Three Newer Things that May Surprise You about iOS Forensics

I recently delivered a webinar, “Apple’s Tween Years: iOS’ Maturation from 10 through 11 and into 12,” followed by an iOS and cloud forensics focused trip in New Zealand, Australia, and Singapore. From talking with examiners at these events, I realized that the lecture content contained three “surprises” that could affect forensic investigations. I wanted to take a moment to share those items that may be important for you to know.
1. Don’t Remove the SIM Card if You Want to Use Biometric Unlocking
SIM card removal from a locked iOS 12 device disables Touch ID and Face ID. It is important to note that if the SIM card is removed with the device in an unlocked state, Touch ID and Face ID are still available. Interestingly, SIM card removal is not listed as a situation that requires a passcode in Apple’s iOS Security Guide.
This can be an issue when an organization’s Standard Operating Procedures (SOPs) involve removing the SIM card for network isolation. Often SIM card removal is used when first responders lack access to other methods of network isolation, such as a Faraday enclosure.
Where this becomes problematic is when the owner of a locked iOS 12 device is deceased, and the first responder is attempting network isolation prior to unlocking via Touch ID or Face ID. In this instance, SIM card removal is often used because Faraday enclosures make it difficult to perform biometric unlocking.
As a result, your organization may want to adapt its SOP to encourage finding alternative methods of network isolation, if available, when encountering locked iOS 12 devices. An alternative method should prevent biometric unlocking from being disabled.
2. Backups Get Harder to Find as a Result of a New UDID Format
An iOS device’s UDID is important because it is also the name of that device’s backup file. This allows you to document that this backup is of this device. The UDID is unique per device and can be found by connecting the phone and looking in iTunes, Xcode (Mac), or the Registry (Windows).
A hardware-based change to the UDID format affects newer devices with the A12 chip, including the iPhone XS, XS Max, and XR, as well as (reportedly) the Apple Watch 4 with the S4 chip.
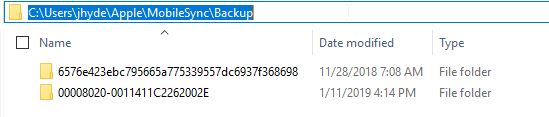
In the screen capture below, you can see backups of an iPad Mini4 with the traditional format UDID on top and an iPhone XR backup with the UDID in the new format. When looking for backups, if you see this new format, rest assured it is an iOS backup of newer hardware.
3. Wait – Where’s my Backup?
You may have noticed something in the screenshot above. That path is different than where you may have seen backups on a Windows device before. And those backups were created with iTunes to the default locations.
Examiners sometimes recover iOS backups from computers as a source of evidence. If you are only looking in the traditional places, you may be missing iOS backups.
This new location for backups occurs on Windows PCs where the installed version of iTunes was downloaded from the Microsoft Store. Currently when PC users go to the iTunes page to download iTunes, the page prompts you to download from the Microsoft Store, so this is likely to be the default location on computers that have only recently installed iTunes for the first time.
Download Locations:
- Mac ~/Library/Application Support/MobileSync/Backup/
- Windows C:Users<username>AppDataRoamingApple ComputerMobileSyncBackup
- Windows if iTunes was downloaded from the Microsoft Store: C:Users<username>AppleMobileSyncBackup
The three changes described in this blog post show that changes — both big and small — can affect forensic examinations. Further, Apple doesn’t limit changes to iOS. Some changes may be hardware dependent; others are grounded in how a user downloaded iTunes.
Ultimately, these changes serve as a reminder that even small changes can have major consequences on our ability to acquire data from devices or even find backup sources. As with everything described in our blog, be sure to validate on your own tools and test devices.
Questions or comments? Reach out to: Jessica.Hyde@magnetforensics.com