
Free Digital Forensics Tools Every Investigator Needs
Magnet Forensics offers a variety of free digital forensics tools designed to assist in many aspects of digital forensics and incident response (DFIR). Some of these have been helping examiners out for years and you may be familiar with them, others you may not even know about, so we’re collecting them here to give you an overview of what’s available.
I spent a few years on the Training Team here at Magnet Forensics and the topic of free tools would come up regularly during classes. I was always surprised to find that some of these incredible free digital forensics tools had gone unnoticed by other examiners. If you are already using Magnet AXIOM or AXIOM Cyber, you will be happy to know that many of these free tools generate output that can be passed as input to those platforms, really helping to streamline aspects of your investigations.
Where Are These Free Digital Forensics Tools
To paraphrase Jack Nicholson (the best Joker), where does he get those wonderful free digital forensics tools? Magnet Forensics hosts them on their website, and many are available right here on our Free Tools page. A few of the other tools require logging into your Magnet Forensics Support portal account to download them.
Different Free Digital Forensic Tools Categories
Looking at the full list of free digital forensics tools, it is easy to divide them into different categories based on their intended use, which is how I have listed them here. Depending on the type of investigations you are working on and your specific use case, you may find other applications for a specific tool.
Additionally, these free digital forensics tools have been used on everything from Windows Vista to Windows 11 and Server 2019, in virtualized environments, on single-user systems, and in enterprise environments. Some, like MAGNET RAM Capture, are extremely lightweight offering a command line option that aims for the smallest footprint when capturing volatile memory. Most of them, if appropriate, run perfectly fine from external media and without installing on your target system and will also run inside of a virtual machine—more on that in a bit.
Triage
In the DFIR world, triagecan mean a few different things depending on context. For some, that means reminiscing about the days of walking around with a freshly burned Linux boot CD and looking for a paper clip to straighten out so you could power on a suspect’s computer. For others, it can mean undertaking the unenviable task of deciding which endpoints in a massive organization need further analysis. For any version of triageyou find yourself faced with, these three tools are some of my go-to options.
RAM Capture
MAGNET RAM Capture is probably one of the most well-known free tools Magnet Forensics offers. As its name suggests, you can utilize MAGNET RAM Capture to acquire the physical memory of a Windows computer. When launching the GUI instance of MAGNET RAM Capture, you will be presented with information detailing how much physical memory will be captured, a text entry field for the memory capture storage location, and an option to segment the memory capture.
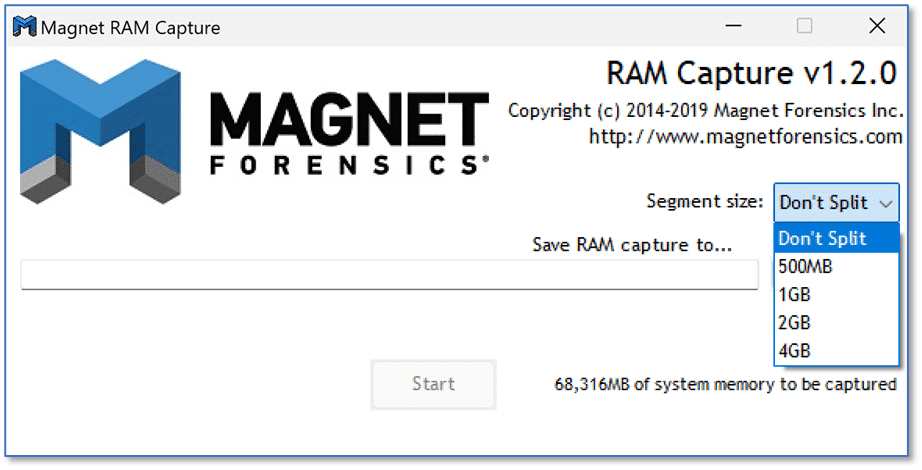
This tool runs perfectly fine from just about any external media you might want to use, making it easy to capture RAM from running Windows computers and storing it on an attached USB storage device. In the context of capturing RAM from a running Windows computer, you are probably concerned about the footprint you are leaving on that system. We all know that by running any memory capture tool, we are making changes to a portion of the system’s available random access memory. There is an option to run MAGNET RAM Capture from the command line without the GUI display, ensuring the smallest footprint. Running the executable with the /? Or /help option will give a breakdown of the available choices when using the CLI instance of MAGNET RAM Capture.
