
Responding at Scale with Magnet RESPONSE
This is a post authored by Doug Metz, Security Forensics Consultant.
What is Magnet RESPONSE?
Magnet RESPONSE is a free tool that lets investigators and non-technical users easily collect and preserve critical data relevant to incident response investigations from local endpoints. A pre-set collection profile enables you to target a comprehensive set of files and data relevant to incident response investigations, including RAM.
Minimal to no training is required—it’s as simple as running it on the endpoint, configuring the collection, and clicking “start capture.” Magnet RESPONSE is helpful in situations where non-technical users may need to collect and preserve data on behalf of law enforcement investigators as part of a cyber incident investigation, as well as for corporate IR scenarios.
What happens when you need to collect from dozens of, or even hundreds of endpoints? That’s where the CLI (Command Line Interface) functionality of Magnet RESPONSE comes into play. Get tips for processing with AXIOM Cyber or ‘turn it up to 11’ with the integration flexibility of Magnet AUTOMATE using Watch Folders.
What happens when you need to collect from dozens of endpoints?
That’s where the CLI (Command Line Interface) functionality of Magnet RESPONSE comes into play.
In this post, I’ll show how with PowerShell, we can run Magnet RESPONSE on dozens of endpoints at once. I’ll share tips for processing data captures from RESPONSE with ‘turn it up to 11’ with the integration flexibility of Magnet AUTOMATE using Watch Folders.
Prerequisites
- Web server where you can host MagnetRESPONSE.zip that’s accessible to endpoints.
- File server repository to centralize the file collections.
- PowerShell script to invoke on endpoints.
Web Server Set-up
While there are many ways to establish a web server, my favorite for quick use is one line of Python. On a Mac or Linux, navigate via command line to the directory where you’ve got MagnetRESPONSE.zip. Run the following:
sudo python3 -m http.server 80When you go to http://[IP_ADDRESS you should see a page displaying MagnetRESPONSE.zip and any other files or folders sharing that location. If you want to automate the process, you can do so with a shell script on the server:
cd /[PATH to Directory hosting zip]
ifconfig | grep [first two octets of IP Range]
sudo python3 -m http.server 80File Server Set-up
Again, there are many means to the same end here. All you need is a file share accessible to the endpoints, including permission to write to that directory.
Doing so via Active Directory is not too complicated but out of the scope of this blog post. I set up a Samba share on an Ubuntu VM for demo purposes. In this case, it’s the same server hosting the .zip file, but the web and file servers don’t have to be the same. Basic Ubuntu Samba configuration instructions are available here: https://ubuntu.com/server/docs/samba-file-server
PowerShell Script
We’re going to use PowerShell to automate our Magnet RESPONSE collection process. The first thing we need to do is establish the variables relevant to this collection.
### VARIABLE SETUP
$caseID = "demo-161" # no spaces
$outputpath = "\\Server\Share" # Update to reflect output destination.
$server = "192.168.4.187" # "192.168.1.10" resolves to http://192.168.1.10/MagnetRESPONSE.zip- Case ID is the identifier for the case or incident number. (No spaces)
- Output Path is the location where RESPONSE will save output.
- The Server is the web server where we have the zip file.
Collection Profiles
Within the script, we need to have at least one set of collection arguments defined. In this case, I’ve built multiple profiles, commented out by default. Uncomment the profile you want to use to mark it as active.
You can design your collection profiles using any of the available CLI options. Just follow the format below. You can get a list of all the available CLI options for Magnet RESPONSE here.
#### Capture Volatile
$profileName = "CAPTURE VOLATILE"
$arguments = "/capturevolatile"
#>
#### Extended Process Capture
<#
$profileName = "EXTENDED PROCESS CAPTURE"
$arguments = "/capturevolatile /captureextendedprocessinfo /saveprocfiles"
#>
#### Systen Files
<#
$profileName = "SYSTEM FILES"
$arguments = "/capturesystemfiles"
#>Execution
When the script invokes Magnet RESPONSE, it will use the arguments from the case variables and the profile.
MagnetRESPONSE\MagnetRESPONSE.exe /accepteula /unattended /output:$outputpath/$caseID-$env:ComputerName-$tstamp /caseref:$caseID $argumentsI’ve assembled all these elements together in a script that you can download and modify to suit your environment. It includes all the functions above with some additional display enhancements. It will also check to ensure it is running with administrator permission before running.
<#
Magnet RESPONSE PowerShell Enterprise
doug.metz@magnetforensics.com
ver 1.7
The script first checks if it is running with administrative permissions and exits if not.
