
How to Uncover Communication Artifacts for Mobile Device Investigations
Communication artifacts are digital breadcrumbs suspects leave behind in the form of emails, social media, native chat applications like the Messages app on iOS, or a third-party application like Signal. These communication artifacts help investigators uncover important connections and unlock the truth. They can reveal what was said, when it was said, and who said it to whom.
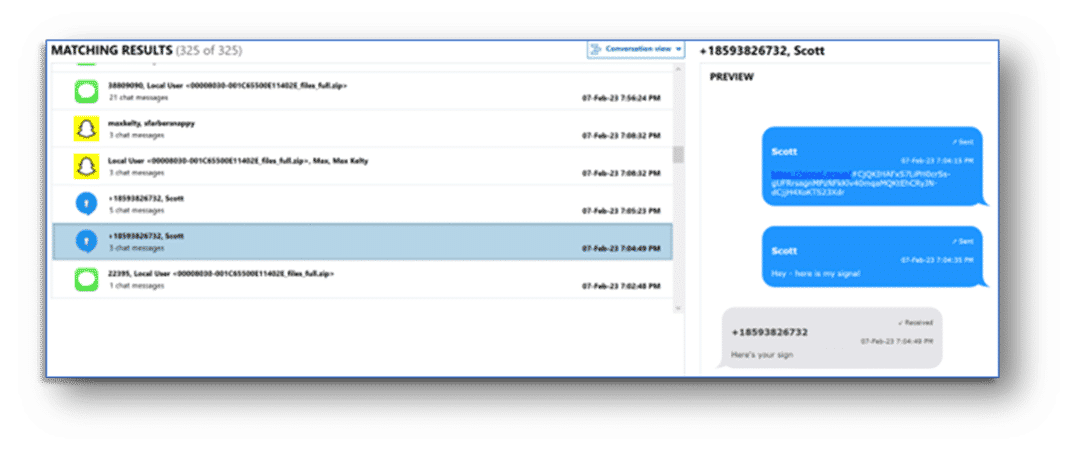
Communication Artifacts in Investigations
Chat message content and the involved parties to those messages can be an extremely rich source of information in almost any investigation type. In addition to chat messages, email communication can be another go-to source of information, and the artifacts related to traditional cellular call logs and contact information cannot be overlooked. Attachments – whether as part of chat messages or in an email exchange – are often a target of investigative interest. Within the various artifact categories of Magnet AXIOM and AXIOM Cyber, these attachments are embedded as part of the rethreaded conversation view or shown within the context of their associated email message. Also, you’ll find all the email attachments recovered from your evidence sources in the category.
Top Communication Artifacts for Android and iOS
Magnet Forensics has curated the following list of top communication artifacts and where they can be found on a given device. Magnet’s AXIOM and AXIOM Cyber tools will surface these artifacts for you quickly and easily, but it’s important you know where to look:
Android Communication Artifacts
| SMS: |
| /data/data/com.google.android.apps.messaging/databases |
| /data/data/com.android.providers.telephony/databases/mmssms.db |
| /user_de/0/com.android.providers.telephony/databases/mmssms.db |
| Call Logs: |
| /com.android.providers.contacts/databases/calllog.db |
| /com.android.providers.contacts/databases/contacts2.db |
| Contacts: |
| /data/data/com.android.providers.contacts/databases/contacts2.db |
| Email | Gmail |
| /data/data/com.google.android.gm/databases/ |
iOS Communication Artifacts
| SMS: |
| /private/var/mobile/Library/SMS/sms.db |
| HomeDomain-Library/SMS/sms.db |
| Call Logs: |
| /private/var/mobile/Library/CallHistoryDB/CallHistory.storedata |
| HomeDomain-Library/CallHistoryDB/CallHistory.storedata |
| Contacts: |
| /private/var/mobile/Library/AddressBook/AddressBook.sqlitedb |
| HomeDomain-Library/AddressBook/AddressBook.sqlitedb |
| Email | Mail App |
| /private/var/mobile/Library/Mail |
| /private/var/mobile/Library/Mail/[UUID]/*.emlx |
| /private/var/mobile/Library/Mail/[UUID]/*.imapmbox/Attachments/ |
By analyzing these artifacts, investigators can track communication patterns. Who is talking to whom and how frequently? Are there sudden bursts of communication followed by prolonged periods of silence? Answering questions like these gives investigators a window into a person’s interactions, enabling them to establish timelines, identify key players, reconstruct conversations, and uncover important connections.