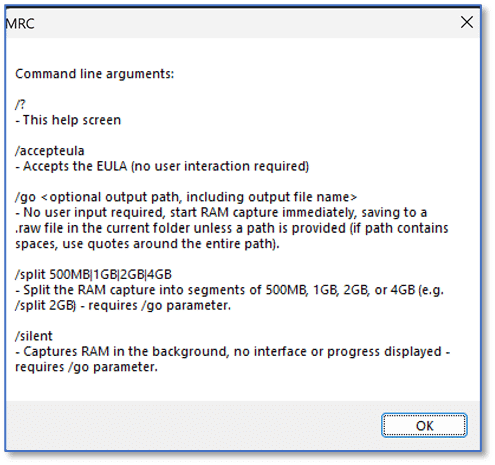
If you have copied MAGNET RAM Capture to a USB flash drive and have that connected to a target computer, launch the program with the following options:
MRVv120.exe /accepteula /go /silent
will launch the program without displaying the end user license agreement screen (/accepteula), causing the RAM capture to be stored in the location you are running MAGNET RAM Capture from (/go) [note that you can pass an alternate output path as an argument], and run as a background process with no user interface or progress bar displayed on the screen (/silent). Collectively, these options make for a very compact instance of a RAM capture utility that stores an unsegmented memory dump in the location you run the tool from—it even works seamlessly as part of script.
Another use case for MAGNET RAM Capture that may be a little outside of the box, is running it within a virtual machine. If you find yourself working with suspected malware and you would like to launch that suspicious executable within a controlled environment to observe its behavior, you can place a copy of MAGNET RAM Capture inside the virtual environment and run the program from within the virtual machine just as you would on a physical computer. You could also gather the virtual machine memory files via the standard process for whichever hypervisor you are using, this just gives you another option.
Process Capture
Ever notice how random physical memory is? MAGNET Process Capture is an excellent choice for extracting the entire logical pool of physical memory allocated to a running process on a Windows computer. This may give more context around what a specific process is doing on a computer and there are some additional options within the program that can support your investigative needs.
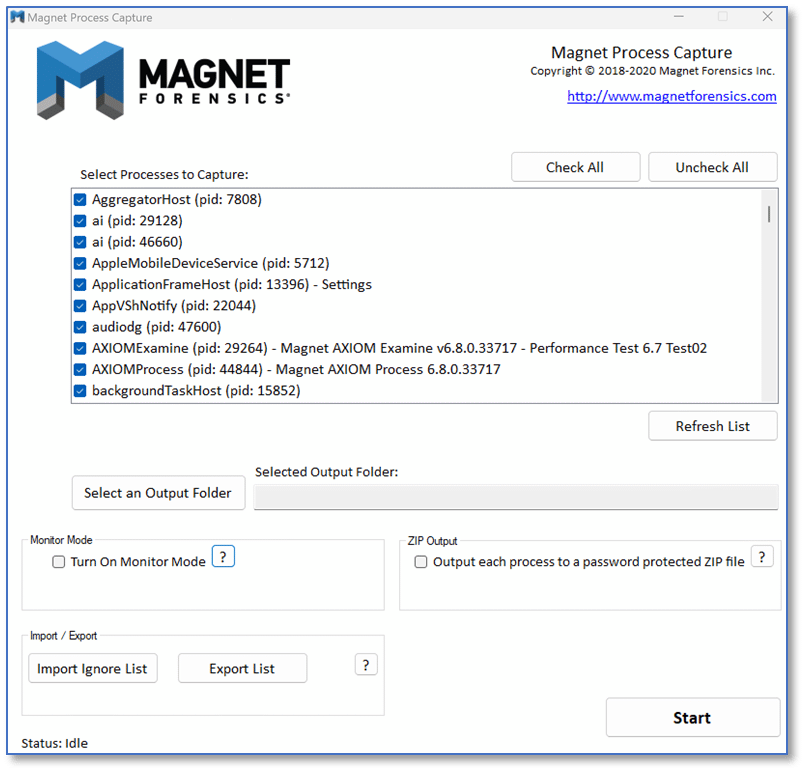
When first launching the program, you are presented with a list of all running processes on the system. You can select which process(es) you want to export and designate an output folder. There is an option to export process memory to a password-protected ZIP file, which is very useful when dealing with potential malware. Otherwise, if your antivirus software is up to par, it might just quarantine that item when trying to export it! Monitor mode is useful when leveraging MAGNET Process Capture in dynamic analysis of malware. Like with MAGNET RAM Capture, this could be run in a locally hosted sandbox environment before launching the suspect binary. Finally, there are options to export a list of processes or import an ignore list to perform whitelisting and blacklisting of items when triaging multiple systems.
