
Why Only Working with Logical Images Isn’t Always Logical
You’re probably starting to realize that not all mobile backups are the same.
The type of backup we can achieve may depend on several factors. Knowing passwords/passcodes and the methods used can play a part in the amount of data contained in the extraction, as well as the categories of that data.
We are going to look at how this plays into examining iOS devices. (As a matter of reference, the same iPhone 6s from the same point in time was used to examine the artifacts described.)
Extraction Methods for iOS Devices
Let’s talk first about extraction methods. If you’re an iOS user, you’re familiar with the term “backup”. In the past, it was popular for users to back up their data to their local machine using iTunes. We often found those when doing workstation exams and could export them for further analysis. Now many users opt to back up their devices to the Cloud.
Then came the encrypted backup, where Apple provided some help in securing portions of user data. What that meant to the examiner was that without the encrypted backup password, data would be left unexamined.
In this example, Magnet AXIOM was used to acquire a “quick” image of our iPhone 6s. This is often referred to as a “logical” extraction or image. The device had an encrypted backup password. Without providing the encrypted backup password, we were able to get roughly 3,700 artifacts, mostly from the Media category in AXIOM Examine. With the password, we had roughly 44,000 artifacts. The Media category contained artifacts not accessible outside the encrypted backup such as media from apps whose data is protected by the encrypted backup. You can read this blog post for more on Encrypted Backups.
Often, we refer to the iOS extractions like mentioned above as an “iTunes style backup”. That’s because iTunes was installed on the user’s workstation to generate a backup for their use or iTunes was installed a forensic workstation for a forensic extraction. Apple has unique and well-defined management over user data by designing their own hardware, software and backup methods. So, we need some help from iTunes to get these extractions, which is depending on the backup functionality.
Unfortunately, having the device passcode or backup encryption password will not get the most comprehensive extraction from an iOS device. Apple’s data protection classes prevent some artifacts from being stored in a backup, even if it’s encrypted.
Obtaining a Full File System (FFS) Image
This is where a full file system (FFS) image can provide more artifacts to help with your examination. FFS images of iOS devices can be achieved by various tools and methods (e.g., GrayKey, which has direct integration with AXIOM). We will focus on the artifacts identified using Magnet AXIOM for both a logical image (AXIOM quick image) and FFS image of our same iPhone 6s. Our first notable difference in the size of the images. Our logical image is 5.17GB and the full file system image is 20.4GB. Perhaps the most impactful variance comes in the number of artifacts. On the left, you will see the comparison from the logical image and the full file system image on the right.