The script will then download Magnet RESPONSE from a web server, extract it, and run with the specified options.
The $outputpath parameter can be used to write to a local directory `C:Temp`, `D:\Output` or network `\\Server\Share`.
Finally, the script removes the downloaded Magnet RESPONSE files and prints the time taken for the collection
and transfer to complete.
#>
param ([switch]$Elevated)
function Test-Admin {
$currentUser = New-Object Security.Principal.WindowsPrincipal $([Security.Principal.WindowsIdentity]::GetCurrent())
$currentUser.IsInRole([Security.Principal.WindowsBuiltinRole]::Administrator)
}
if ((Test-Admin) -eq $false) {
if ($elevated) {
} else {
Write-host ""
Write-host "Magnet RESPONSE requires Admin permissions.
Exiting.
"
}
exit
}
### VARIABLE SETUP
$caseID = "INC-KC-demo-001" # no spaces
$outputpath = "\\server\Automate\WatchFolders\Magnet_Response" # Update to reflect output destination. C:\Temp R:\Output \\Server\Share
$server = "192.168.4.187" # "192.168.1.10" resolves to http://192.168.1.10/MagnetRESPONSE.zip
$tstamp = (Get-Date -Format "yyyyMMddHHmm")
#######
### COLLECION PROFILE - Uncomment the collection type to be used:
#### Quick Sweep
<#
$profileName = "QUICK SWEEP"
$arguments = "/capturevolatile /captureextendedprocessinfo"
#>
#### Capture Volatile
$profileName = "CAPTURE VOLATILE"
$arguments = "/capturevolatile"
#>
#### Capture Volatile & RAM
<#
$profileName = "CAPTURE VOLATILE & RAM"
$arguments = "/captureram /capturevolatile"
#>
#### Extended Process Capture
<#
$profileName = "EXTENDED PROCESS CAPTURE"
$arguments = "/capturevolatile /captureextendedprocessinfo /saveprocfiles"
#>
#### Systen Files
<#
$profileName = "SYSTEM FILES"
$arguments = "/capturesystemfiles"
#>
#### Just RAM
<#
$profileName = "CAPTURE RAM"
$arguments = "/captureram"
#>
#### Magnet TRIAGE
<#
$profileName = "Magnet TRIAGE"
$arguments = "/captureram /capturevolatile /capturesystemfiles /captureextendedprocessinfo"
#>
#### Full Capture
<#
$profileName = "FULL CAPTURE"
$arguments = "/captureram /capturepagefile /capturevolatile /capturesystemfiles /captureextendedprocessinfo /saveprocfiles"
#>
#### Kitchen Sink
<#
$profileName = "KITCHEN SINK"
$arguments = "/captureram /capturepagefile /capturevolatile /capturesystemfiles /captureextendedprocessinfo /saveprocfiles /capturefiles:.ps1,.vbs,confidential /skipsystemfolders /maxsize:500 /captureransomnotes"
