Getting Evidence from iOS Screen Time Artifacts
Screen Time, a new feature added to the release of iOS 12, is designed to supervise activities that are going on within the device. Whether set up from a parental standpoint to limit how much time is being spent on video games, or someone is simply trying to limit how much time they spend on email outside of work, the Screen Time functionality has some helpful real world uses — and major implications for forensics as well.
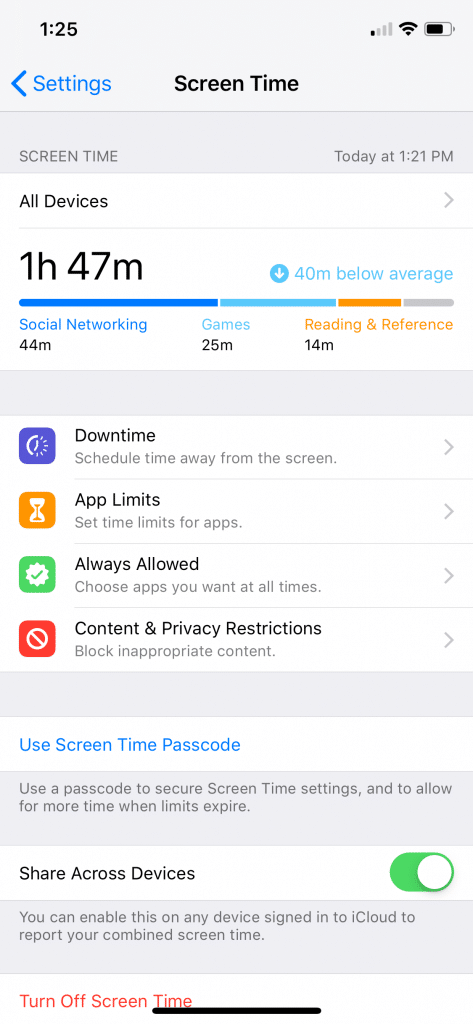
Screen Time is enabled by going into the iOS 12 device’s Settings application and selecting Screen Time > Turn on Screen Time. At this point the user can select “This is My Device” or “This is a Child’s Device”. Users can also set up a device-based password in order to manage and administer the Screen Time reports.
Once Screen Time is set up, there are four settings the user can manage:
- Downtime
- App Limits
- Always Allowed
- Content & Privacy Restrictions
Each of these are made for supervising a device or shared device but can still offer some insights into when applications should and shouldn’t be active within the system. The real forensic value comes from the Screen Time reports themselves.
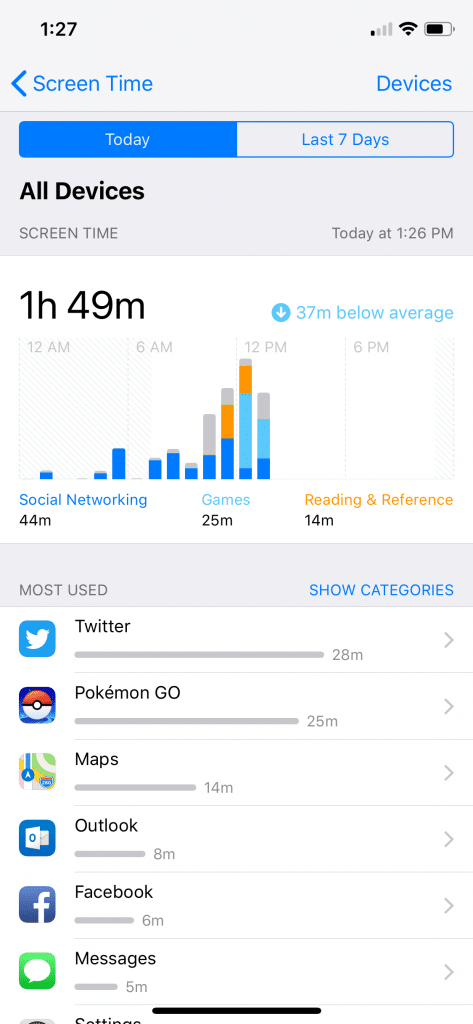
By default, Screen Time is not synced between devices but users can turn that on with a toggle at the bottom of their screen. Once enabled, Screen Time reports will be generated for all attached devices into that account. Screen Time will make two reports, a daily report, and a weekly report and the data is only kept within the UI for 7 days.
These reports allow a user to track information such as the most used daily and weekly application including how many minutes that application has been used, how many device pickups the users had done — including when — and how many notifications each application has generated (and when.) This information is Incredibly valuable as we can now gleam when a user was active with their device, what applications were active, and for how long those applications were active.
