APFS File System and New Mac Artifact Support in Magnet AXIOM 3.0
Magnet AXIOM is entering its third year, so, with Magnet AXIOM 3.0, we’ve really worked hard to make it a huge release, focusing both on supporting a new file system as well as adding a plethora of new artifact support.
With a powerful new timeline explorer, redesigned media categorization (Project Vic/CAID), and added cloud support for Slack, Warrant Returns & “Download Your Information” from Facebook, and Twitter acquisitions, AXIOM 3.0 would already be a significant release. But we’re really excited to also introduce extensive support for macOS and APFS. In this how-to, we’ll walk through the APFS file system and what new Mac artifacts are supported in AXIOM 3.0.
The latest version of Magnet AXIOM is now available for customers to download! Either upgrade in-app, or head over to the Customer Portal to download AXIOM 3.0.
APFS File System Support

The Apple File System (APFS) was originally previewed in macOS Sierra (10.12) in 2016, allowing access to users via the Terminal App and becoming the defacto successor to the aging HFS+ file system in macOS High Sierra (10.13) in 2017.
APFS was built upon its predecessor, being optimized for solid-state drives with an emphasis being placed on encryption. APFS supports encryption natively while the HFS+ file system relied on CoreStorage. While APFS encrypts data at the file system level in contrast to HFS+’s encryption at the block level.
AXIOM 3.0 supports both HFS+ and APFS, with the ability to also decrypt FileVault 2-enabled images.
Once decrypted and parsed, examiners will be presented with numerous new macOS specific artifacts such as:
- OS Information User Accounts
- Network Profiles
- MRU Files
- KnowledgeC
- Bluetooth Devices
- Trash
- Quarantined Files
- Spotlight Shortcuts
- Installed Applications
- Finder Sidebar Items
- Daily.Out
- Network Interfaces
- Custom Menu Items
- Dock Items
- Bash Sessions
- Launch Agents/Daemons
- Messages
- USB Devices
- FSEvents
Investigators can also traverse the Mac file system within AXIOM’s File System Explorer, to review property list (plist) and databases found or to validate the information provided in the Artifact Explorer via source links.
MacOS artifacts will only be available in AXIOM, so contact us if you want to upgrade from IEF to take advantage of this functionality.
Here are a few of the new macOS artifacts available:
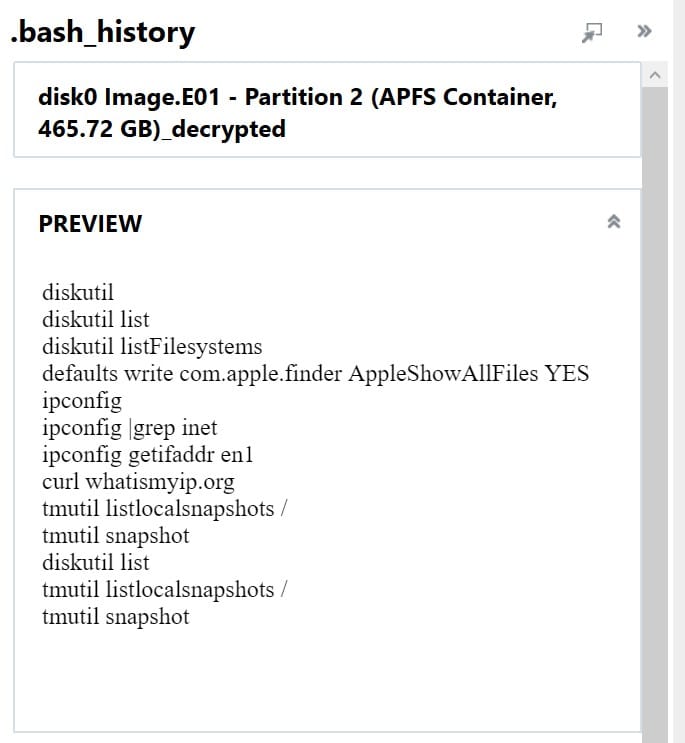
Bash Sessions (Terminal History)
Akin to command prompt on Windows, the Terminal App on macOS provides users a command line interface to the operating system. The default Unix shell for macOS is bash.
Bash history can be found /users/<USER>/.bash_sessions
AXIOM recovers information from bash sessions, including user, commands executed, and start and end time of session.
Examiners investigating bash history need to be aware of the following:
- Bash session sequences depends on when the shell was closed versus the execution order.
- Bash session time stamps are identified in AXIOM by:
- Start Date/Time Column: Term_session_id.historynewCreated
- End Date/Time Column: Term_session_ID.history
Spotlight Shortcuts

Mac users for years have had use of quick search functionality by quickly pressing the CMD ⌘+Spacebar, which opens a Spotlight search window as seen above.
Whether the user is looking for a specific file or application, Spotlight can provide a preview and allow for quick access. Typically, there are two types of Spotlight users: those who never use it or those who use it constantly for opening applications and documents.
AXIOM will display the Spotlight searches that have been run on the machine. The Spotlight Shortcuts artifact can help examiners tell the story of their investigation, down to how the application or file in question was opened. Providing such detail to a case really helps paint the picture for non-technical stakeholders such as juries, leadership, or HR.