#>
#### End of Collection Profiles
Clear-Host
Write-Host ""
$global:progressPreference = 'silentlyContinue'
$stopwatch = [System.Diagnostics.Stopwatch]::StartNew()
[console]::ForegroundColor="DarkCyan"
Write-Host "Downloading Magnet RESPONSE"
Invoke-WebRequest -Uri http://$server/MagnetRESPONSE.zip -OutFile .\MagnetRESPONSE.zip
Expand-Archive -Path .\MagnetRESPONSE.zip
Remove-Item .\MagnetRESPONSE.zip
Clear-Host
Write-Host ""
Write-Host "Magnet RESPONSE v1.7
$([char]0x00A9)2021-2023 Magnet Forensics Inc
"
$OS = $(((gcim Win32_OperatingSystem -ComputerName $server.Name).Name).split('|')[0])
$arch = (get-wmiobject win32_operatingsystem).osarchitecture
$name = (get-wmiobject win32_operatingsystem).csname
Write-Host "
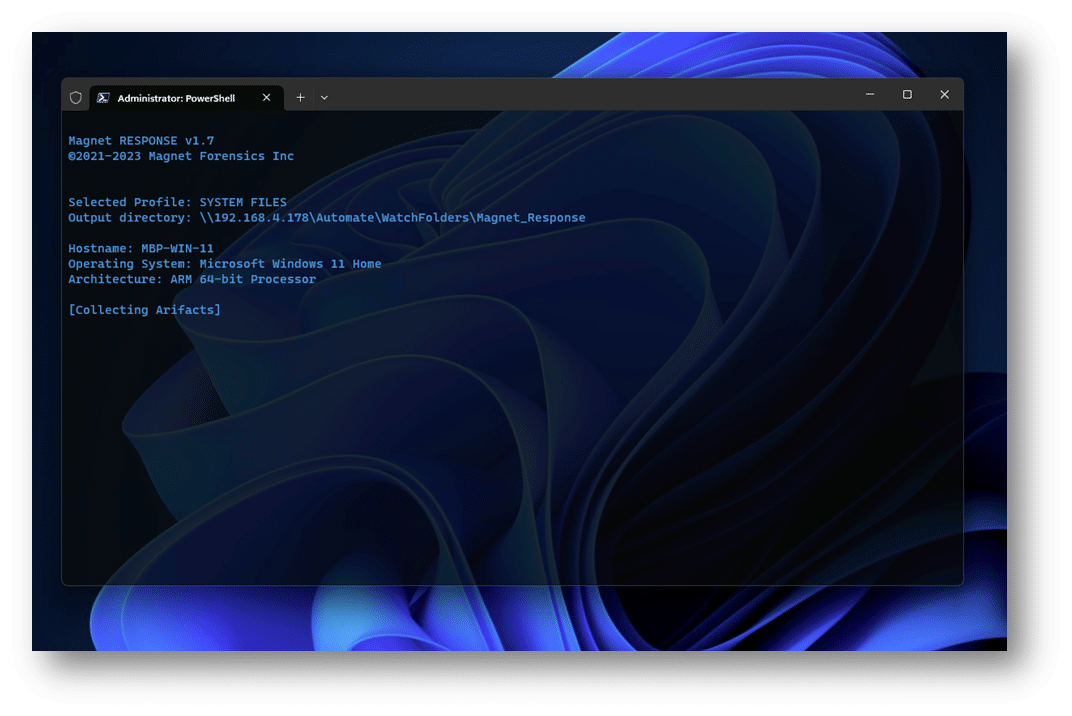
Selected Profile: $profileName"
if (Test-Path -Path $outputpath) {
Write-host "Output directory: $outputpath"
} else {
Write-host "Specified output path does not exist.
"
exit
}
Write-host "
Hostname: $name
Operating System: $OS
Architecture: $arch
"
MagnetRESPONSE\MagnetRESPONSE.exe /accepteula /unattended /silent /output:$outputpath/$caseID-$env:ComputerName-$tstamp /caseref:$caseID $arguments
Write-Host "[Collecting Arifacts]"
Wait-Process -name "MagnetRESPONSE"
$null = $stopwatch.Elapsed
$Minutes = $StopWatch.Elapsed.Minutes
$Seconds = $StopWatch.Elapsed.Seconds
Write-Host "** Acquisition Completed in $Minutes minutes and $Seconds seconds.**
"
Remove-Item "MagnetRESPONSE\" -Recurse -Confirm:$false -Force
Write-Host "Operations Complete.
"
All that’s left is to execute the script on the endpoints to collect from. You can do this via PowerShell Remoting or SOAR or EDR tools. Every host that executes the script will download Magnet RESPONSE from the web server, run the specified collection profile, and then save the output to the file server. The results can be investigated by hand or ingested into tools like Magnet AXIOM Cyber.
Note: you can download the script, as well as contribute to future developments, at https://github.com/MagnetForensics/Magnet-RESPONSE-PowerShell
Note: you can download the script, as well as contribute to future developments, at https://github.com/MagnetForensics/Magnet-RESPONSE-PowerShell.
