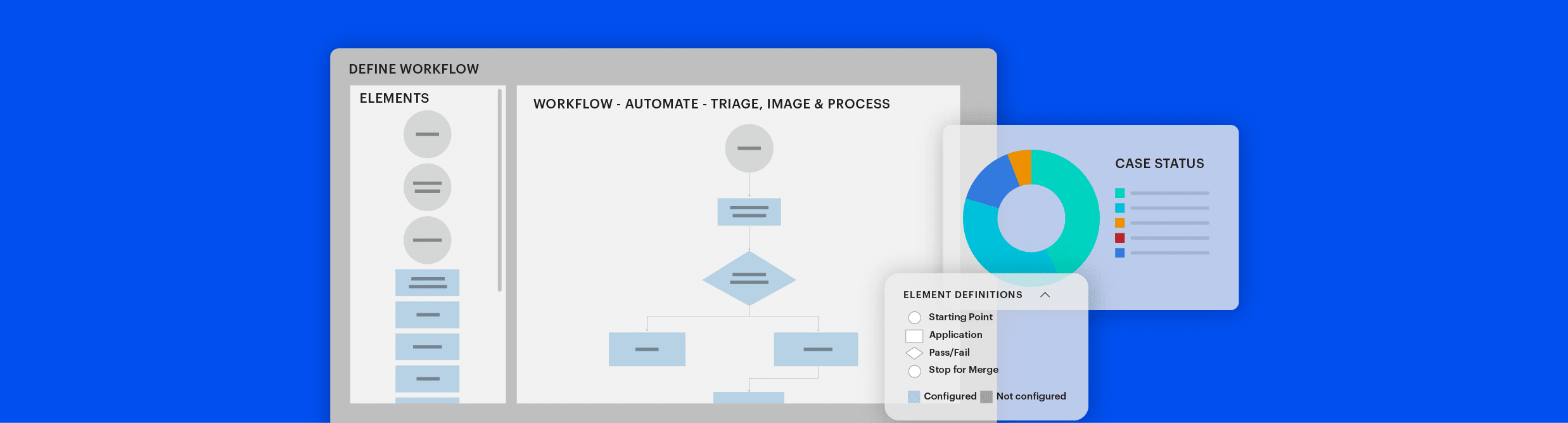
Rapid triage, ultra-simple approach
Quickly triage Mac and Windows computers, iOS and Android mobile devices, and external drives for illicit content such as CSAM, usernames, and contacts in the field or the lab with automated insights, enabling examiners and non-technical stakeholders to use Magnet Outrider with confidence.

Over 90% of criminal investigations include some form of digital evidence.¹
The average U.S. household owns 25 connected devices, including smartphones, laptops, tablets, smartwatches, etc.²
¹ National Police Council. ² Deloitte, 2021 Connectivity and Mobile Trends Survey, March 2021.
