
Perform remote collections of endpoints with confidence
In today’s evolving digital landscape, forensic examiners in corporate environments are increasingly tasked with managing incident response, internal investigations, and eDiscovery efforts across complex work environments, such as remote and hybrid work models. The diversity and volume of different data sources—ranging from cloud storage to mobile devices, and collaboration tools—create complexity and significant challenges in modern investigations.
Not only that, the lack of physical access to endpoints can introduce delays and increase costs, necessitating travel and additional resources. This added complexity makes having the right investigative tools in your toolkit more essential than ever.
Legacy enterprise DFIR solutions, specialized remote acquisition tools, open-source tools, and custom scripts have long been staples in the examiner’s toolkit, enabling them to adapt to various situations. However, as the landscape of corporate environments evolves with these new work models, the limitations of these traditional tools become apparent. Legacy DFIR solutions have struggled to adapt to the complexity of today’s cloud-based and hybrid environments, leaving examiners without critical data to perform their investigation.
DFIR solutions like Magnet Axiom Cyber and Magnet Nexus are designed to meet these challenges head on. They provide robust and reliable capabilities for remote collections, particularly in environments where endpoints are geographically dispersed and diverse in their operating systems. These tools are crucial for ensuring that forensic examiners can efficiently manage investigations, minimize delays, and preserve the integrity of data in today’s fast-paced and ever-changing digital world.
Why having the right tool is important
Let’s consider a scenario that many forensic examiners have likely encountered:
You receive a notification from your SOC analyst about potentially malicious activity on an endpoint located in one of your satellite offices, possibly on the other side of the world.
The situation could involve anything from a network intrusion, a malware or ransomware attack, to IP theft or data exfiltration. As the possibilities race through your mind, you recognize the gravity of the situation:
- Time is critical: A variety of stakeholders—ranging from SOC members to senior leadership and IT—are anxiously waiting for your analysis.
- Tool reliability: If you’re using a legacy tool like EnCase for remote acquisition, you might face several challenges. Connectivity issues with the agent on the target endpoint could cause significant delays. The risk of a timeout, requiring a restart of the collection, looms large, especially if the target endpoint is a Mac.
Introducing Axiom Cyber and Nexus: reliable remote endpoint forensics for on and off-network devices
Imagine a different scenario, one where you’re equipped with Magnet Axiom Cyber and Magnet Nexus, both designed to handle the complexities of modern digital forensics easily.
With Axiom Cyber, you can generate an agent and deploy it on-demand (as needed) by the method of your choosing, or through the Axiom Cyber interface.
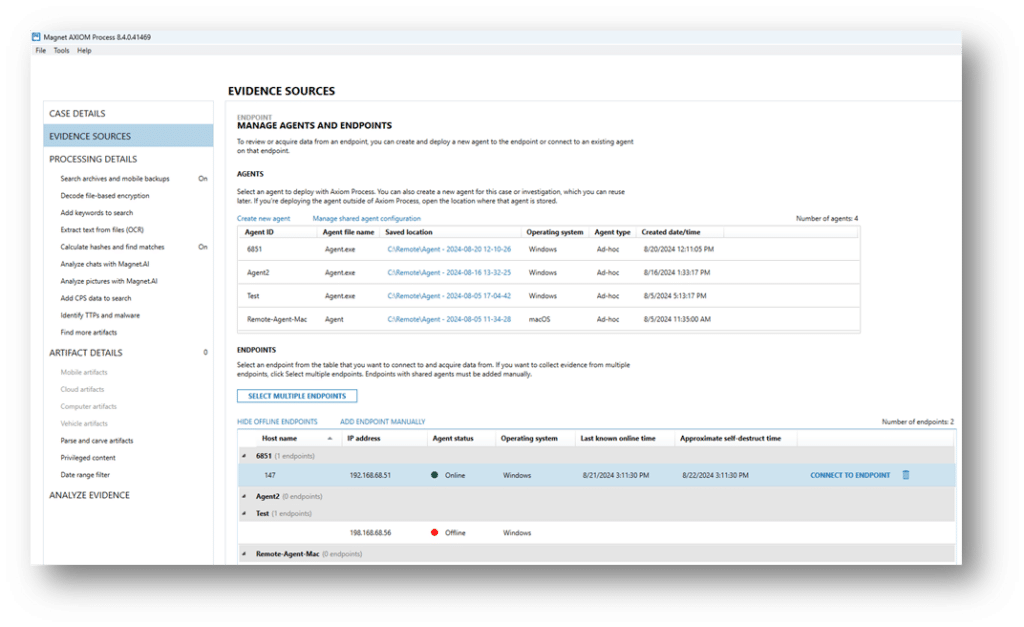
As soon as you receive the notification from your SOC analyst, you launch Axiom Cyber and swiftly create a covert agent, naming it something innocuous to avoid raising any red flags with the end user. The agent is deployed seamlessly to the target endpoint and connects within seconds.
With Axiom Cyber, you have confidence that the collection will proceed smoothly. Even if the endpoint goes offline temporarily, the collection will pause and resume automatically, ensuring no data is lost. Axiom Cyber is also integrated with Jamf for managing and securing Apple devices. This integration extends capabilities to Mac endpoints, even those equipped with security chips and SIP-enabled, so you don’t have to worry about compatibility issues.
By using Jamf in conjunction with Axiom Cyber, you can:
- Quickly deploy collection agents across your Apple device fleet with minimal user intervention.
- Maintain compliance with corporate policies and security standards, even during remote collections.
- Manage your Apple endpoints efficiently, reducing the time spent on manual configurations and increasing your focus on threat investigation.