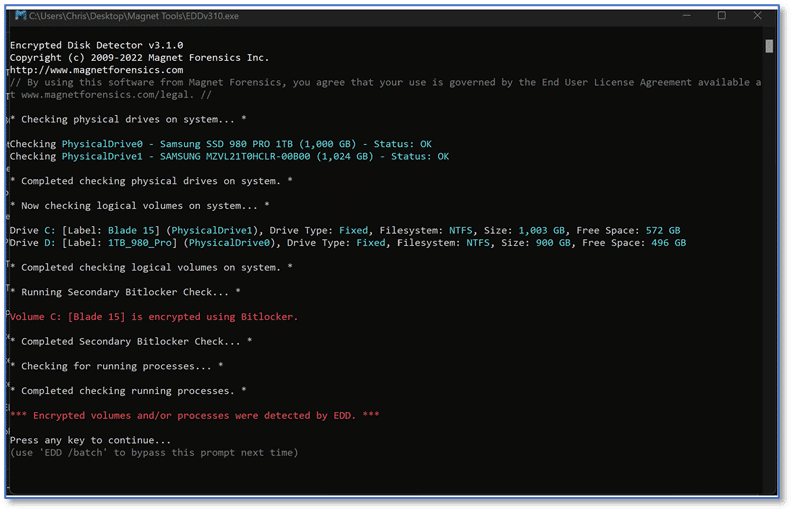
Encrypted Disk Detector
MAGNET Encrypted Disk Detector is a command line tool that checks local drives on a system for indicators of encrypted volumes, including:
- TrueCrypt
- PGP
- Bitlocker
And several other popular full-disk encryption solutions. This is a beneficial option when examining systems in an environment you may be unfamiliar with. In theory, by the time you run this tool you have already utilized MAGNET RAM Capture, so using something like Passware with that memory capture would likely provide a method to access those encrypted volumes. But why takes chances? If you can identify a full-volume encrypted disk on the system that is powered on and accessible using Encrypted Disk Detector, you just may decide to live image that device before powering down the system.
Acquisition Tools
The next group of tools is focused on acquisition, whether you need to image an internal drive, USB device, or acquire an unlocked mobile device, there are options here for you.
