
CSAM: Arming Investigators With Tools and Tips to Combat Child Sexual Abuse Material
Since Magnet Forensics’ inception, we’ve been dedicated to our mission statement: Seek Justice and Protect the Innocent. Combatting Child Sexual Abuse Material (CSAM) is a big part of that. The ethos and culture of Magnet is one of service to our customers, and with many folks joining us as they transition from the public sector to the private sector, we continue to develop solutions to help investigators bring justice to those who victimize children.
As Magnet has grown, our ecosystem and product capabilities have continued to evolve, so in this article we’ll discuss both products and features found within various products that help aid agencies in their CSAM investigations.

Triage for CSAM Investigations
OUTRIDER has become an instrumental tool in the workflow of many agencies, especially when fast results are needed in the field. OUTRIDER includes several features which are targeted at helping law enforcement investigators locate files of interest and commonly used applications found in CSAM investigations.
Often, law enforcement triages devices located during a consent-based encounter or via a search warrant. The ability to triage computer-based evidence on-scene and quickly locate information that can be leveraged during initial interviews can be beneficial to the ultimate outcome of an investigation. With its ease of use, non-technical investigators can be up and running within minutes using OUTRIDER, which currently supports Windows, Mac, and Android devices—with more platforms coming soon. OUTRIDER utilizes Child Rescue Coalition’s Neula technology to quickly detect fragmented pieces of CSAM and has block-hashing technology as a core component.

Additionally, OUTRIDER can ingest NCMEC CyberTips for identifying matches found on the device(s) being scanned. The U.S.-based nonprofit the National Center for Missing & Exploited Children (NCMEC) said it had recorded a 35% increase of reports in 2021 from 2020, with over 29 million CyberTip Reports being filed.
During the course of a CyberTip investigation, it is not unusual to locate a variety of electronic storage devices. OUTRIDER can be used to quickly triage those devices and locate screen names, file names, files hashes, internet protocol (IP) addresses, and other information that may have been imported from the CyberTip report. This feature allows investigators to determine which devices may have been involved with the activity that led to the CyberTip report being generated allowing them to focus their efforts.
Live Scan
OUTRIDER was designed for use as a triage tool and includes numerous features that are mainstays of live system analysis. To support this, OUTRIDER can be run from an external device such as a USB flash drive or external solid-state drive (SSD), meaning that you can take a preconfigured external storage device with OUTRIDER and connect it to a powered on and running Windows or macOS computer that you encounter.
In addition to the operating system artifacts collection, OUTRIDER provides the option to collect physical memory (RAM), perform a check for known full-volume disk encryption, save a screenshot of the desktop, search running processes, scan connected network devices, identify keyword hits found within web browser history, and obtain the IP address of the machine being analyzed. Within the Live System scan settings, investigators can select from collecting operating system artifacts listed in Figure 1 below.
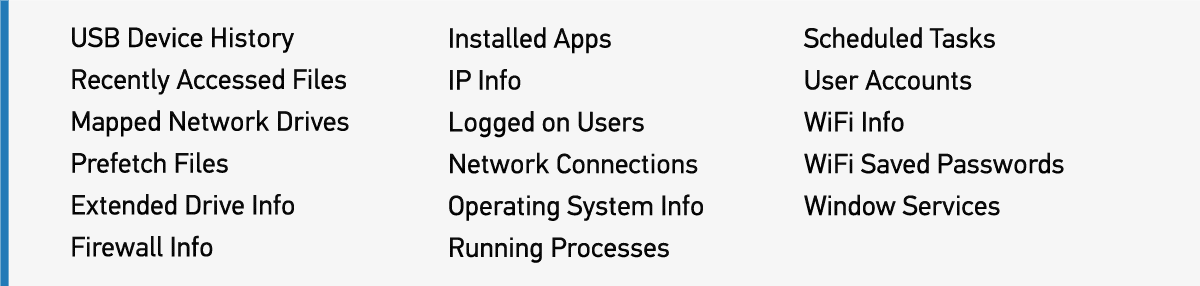
In addition to live system artifacts that OUTRIDER can collect, investigators will also be able to quickly identify applications of interest. These programs are grouped together for review by:

Dead Box and External Devices
OUTRIDER provides flexibility with options for live systems and capturing volatile data (discussed above), along with a bootable option for triage of any dead-box devices that are discovered. For this use, OUTRIDER can be configured for use from a Windows-To-Go bootable device. This allows examiners to power on any non-running computers and boot into a Windows environment that has previously been configured. OUTRIDER will automatically detect it is running in a bootable environment and a Drive Manager option is available to mount available storage devices in a read-only state.
