
Digital Forensics Tools: The Ultimate Guide (2022)
Digital forensics tools have improved a lot in the past several years. With these advances, the digital forensics community now has many tool options for each phase of an investigation.
In fact, there can be a lot of options to keep track of.
That’s why we wanted to bring together the ultimate guide to DFIR tools—highlighting options available to examiners and when the best time to use them can be.
The advancements in digital forensic tools over the years have largely been driven by two things to meet evolving investigation needs: competition between more forensic software developers, and the maturation of the digital forensics open source and research communities.
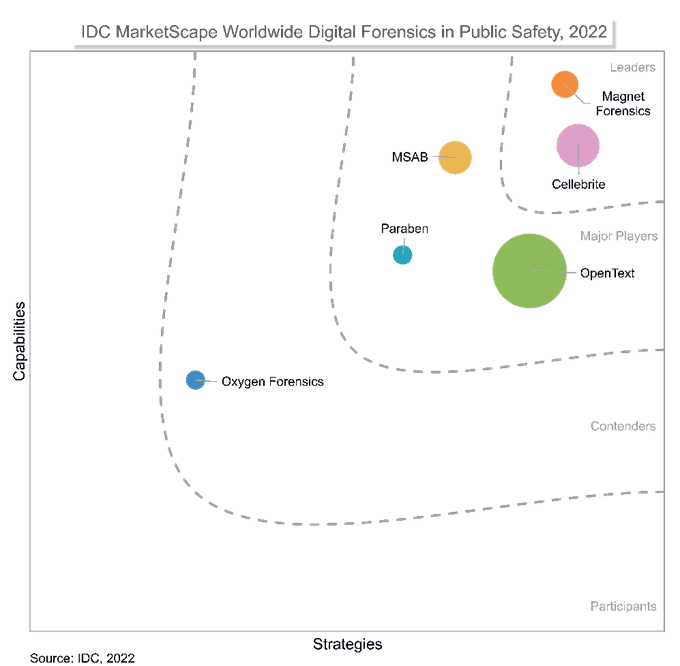
When it comes to the rise in competition between software providers, IDC has created a few in-depth reports comparing digital forensic tools for both private sector cyber security professionals and public sector digital investigators. Their recent MarketScape report found Magnet Forensics to have the highest capabilities of any digital forensic tools.
As for the maturation of the digital forensics research community, conferences like the Digital Forensics Research Workshop, the Open Source Digital Forensics Conference, and the Magnet Summit have been great opportunities for the community to get together and share knowledge and pain points. Companies like Magnet Forensics support these communities with resources and data sets, and provide an easy way for the community to capture, re-use, and share new artifact knowledge. Instead of gatekeeping, software companies working with the digital forensics community have led to rapid advancement in all types of digital forensic tools. Whether closed or open-source, free or paid, we’re bringing you a comprehensive list of digital forensic tools to help you kit out a digital forensic laboratory of any size.
This guide will focus on the tools you need to build a functioning general-purpose laboratory in either the public or private sector.
Digital Forensics Tools
Typically, a digital forensics laboratory will have several digital forensics tools that do the same task. For example, several overlapping tools allow the laboratory to validate investigation results (see Josh Brunty’s guide & SWGDE validation guidelines).
Whatever tooling you choose, ensure that you can get the same results using different methods. If you can’t, you must be able to explain why you can’t. Validation may mean manual parsing, conducting research, and reaching out to the forensics community.
When choosing digital forensics tools for your toolkit, think about each part of your investigation workflow and the tasks that normally need to be completed. Comprehensive digital investigation toolkits support the most common investigation tasks. These toolkits can often include third-party or user-created artifacts or modules. Custom artifacts let a lab quickly develop parsers for newly observed sources of evidence, regardless of the underlying software tool. It’s worth learning how to write custom artifacts for your preferred toolkits.