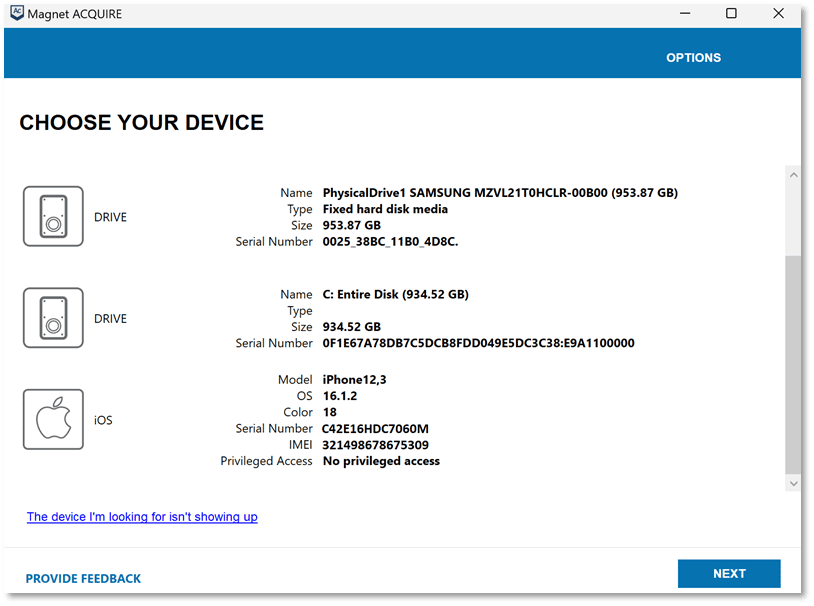
Magnet ACQUIRE
Magnet ACQUIRE lets you quickly acquire images of a variety of storage media and can be run from external storage devices. Using the appropriate write-blocker allows you to make forensically sound images of different media types. Magnet ACQUIRE will also perform acquisitions from iOS and Android devices, just note that you will need the device passcode for these. Magnet ACQUIRE cannot circumvent device security protections but is a great option for known-passcode devices or consent cases with cooperating individuals when away from the lab. You can also run multiple instances of Magnet ACQUIRE—on one computer or multiple machines—making the process even more efficient when you find yourself out in the field and need to capture multiple forensic images.
Magnet SHIELD
Magnet SHIELD is a free tool designed to empower frontline law enforcement officers with the ability to collect and report on digital evidence. Magnet SHIELD is intended to maintain privacy and build trust by giving cooperating individuals the ability to limit a collection to specific items that are shared with law enforcement, potentially alleviating concerns over acquiring other sensitive information which may not be within the scope of the investigation.
As an example, a witness with relevant photos or videos on their mobile device that is willing to provide that information at the time of the incident could do so. This means they would not be required to bring their mobile device to a digital forensics lab for acquisition and possibly surrender their device until that relevant data can be acquired. Magnet SHIELD provides the ability to include your organization’s consent to search forms and controls that make it easy to select only specific media items or those from a certain time frame.
Web Page Saver
The MAGNET Web Page Saver can be used to capture the content of a web page as it exists at a point in time. This is a great resource to have during the investigative process as web page content can change over time. The tool offers both automatic and manual capturing and users can import a list of URLs when multiple pages need to be captured, useful when generating a report of URLs of interest from an AXIOM case.
Additionally, a log is created showing the start and completion of the web page capture, and hashing is performed on the downloaded HTML content if that option is enabled. This provides not only the ability to capture web page data that is relevant to an investigation but also a method for demonstrating web content has not been altered after download.
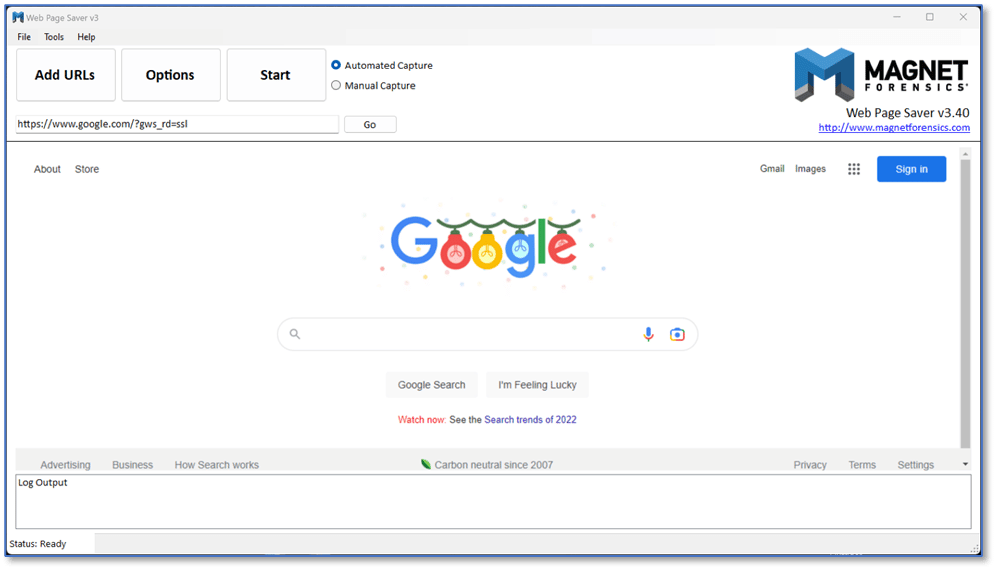
The Web Page Saver is using an embedded Chromium browser and includes options for a few output formats, including an SQLite option designed for importing the saved webpage data into an AXIOM case. There’s even a portable version of the Web Page Saver that can be run without installation.
