
Connect to GrayKey: AXIOM Integration for Android
Our integration with GrayKey has recently further increased and added some great new functionality, including the ability to grab Android data straight from the GrayKey unit and ingest it directly into Magnet AXIOM.
To start this workflow, select EVIDENCE SOURCES -> MOBILE -> ANDROID and then select the new CONNECT TO GRAYKEY option.
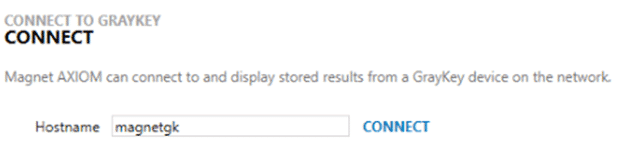
Similar to the iOS workflow, after selecting the CONNECT TO GRAYKEY option, you’ll need to specify the hostname of the unit you are trying to collect the data from. Since you may have multiple units in your network, make sure to specify which hostname has the data you’re looking for.
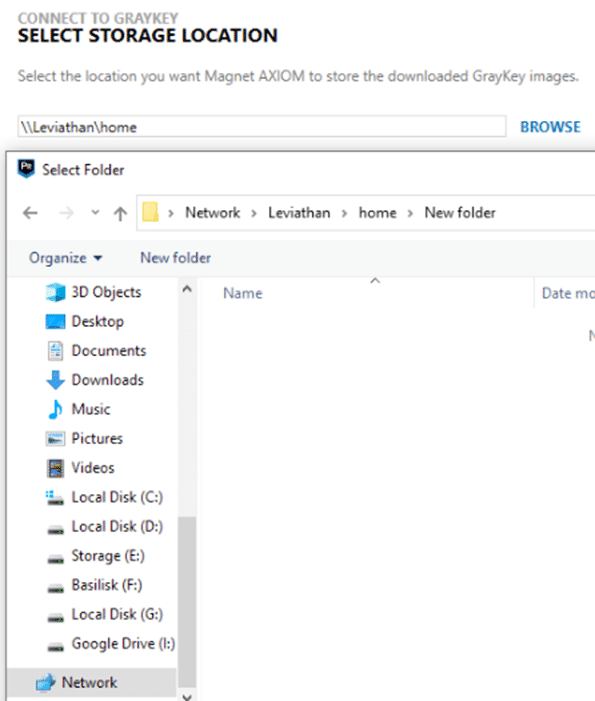
From here, you can specify where you would like the data to be placed — whether that is in a fixed drive, a removable drive, or even network storage.
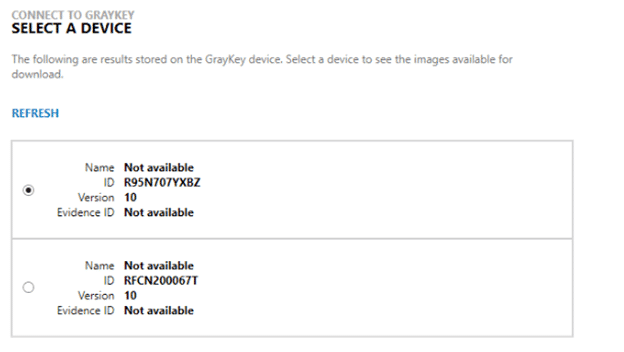
Once a location is specified, you can then select which device you would like to acquire files from. AXIOM will list out the queried images, a device name if available during collection, the ID of the device (the manufacturer Serial Number in this case), the Android version, and any Evidence ID that has been applied.
Any of the available file system extractions and keystore data files will be available to then be extracted from the unit. AXIOM will list out the SHA256 hash values, size of the image, and date of the extraction.
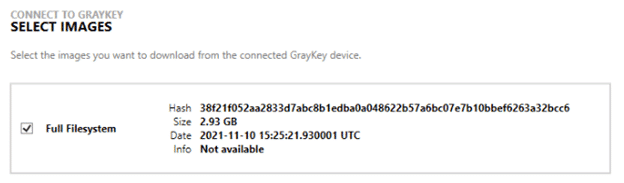
AXIOM will download all of your selected files from the device in parallel. These files will stream to a target location and when they are finished, AXIOM will automatically start the hashing process to check the downloaded file’s SHA256 hash against the stored result, ensuring a proper data download.
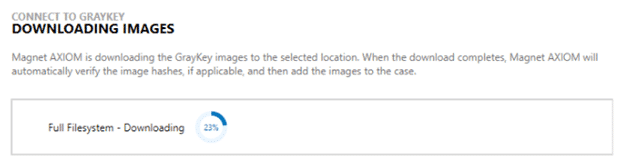

From here, you are ready to go! Whether you have extracted a BFU, AFU, or Full Filesystem extraction, AXIOM will be ready to process it for all available artifacts and information to help deliver evidence to you as quick and efficiently as possible.
Christopher Vance is Magnet Forensics’ Manager of Curriculum Development. In addition to keeping Magnet’s course offerings up to date, he frequently works on new research projects including looking into the latest versions of Android, iOS, and macOS. Christopher keeps many of these projects online at his blog “D20 Forensics” which can be found at http://d204n6.com.