Processing and Analyzing with Magnet AXIOM Cyber
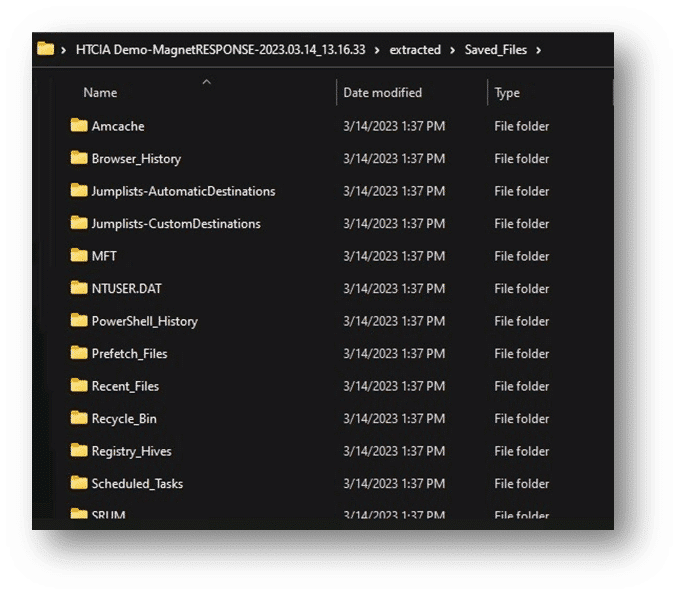
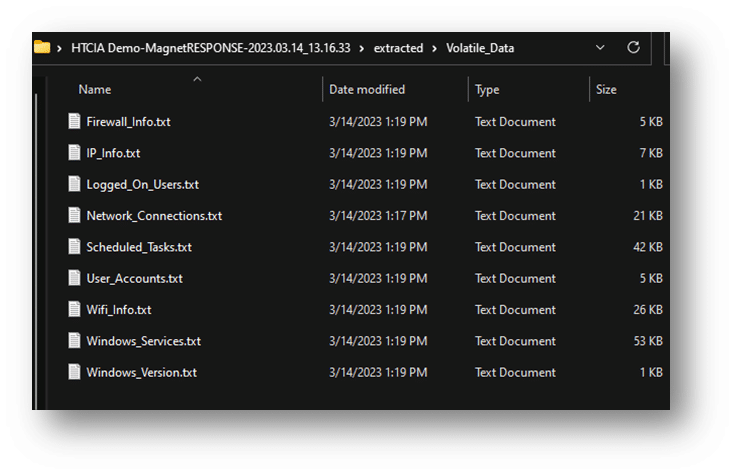
Magnet AXIOM Cyber is a robust yet intuitive digital forensics solution that enables you to unravel and understand cyber threats efficiently. AXIOM Cyber easily supports the processing of Magnet RESPONSE output collections.
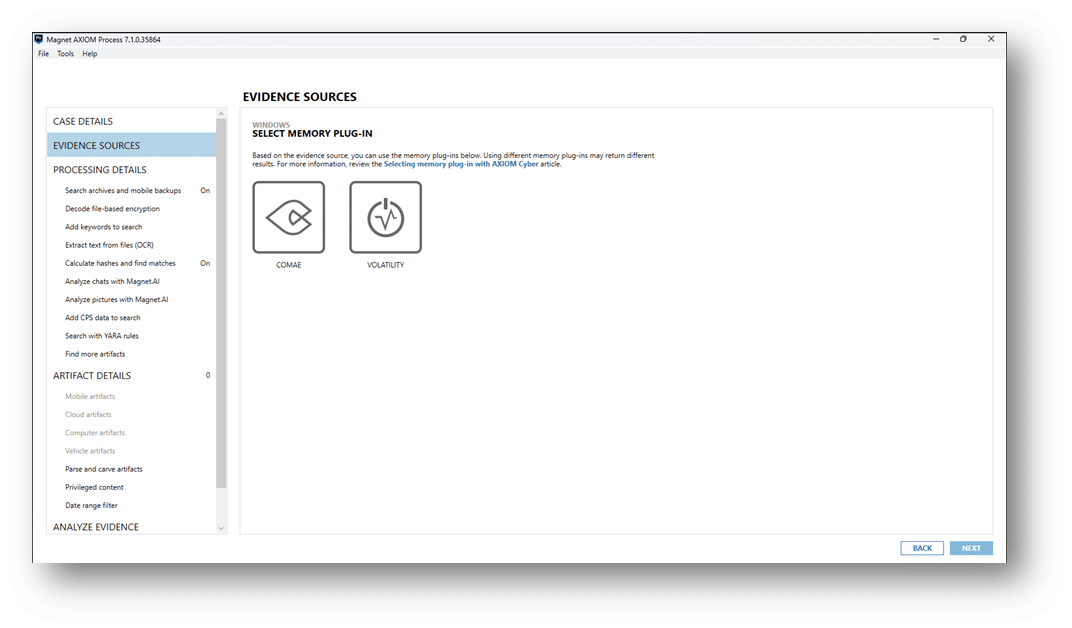
Magnet RESPONSE will collect memory by default using MAGNET DumpIt For Windows. If the collection attempt fails, Magnet RESPONSE will fall back to using MAGNET RAM Capture. You can process either format within AXIOM Cyber. For DumpIt For Windows collections, you can process using Comae or Volatility.
