Using F-Response and Magnet AXIOM to Conduct Enterprise Investigations
One major difference between law enforcement and corporate investigations is that corporate investigations may span across several countries or regions whereas LE typically deals with cases within their own city/state/region/etc. One of the challenges of corporate investigations is that you won’t normally have examiners in each of these locations so there is a requirement to handle some of these cases remotely over a network.
Gaining disk or file system level access to remote machines can be challenging if you haven’t done it before. There are several ways to do this, but using a tool like F-Response Enterprise Edition can be quite helpful in an investigation that requires remote access. F-Response is a network connectivity tool that establishes a read-only, secure connection to a remote host, enabling an examiner to acquire or analyze physical disks and volatile data such as memory as if they were attached to your local forensics machine. F-Response is also tool-agnostic, meaning that once it establishes the remote connection, you can use any forensic tool at your disposal to conduct your investigation, including Magnet AXIOM.
F-Response has several editions of their products available depending on your use case. Tactical uses two USB devices, one acting as the subject and the other acting as the examiner to help establish the connection, or they have larger deployments for enterprises or consultants requiring connections to multiple hosts or acting covertly to a subject’s computer.
Today we’re going to walk through using F-Response Enterprise to connect to a remote machine on my network and analyze its contents.
To see a walk through of Magnet AXIOM and F-Response, watch our video:
Setting up F-Response Enterprise
The first thing you’ll want to decide is whether this will be a covert investigation (the employee doesn’t know you’re investigating their system) or not. In some cases where you’re investigating the employee, this will be expected, other times you may be investigating the system, not the user, and it might not matter whether the employee knows or not (ex. malware/intrusion). For covert investigations, you’ll need to have the agent or Subject executable pushed to the target machine by an admin (either local or domain) or have it pre-installed across the enterprise. If being covert isn’t a concern, you can simply deploy a GUI executable from the F-Response Management Console and then run it on the subject system.
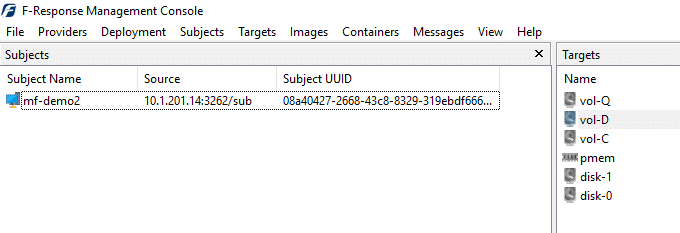
Start the F-Response License Manager on your forensics machine and have the Subject executable on the remote machine point back to the License Manager on your examination machine (I had to create a Windows firewall rule to allow inbound TCP connections on the port I chose to use for the License Manager), or connect a dongle license directly to the target. Once the license is detected and up and running and the service is started, you should be able to see the host in the F-Response Management Console. Double-clicking on it will reveal the disks and volumes available to you for that given host.
Right-clicking on any of the Targets on the right and choosing to “Attach Target,” will allow you to mount the disk or volume on your local examination machine. Once mounted, it will appear as a local drive and you can then analyze it with whatever tools you prefer to use for the given case.
Acquiring and Analyzing with Magnet AXIOM
In this case, I have mounted disk-0 and pmem to my forensics machine. Disk-0 represents the primary physical disk on the remote machine, disk-1 is a USB drive connected to the remote machine, and pmem is the remote computer’s physical memory mounted to my system for analysis. You can also see that F-Response gives you access to any given volume on the available disks as well so if you only need to access the logical volume, you could choose to mount it instead of the physical disk. Using AXIOM at this point, you can choose to either acquire or directly analyze either of these sources along with anything else that may be connected to your system.
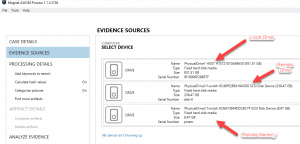
To acquire the remote evidence in AXIOM, go to: Evidence Sources, choose Computer, then Acquire Image. As in the above screenshot, I am presented with three options. The first is my local hard drive, the second is the physical hard drive of the remote computer mounted as disk-0, and the 3rd is the volatile memory of the remote machine mounted as pmem. I have selected to acquire the physical memory first (8 GB) and then instead of acquiring the entire remote drive (250 GB), I will simply analyze it remotely looking for any artifacts of value.
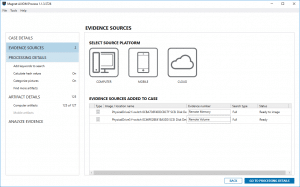
Both evidence sources get loaded into AXIOM and the order of operations will first acquire the physical memory and then process both the disk-0 and memory, because we chose not to acquire disk-0.
Once complete, we’ll get a RAW image of the memory as well as a completely processed case consisting of any artifacts pulled from both the remote memory and disk-0. I would expect the acquisition and processing to take longer as it is conducting this over the network but this can be quite helpful if the remote machine is at another office or location that is not readily accessible to the examiner.
There are several other use cases that you may want to try depending on the type of investigation you’re conducting and the time available. We are going to post two use cases for F-Response and Magnet AXIOM over the next week, so keep an eye out for: An investigation requiring a targeted acquisition; and An investigation using preview with no acquisition.
Any questions? Send an email to Jamie at jamie.mcquaid@magnetforensics.com.