MAGNET Apple Warrant Return Assistant
The MAGNET Apple Warrant Return Assistant automates the process for acquiring and formatting data produced in response to Apple search warrant returns for law enforcement. This tool was created in response to difficulties with downloading and reviewing the production data after changes were made to the return format. The Apple warrant return will be named similar to:
2021123123_production_20211232006.zip.gpg
Select or drop the .zip.gpg file onto the MAGNET Apple Warrant Return Assistant, provide the password provided by Apple, and specify an output location.
Once the package has been decrypted, a file named Evidence.zip will be created in the specified output directory, which can be loaded as an evidence item in AXIOM Process through the typical Apple warrant return workflow.
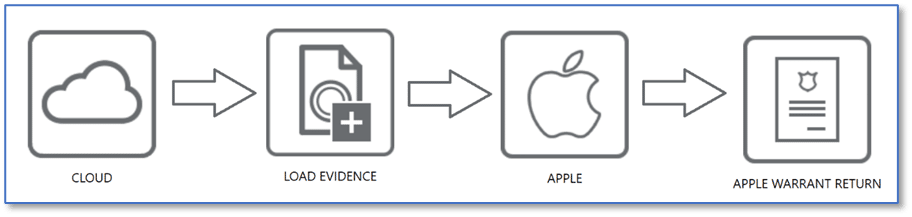
A step-by-step guide for using the MAGNET Apple Warrant Return Assistant and troubleshooting options can be found here.
Magnet RESPONSE
In an incident response investigation, it’s a race against time to quickly collect and preserve data from local endpoints before it is potentially modified or lost. Magnet RESPONSE lets investigators and non-technical users easily collect and preserve critical data relevant to incident response investigations from local endpoints using a pre-set collection profile to quickly target a comprehensive set of files and data relevant to incident response investigations, including RAM.
We developed this tool with the non-technical stakeholder in mind. Due to hybrid work environments, there might not be an incident response team nearby to collect data from physical endpoints. RESPONSE is easy to set up; with one click, a non-technical user can start a collection, and preserve critical IR-related evidence, in minutes.
To learn more about Magnet RESPONSE, check out our how-to blog and video to see it in action.

MAGNET DumpIt
Memory analysis is an essential component of incident response and network forensics. Various tools can be used to capture and analyze memory dumps, whether that be full memory dumps or crash dumps (with crash dumps providing you with additional information for your investigation.)
MAGNET DumpIt for Windows and MAGNET DumpIt for Linux are fast memory acquisition tools for Windows (x86, x64, ARM64) and Linux machines that generate full memory crash dumps. DumpIt for Windows runs in kernel mode, and the dumps can be analyzed by the Comae Platform and tools supporting Microsoft format, such as Microsoft WinDbg. Additionally, DumpIt comes with a PowerShell interface that is documented on the Comae Knowledge Base.
Additionally, DumpIt for Linux is written in Rust and this version leverages the existence of /proc/kcore to create memory dumps and generate an ELF Core Dump file to avoid creating a new format. DumpIt can be analyzed with gdb, crash and drgn and additionally, it has a compressed version as a zst archive which is a fast streaming compression algorithm, making it easier to acquire large memory images. In archive mode, DumpIt also has the ability to collect more files from /proc/.