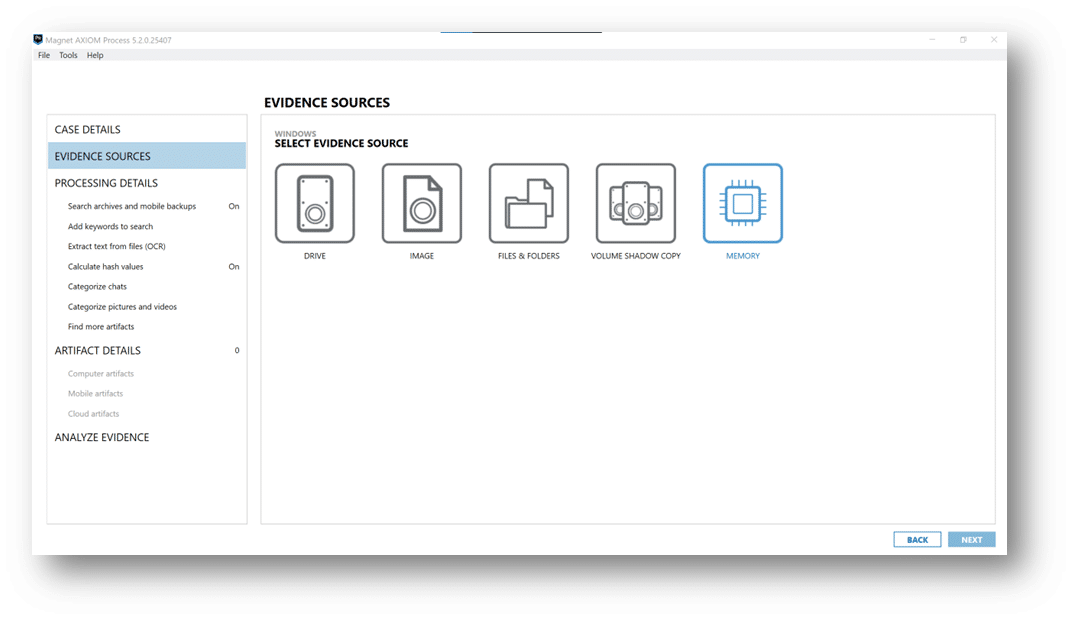
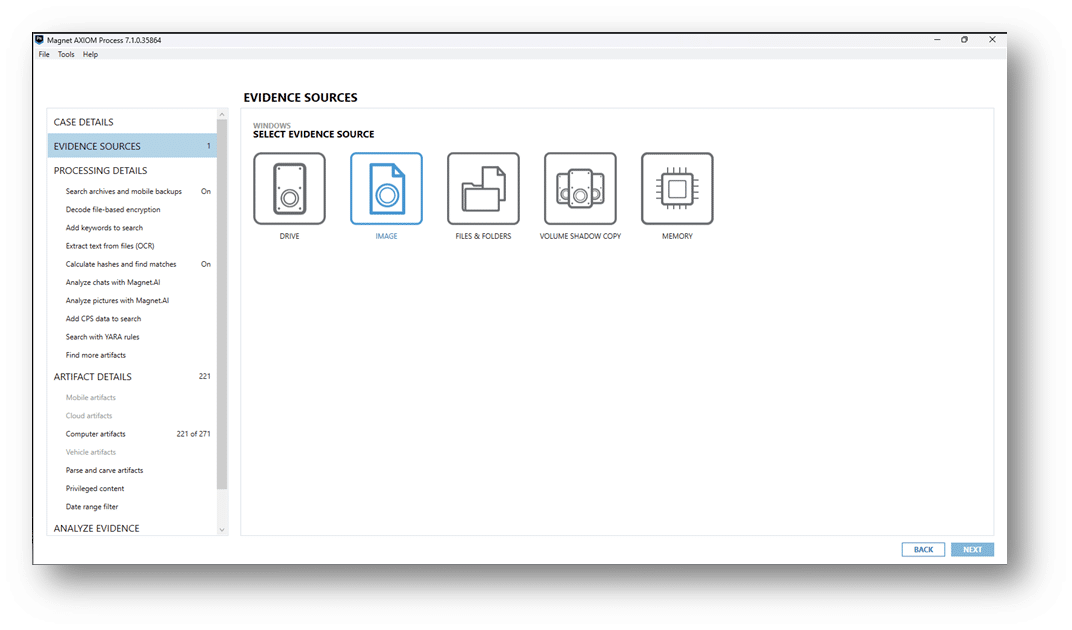
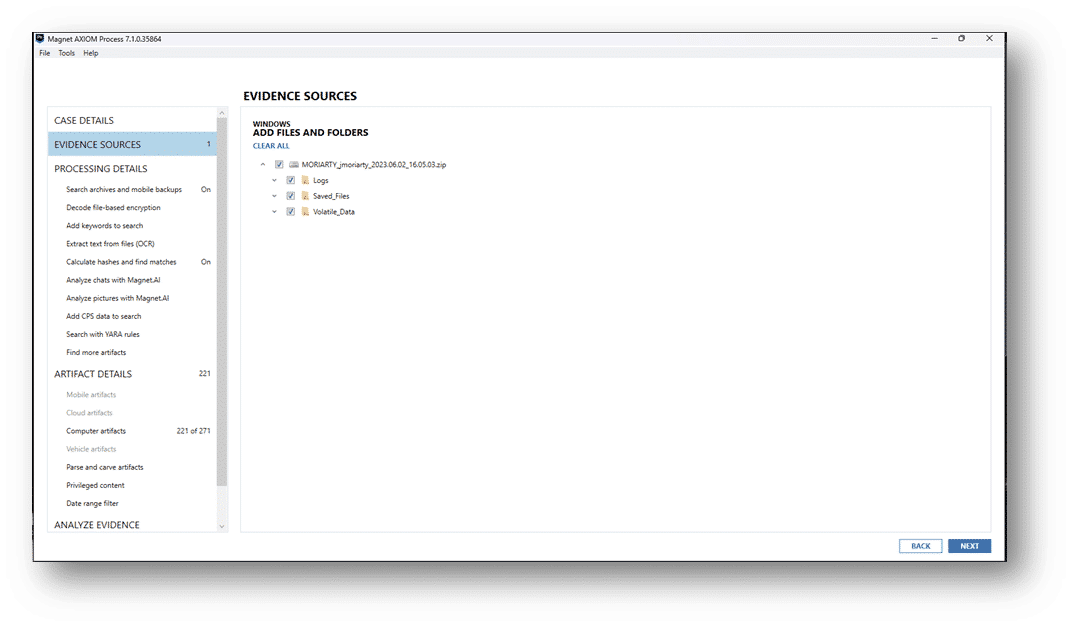
For all the other collected data, simply point AXIOM Cyber to the .zip file as an Image.
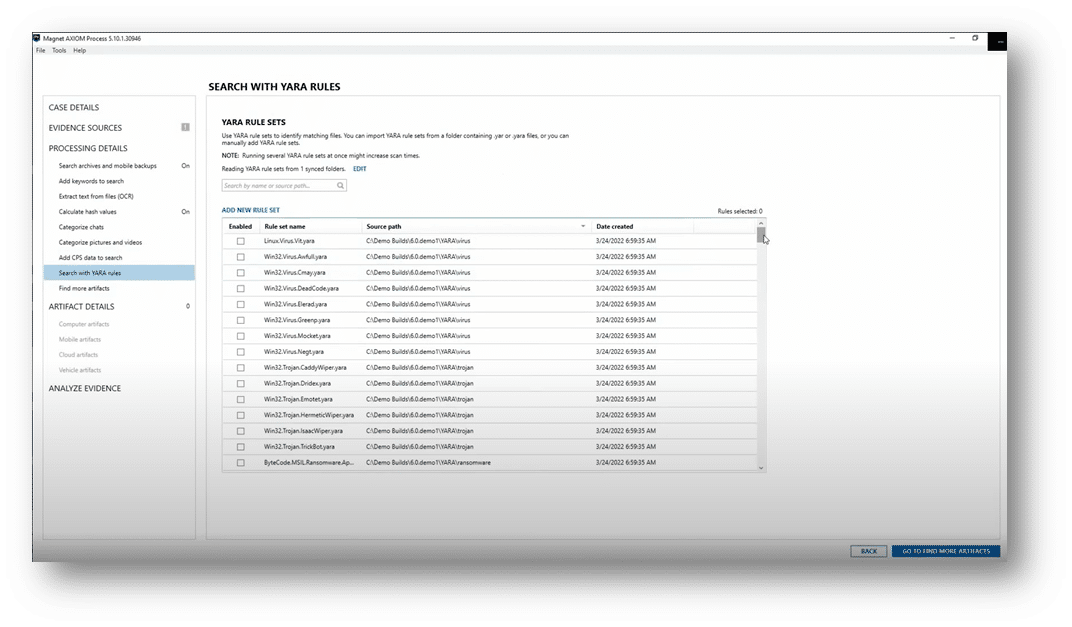
Utilizing features like YARA searching and keywords can significantly reduce investigation time for incident response investigations. To learn more about YARA rule processing in AXIOM Cyber, check out the blog post “YARA Rule Processing in Magnet AXIOM Cyber.”
