
Hunting Russian Intelligence “Snake” Malware in Memory With Magnet AXIOM Cyber
This memory analysis post is authored by Matt Suiche (Director, Memory, IR & R&D).
This week, a joint cybersecurity advisory was issued by the cybersecurity authorities (AA22-110A) of the United States, Canada, Australia, New Zealand and United Kingdom to provide an overview of Russian state-sponsored cyber operations and TTPs.
In the advisory AA23-129A, we learn more about intelligence collection capabilities used by an implant dubbed as “Snake” to target multiple industries in multiple countries over the past 20 years.
The Snake implant has been called “one of the most sophisticated cyber espionage tools” and has been attributed to Center 16 of Russia’s Federal Security Service (FSB) by CISA.
Memory Analysis Can Help Detect the Snake Implant
Memory analysis has been highly rated as a detection mechanism within the report as providing “the greatest level of visibility into Snake’s behaviors and artifacts”.
At Magnet Forensics, we strongly believe that having access to memory analysis capabilities should be easy. That’s why we’ve integrated our new Comae memory analysis capabilities within AXIOM Cyber 7.0, which also includes YARA scanning for memory.
Dealing With Techniques Used by the Snake Implant
One of the techniques used by the Snake implant is process injection (T1055), which in this instance, results to a newly allocated memory space in the target process with the PAGE_EXECUTE_READWRITE permissions, which are often associated with process injection, that will contain the injected user-mode module. Memory analysis here is a powerful method as it allows analysts to study and analyze how Snake hides its presence.
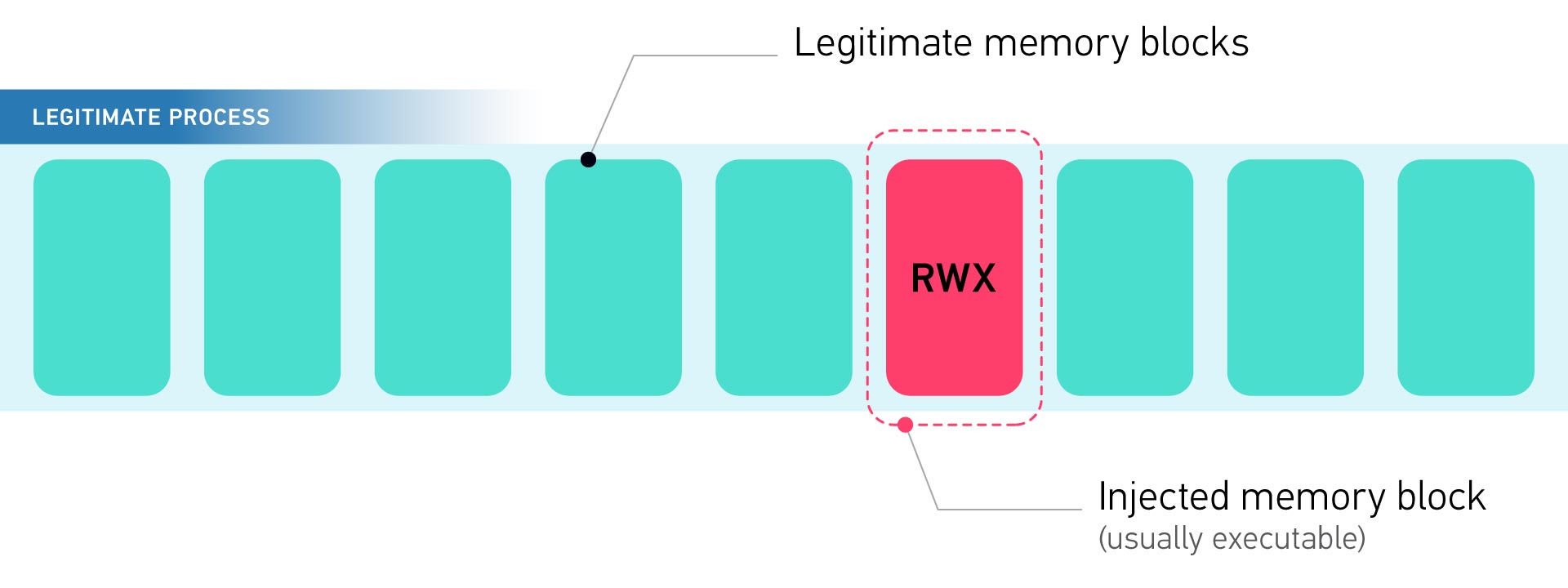
To quickly and efficiently capture memory on a potentially targeted machine, we recommend analysts get a free copy of Magnet DumpIt to perform a memory acquisition in a Microsoft crash dump format. This will also enable easier deep dives in advanced troubleshooting and debugging tools such as Microsoft WinDbg, particularly to analyze kernel components (T1014) of threats.
Resources: Scanning for Snake Using YARA Rules in AXIOM Cyber
One of the shared resources and indicator of compromises (IOCs) featured in the report to detect Snake, is a Volatility plugin to scan the memory space of processes for a set of known strings and extensions that are part of Snake’s principal user-mode component:
- %s#1
- %s#2
- %s#3
- %s#4
- .tmp
- .sav
- .upd
This search can easily be converted into a YARA rule, which can be found at the end of this blogpost and used within AXIOM Cyber to scan the memory space of all processes through our newly integrated memory capabilities. This allows investigators and analysts to quickly and efficiently scan multiple machines in a simple and efficient manner. For more information on using YARA rules in AXIOM Cyber check out: YARA Rule Processing in Magnet AXIOM Cyber
This operation disruption is a great example of how memory analysis can be easily leveraged within AXIOM Cyber for the detection of sophisticated threats targeting sensitive assets. And as we have seen in our previous blogpost about the FORCEDENTRY exploit, it is very common for nation-state threats to never see their samples shared therefore requiring detection engineering to be more creative to overcome this challenge when information shared is only partial.
Find Out More About Memory Analysis in AXIOM Cyber
To learn more about the recently updated memory analysis capabilities of AXIOM Cyber check out Comae Memory Analysis Capabilities Integrated Into Magnet AXIOM Cyber.
To try the memory analysis capabilities of Comae in AXIOM Cyber for yourself, update to the latest version over at the Customer Portal or request a free trial today!
Windows_Snake_Malware Rule
/*
Hunting Russian Intelligence “Snake” Malware
The Snake implant is considered the most sophisticated cyber espionage tool designed and used by
Center 16 of Russia’s Federal Security Service (FSB) for long-term intelligence collection on sensitive
targets.
*/
rule Windows_Snake_Malware {
meta:
author = "Matt Suiche (Magnet Forensics)"
description = "Hunting Russian Intelligence Snake Malware"
creation_date = "2023-05-10"
threat_name = "Windows.Malware.Snake"
reference = "https://media.defense.gov/2023/May/09/2003218554/-1/-1/0/JOINT_CSA_HUNTING_RU_INTEL_SNAKE_MALWARE_20230509.PDF"
severity = 100
scan_context = "memory"
license = "MIT"
os = "windows"
/* The original search only query those bytes in PAGE_EXECUTE_WRITECOPY VADs */
strings:
$a = { 25 73 23 31 }
$b = { 25 73 23 32 }
$c = { 25 73 23 33 }
$d = { 25 73 23 34 }
$e = { 2e 74 6d 70 }
$f = { 2e 73 61 76 }
$g = { 2e 75 70 64 }
condition:
all of them
}