Analysis Tools
The final two tools for this roundup are commonly used during the analysis phase of an investigation. After all your evidence has been added to a case, thoroughly parsed and carved for artifacts using AXIOM Process, keyword lists have been checked, and hash sets used to include and exclude items, you then begin to work your way through it all in effort to find the truth, and you run straight into an encrypted file or unsupported third-party application. So now what?
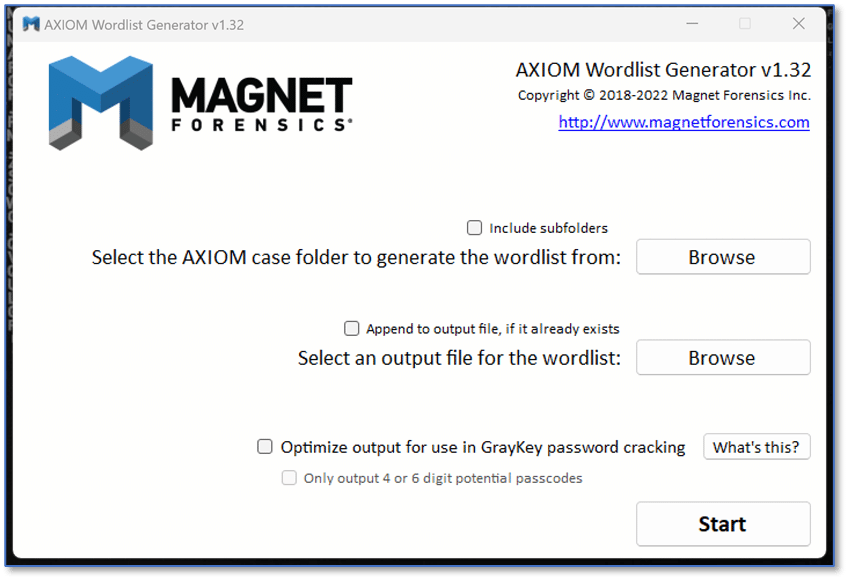
AXIOM Wordlist Generator
The AXIOM Wordlist Generator is a free tool that can be used with both MAGNET AXIOM and AXIOM Cyber to create custom word lists of all the unencrypted content available in a case. This word list can then be used with dedicated password-breaking software for dictionary-based attacks. As the use of encryption continues to become more commonplace, the likelihood of encountering encrypted containers will only increase. Even when encountering an encrypted device or file during an investigation, there are likely other sources of data for that target of investigation which are not encrypted.
For example, we could use the MAGNET Web Page Saver to acquire the content of any social media pages or other open-source intelligence that can be located. Other devices may be available, such as USB flash drives or cloud storage, which contain unencrypted data. Any device which contains information your target of investigation has interacted with that contains unencrypted data, can be processed in an AXIOM case specifically to create a custom dictionary for use in defeating the passwords the user may have implemented on encrypted containers.
Humans are such creatures of habit, and we have all probably experienced this on a case, or maybe even do it ourselves. There just might be something in that unencrypted data which has been repurposed as a password by your user—pet’s name, favorite sports team, or school mascot. So many things commonly get shared on social media.
MAGNET Custom Artifact Generator
Finally, the MAGNET Custom Artifact Generator should be in every digital forensic examiner’s arsenal for leveraging Magnet AXIOM and AXIOM Cyber’s ability to support the unsupported. There are a few common methods for developing custom artifacts to use within AXIOM such as the Dynamic App Finder or the Artifact Exchange. Another method is using a standalone free tool—the MAGNET Custom Artifact Generator (MCAG).