Dial it up to 11 with Magnet AUTOMATE
So, your process is in place now on when and how the collection script will execute. You’ve centralized your collections and made them accessible to the SOC and IR teams. Suppose your workflow includes having your collections processed as Magnet case files. In that case, AUTOMATE is a powerful solution to automate forensic processing workflows from all data sources (computer, mobile, cloud, and IoT) and even 3rd party images.
We can already direct our scripted Magnet RESPONSE collections to a specified network folder. If that folder is set up as a Watch Folder in AUTOMATE, any time a new RESPONSE collection completes, AUTOMATE will initiate the respective evidence processing workflow. If that folder is set up as a Watch Folder in AUTOMATE, any time a new Magnet RESPONSE collection completes, AUTOMATE will initiate the respective evidence processing workflow.
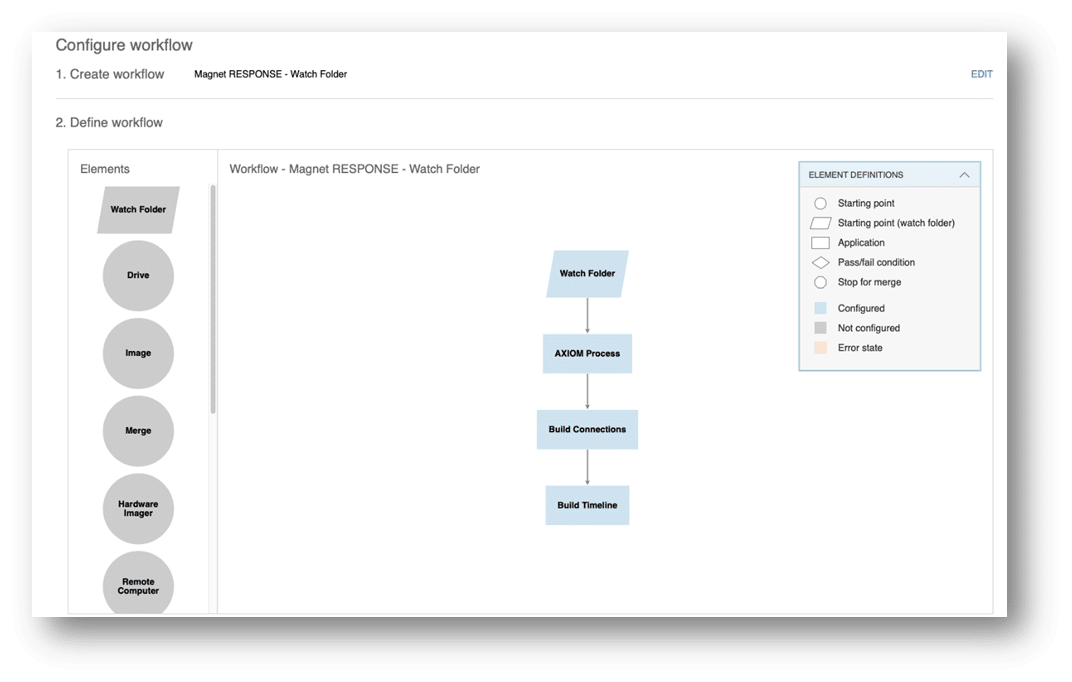
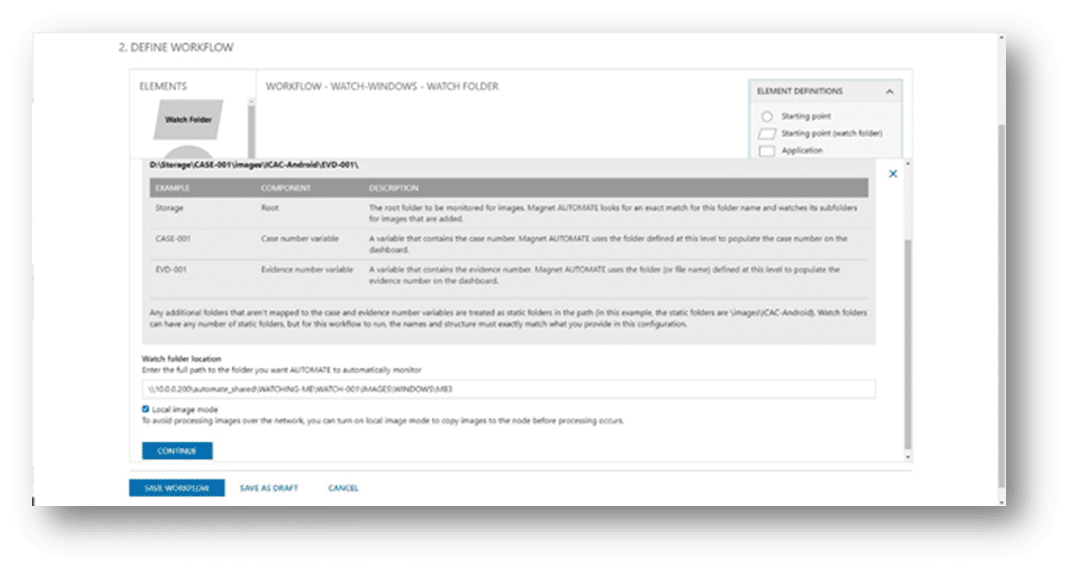
