and many court proceedings), Sven’s company got their money back and the BEC attackers were arrested.
Learn more about Magnet AXIOM Cyber and request a free trial to see how it can help you work through your eDiscovery cases with speed and efficiency.
Further Reading:
- Anatomy of an eDiscovery Investigation
- Anatomy of a Workplace Harassment Investigation
- Anatomy of a Data Breach Investigation
- Anatomy of a Ransomware Investigation
- Anatomy of a Data Exfiltration Investigation
Technical Advice Disclaimer
Magnet Forensics is dedicated to engaging with the DFIR community through our blogs and whitepapers. However, properly addressing technological issues often includes numerous variables that require independent assessment and strategies designed for each specific circumstance. Since Magnet Forensics cannot have complete insight into all variables involved in a specific situation, this blog/whitepaper is for informational purposes and should not be read as professional advice recommending techniques or technologies to address your specific situation. We do not accept responsibility for any omission, error, or inaccuracy in this blog/whitepaper or any action taken in reliance thereon.