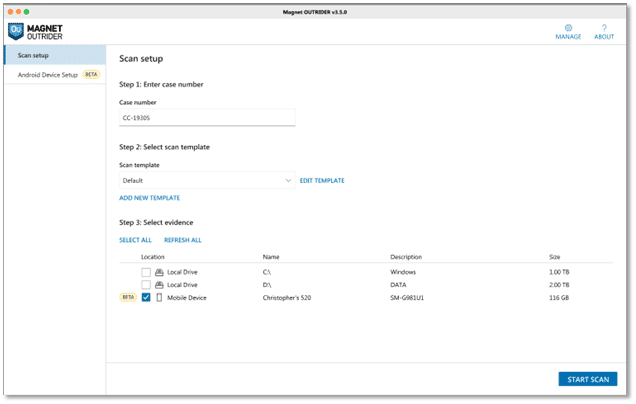
Investigators can boot a powered-off suspect device into an environment they control, mount the internal storage from that suspect device in a read-only state, and then utilize all features available in OUTRIDER to scan that device.
With external storage devices being so commonplace, investigators often find themselves needing to perform triage functions against USB flash drives or external hard drives, and this is the final use case we’ll discuss for using OUTRIDER.
In a scenario such as this, OUTRIDER can be run from the investigator’s laptop, and external devices connected via write-blocker for scanning. While operating system artifacts may be less of a concern here, other features included within OUTRIDER for locating items of interest related to keyword or hash matches, or data from CyberTip reports, and the CRCs block-hashing technology to quickly identify known files of interest, can all be leveraged to quickly identify external storage devices which may be relevant to the investigation.
For agencies who have adopted automation technology like Magnet AUTOMATE, OUTRIDER can easily be incorporated into workflows, allowing for quick triage of devices before further analysis. This can help to identify a subset of devices that may have been submitted in any given case to best allocate resources for processing with forensic tools.
Processing and Analysis for CSAM Investigations
Many of the product offerings from Magnet Forensics include functionality designed to assist examiners with the location and categorization of CSAM material within their data sets.
Below, we will walk through some of the features available within Magnet AXIOM to support examiners in their efforts.
Media Recovery
Once the electronic evidence has been submitted for analysis, a typical workflow in a CSAM investigation involves the acquisition and analysis of the data contained. With CSAM investigations, we have all found illicit material is distributed using an almost endless variety of methods, and the offenders in these investigations have shown to evolve with technology to come up with new ways to achieve this.
One of the constants with CSAM investigations is the need to locate media files. Whether you are talking about a CSAM investigation stemming from a NCMEC CyberTip involving contraband material shared through a Dropbox link, a parent reporting their child having shared self-produced material via a chat application, or even someone using any of the various file sharing applications, the recovery of picture and video files is a key requirement.
Magnet AXIOM incorporates media recovery options for many industry-standard video and picture file types, including common RAW file formats used by digital cameras. RAW file formats, as opposed to something like JPG, are typically unprocessed or minimally processed files from the image sensor of a digital camera. These file formats vary widely based on the manufacturer, with many brands implementing their own file format to meet the needs of their devices. The need to search for less common media file types arises in many CSAM investigations and examiners with knowledge of a less popular file type that could potentially be involved in an investigation can leverage the SEARCH FOR CUSTOM FILE TYPES feature within AXIOM Process.