Triage mobile devices
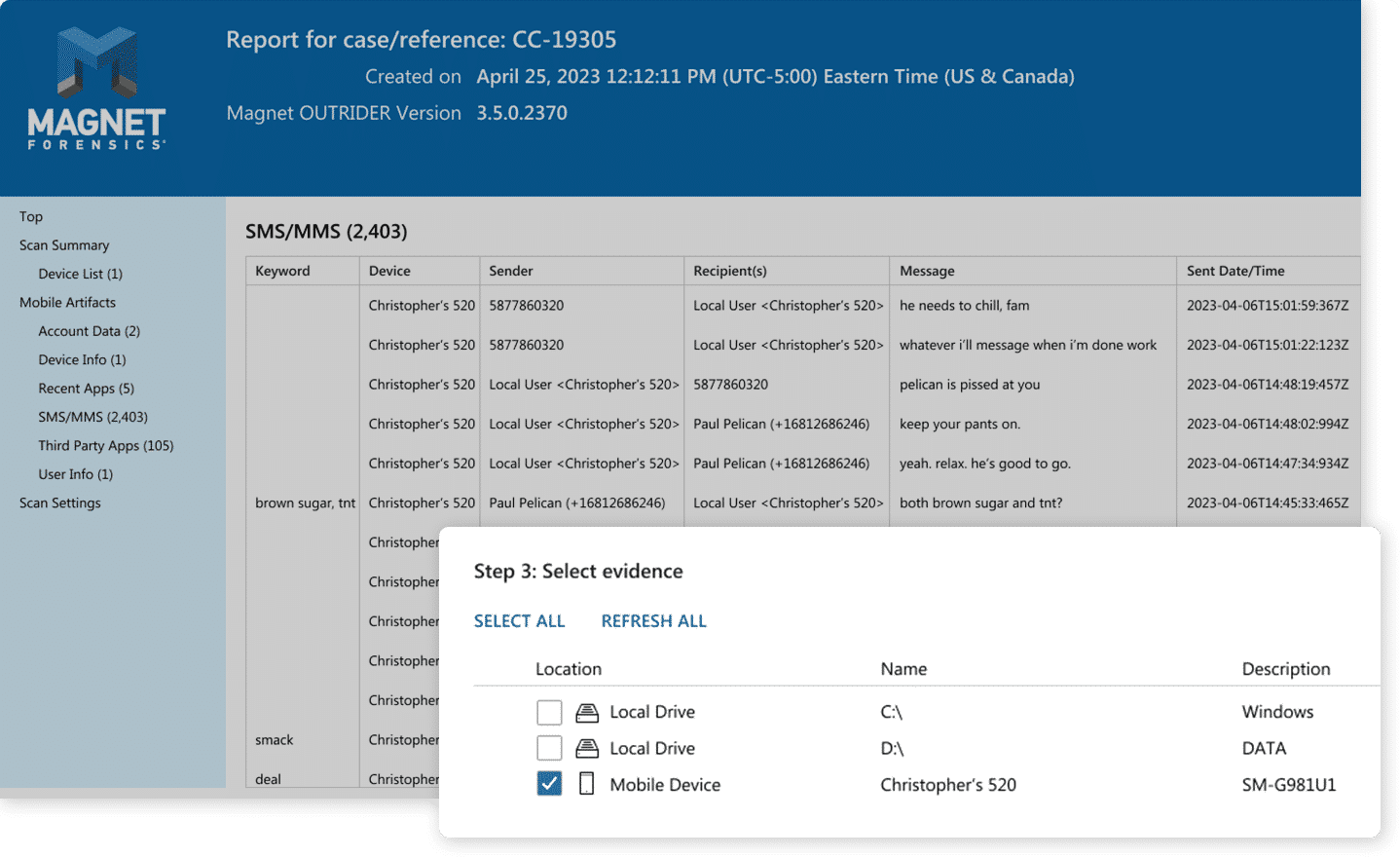
Save valuable time in the field or in the lab by using Magnet Outrider to quickly scan iOS and Android mobile devices and automatically uncover SMS/MMS messages, illicit apps, device ID, recently used apps, contact list, call logs, and more, in minutes.
Key takeaways
- Lightning-fast mobile scans in under a minute.
- Scan multiple mobile devices at the same time.
- Use keywords to filter and scan for specific evidence relevant to your case.
- Detect the presence of secure folders and multiple user accounts.
