Getting Started With Magnet RESPONSE
Magnet RESPONSE is an evidence collection and preservation tool, targeted towards incident response (IR) cases and the data that is relevant to those investigations. It’s designed to be portable (running from a USB drive), easy to use and fast, with minimal training required to operate the tool, while still targeting a comprehensive set of files and data relevant to IR investigations.
We developed this tool with the non-technical stakeholder in mind. Due to hybrid work environments, there might not be an incident response team nearby to collect data from physical endpoints. RESPONSE is easy to set up; with one click, a non-technical user can start a collection, and preserve critical IR-related evidence, in minutes.
Collecting IR-Related Data Using Magnet RESPONSE
Primarily designed to be run from external media, once downloaded from the Magnet Forensics website, the RESPONSE .zip archive includes the application file, release notes, and quick start guide in PDF format. Once these items are extracted, you have a ready-to-use volatile data collection application that is less than two megabytes in size.
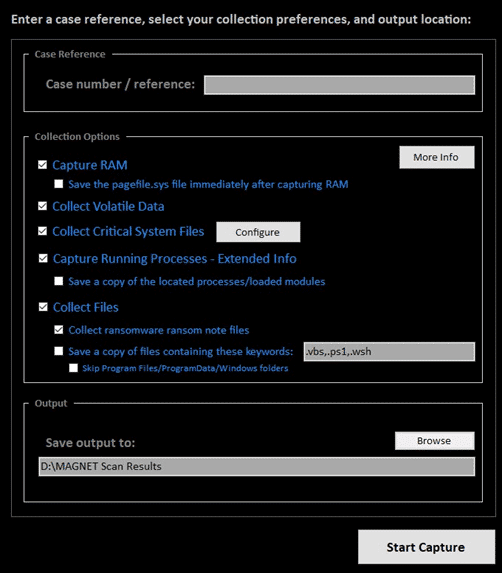
To conduct a RESPONSE capture, launch the tool and enter a case reference/number, select your capture options, and an output location. The output will be saved to a standard .zip file, and if RAM is selected for capture, it is saved separately to a .bin (raw dump) file.
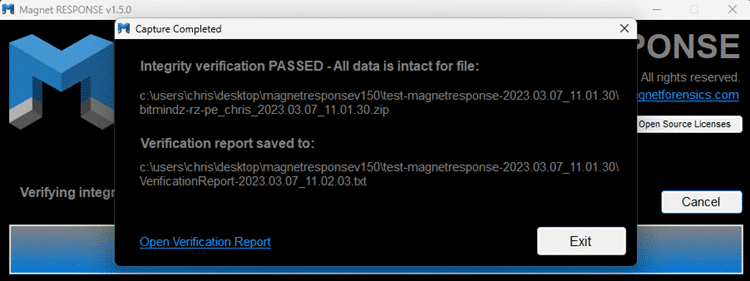
An embedded hash value is provided to verify the integrity of the data. This hash value is saved within the .zip file that can be used to verify that the .zip contents have not been altered or corrupted. A file within the .zip contains the hash value for the captured RAM if any verification needs to be done on that file.
Saved files & RAM can be processed and analyzed in a forensics tool like Magnet AXIOM and Magnet AXIOM Cyber. Simply add the .zip file as a Computer/Windows image, and the RAM as a Memory Image.
Verifying a Capture Package
To verify the .zip, simply drag and drop it on to the RESPONSE executable. Magnet RESPONSE will launch as normal and go directly into a verification process, providing a message at the end indicating if the verification was successful.
Data Collection Options
Configure a collection by selecting from a comprehensive set of options, such as:
- Capture RAM – If the user enables to the option to Capture RAM, that is saved separately as either a .dmp (Microsoft crash dump) or .BIN (raw dump) file, depending on which memory capture tool was used. Magnet RESPONSE defaults to using MAGNET DumpIt for physical memory acquisitions, but should that fail to complete, the tool will automatically run MAGNET RAM Capture as a fall-back measure.
- Capture pagefile.sys – Captures the pagefile.sys file, immediately after RAM is captured (if enabled).