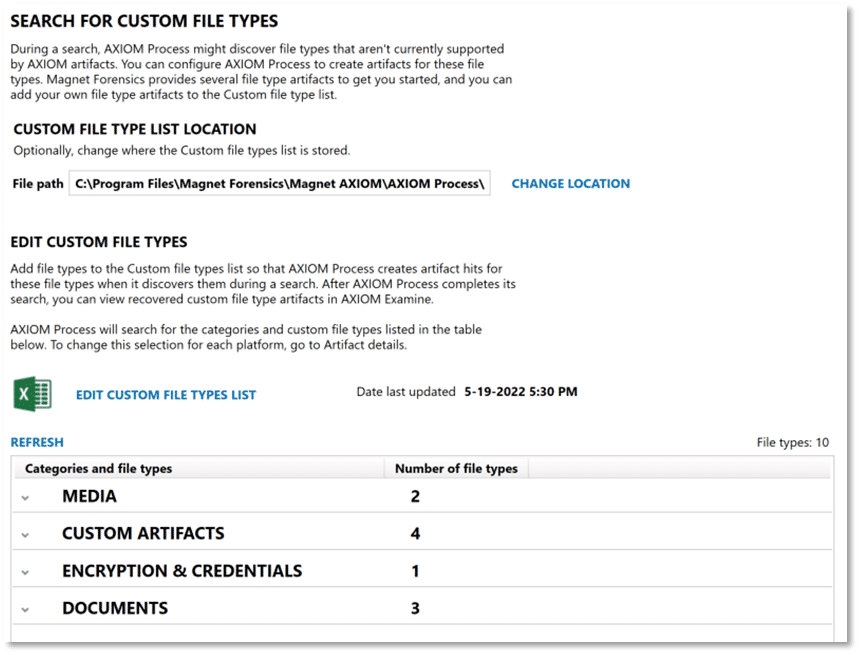
At a basic level, this can be used to search (via parsing active data) for a specific file extension. If desired, examiners can provide matching header and footer information for those same file types to perform carving of data for potential matches. This provides a mechanism for examiners to tailor AXIOM’s media recovery capabilities to meet the needs of a specific investigation or application that is in use.
Media Explorer
Longtime users of Magnet AXIOM will remember the introduction of Media Explorer, originally introduced with AXIOM 5.0. While prior versions of AXIOM included features useful in the review and categorization of media, providing a dedicated explorer within AXIOM Examine for this work improved efficiency—and offers several additional benefits.
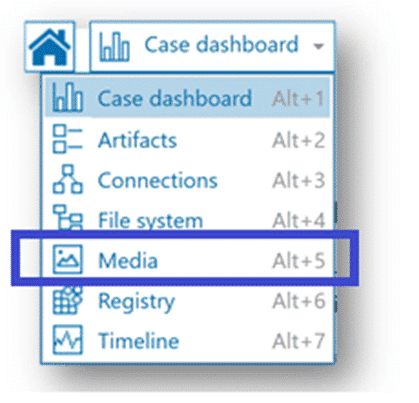
Like other post-processing options in AXIOM Examine, Media Explorer must be built prior to use. Once the Media Explorer is ready for use, there are a number of filter criteria available from the navigation pane with options uniquely suited to media review. For example, let’s say that during case processing, AXIOM recovered a number of image files with the .crw extension. We determine this is the file extension used by certain Canon digital cameras for their RAW file format and that our suspect in this scenario is using a Canon digital camera. We can use the filter options in the Media Explorer’s Camera Details section to only show images where the EXIF data indicates a camera make of Canon.
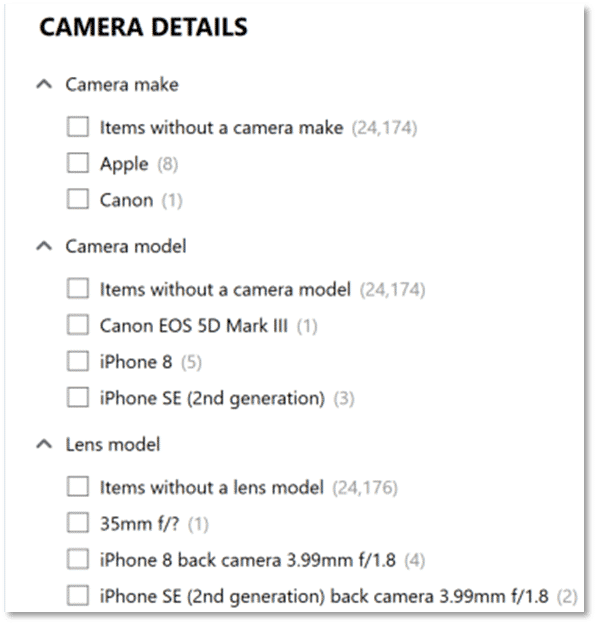
The filtering options available can be stacked, if we knew that our suspect was not only using a Canon, but a Canon EOS 5D Mark III, we could add that model information to further narrow the scope of items shown in the Media Explorer.
In addition to camera details, there are other options within Media Explorer to filter results based on criteria that may be of interest in your investigation.