Leveraging Communication Artifacts
While many examiners spend the bulk of their time using the artifact explorer in AXIOM Examine, other features like Timeline and Connections can help surface items of interest. The volume of artifacts from a modern mobile device examination can make it easy for potential communication artifacts of interest to blend into the noise, almost hiding in plain sight.
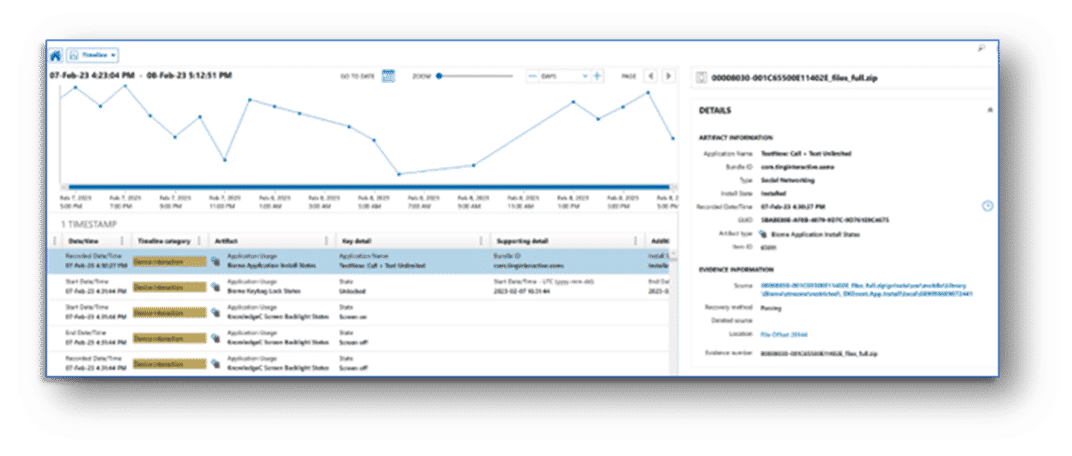
Using the Timeline explorer can help to profile when a particular activity occurred on a device or provide context as to what a user was doing on their device at a certain time. The use of absolute and relative time filters can also help examiners find key details around points of interest in the timeline of a specific investigation.
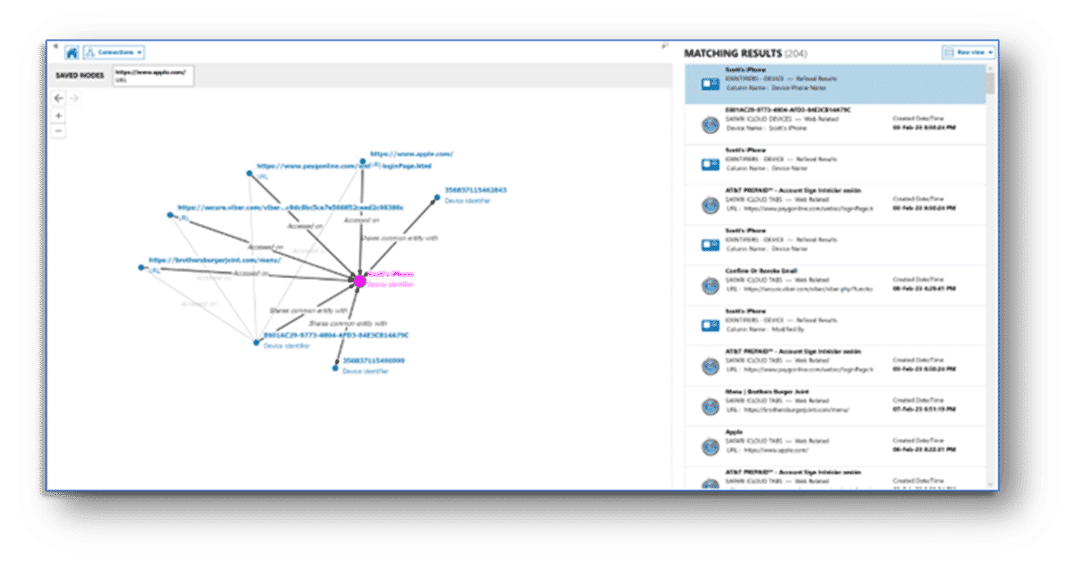
The connections explorer provides a visual representation of how the various artifacts in your case are related. By using the distinct properties of each artifact, called artifact attributes, you can show relationships between an artifact of your choosing – such as a screen name or phone number – to see how they relate to the communication artifacts in your case.