- Collect Volatile Data – Saves the following items:
- Network connections
- Running processes (basic list)
- Logged-on users
- Scheduled tasks
- IP config info
- Firewall info
- Wi-Fi info
- Windows services
- Local users accounts
- Windows version details
Note: Data is saved to individual text files to enable quick review.
- Collect Critical System Files – Collects the following files/locations:
- Master File Table ($MFT)
- Registry Hives
- NTUSER.DAT files
- UsrClass.dat files
- Recent Link files
- Amcache data
- Jumplist files
- PowerShell history
- SRUM data
- Scheduled Tasks
- Windows Timeline data
- Windows Event Logs
- Prefetch files
- Firewall Logs
- TeamViewer Logs
- AnyDesk Logs
- LogMeIn Logs
- Recycle Bin
- Chrome Browser History
- Edge Browser History
- Firefox Browser History
- Capture Running Processes – Extended Info – This option collects more data about running processes (and loaded modules in memory), saving hash values and metadata from identified files which can be used to enable post-collection lookups/enrichment in another tool.
Note: If the option for Capture Running Processes – Extended Info is not checked, but “Volatile Data” is, a more basic list of running processes will still be captured.
- Sub-option: Save a copy of located processes/loaded modules – If this option is checked along with the Capture Running Processes – Extended Info option, copies of the located running processes/loaded modules will be saved to the output .zip file for analysis on another system.
- Collect Files Options
- The Collect Files section shown in Collection Options includes several items which can be useful in different types of investigations.
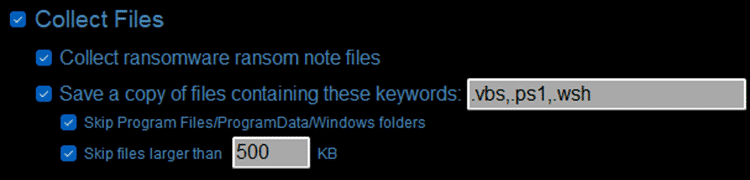
- Collect ransomware ransom note files – This option attempts to locate and save ransomware ransom note files based on file names/keywords known to be used by ransomware.
- Save a copy of files containing these keywords – This option attempts to locate and save copies of files based on user-specified keywords or file extensions
By default, RESPONSE will search for the script file extensions shown that are commonly used by malware. However, if a file named “collectkeywords.txt” is present in the same folder as the RESPONSE executable, it will instead be loaded, and the contents are leveraged as keywords for file collection. As with keyword lists in other Magnet Forensics products, keywords should be entered one per line in the collectkeywords.txt file.
Two further sub-options are available that can be enabled to streamline the search. The first is to direct RESPONSE to skip the Program Files/ProgramData/Windows folders to reduce the number of files collected. The second option enables users to specify a file size limit, this helps to maintain a super fast collection speed by bypassing large files such as videos.
Auto-Collect Options
These options can be helpful if you provide the tool to a non-technical user to simply capture the data and bring it back to you for processing and analysis:
- Option 1 – Capture Everything
- Rename the executable with the text “AutoCapture” (no quotes) anywhere in the filename. All options will be enabled, and the capture will start without the user’s prompting for configuration. The capture data will be saved to the folder the executable runs from.
- Option 2 – Minimal Capture
- Rename the executable with the text “AutoCaptureMinimal” (no quotes) anywhere in the filename. Only the “Volatile Data” and “Critical System Files” options will be enabled (no extended info saved for running processes), and the capture will start without prompting for any configuration from the user. The captured data will be saved to the folder the executable runs from.
After the files have been collected, they can be loaded into AXIOM or AXIOM Cyber and processed for a detailed examination of the recovered artifacts.
Are you already using RESPONSE for incident response cases? We’d love to hear how it’s helping you improve your forensic collections, please email us and share how you’re using this new free tool.
Download Magnet RESPONSE Now
Magnet RESPONSE is free for members of the forensics community. Visit our Free Tools page to download your copy of RESPONSE today!
Additional Resources
- Speed is essential when investigating a cyber incident. Learn how our DFIR solutions can help enhance your incident response playbooks in this blog post.
- Have you tried Magnet AXIOM Cyber yet? Get your free trial now and see how AXIOM Cyber helps you quickly uncover the truth by getting you the evidence you need to safeguard your business.