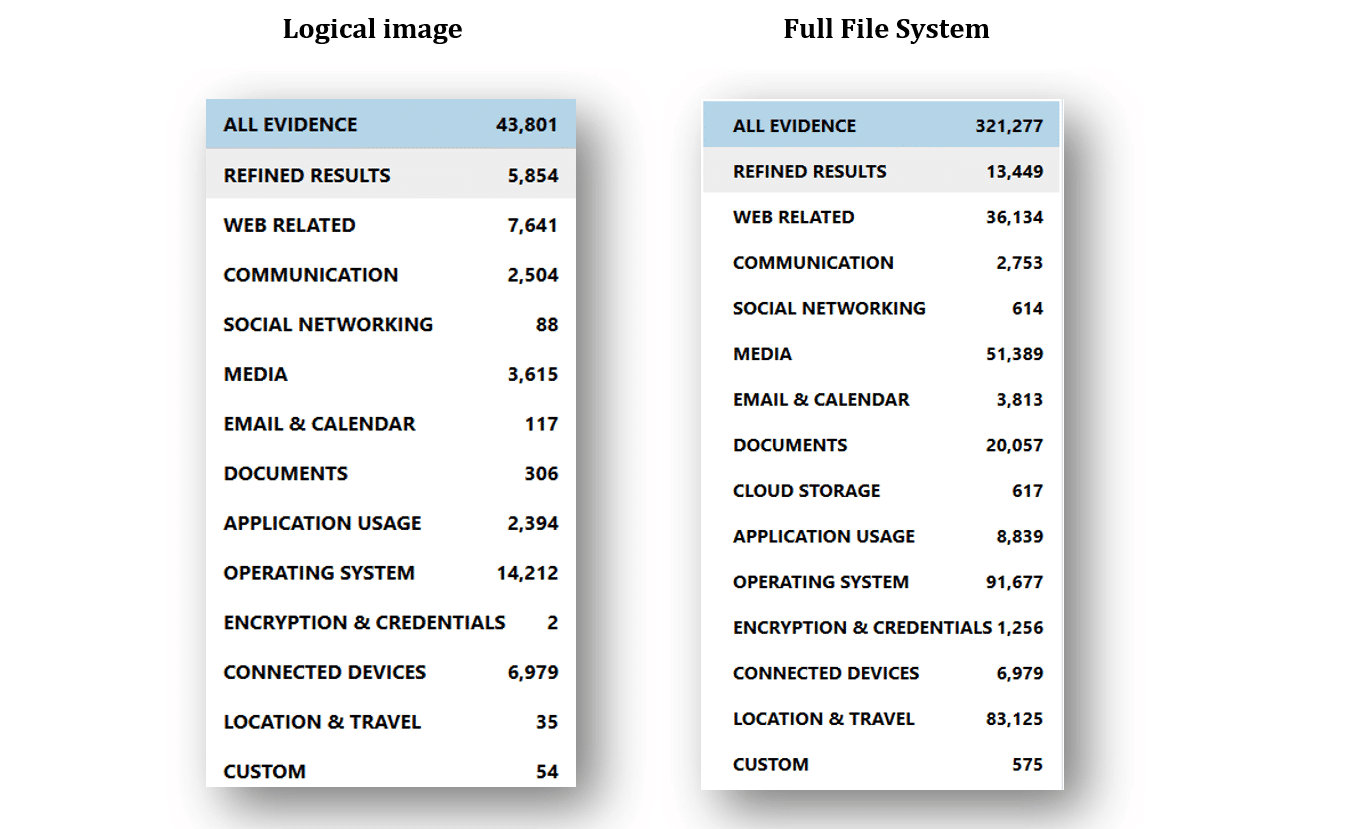
What’s in an FFS Image Vs. a Logical Image
Let’s look at a few items we get from a FFS images that aren’t in logical images.
A great category to begin reviewing is “Encryption & Credentials”. In our FFS image, we will find Apple Keychain data which may have passwords in plain text, tokens or keys that can be used to decrypt or access other data. The Artifact Reference within the Magnet AXIOM user guide can provide more information on using Keychain information to decrypt application data.
Our FFS image also provides us with artifacts from the KnowledgeC database. The KnowledgeC database stores user device interaction and helps to answer questions such as: was the device plugged in? What was the orientation of the device? Was the screen locked? Was music playing from Spotify or a video from YouTube? What application was in focus? When was Siri engaged?
Email, health and location data are included in the most protective data classes in the iOS, meaning we are very limited in what, if anything, we get from these categories in a logical image. Email on a FFS image may contain content such as To, From, Dates, Subject, Body and Header details as well as Attachments. A logical image may only get a few fragments from email or data from within third party email applications.
Also within an FFS image is vast amount of location data that is not in a logical image. Locations that have been cached for various apps and tracking may be available (how else will your Uber driver find you?), along with Parked Car Location and what Apple calls “Significant Locations”. Cell tower locations and wifi locations can also aid in the investigative process.
Using Magnet AXIOM to Build a Timeline
As with any type of evidence, the amount of artifacts can be overwhelming.
By building a Timeline within Magnet AXIOM, you can get a chronological view to help see a more comprehensive view of your case.
For example, using the Relative Time filter around a particular text message can help look before and after a text message was sent may indicate Siri was used for the action. Or, if a suspect has an alibi at a particular time, we may see device interaction such as the device being plugged in, if the device is locked, the camera being used or what application is in focus to help confirm or refute their claims.
Lastly, artifacts within FFS images often have a shelflife or expiration that varies per artifact. As such, it would be aventageous to collect and extract devices as soon as feasible.
Don’t hesitate to reach out at kim.bradley@magnetoforensics.com if you have any questions!