Identify actionable evidence fast
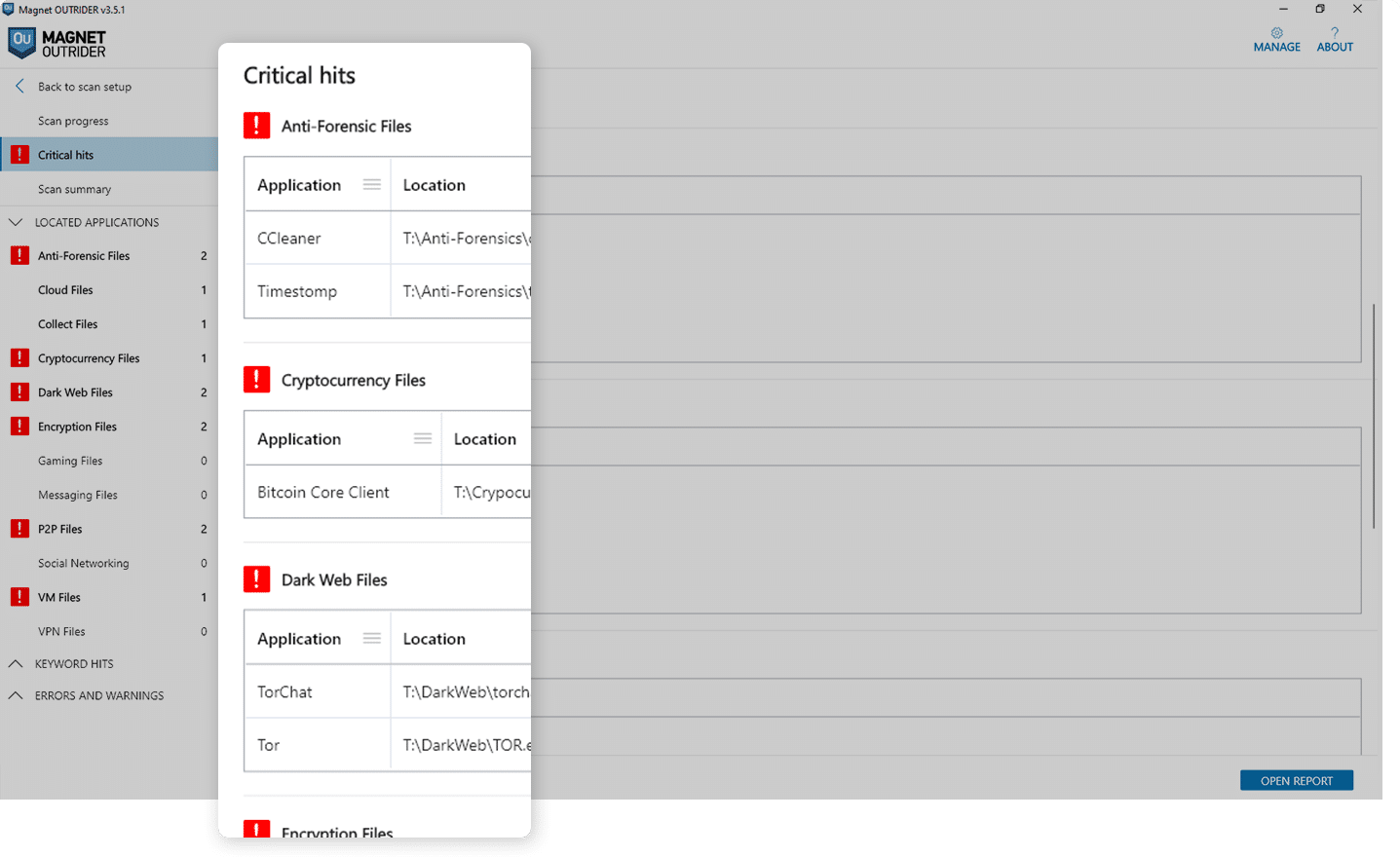
Get your team real-time intel for interviews, warrants, and seizures by uncovering actionable evidence from mobile devices, computers, and hard drives in under six minutes without having to perform a full extraction. Scan internet browser history, text messages, recent activity, and account information for keywords, specific URLs and file names from an imported NCMEC CyberTip report, or load targeted URLs and keywords into Outrider that are relevant to your case.
Key takeaways
- Use MD5 and our patent pending MAG24 hash matching to locate files from known hashsets like VICS or CAID.
- No more manual scans: Outrider automatically counts and displays the number of hits during a scan.
- Scan multiple devices for evidence in less than six minutes.
- Outrider’s first Gen CSAM detector identifies CSAM that isn’t yet known to authorities.
- Load custom keywords or NCMEC reports to find evidence fast.
