
Keychain Pre-Processing and Easier Data Decryption for iOS in Magnet AXIOM
Streamlining and automating the extraction of encrypted information from iOS filesystem images can now happen easier in Magnet AXIOM with the iOS Keychain — one of the most important evidence items in a case because of how many crucial tokens, passwords, and keys it can store.
Click here to learn more about the “Connect to GrayKey” Android workflow. Or, if you’d like to learn more about ingesting extractions from other third party tools such as UFED and XRY, click here.
The keychain can store several important decryption keys for major third-party applications such as Snapchat as well as first-party data such as Apple’s Notes application. Previously, in order to extract these values, examiners would have to locate the proper keys within the keychain data and use them with the correct OPTIONS button for each artifact within AXIOM they wanted to parse. This could cause examiners to miss data or even when it was properly located, it was very common to not grab the proper value on the first pass.
Now AXIOM prompts the examiner to associate a keychain file to a filesystem image when loading it using several different workflows. This will allow the examiner to tie the correct keychain data to the proper filesystem and will allow AXIOM to automatically extract the correct values and apply them to their respective artifact.
One such workflow would be to select MOBILE -> iOS -> CONNECT TO GRAYKEY and select the iOS device and keychain file straight from your locally available GrayKey unit.
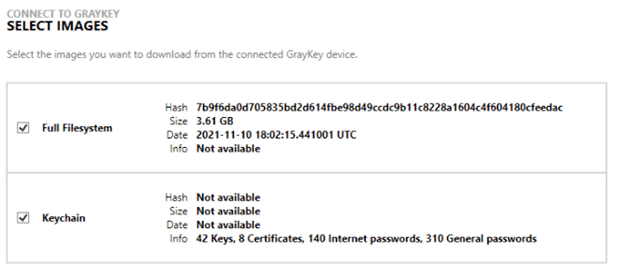
As long as you select both files together, AXIOM will automatically take the required decryption values from the keychain and apply them to the respective artifacts.
If you don’t have the GrayKey unit attached to your local network or have already grabbed the files from the unit, there are other ways to achieve the same goal. Even if that image was generated with a separate process such as using a checkra1n style exploit or another full filesystem acquisition tool. In that case, you’ll want to use the MOBILE -> IOS -> LOAD EVIDENCE workflow and select IMAGE. Once the source filesystem file has been loaded, a new screen will prompt the examiner to locate the respective keychain file.
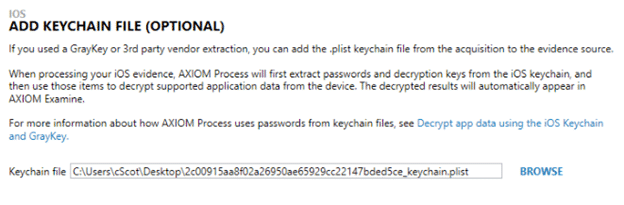
AXIOM will then automatically pull the required values from the keychain file and place them where they need to be. You will not need to use the OPTIONS link for each artifact that previously required the entering of separate keys.
We hope that the release of this great feature will not only help you access your evidence faster and more efficiently, but also unearth those encrypted values that you may have missed on first pass.
Christopher Vance is Magnet’s Manager of Curriculum Development. In addition to keeping Magnet Forensics’ course offerings up to date, he frequently works on new research projects including looking into the latest versions of Android, iOS, and macOS. Christopher keeps many of these projects online at his blog “D20 Forensics” which can be found at http://d204n6.com.