The default behavior for Media Explorer is to only show a single instance of any file, so if you have duplicates of an image or video stored in various locations across your evidence items, the Media Explorer is stacking those matching results based on their MD5 or SHA1 hash values. With stacked items in Media Explorer, examiners will see a count below the thumbnail showing how many binary copies were located. Clicking on the stacked item icon will open a window displaying the file name, evidence source, and path for each of the duplicate files.
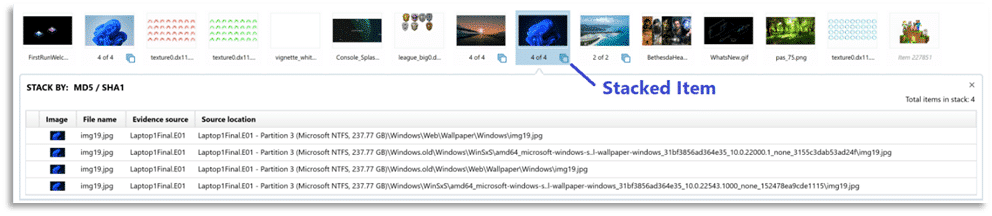
An added benefit of hit stacking is when applying a tag or media categorization to a stacked item, it will apply the same classification to all copies of the file, thereby speeding up the process. To learn more about the Media Explorer and to see it in action check out our video:
Officer Wellness Tools
Commitment to our mission includes not only the victims of crimes but also to the investigators aiding in bringing those to justice to answer for their crimes. In CSAM investigations, this can often take both a mental and physical toll on officers, which can lead to burnout and the need to separate from the unit, or from law enforcement all together.
At Magnet, we’re working hard to provide officer wellness features across all our product offerings to help protect investigators from unnecessary exposure to CSAM, where it can be avoided. Founder and CTO of Magnet (and former police officer), Jad Saliba provides his thoughts on officer wellness and why it is so important:
AXIOM Examine includes a set of features collectively referred to as Officer Wellness features. These include options to automatically blur from view any media that was categorized as illegal via hash match or manually by examiner grading.
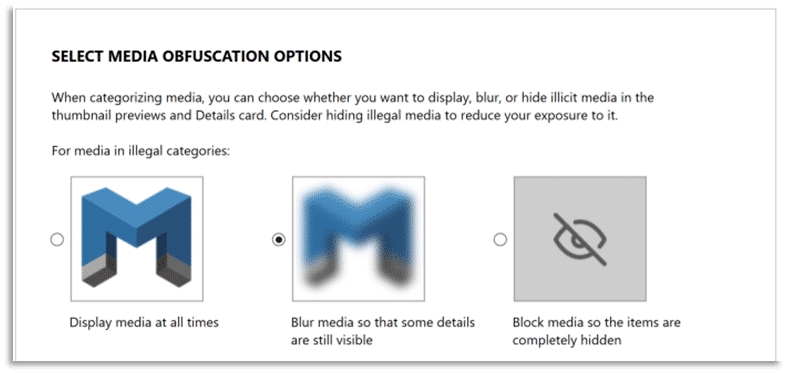
Examiners have the choice to turn this feature off entirely, or they can choose to block media items categorized as illegal, so they are completely hidden. The Media Explorer includes a link for SET UP REMINDER that will open the Manage media categorization window, shown here.
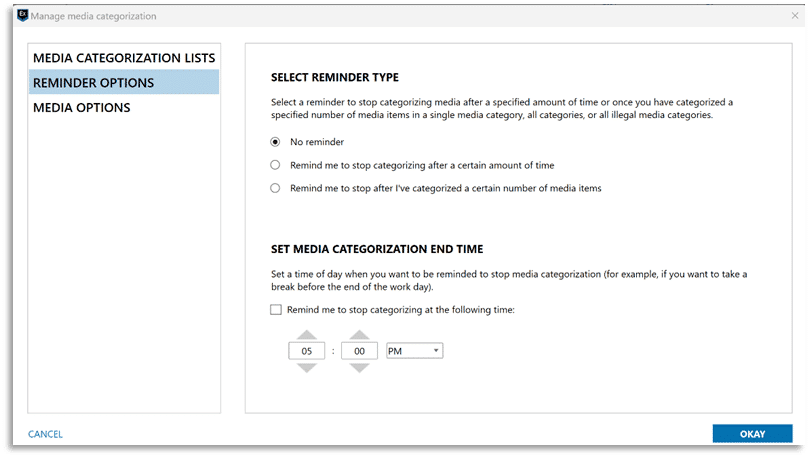
Examiners can adjust settings related to hash sets utilized for media categorization, as well as enable reminder options when using the Media Explorer which can be used to let AXIOM Examine notify them after they have performed media grading for a predetermined length of time or after reaching a designated number of graded items. Additional options associated with the Officer Wellness features include a setting to automatically mute audio from any video that is played via the built-in media player in AXIOM Examine.
