Analysis of GrayKey Images with AXIOM: New KnowledgeC Database Artifact Additions
With the past few releases of Magnet AXIOM, we’ve added new artifacts found on iOS file system images seen primarily when investigators have access to tools such as GrayKey. With the release of AXIOM 2.8, we’ve included additional iOS artifacts, including the KnowledgeC database artifacts found on iOS devices.
KnowledgeC Database
As investigators, our job revolves around finding evidence and providing context to the big five W’s; the who, what, when, where, and why. Telling the story and connecting these dots are critical, especially when we are seeking justice for victims in court. Utilizing a tool such as a GrayKey, law enforcement investigators once again have access to the Apple iOS file system, which contains the KnowledgeC database. This database will not be found using traditional iOS imaging techniques, nor is it found in a local iTunes backup.
On iOS the database can be located: /private/var/mobile/Library/CoreDuet/Knowledge/knowledgeC.db
The KnowledgeC database is also found on MacOS: ~/Library/Application Support/Knowledge/
This database is responsible for tracking various activities ranging from when the device was plugged in to the orientation of the device at a given time. It’s also important to note timestamps found in the KnowledgeC.db are recorded in Mac Epoch Time (1/1/2001: 00:00:00 UTC).
AXIOM 2.8 KnowledgeC. DB Artifacts Added
| · Application Activities | · Device Lock States | · Safari History |
| · Application Focus | · Device Orientation States | · Backlight States |
| · Application Install States | · Device Plugged-in States |
KnowledgeC.db: Application Activities
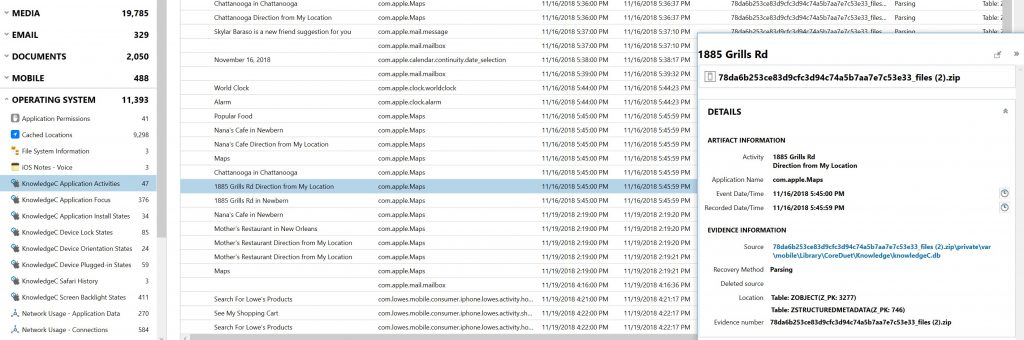
The Application Activities artifact provides a valuable look into user activities on the device at any given time. The activity data is parsed from the ZOBJECT and ZSTRUCTUREDMETADATA tables found within the KnowledgeC database.
(Examiners can always validate what they are seeing in AXIOM by looking under the Evidence Information found in the Details Panel of any artifact that’s selected. There you’ll find the source location with a hyperlink which will direct you to the raw data.)
Figure 1. KnowledgeC Application Activities view within AXIOM 2.8
In the image above, we can see where the Apple Maps application was used to navigate from the current location to 1885 Grills Rd on 11/16/2018 at approximately 5:45 PM. Other activities recorded on this particular device include: new notes being created along with specific notes being edited, email activity, and searches within 3rd party apps (Lowes in this case).
KnowledgeC.db: Application Install Dates
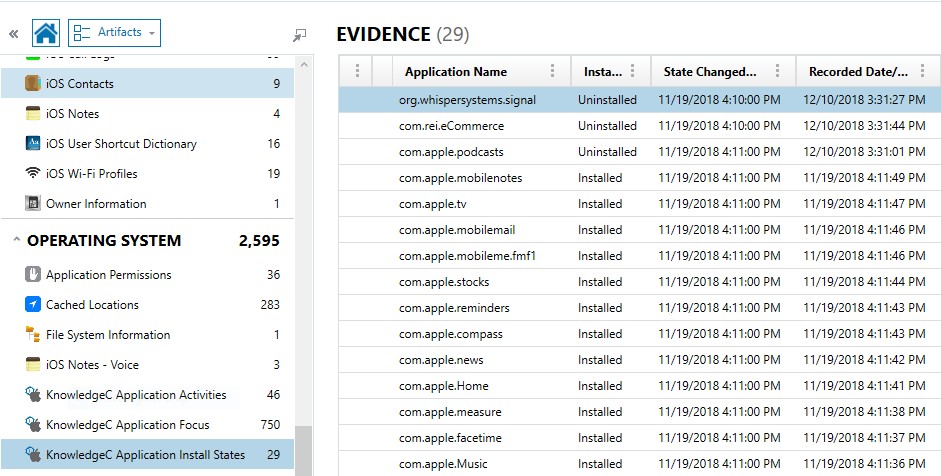
As the name implies, the Application Install Dates artifact provides analyst a timeline around when applications were both installed and uninstalled from a device. As an investigator this artifact goes a long way in proving intent when you can show a suspect deleted an app before the device was seized as evidence. Just like with Application Activities, AXIOM consolidates data from both the ZOBJECT and ZSTRUCTUREMETADATA tables from within the KnowledgeC database to provide examiners with the install state of applications.
As seen in Figure 2 below, you can see where the Signal application was uninstalled, with the recorded date providing the time stamp of the action, 12/10/2018 at approximately 3:31PM (EST).
Figure 2. KnowledgeC Application Install State view within AXIOM 2.8
KnowledgeC.db: Device Lock State
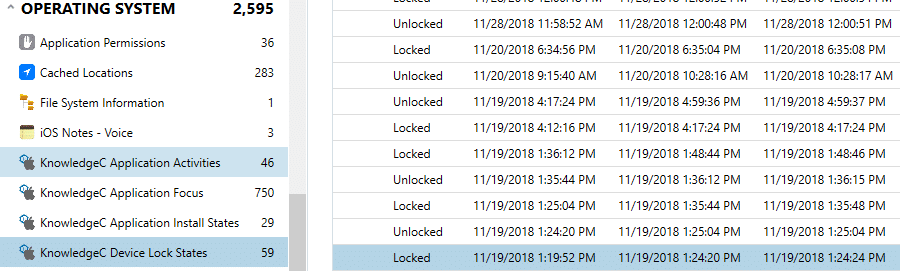
For investigations revolving around whether or not individuals were on their device at the time of an incident the ZOBJECT table parsed from the knoweldgeC.db provides valuable insight. For example, if an investigator works a vehicular homicide investigation and needs to provide evidence to support charges, having information on whether or not the screen of the device of the suspect was unlocked and potentially being used during the time in question.
Figure 3. KnowledgeC.db Device Lock State artifact view available on AXIOM 2.8
Recap
Acquisitions from tools such as a GrayKey unlock substantial amounts of file system evidence that examiners might otherwise not have access to, and with the help of AXIOM, investigators can analyze and report quickly on their findings. With the recent addition of knowledgeC.DB artifacts added to AXIOM 2.8, investigators can provide additional context for their investigations, helping non-technical stakeholders establish a better understanding of the user’s activity.
If there are artifacts you’d like to see supported in AXIOM or if you have any questions, please don’t hesitate to reach out to me at trey.amick@magnetforensics.com
If you’re already using AXIOM, download AXIOM 2.8 over at the Customer Portal. If you want to see how AXIOM 2.8 can give you a better investigative starting point, request a free 30-day trial today!