Free, open-source forensics software tools are excellent for validating results. But outfitting an entire lab with free software can lead to a patchwork of tools that don’t always work together. Sometimes, this can make for complex and inefficient workflows and reduce your time to evidence. It’s recommended that a professional lab have at least one fully comprehensive software solution, like the Magnet Digital Investigation Suite, to work quickly through cases with a minimum of downtime. Using tools that are well-recognized by courts will also save time, and smooth testimony at trial.
The following digital forensic tool lists are categorized using the first Digital Forensic Research Workshop investigative process for digital forensic science. Although proposed in 2001, the procedural concept is holding up surprisingly well. Let’s look at digital forensic tools and where they fit in identification, preservation, collection, examination, and analysis.
Identification
This is probably the most challenging part of any investigation. Before we can respond to an incident, we must detect it. Reporting could come from victims opening a case, a financial audit, or an admin checking their logs.
In criminal investigations, cases are typically reported to law enforcement. For private organizations, however, incident detection is critical. Passive measures like honeypots and canary tokens can greatly assist in alerting an organization to a compromise, while a tool like Magnet AXIOM Cyber, help with threat-hunting Windows event log analysis and incident response tasks.
Increasingly, users identify security incidents from threatening messages on the screen. Ransomware encrypts user files and demands payment for the decryption key. If you or your organization have been a victim of ransomware, find information and tools from Magnet AXIOM Cyber. Continue with your incident response plan and make copies of all data. To learn more about ransomware, see this excellent talk by Cindy Murphy.
Tools to assist in incident identification are either used pre- or post-incident. Pre-incident monitoring often results in more data and higher fidelity. Post-incident analysis requires much more challenging event reconstruction, often with limited data. Corporate environments have control of their systems and may enable pre-incident monitoring with additional logging and detection systems. Law Enforcement, however, almost always deals with post-incident default (or disabled) logging and anti-forensics.
Magnet AXIOM Cyber is the industry leader in both pre-incident monitoring and post-incident acquisition. Allows you to recover deleted data and investigate digital evidence from mobile, computer, cloud, and vehicle sources all in one case file with powerful analytics.
Preservation
Unfortunately, an incident has been identified and you now need to create a case, start documentation, and preserve any related data.
Case Management, Documentation, and Reporting
Most comprehensive digital investigation toolkits require creating a “case” in the software before adding exhibits. Case management within your primary analysis tool may be possible. However, consider overall lab management and collaboration. An organization-wide case management system will provide better visibility and coordination.
Regardless of where case management tools are placed, ensure your investigators can easily document their processes and are supported in writing comprehensive reports. This support implies access to a knowledge base of commonly used legislation, definitions, references, and procedures.
Requirements for case management, documentation, and reporting have advanced beyond an MS Word document. Here are tools to assist in the quality and security of investigation communications.
Magnet ATLAS is the gold standard tool here; improve efficiency and break down silos by enabling stakeholders agency-wide to manage, collaborate, analyze, and report on all aspects of your digital investigations.
Help first responders collect evidence from witnesses on-scene without asking them to give up their device with Magnet SHIELD.
Digital Forensic Imaging
Forensic imaging is both common and important in digital forensic investigations. But imaging is not easy. Resources like Practical Forensic Imaging are great for understanding the imaging process and challenges. Hardware and software can help make the imaging process easier, but validation still remains difficult.
Forensic Hardware Write Blocker and Disk Imagers
We’ve talked before about what to look for in a write blocker. With any hardware write blocker, it is crucial to have a standard testing methodology that your local court accepts and test your hardware regularly.
Hardware write-blockers are highly reliable devices and typically only fail when misconfigured. Some write blockers allow you to disable write-block functions and use the device as a read/write hardware bridge. Be sure to include usage training and testing when adding hardware write blockers to your toolkit.
Most Linux-based forensic operating systems include software (kernel-level) write-blocking. There are several commercial write blockers for Windows, but they tend to be more expensive than hardware write blockers. If you choose a software write-blocker, ensure you have a testing and validation procedure in place.
Disk Acquisition Software
Hardware and software write blockers need to be paired with imaging software. Hardware disk imagers have disk imaging software built-in; some external write blocker devices do not. Correct imaging is critical in any investigation, and the community is lucky to have such solid tools available for free.
