
Connect CrowdStrike to Your DFIR Workflows for Instant Collections
We’ve integrated Magnet AUTOMATE Enterprise with CrowdStrike Falcon Real Time Response to help instantly perform forensic collection and process endpoints at enterprise scale.
Learn more about the benefits of DFIR automation and how our open, vendor-agnostic approach enables you to integrate your entire tech stack into streamlined, efficient workflows.
Lost Insights: The Challenge With Disconnected Tools
The delay between an alert in the SOC and manual forensic collection could have severe consequences. It can mean the difference between getting the insights you need to stop a sophisticated attack for good or inadvertently letting it linger (and causing more damage.)
This is because, between alert and investigation, remediation occurs. This is where data is often modified or completely lost as IR teams rush to quarantine endpoints or re-image the endpoint. This leaves you with data that may not reveal the full picture of an attacker’s TTPs.
Bringing together the detection and response capabilities of leading XDR tools, such as CrowdStrike, with your Magnet Forensics solutions and DFIR workflows, creates a complete end-to-end workflow from the SOC to the DFIR team.
This helps to ensure critical data is collected quickly and at the depth that you need to gain a full picture of the incident—answering the how, what, where, and when (and sometimes who) is only possible with the deep collection, parsing and carving capabilities of forensics tools, like Magnet AXIOM Cyber.
Instant, Automatic Collection Preserves Critical Evidence
With legacy tools, forensic investigations were manual and time-consuming. And the work only happened when an investigator was behind the keyboard.
Now, with AUTOMATE Enterprise and the power of DFIR automation, the same benefits of automation realized in the SOC can be realized in the DFIR lab. Response times are faster—a collection is kicked off immediately—reducing the delay to collect down to seconds, and at any time of the day. With the collection and processing of incidents fully automated, investigators can spend their time focused on high-value tasks such as analysis, while letting technology handle the repetitive tasks.
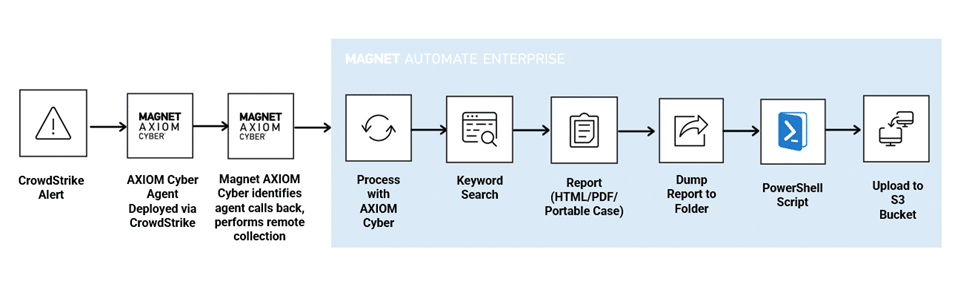
How AUTOMATE Enterprise Integrates With CrowdStrike
- Step 1 – An alert in CrowdStrike Falcon Real Time Response is ingested into the SIEM.
- Step 2 – The SIEM runs a playbook and determines that a forensic collection is required.
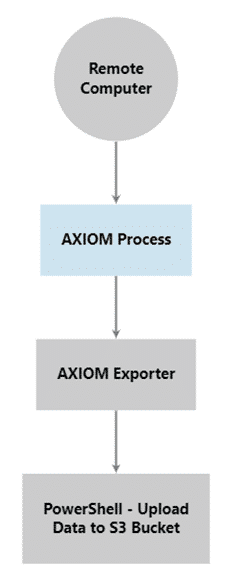
- Step 3 – CrowdStrike deploys the AXIOM Cyber Remote Acquire agent to the endpoint.
- Step 4 –The Remote Acquire agent calls back to AUTOMATE Enterprise and triggers the relevant workflow, instantly performing the forensic collection.
- Step 5 – Collection is completed, and processing begins in AUTOMATE Enterprise. In this case, the data is run through a keyword search and a report is created and saved to a network folder for the investigator to analyze.
- Step 6 – Run custom PowerShell scripts, as required.
- Step 7 – The data export is uploaded to an S3 bucket for storage.
Key Benefits
- Reduce time to response (collection) down to seconds—don’t let critical evidence get modified or lost.
- Integrate tooling from your SOC, such as Crowdstrike, with the rest of your DFIR tool & tasks—allowing you to streamline workflows and remove manual touchpoints that waste time.
- Boost productivity—keep investigators focused on high-value tasks not time-consuming data acquisition.
Learn More About Automating DFIR Workflows
Magnet AUTOMATE Enterprise integrates with almost any tool from your toolkit, allowing you to streamline and automate workflows for almost any use case. To learn more about automating your DFIR workflows, check out these resources:
- Wondering how AUTOMATE Enterprise differs from a SOAR? Read the solution brief, Complement Your SOAR by Automatically Collecting, Processing, & Preserving Forensic Evidence, to learn more about how AUTOMATE Enterprise and SOAR platforms can work together to accelerate your triage and forensic investigation workflows.
- Modernizing Forensic Workflows with Magnet AUTOMATE Enterprise – download the guide to learn how AUTOMATE Enterprise can streamline data loss prevention malware investigations, and smooth out internal communications.
- Watch the Overview of Magnet AUTOMATE Enterprise webinar to learn more about the solution and how it works
Ready to see AUTOMATE Enterprise in action? Request a personalized demo today.