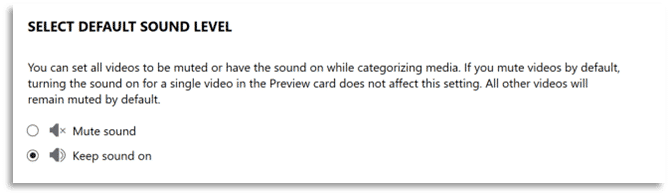
Hit stacking (discussed above) pairs well with the use of hash datasets from Project Vic or CAID along with PhotoDNA integration available in AXIOM. Examiners using these technologies benefit from having previously identified CSAM material categorized appropriately, potentially limiting exposure to illicit material.
After using all the available options to automate media categorization, examiners are invariably left with items to review manually. Other media-tagging features within AXIOM Examine include keyboard shortcuts for categorizing media and an option to apply a predefined category to all uncategorized items that are currently displayed with one keystroke. Examiners can also scrub across a video thumbnail for a playable preview of the content. The use of keyboard shortcuts, video scrubbing, and bulk categorization can be great time savers when performing manual categorization of media items. If you want to see the officer wellness features in AXIOM, check out this video:
CRC Data Exports
In the fall of 2018, Magnet Forensics and Child Rescue Coalition (CRC) announced a technology integration using the extensive catalog of data from CRC’s Child Protection System and the analytic capabilities of Magnet AXIOM.
This integration allows CSAM investigators to provide CPS platform data for an investigation to digital forensic examiners to use in searching case-specific identifiers which may be found on the digital evidence items which are submitted for analysis in an investigation.
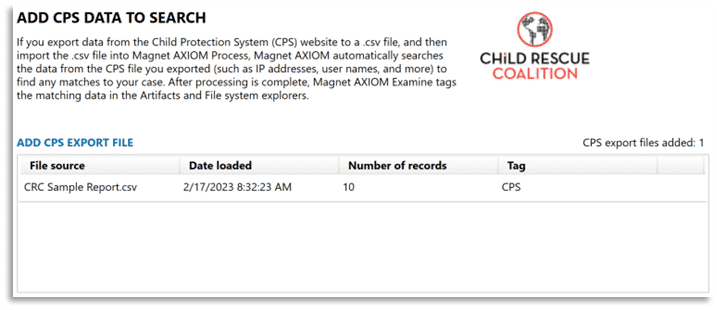
A CPS data export can be added via AXIOM Process during initial case processing, shown above, or can be added to a previously processed case in AXIOM Examine from the Process menu and selecting the option to Add a CPS Export file. Additionally, the Case Dashboard in AXIOM Examine includes a card for CPS DATA MATCHES which can be used to review matches to any CPS data matches or to import a CPS export file to a case.
Magnet.AI
Magnet.AI uses machine learning to automatically categorize pictures depicting content from a variety of categories which may be of interest in a CSAM investigation.
Magnet.AI media categorization features can be used to search across data sets for things like bedrooms, child abuse, human faces, and nudity—among others. Updates to Magnet.AI include support for GPU acceleration during media categorization and leveraging the power of NVIDIA-based graphics cards to improve performance.
