
Deploying AXIOM Cyber Mac Agents via Command Line
In Magnet AXIOM Cyber 4.0, we added the ability to quickly and covertly acquire evidence from Mac endpoints. While many customers rely on AXIOM Cyber for the deployment of the agent used for logically collecting files from endpoints under investigation, we understand the need for flexibility in how agents are deployed.
In this blog, we’ll review how to deploy an agent via command line from a Windows workstation to a Mac being investigated.
For more information on remote acquisition of Mac endpoints check out this article.
If you’re not already using AXIOM Cyber and would like to try it for yourself, request a trial today.
Why Use a Command Line Interface?
You may be wondering, if AXIOM Cyber makes it easy to deploy agents for remote acquisitions, why do I need to use a command line interface instead? Great question! We want to provide as much flexibility as possible for organizations when it comes to using our tools. Perhaps only IT or an End-Point Security Team has access to admin accounts and the authorization to utilize SSH capabilities. With the command line deployment approach, you can create and provide the agent to third-party teams, letting them deploy the agent while you then acquire and process the evidence.
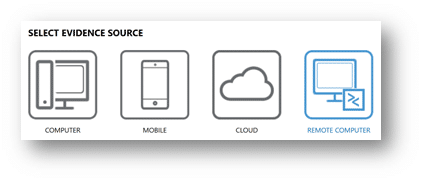
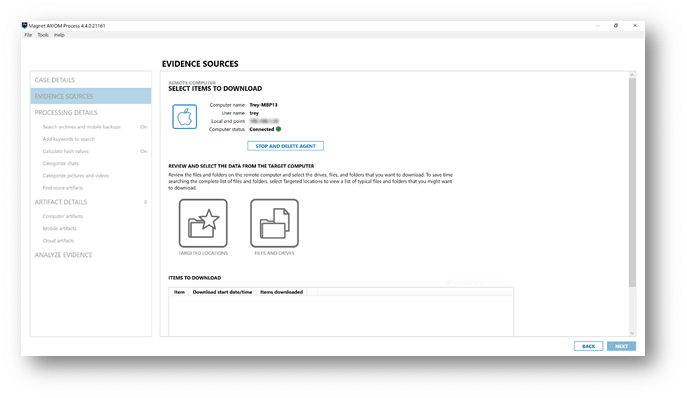
Once alerted that a Mac endpoint needs to be investigated, you’ll start by launching AXIOM Cyber Process and creating a new case. Now that you have a new casefile created, we’ll need to select your evidence source, which in this case will be REMOTE COMPUTER, as seen below.
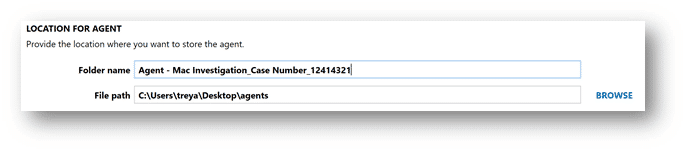
Next, we’ll create a new agent, making sure to select Mac as the operating system. In this exercise, I’m leaving the agent name as the default, Agent, however AXIOM Cyber gives examiners the flexibility to name the agent and include customized metadata as a part of the configuration process. Make sure to take note where you’re saving the agents created, as we’ll need to grab the binaries for the deployment. As you can see below, I have an Agent folder on my desktop setup as my default location to store agents created with AXIOM Cyber.
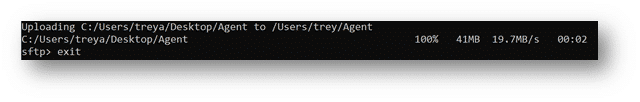
Now that you’ve created an agent, let’s deploy it using Command Prompt on Windows. In this example, I’ve simply placed the agent on my Desktop. It’s worth noting this agent was deployed to a T-2 based Mac with SIP enabled, running macOS Big Sur (Version 11 Beta). Also, keep in mind Remote Login needs to be enabled on the Mac you’re wishing to collect from. This can be enabled by navigating to:

- Launch Command Prompt
- cd Desktop (or to where the agent is located on your local system)
- dir (to confirm agent is listed)
- Type: sftp user@host or IP
- Enter Password
- Once connected:
- Type: put (drag the agent into CMD prompt) then hit enter
- Command Prompt should now show the agent being uploaded.
- Type: Exit sftp
At this point the agent has successfully been deployed to the Mac under investigation, but we still need to launch it.
- From Command Prompt, type: ssh user@host or
IP (can also try ssh user@host /path/to/agent directly. If that fails agent
may not be executable. See steps below to make agent executable and manually
launch)
- Enter password
- Type: ls -l command to confirm agent is listed and has RW and Execute privileges
- if the agent wouldn’t launch you’ll need to
promote its privileges
- Type: chmod 755 Agent
- Type: ls -l to confirm updated privileges
- Type: ./Agent
Once you run the last command the agent should successfully be launched and running covertly on the endpoint you’re investigating. At this point you’ll want to head back to AXIOM Cyber and select “Connect Agent” from the list of recently created agents as seen below.
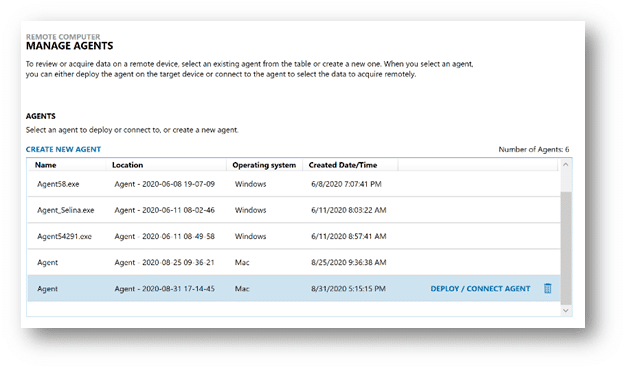
Once connected, simply select between Targeted Locations and/or Files and Drives to collect evidence needed in your investigation.
If you have any questions please don’t hesitate to reach out to either our superb Support team: Support@magnetforensics.com, myself: trey.amick@magnetforensics.com, or Dallas Jordan: dallas.jordan@magnetforensics.com.