
Software kernels: Unraveling digital forensics intricacies
Software kernels: What are they?
You may hear about kernels if you deal with software or digital forensics.
What is a kernel?
Nope, it’s not popcorn, and it’s not referring to an old guy from Kentucky who is famous for his southern drawl and fried chicken, either. (Mmmm, lunch. But I digress.)
In this article we will cover the basics of what a software kernel is, the application of software kernels in the context of digital forensic examinations, and we’ll shed some light on how kernels contribute to the acquisition and analysis of data during a forensic investigation.
Let’s start with the basic definition of a kernel: a software kernel is an operating system’s central component responsible for managing tasks such as process scheduling, memory management, and hardware multitasking. It acts as an intermediary between the hardware and applications, providing a secure and controlled environment for software execution.
Kernel functions
To break down the functionality of a kernel, it is important to know the kernel’s involvement in a variety of tasks.
Process management is a critical role of a kernel’s functionality that involves creating, scheduling, and terminating processes—a process being an instance of a running program. The kernel creates and initializes processes and it allocates resources such as memory space, assigns a unique process identifier (PID), and sets up the necessary data structures.
The kernel also decides which processes should run at any given time. It employs scheduling algorithms to allocate CPU time and ensures fairness and efficiency in resource allocation. The kernel controls context switch, or the switching between processes. This involves saving the current state of a running process, loading the saved state of the next process, and transferring control of the new process. Kernels also manage the orderly termination of processes, including releasing allocated resources and updating system information.
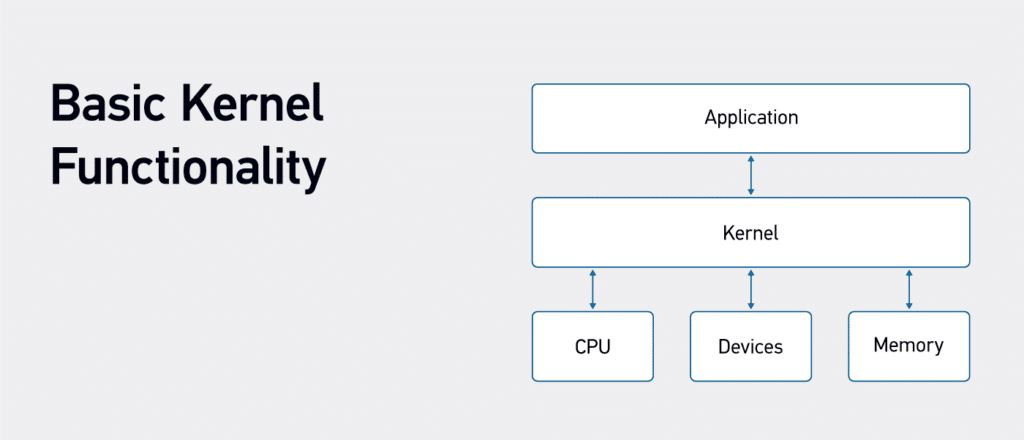
Software Kernels are crucial to managing and allocating system resources, which is a key role is memory management. The kernel allocates memory to processes and ensures each process has the required space for code, data, and stack. When a process is terminated, it also handles memory deallocation. The kernel also manages file systems by providing processes with access to files and directories. It helps to ensure proper permissions and security. When a process requires access to input/output devices or communication ports, the kernel allocates and manages this access.
The kernel facilitates multitasking to maximize CPU utilization. It allows multiple processes to run concurrently, even on a single-core system. It accomplishes this through key aspects such as time-sharing, priority scheduling, and parallel processing. Time-sharing is where the kernel divides CPU time among processes, allowing each to execute for a small time slice before switching to another. This gives the illusion of simultaneous execution. Priority scheduling is where the kernel uses a scheduling algorithm to allocate CPU time based on the priority of a process. The more important a process, the higher priority it receives for CPU time. Within a system with multiple cores, the kernel manages parallel execution, distributing processes across cores for improved performance.