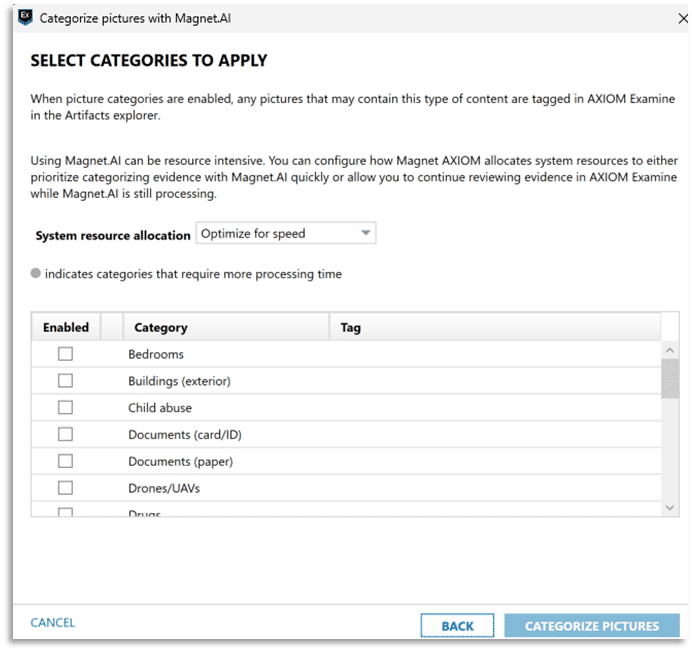
The use of Magnet.AI to assist in locating images depicting certain content across the many images which may remain for manual review by an examiner can greatly reduce the exposure to illicit material.
Through Magnet’s partnership with Thorn, Magnet AXIOM leverages Thorn’s CSAM Image Classifier alongside Magnet.AI. Thorn’s CSAM Image Classifier is a machine-learning classification model that offers investigators another way to quickly identify victims of child sexual abuse by automatically categorizing illicit pictures and videos, minimizing the manual effort required to review images in CSAM cases. This both improves time-to-evidence promotes officer wellness.
Find Similar Images
Additional capabilities have been added around content-based image retrieval (CBIR) for quickly identifying and grouping visually similar images found within the digital evidence, or for cross-referencing with an image not originally found within the processed evidence.
Magnet.AI finds similar pictures based on a picture’s general attributes, rather than specific details such as small objects or faces. Use Magnet.AI to help you find other pictures that are similar, such as pictures of the same room or pictures with similar scenery.
To use the Find Similar Pictures, the examiner must first open Examine and build picture comparisons by choosing Tools > Build picture comparison after opening a case. Unlike building a Timeline or Connections with AXIOM, this process may take longer depending on your system hardware specifications. Examiners wishing for picturing comparison, connections, and timeline to be run automatically after processing can navigate to Tools -> Settings to enable the post-processing options they wish to have run.

Once the process has completed, you can select a reference picture to find similar pictures.
1. In AXIOM Examine, from the Artifact or File system explorers in Row, Column, Classic, or Thumbnail view, right click on a picture
2. Click Find Similar pictures and choose Select picture
Figure 17: How to find similar pictures in AXIOM Examine.
3. AXIOM Examine will then display matching results in the Thumbnail view in the Artifacts explorer and will sort the pictures automatically so that the most similar pictures appear at the top. To see this feature in action, check out the Find Similar Images video found:
Hash Sets Manager
The Hash Sets Manager is a standalone tool with full integration in AXIOM and AXIOM Cyber for centralized management of hash data sets. Once enabled within your installation of AXIOM or AXIOM Cyber, the synchronization of hash dataset information will occur transparently and allow you to both include items of interest and exclude known-good files.
Features are available in the Hash Sets Manger to protect certain hash sets from unintended modification and for uploading new media categorization from a case to your centralized database of hashes that can be shared amongst off of you AXIOM installations.
Working Smarter Not Harder to Combat CSAM With Automation
Between agencies facing wide-ranging backlogs and the shortage of budgets and manpower, many have adopted a philosophy of working high profile, priority cases while other cases sit due to the sheer volume of forensic analysis requests entering the lab.
Every examiner knows the pains of scheduling your days, nights, and weekends to work around when you need to be available to stop by the lab to simply kick off the next part of the investigative workflow, which in the long run has implications on officer wellness. Leaving cases partially processed over the weekend leaves expensive forensic towers idle, often with just a few mouse clicks needed to continue the workflow.
Ultimately, Magnet wants to help agencies maximize their staff’s time and expertise to actually investigating cases versus routinely completing mundane tasks that eat up limited personnel bandwidth.
This is where Magnet AUTOMATE can help.
“How we used to do digital forensics” is no longer fit for purpose in a world where data volume and complexity have ballooned…a more integrated approach could be transformative.