Finding the Database that Stores Records
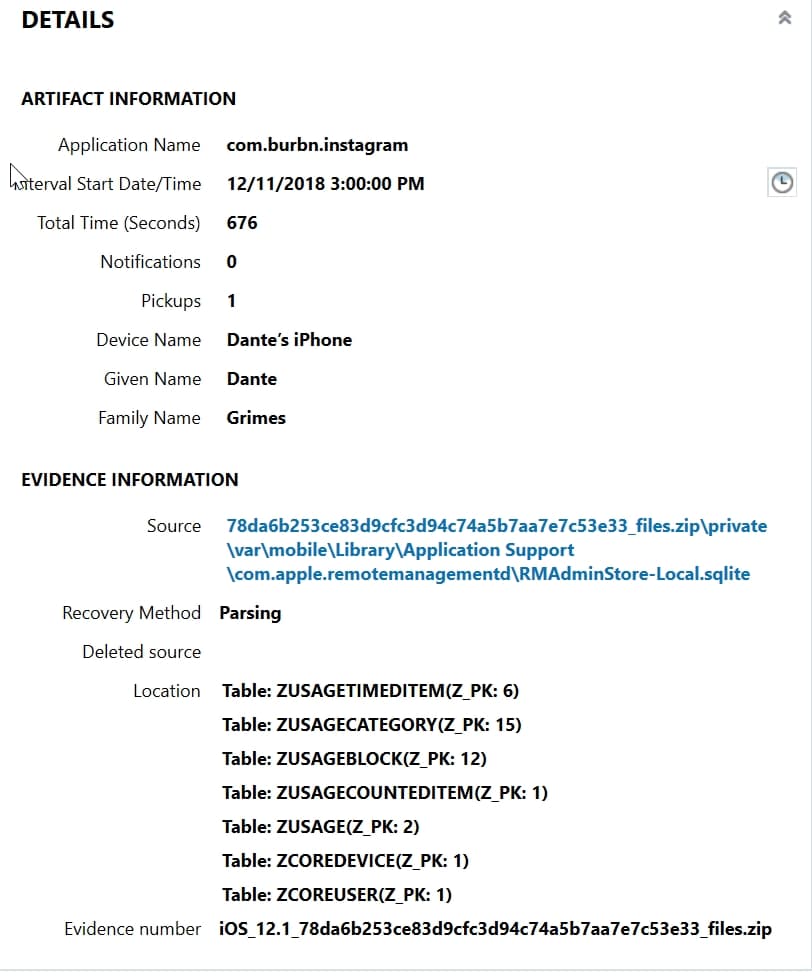
The database responsible for storing these records are found within the iOS 12 device’s file system. They are not part of a standard iOS backup and have to be acquired using a method to obtain a full filesystem such as a GrayKey image. Once obtained, the database in question is found within privatevarmobileLibraryApplication Supportcom.apple.remotemanagmentd and the relevant database is the RMAdminStore-Local.sqlite. There’s also another database which talks about the synced devices to this account RMAdmin-Store-Cloud.sqlite.
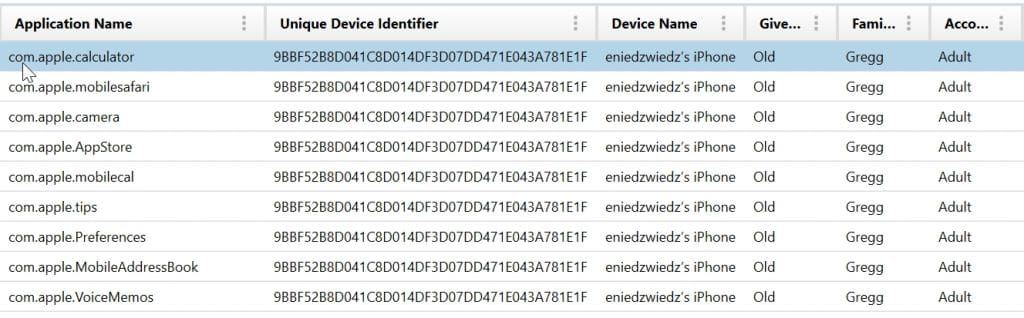
While work is being done to rip this database apart at the seams, Magnet AXIOM has recently added two Screen Time artifacts to process these records and report it out to the user. The first is Screen Time Synched Applications. This artifact pulls out all of the records that have been recorded by the Screen Time application on iOS 12 which includes the application name, the UDID of that device, a device name, given name, family name, and account type.
If multiple accounts are tied into a single “Family Sharing” plan through Apple and all have Screen Time enabled, users can see what applications have been used on those devices as well as the UDID of those devices even if the devices aren’t in their possession currently. This gives examiners new avenues to investigate if their search warrants it.
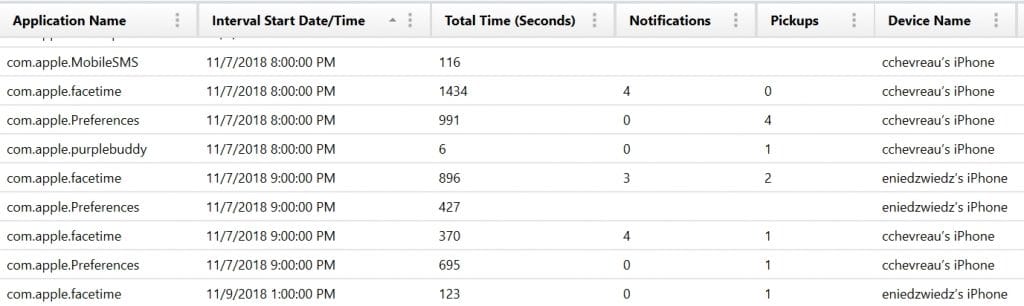
The Screen Time Application Usage artifact tracks the actual usage of those applications in the Screen Time report. These applications are also tracked here in the Application Name, when the tracking interval started, how many times in seconds that application was active, how many notifications, and how many pickups occurred around that application.
Some of the application names listed will be for core applications or functions. However, third-party applications are also tracked in this list so that examiners can see what applications are being most heavily used by the user of the device. The interval start date/time column lists when the one-hour window starts that’s being tracked. From there, examiners can then see during that one-hour window how long that application was active, how many notifications the user received, and how many times they performed a pickup of their device during that time window.
For an examiner this can be incredibly relevant when a user says their device was inactive but also for tracking their device behavior. As you learn what applications are most active, examiners can then target these applications for deeper analysis in AXIOM. From here, examiners can also track data across other important file system artifacts such as Network Usage and KnowledgeC to get a better picture of an application or device’s usage.