
Remote Acquisition of Apple’s New M1-Based Endpoints with Magnet AXIOM Cyber
2020 brought many challenges to the InfoSec and DFIR community. Between many organizations transitioning to WFH and needing more robust VPN solutions for securing their network traffic along with the rising need for examiners to remotely acquire endpoints not currently on internal networks, the industry has stayed strong and met the needs of their organizations. On top of the other challenges faced, Apple unveiled their new M1 chip, our next forensic challenge.
In this blog we’ll discuss AXIOM Cyber’s ability to acquire from M1 based Mac endpoints.
If you haven’t tried AXIOM Cyber yet, request a free trial here.
15 years after Steve Jobs announced Apple would be migrating away from the use of PowerPC processors to Intel, Apple has once again made a huge transition in the processors their endpoints will use for years to come. Enter Apple Silicon and the M1, an ARM based processor developed in house by Apple which promises huge performance gains over intel processors.

The new ARM-based M1 chip, available currently in the MacBook Air, MacBook Pro 13”, and the Mac Mini line is touted as Apple’s highest performing chip ever. The M1 hosts an 8-core CPU, which is broken down to 4 performance cores and 4 efficiency cores which will aid with battery life among other things. Apple states the M1 is 2x faster CPU using only 25% of the power to do so1.
With new architectures comes new challenges, and as examiners we need to think about what software can run on the new M1 based Mac’s either natively or with the help of Rosetta 2, which helps applications not natively designed for macOS Big Sur and ARM processors run seamlessly. Just as important, is how we get access to these endpoints for investigations, which as anyone who has worked with Macs before knows, can in and of itself, be challenging.
With the new architecture and additional security features of the M1-based Macs and Big Sur investigators can’t currently boot from traditional Mac imaging solutions due to the limitations around 3rd party software on bootable macOS USB’s, which only leaves logical imaging from a live machine, if you have the machine present. For examiners needing to acquire Macs whether they are intel based T2 or the new Apple Silicon M1 chip, AXIOM Cyber is here to help. Using AXIOM Cyber we will create a custom agent that is then deployed to the endpoint under investigation. It’s important to note we support the new macOS Big Sur (11) and do not require System Integrity Protection (SIP) to be disabled for acquisition.
Unlike our Windows remote acquisition capabilities where users can select both logical files or the physical disk for acquisition, our macOS agent allows for only logical file collection. AXIOM Cyber leverages operating-system calls (vs bytes from a mounted volume) for the acquisition.
We’ve also added the ability to quickly acquire from pre-packaged targeted locations, removing the need to dig through the file system to find data that is needed routinely in your investigations. This could range from browser history to quarantine files, iOS backups, iCloud data, or the unified log. Examiners can also create their own targeted locations for future use as well.
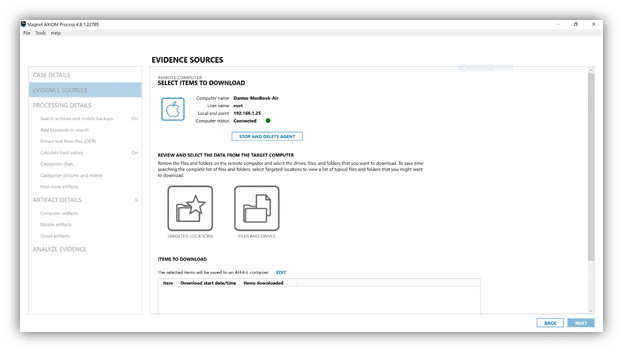
Deployment
Once the Mac agent is created in AXIOM Cyber, it’s time for deployment. In order for our agent to deploy we require Remote Login enabled. Remote Login can be found by navigating to:
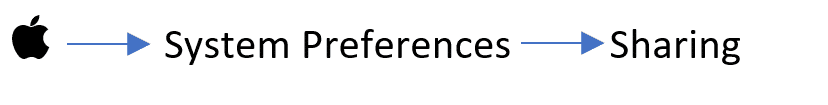
If an examiner is using a root user (different from admin user with sudo), they will need to enable SSH for root, but this isn’t recommended or feasible in most corporate environments. When Remote Login is activated in settings as discussed above, SSH will be enabled. For those who may need to deploy the AXIOM Cyber agent outside of the tool, check out this blog where we discuss deployment via command line.
AXIOM Cyber’s macOS remote acquisition deployment will attempt to run the agent with sudo if the supplied user credentials have permissions based on the sudoers file. If the user credentials have sudo permissions enabled AXIOM will display the user as root.
Once the agent “calls home” back to your instance of AXIOM Cyber and is connected, simply select the files you wish to collect. AXIOM Cyber gives you the option to collect and save the files in a .ZIP or AFF4-L formatted image. More information on our AFF4-L support can be found here.
As always, if you have any questions or have suggestions on what you’d like to see in AXIOM or AXIOM Cyber please don’t hesitate to reach out to me at trey.amick@magnetforensics.com