Dr. Gillian Tully, UK Forensic Science Regulator, 2019 Annual Report, February 25th 2020
Automation technology is used in countless ways already, from assembly lines utilizing robotic process automation to homes equipped with Smart Hubs. For iOS users, navigating to the Shortcuts.App allows for quick workflows, ranging from getting your device’s current IP address to showing account information, calculating tips, or anything else a user can dream up.
These workflows string along a series of commands that otherwise would take additional time for the user. Applying this same methodology, Magnet AUTOMATE relies on predefined (agency-specific) workflows that can immediately begin the imaging or processing of evidence as cases are queued in the system. The tool is intended to not replace your forensic toolbox, but help orchestrate it, maximizing and providing a return on investment the agency has spent on expensive forensic workstations that aren’t being utilized to their full potential when left idle between processing tasks.
“We get digital evidence to our detectives in hours or days, and not the weeks or months it’s been for years with the massive amount of digital devices.”
Chad Gish, Criminal Investigations Division Detective, MNPD
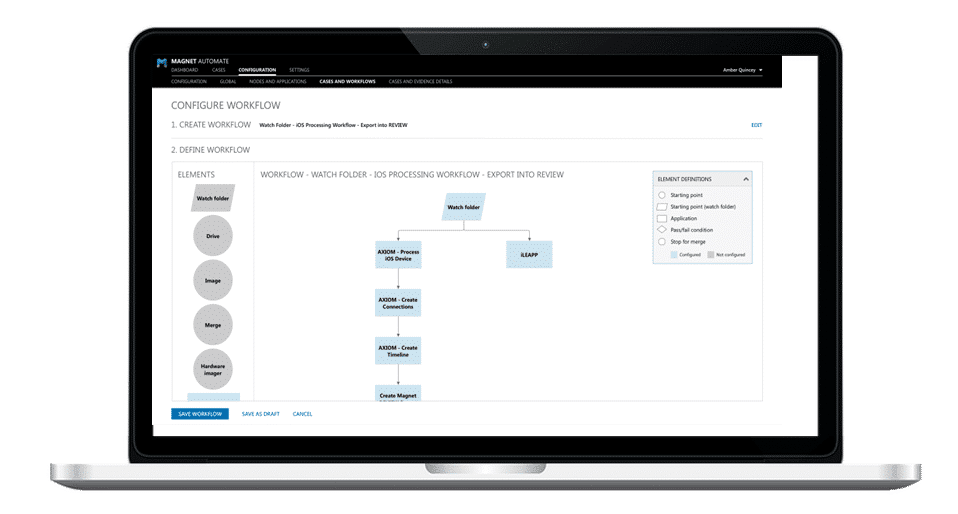
Just like we previously mentioned with the Shortcuts.App, Magnet AUTOMATE’s workflow builder can be utilized to create workflows ranging from very simple to as complex as an agency would like to create. The AXIOM Processing Engine that agencies have come to depend on for parsing artifacts from digital evidence is included with Magnet AUTOMATE, but users can add any tool they have CLI access too, custom scripts, or popular tools such as iLEAPP, aLEAPP, or X-Ways.
For ICAC-based workflows, agencies can also utilize Project Vic / CAID hash sets, keywords, and Magnet.AI to help identify evidence for the investigation, just as in Magnet AXIOM. Once processing is complete, AUTOMATE can then export results out, either via standard reports, Portable Case, AXIOM Casefile, JSON exports for use with other tools such as Griffeye, or to Magnet REVIEW—allowing investigators to immediately access the evidence for their cases.
Ultimately, Magnet AUTOMATE allows examiners to focus on the important task of evidence analysis and not spend countless hours completing mundane tasks, or waiting for one task complete, simply to kick off the next one.
Closing Thoughts on Fighting CSAM
Whether you’ve recently adopted Magnet products into your ICAC workflows or you’ve been a longtime supporter, we hope you’ve found the evolution of our products and features within those products dedicated to ICAC investigations useful.
We have an exciting roadmap ahead and look forward to sharing it with you. If you’re looking for additional resources for your ICAC investigations make sure to check out Child Rescue Coalition’s GridCop, which is free for law enforcement to utilize. It helps identify users offering to participate in the sharing of CSAM within your jurisdiction.
Additionally, Operation Light Shine created the Intercept Task Force aimed at combatting human trafficking and CSAM, they have valuable resources for agencies looking to expand their ICAC units.
If you haven’t had the opportunity to try Magnet AXIOM or OUTRIDER don’t hesitate in requesting a trial license.