These days, mobile devices often have greater storage capacity, even rivaling traditional computers. Still, the always-on, always-connected nature of mobile devices means that cloud stored data cannot be overlooked. The Potential Cloud Evidence Leads dashboard is a great resource for identifying other sources of data which may be relevant to your investigation – particularly when mobile devices are involved.
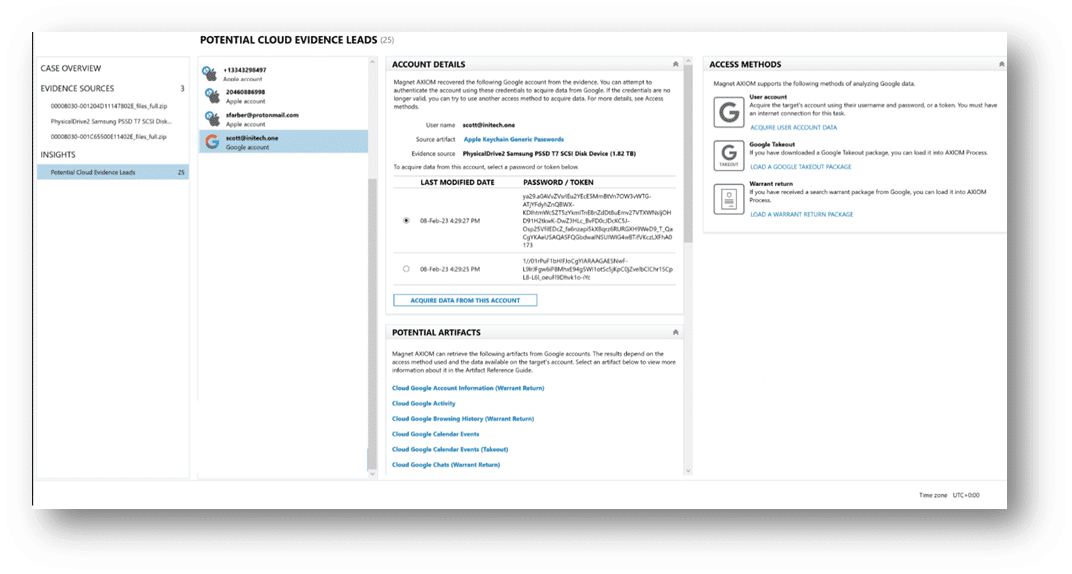
Applications on a device may not always store data locally or there may be additional logs, usage, and analytics data available directly from the connected cloud account. The potential cloud evidence leads dashboard helps examiners by surfacing potential sources of cloud-stored data and accounts from the installed applications and accounts recovered on a device. This can help to provide an efficient method for directing further investigative efforts in a case.
If you haven’t tried Magnet AXIOM or AXIOM Cyber, request a free trial today. You can also learn more about how Magnet GRAYKEY and VERAKEY provide same-day access to the latest iOS and Android devices.