Get started quickly
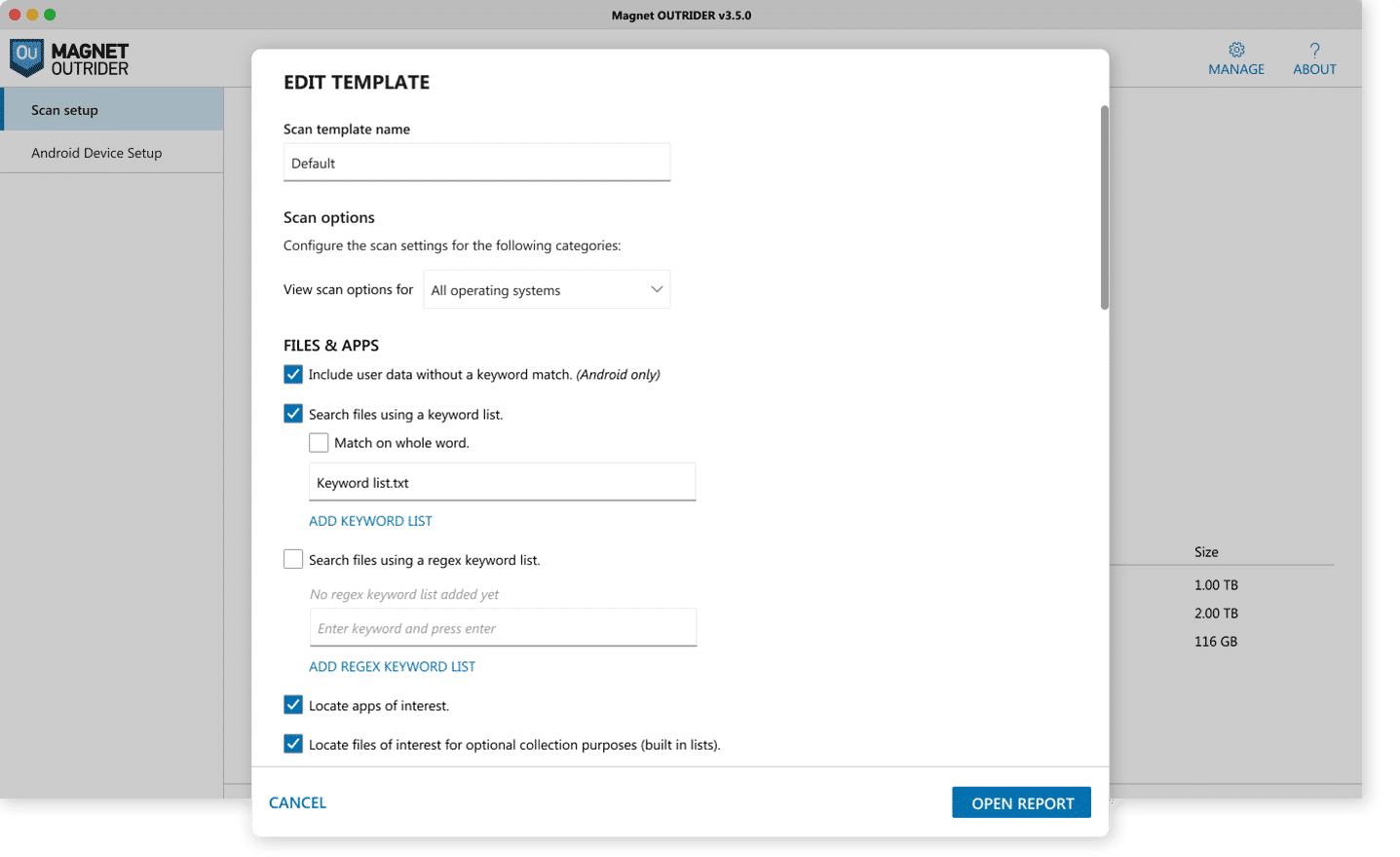
Outrider was designed for speed and simplicity. As a preprogrammed, turnkey solution, Outrider enables even non-technical stakeholders to confidently use Outrider with its preconfigured artifact categories that automatically count and display the number of hits during scans. In less than three steps, you can start running scans in the field or in the lab.
Key takeaways
- Get Outrider up and running in less than three clicks.
- Detect known CSAM in a fraction of the time (minutes) with pre-programmed Child Rescue Coalition CSAM detection technology (Neula).
- Easy-to-use interface to enable non-technical users to confidentially run scans.