Magnet ACQUIRE is the best tool for physical and logical disk imaging as well as mobile device imaging. It allows investigators to quickly and easily acquire forensic images of any iOS or Android device, hard drive, and removable media. Best of all it is completely free.
With disk acquisition, be aware of how the acquisition software treats bad clusters. For example, some software may write 0’s where disk read fails. Others may skip and not write anything to the image. Imaging error response can lead to two different images from the same failing disk. Configure your imaging software to respond to errors according to your lab’s SOP. Unfortunately, imaging software often does not allow error configurations and may not document their read failure procedure. In that case, you will need to test responses from different software and choose those that fit your lab the best.
RAM Acquisition Software
Like disk imaging, laboratories should acquire RAM acquisitions from case-related systems. Random Access Memory (RAM) contains information about the system and user activities since the last time the computer was shut down. This might include information that will never be written to disk. As such, it can be a valuable source of evidence for investigators.
RAM is volatile, meaning that it changes quickly. If a computer or device is shut down, all data in RAM is cleared and cannot easily be recovered. First-responders need the tools and training to collect a RAM image from a live environment. Live Data Forensics is not easy and should only be done by those competent to do so.
Many tools described in incident response can remotely collect a RAM image. Magnet RAM Capture, an easy-to-use, full-featured RAM acquisition tool, is meant to run directly on a running target system. Usually, tools are run from a prepared live data forensic toolkit on a USB stick or external storage medium. Remember that you will need an external storage location to save the memory dump.
Remember that RAM acquisition is complicated. You will need to load the tool into memory to acquire memory. As forensic examiners, we want to reduce the size of forensic tools in memory, so we don’t overwrite valuable evidence. Also, if the system is on, the RAM contents are changing. Imaging the same RAM twice will never result in the same image (and hash value). Hash the RAM image after the acquisition, and that hash becomes your ground truth.
Mobile Acquisition Software Digital Forensics Tools
Just like computer forensics, mobile forensics is split into acquisition and analysis. Recently, more analysis toolkits include processing data from mobile devices. Acquisition, however, remains a huge challenge. Newer mobile devices are often secure, meaning that expensive software vulnerabilities are needed to acquire data from the device. Differences in geographic location also somewhat dictate device support.
Generally speaking, older devices often have publicly-released vulnerabilities and utilities to bypass disk protection. Commercial tools are more expensive, but the interface and resources are user-friendly. Commercial tools also (usually) include non-publicly released exploits for newer devices. A laboratory using commercial tools can often acquire most of the newer devices. Users can also request support and additional service for devices that are not yet supported.
Magnet ACQUIRE allows mobile device acquisition for both iOS and Android.
Shout out to H-11 Digital Forensics and Rusolut for their chip-off kits and adapters. Most digital forensic laboratories do not have chip-off capabilities. As embedded devices become more popular, the need for chip-off will likely increase.
Collection / Examination / Analysis Digital Forensics Tools
Collection, examination, and analysis are theoretically separate concepts in the DFRWS process model, but multi-function digital forensics tools tend to cover some aspects of each. Multi-function tools help an investigator understand the data and its relation to the investigation question. From there, we tend to dig deeper into specific artifacts or even pivot to other more specialized tools for analysis.
We have our forensically-sound acquisitions of all case-related devices. Most full-featured digital forensic tools will ask to create a case in the tool’s management system. All exhibits and data sources are typically added under a single case. Grouping exhibits by case keeps everything together, but tools like Magnet AXIOM and Magnet AXIOM Cyber can find similarities between data sources such as files, usernames, phone numbers, etc.
The following tools are the gold standard investigation tools used worldwide:
- Magnet AXIOM — The industry standard: it lets you recover data from smartphones, computers, and the cloud and includes advanced analytics and reporting tools to help find case-related data faster.
- Magnet AXIOM Cyber — Purpose-built for private sector acquisitions with covert remote collection and support for enterprise cloud apps and services.