What if you need comprehensive visibility across all endpoints and the ability to perform multiple collections simultaneously? While Axiom Cyber allows you to queue up to 15 endpoint collections, Magnet Nexus offers both enterprise-wide visibility and the capability to conduct several collections and process them at once.
Magnet Nexus: SaaS-based endpoint forensics solution for multiple endpoint investigations
Magnet Nexus enhances your ability to perform remote collections with even greater precision and efficiency. Nexus allows you to remotely acquire data from a wider range of endpoints, regardless of location or operating system, all from a single web-based interface.
Key features of Magnet Nexus:
- Cross-platform compatibility: Whether the endpoint is running Windows, macOS, or Linux, Nexus provides a unified solution for remote endpoint forensics.
- Secure deployment: The Nexus agent(s) can be deployed manually or through your preferred enterprise deployment software.
- Flexible agent deployment: The deployed agent can persist on every endpoint, so it is there when you need it. Alternatively, you can create and deploy an agent on demand, whatever meets your organization’s requirements.
- Dynamically scale with cloud-based processing: Nexus efficiently processes larger data sets utilizing optimized parallel processing. As a SaaS solution, it can also be accessed from anywhere at any time.
- Resilient data acquisition: Nexus ensures that even if an endpoint goes offline, the data acquisition process can pause and resume without any data loss, providing a seamless experience.
- Saves time: Targeted collections with Nexus protect employee privacy and reduce the amount of data that needs to be reviewed. The agents can also be set up with automatic expiration so that they are automatically removed, reducing clean-up tasks.
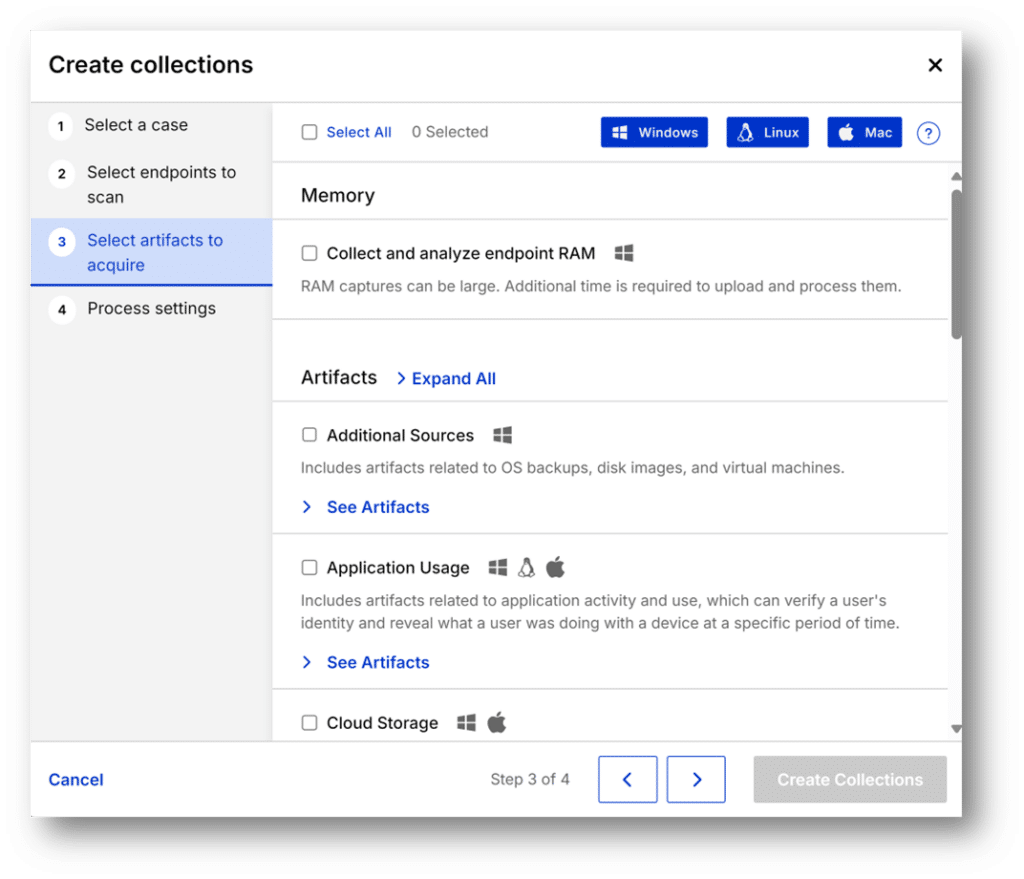
- Advanced techniques: Nexus can collect RAM dumps, active connections, users, network shares, and services and apply Yara rules to those collections. It forensically acquires and analyzes network activity, file logs, live system artifacts, and more.
- Broad view across networks: The endpoint manager allows you to view which endpoints are online, when they were last updated, and can be searched by name or IP.
Confidently approach every remote endpoint investigation
In the ever-evolving field of digital forensics, having the right tools is paramount. The combination of Magnet Nexus, as a SaaS-based digital forensics solution, and Axiom Cyber advanced parsing capabilities provides forensic examiners with a robust, reliable, and scalable solution for conducting remote data collection and analysis. With these solutions in your toolkit, you can confidently approach each investigation, knowing that you have the technology needed to uncover the truth, regardless of where the endpoint is located or what operating system it runs.
For more information about Axiom Cyber: https://www.magnetforensics.com/products/magnet-axiom-cyber/
For more information about Magnet Nexus: https://www.magnetforensics.com/products/magnet-nexus/