Capture live system artifacts and memory
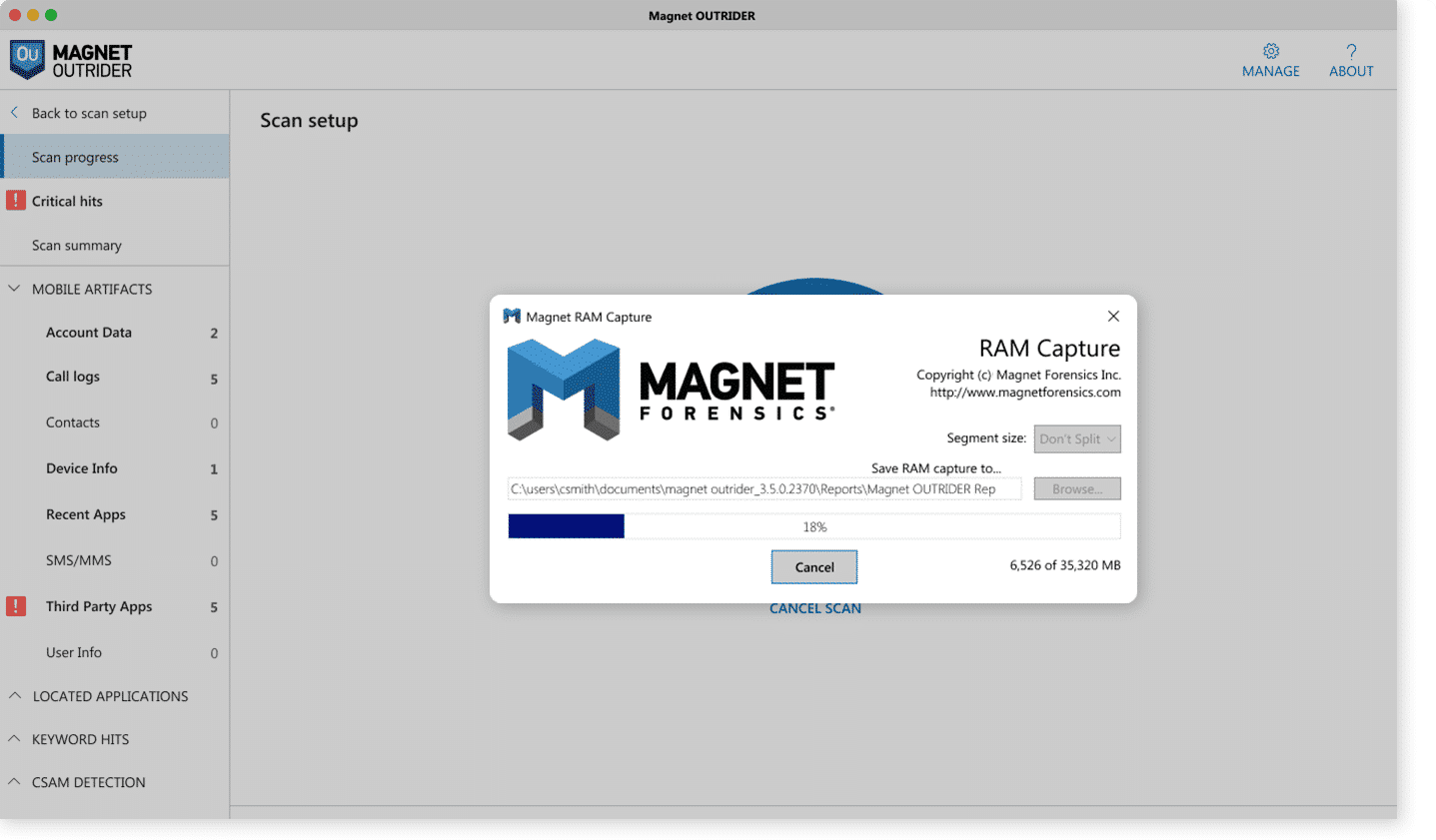
Quickly gather another layer of information by analyzing live system artifacts and processes actively running on the device. Gather additional browsing history, access files that have been unencrypted, and encryption keys.
Key takeaways
- Perform live system scans with option to collect:
- Valuable operating system artifacts.
- Capture RAM.
- Take a screenshot of the desktop.
- Obtain the external IP address for the system.
- Leverage insights to support probable cause for additional search warrant requests.
Related resources
Recover deleted data and investigate digital evidence from all your sources, all in one case file.
Request your free trial today
Try Magnet Outrider today
Start your free trial today and put Outrider to the test in the field and in the lab.