Memory management
Memory management is a crucial aspect of kernel functionality. The kernel manages the distribution of physical and virtual memory to individual processes. The kernel assigns a separate address space to each process. This includes sections dedicated to code, data, heap, and stack. It ensures that processes cannot access each other’s memory directly. It also facilitates dynamic memory allocation and keeps track of free and allocated memory blocks. The kernel also manages paging and swapping in systems with virtual memory. It swaps data between physical RAM and secondary storage to accommodate processes where memory requirements exceed physical RAM.
Memory addressing by kernels entails mapping logical addresses to physical addresses. The kernel plays a pivotal role in ensuring efficient and secure memory addressing. Virtual memory gives each process the illusion of having its own dedicated memory. The kernel translates the virtual addresses to physical addresses. This translation is accomplished by the Memory Management Unit (MMU) within the kernel. The kernel also enforces memory protection by assigning access permissions to different memory sections. This prevents unauthorized access and ensures that processes only access what is assigned to them. This memory protection is vital for system stability and security. The kernel’s implementation of various mechanisms to prevent unauthorized access or usage protects the systems integrity.
System stability and integrity are key components for secure operations. Preventing buffer overflows and unauthorized access attempts is vital to maintaining a secure system. The kernel prevents memory conflicts that could lead to data corruption or system crashes. The kernel prevents memory leaks, where a process fails to release memory, and safeguards against malicious activities.
Types of kernels
There are multiple types of kernels. The most common variations of kernels are the Monolithic kernel, Microkernel, and Hybrid kernel. The Monolithic kernel is a single, large executable containing the operating system’s core functionality. These functions include process management, memory management, device drivers, and file systems. In this architecture, all these functions run in the kernel space. The Monolithic kernel structure is relatively straightforward, making it easier to develop and maintain. Some operating systems that use this kernel type include Linux and old versions of Windows (pre-Windows NT).
Microkernels are different because they are structured to provide only essential functionality in the kernel space. Non-essential services such as device drivers and file systems are moved to user-space. Inter-process communication (IPC) mechanisms provide communication between these user space components. Microkernels are highly modular and allow for easy addition or removal of services without affecting the core kernel. Microkernels are used in operating systems such as QNX and MINIX.
Hybrid kernels strive to take the benefits of both monolithic and microkernel architecture. They have a small, essential kernel that handles critical tasks like process scheduling and memory management, but they also incorporate non-essential services for performance reasons. Modern versions of Windows are built using Hybrid kernels.
Kernels in digital forensics
Knowing how the kernel works is very important in the world of digital forensics. The results or products of the kernel interaction do provide a great deal of forensic value. Examination of the memory, running processes, network connections, and open files will yield artifacts of value during an examination. In the future, there may be a need for kernel-based forensic examinations. Actual forensic examination of a kernel is not an entry-level-based investigation. Examiners could take multiple general steps to examine a kernel forensically.
Source code analysis is a starting point. This would include analysis of the code for security vulnerabilities, backdoors, or suspicious code patterns. Binary code analysis can also be deployed. This requires using a dissembler and decompilers to convert the machine code to assembly language. From there, analysis would have to be done to identify and analyze critical functions, system calls, and interrupt handlers to ensure the kernel is operating as it should.
Behavioral analysis requires less coding background to complete. Behavioral analysis entails running the kernel in a controlled environment and monitoring system calls, network activity, and resource usage for abnormal behavior. Log analysis of the system and kernel logs will assist in searching for suspicious activities. Analyze the logs for error messages, warnings, or entries that might indicate security incidents or unauthorized access. Network analysis of traffic generated by the kernel can reveal unusual communication patterns or connections. This can lead to identifying network protocols or services implemented by the kernel .
As you can see, the kernel is a core component of the functionality of a system. Attacks at a kernel level are rare. However, it is important to understand how the kernel works and the possibility that a system’s kernel could be compromised in a cyber-based attack.
If you like this piece, check out our articles on Forensic Analysis of Prefetch files in Windows, SRUM: Forensic Analysis of Windows System Resource Utilization Monitor, and Forensic Analysis of MUICache Files in Windows.