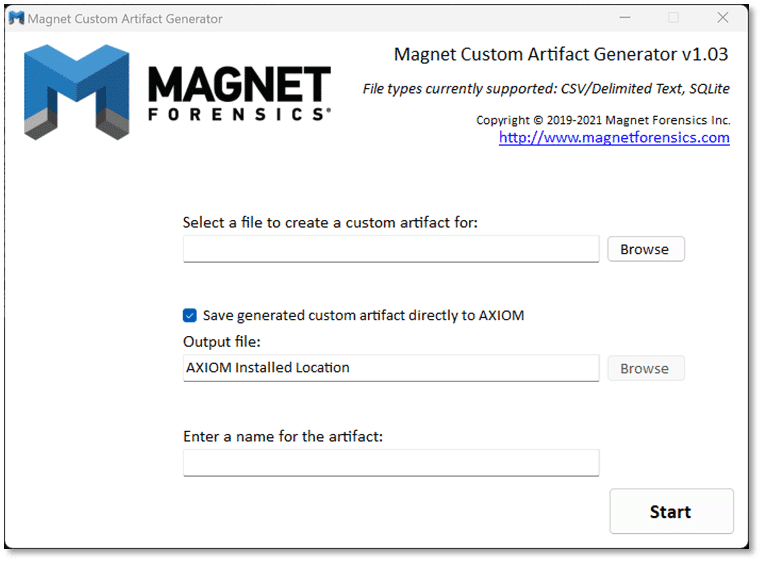
The MAGNET Custom Artifact Generator will accept delimited text or SQLite database files as input, then provide you with a preview of the content to map how the content is interpreted, including adjustments for many different timestamp conventions.
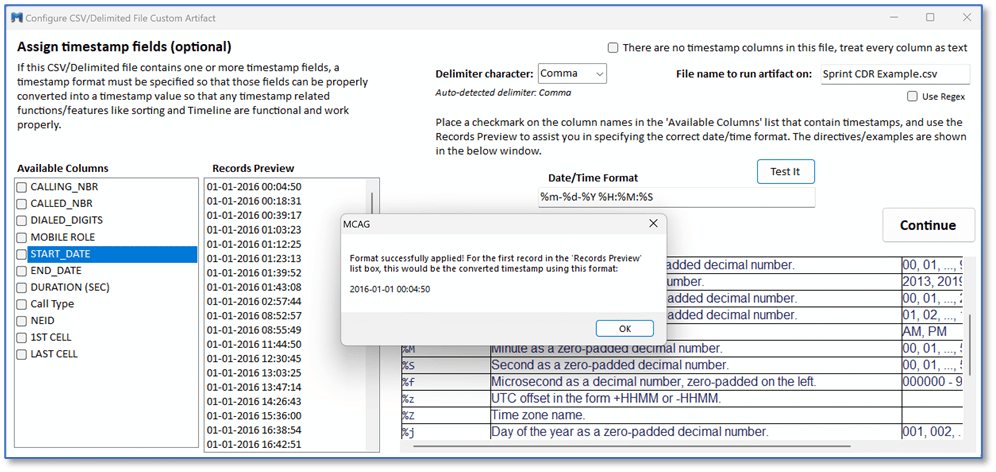
This allows examiners to accommodate delimited text records with things like regional differences in date format, 12/24-hour clock, and leading zeros in both dates and times. A Python-based custom artifact is generated that can then be added to AXIOM Process for use in parsing the content of the source file and its associated data is included in your case data for review in AXIOM Examine.
Many open-source digital forensic tools, logging solutions, and other applications provide an option to generate output in a comma-separated value file; the ability to quickly take the output from a variety of external sources and create custom artifacts for that data can be hugely beneficial. These data sources can then be included in an AXIOM case for analysis alongside the other items of relevance. This may provide context around artifacts that may be missed when looking at the data sources individually and also provides the option to add tags and comments associated with these items in your AXIOM Case. For additional information on the MAGNET Custom Artifact Generator, check out this post.
MAGNET Hash Sets Manager
The Hash Sets Manager offers you a central database that allows you to automatically manage hash set distribution to instances of Magnet AXIOM or AXIOM Cyber in your lab, even if it’s offline.
Conclusion
Hopefully, this overview of free digital forensic tools from Magnet Forensics is useful and you make your way over to our Free Tools page to check them out. If you have another use case or success story for any of the tools mentioned here, let us know. If you are a Magnet Idea Lab member, don’t be surprised to see some of the great things there making it out to the free tools page in the future.