AXIOM processing and post-processing (Timeline, Connections, etc.) and any other elements you want to add into the workflow, are run using automation.
The result: you go from script execution to case processing and export without human intervention. If it’s a SOC automation solution, such as a SOAR, that triggered the RESPONSE collection, the analyst can go directly to the processed triage case to begin their investigation using Magnet AXIOM or Magnet AXIOM Cyber.
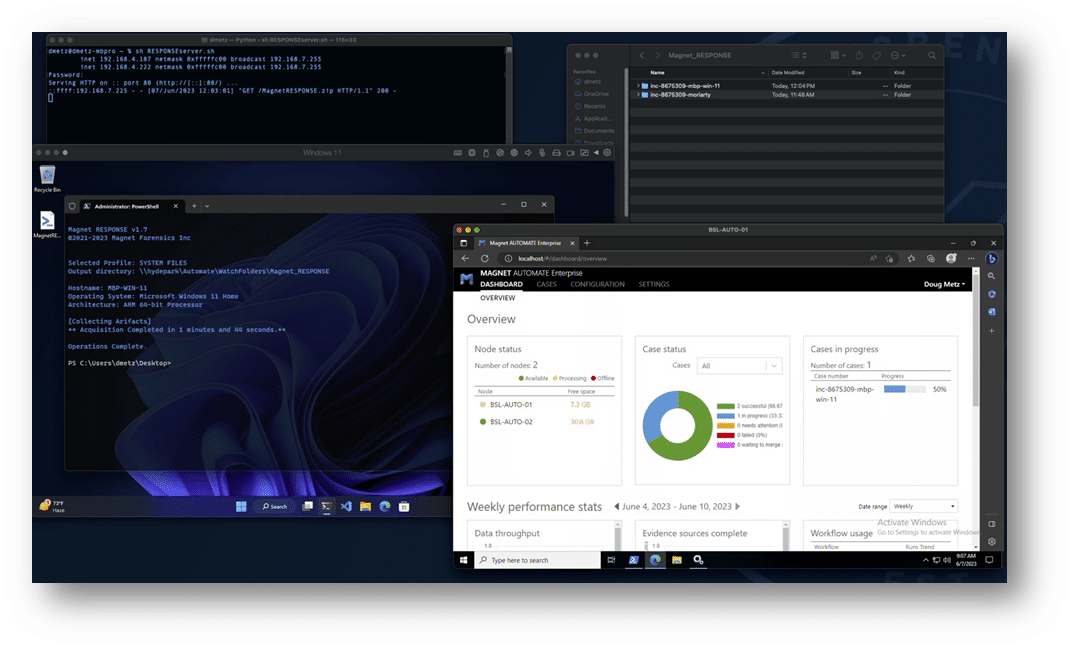
Learn More About Using Magnet Forensics Solutions for Incident Response
- Check out the accompanying webinar to this blog post to see Doug demo the Magnet RESPONSE CLI and AXIOM Cyber.
- Haven’t tried AXIOM Cyber yet? Request your free trial here and experience the power of a robust forensic solution that simplifies your digital investigations.
- Learn more about all of the ways AXIOM Cyber can help with your incident response investigations here.