
Forensic analysis of LNK files
This is the third blog post in a series of five about recovering Business Applications & OS Artifacts for your digital forensics investigations.
What are LNK files?
LNK files are a relatively simple but valuable artifact for the forensics investigator. Shortcut files link to an application or file commonly found on a user’s desktop or throughout a system and end with an .LNK extension. LNK files can be created by the user or automatically by the Windows operating system. Each has its own value and meaning. Windows-created LNK files are generated when a user opens a local or remote file or document, giving investigators valuable information on a suspect’s activity.
Why are LNK files important to your digital forensics investigation?
LNK files are excellent artifacts for forensic investigators trying to find files that may no longer exist on the system they’re examining. The files might have been wiped or deleted, stored on a USB or network share, so although the file might no longer be there, the LNK files associated with the original file will still exist (and reveal valuable information as to what was executed on the system).
The key artifacts that need to be found when investigating LNK files
LNK files typically contain the following items of evidentiary value:
- The original path of the file
- MAC times of the original file; not only will a LNK file contain timestamps for the LNK file itself, it will also contain MAC times for the linked file within its metadata as well
- Information about the volume and system where the LNK file is stored. This will include volume name, serial number, NetBIOS name, and MAC address of the host where the linked file is stored
- Network details if the file was stored on a network share or remote computer
- File size of the linked file
Let’s take a look at an example:
From a Windows 11 workstation, the following lnk file was located. Here is the hex view of the lnk file:
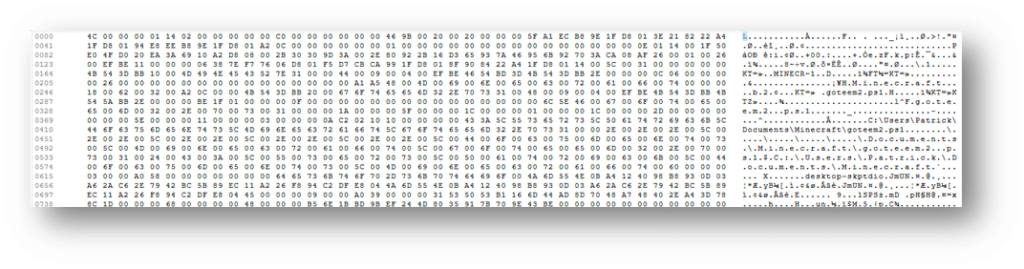
Making LNK file analysis easier with Magnet Axiom and Magnet Axiom Cyber
Although the above hex can be parsed manually, Axiom takes this data and cleans it up for the investigator, providing a wealth of information. This parsed data includes the linked path, computer and volume information where it was first run from (including the computer’s MAC address), and most importantly, timestamps around the LNK file and the original file. The ‘date-created’ MAC time for the LNK file will tell the investigator when the file was first opened, and the ‘date-modified’ time will identify when the user last opened the file. Additionally, inside the LNK file are timestamps related to the creation and modification dates of the original file.
We can see below that Axiom has taken the raw data above, sorted, and organized it for the investigator in a far easier format:
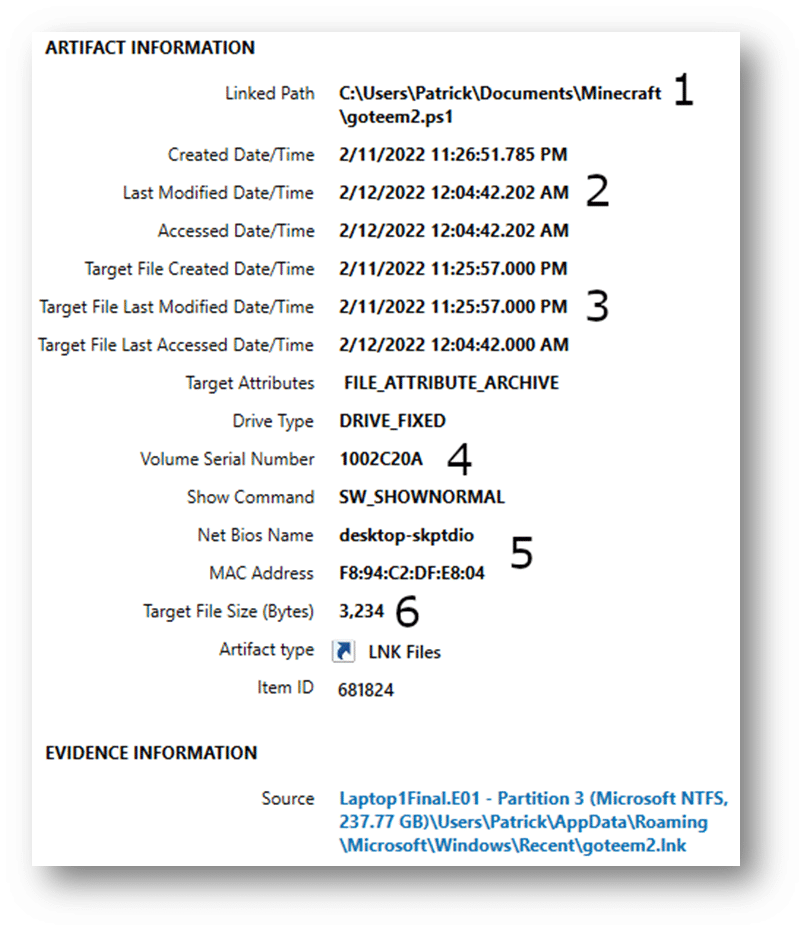
- Path of the file being linked to
- MAC times for the LNK file
- MAC times for the original file
- Volume serial number
- NetBIOS name and MAC address of source computer
- File size of the original file
By adding LNK artifacts to Axiom, we aim to simplify the recovery of this well-known artifact and improve the efficiency of your investigations by allowing you to find more types of evidence with one search and tool.
In conclusion, the analysis of LNK files is a crucial component in the realm of digital forensics. These files serve as valuable artifacts that can provide forensic investigators with critical insights into user activity, system behavior, and the presence of potential security breaches. By examining LNK files, investigators can reconstruct timelines, identify accessed or moved files, and uncover traces of malicious activity that may not be evident through other means. The detailed metadata within LNK files, such as file paths, access dates, and network share information, can significantly aid in piecing together complex digital investigations. As cyber threats continue to evolve, the ability to effectively analyze LNK files remains an indispensable skill for forensic professionals, ensuring a thorough and comprehensive understanding of digital environments and their associated activities.
Get Magnet Axiom today!
We continually improve Axiom to make it our most comprehensive digital forensic platform. When every second counts, it’s important that we do what we can to streamline the primary workflow of examiners.
If you’re already using Axiom, download the newest version of Axiom at the Customer Portal. To try Axiom for yourself, request a free trial today!
If your agency needs to perform remote collections, collect from cloud storage services, or Microsoft Office 365, check out what’s new in Axiom Cyber here.