Mobile Analysis Software
We talked about mobile acquisition in a separate section because acquisition is a hard problem by itself. If you can get a good acquisition, congratulations! Now you need to deal with odd and complex data structures and rapid mobile application development.
Some of the full-featured tools listed previously have built-in mobile data analysis capability. Sometimes integration for mobile analysis feels like an add-on rather than the main investigation point. That’s useful for basic searching and analysis, but it’s quite common to need more in-depth functionality. The following tools appear to put mobile device data analysis first, including the challenges that come with it.
- Magnet AXIOM — yes, we’ve listed this before, but AXIOM is fully-integrated with GrayKey, and processing mobile device data feels like a first-class workflow instead of an add-on. Using AXIOM also lets you take advantage of Magnet custom artifacts for applications and data structures that are not supported.
- Magnet AXIOM Cyber — data reduction with keywords, hash lists, and advanced picture and video analysis.
When looking for a mobile analysis tool, consider whether the tool can parse common as well as trending data structures, an ability to customize or get support for case-specific data structures, and how easily (and comprehensively) the tool allows you to search and visualize the data. With mobile data analysis, you’re looking for updates more often than with computer analysis.
eDiscovery
eDiscovery solutions focus more on litigation and discovery workflows. They have feature sets that are often useful for any digital forensic investigation. It is common to see eDiscovery software used with comprehensive toolkits described above. The scope of eDiscovery can vary, and the tools required will as well. We’ve talked about the anatomy of an eDiscovery investigation before. You’ll need a tool that helps with data collection, reduction, and review.
Magnet AXIOM Cyber allows for covert remote device acquisition, data reduction with keywords, hash lists, and advanced picture and video analysis. After data reduction, AXIOM Cyber produces a load file for eDiscovery review platforms.
Modern eDiscovery tools are very powerful and tend to prefer cloud-based systems. Cloud-based systems make processing much faster and allow for advanced automation and machine learning. Each tool will work great for standard workflows. Which one works best for you will depend on the types of data you tend to work with and your goals. Almost all eDiscovery tools are attempting to use machine learning for classification. The best model for you will be the one that most closely matches your data.
Open-Source Intelligence
In investigations, it’s increasingly common that some sort of open-source intelligence (OSINT) is necessary. In other words, looking up publicly available information online to help build timelines, corroborate evidence, and sometimes blatantly get a confession.
Magnet Web Page Saver can act as a browser and allows you to take full-page snapshots, including source files, an acquisition report, timestamping, and automatic file hashing. It also accepts a list of URLs to render and acquire automatically. If you ever take screenshots of web pages, this is a must-have.
Bonus Round!
We’re not quite done! The most valuable piece of your kit is you (and your team). Hardware, software, automation, and artificial intelligence can get you far. Still, a well-trained investigator must put the puzzle together and tell the story. Invest in your investigators.
- Magnet Forensics Training Programs — basic through advanced training on all aspects of digital investigation offered online and in-person, also offers several Magnet-specific certification courses. Some of the most well-regarded courses in the industry.
- SANS — an extensive range of high-quality training on information security and digital investigation topics.
- NW3C — basic through advanced training related to various types of crime investigation. Often free for Law Enforcement.
- ECTEG — develops basic through advanced digital investigation training in the European Union. Law Enforcement from any country can request free training from ECTEG.
- DFIR Science and 13Cubed consistently produce digital investigation-related instruction videos for free on YouTube.
Similarly, the digital forensics community is relatively small but very active. There are some great resources like This Week in 4n6, DFIR Training, and About DFIR. Public and private sector experts often share information and resources and answer questions at the DFIR Discord as well as Forensic Focus.
If you are ready to collaborate and share resources with the community, check out Use GitHub to get started in the DFIR Community below.
Conclusions
That about does it for the ultimate guide to DFIR tools in 2022! It’s a fantastic community with a lot of rapid development. No list can do justice to all the great work, but this should be enough to get any digital forensic laboratory started. Check back often to see what’s new. And don’t be afraid to search for specialty tools on GitHub. You never know where you will find the next big break in the case. Keep your options open.