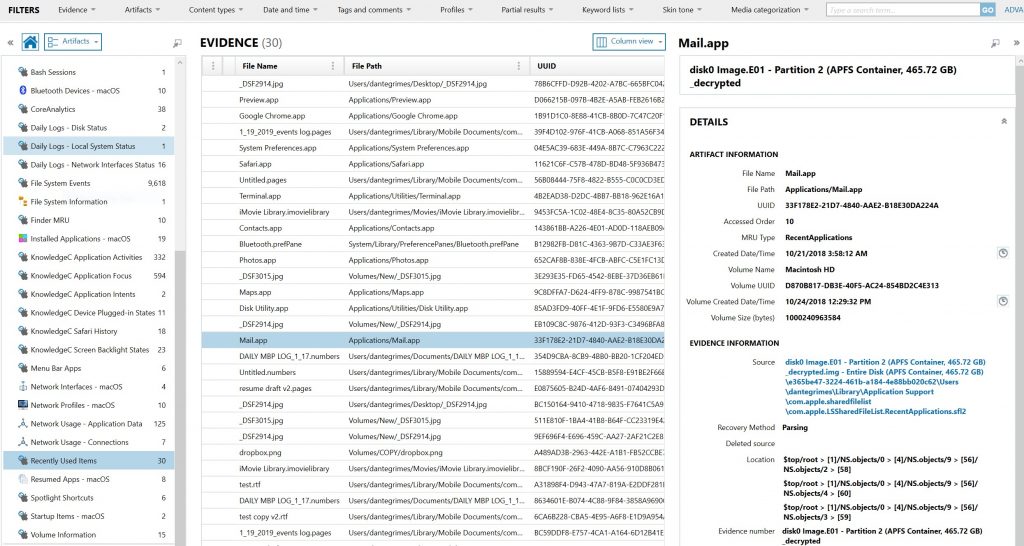
Recently Used Items & Finder MRU
The new Recently Used Items and Finder MRU artifacts for macOS assist examiners in defining a timeline of events for the mac in question. The Finder MRU and Connected Volumes artifacts provide information found from within the com.apple.finder.plist, which provides connected volumes from both external media (USB’s) or internal volumes and images. AXIOM will also provide an accessed order for the items listed.
The Recently Used Items artifact contains a whole host of information relevant for case work, including the file name of the application or file opened and the file path of said artifact. Just as the Finder MRU artifact does, Recently Used Items will also provide the accessed order, as well as the MRU type.
Artifacts being displayed by Recently Used Items are pulled from multiple locations, including several .sfl1 and .sfl2 files.
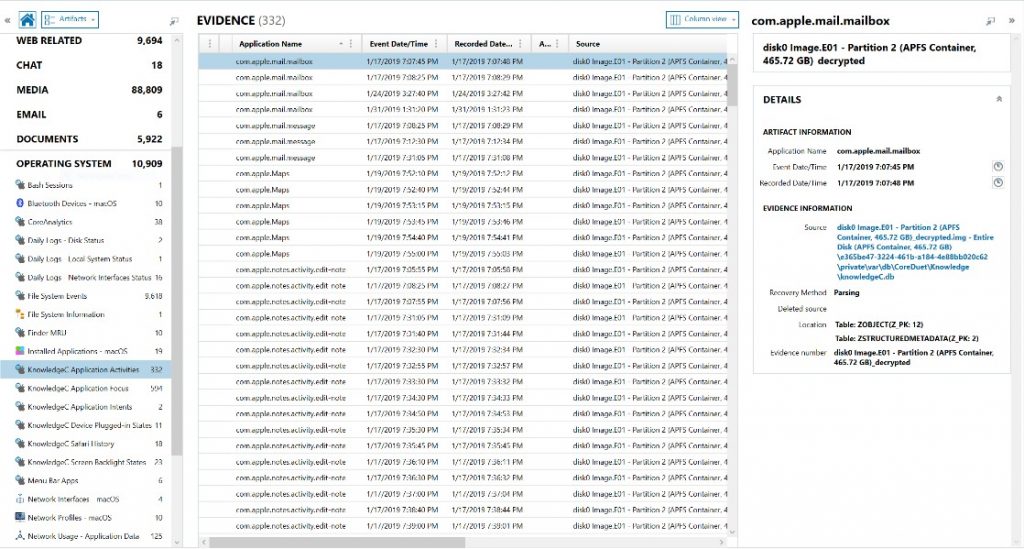
KnowledgeC
Originally released as an iOS artifact in AXIOM 2.8, we’ve now added an additional artifact for the KnowledgeC database found on macOS. Read more about the iOS knowledgeC artifact here. The database provides valuable insight for examiners around application and device usage statistics including application activity, application focus, device charging states, Safari browser history, device plugged-in states, and whether the screen was off or on.
The knowledgeC databases can be found on macOS:
- /private/var/db/CoreDuet/Knowledge
- /Users/macintosh/Library/Application Support/Knowledge
Stay tuned, we’ll be adding more artifacts found on Macs soon! If there are artifacts you’d like to see supported in AXIOM or if you have any questions, please don’t hesitate to reach out to me at trey.amick@magnetforensics.com.