
How EDR Complements DFIR
Chances are if you have EDR (Endpoint Detection and Response) tools, your cybersecurity posture is mature enough that you also have DFIR (Digital Forensics and Incident Response) tooling as well. But you may be wondering: how they overlap, if at all. Do EDR tools and DFIR tools do the same thing, or do they complement each other?
The short answer, as far as we’re concerned, is EDR and DFIR tools are complementary to each other. EDR tools are limited in their forensics capabilities, so DFIR tools are there to perform deep dive analysis to ensure that remediation of security incidents is effective.
Keep reading for the long answer!
Incident Response Framework
The most widely adopted framework that outlines the incident response (IR) process is from National Institute of Standards and Technology (NIST) Special Procedure (SP) 800-61.
There are four key steps within this framework: preparation, detection and analysis, containment eradication and recovery, and post-incident activity.
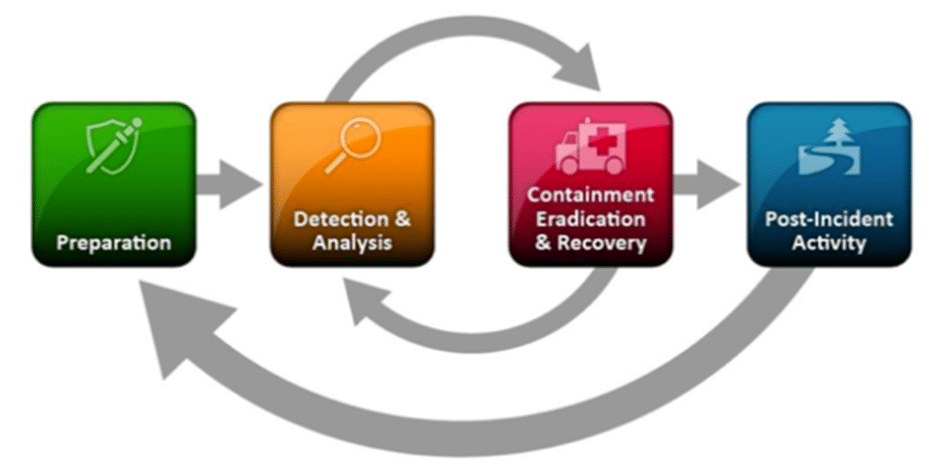
The IR lifecycle provides a foundation for understanding how both EDR tooling and DFIR tooling fit in the various stages.
What is EDR?
The EDR market, a term introduced by Gartner analyst Anton Chuvakin, has solutions that “record and store endpoint-system-level behaviors, use various data analytics techniques to detect suspicious system behavior, provide contextual information, block malicious activity, and provide remediation suggestions to restore affected systems.” Further to that, EDR solutions must provide four primary capabilities which are aligned nicely to the NIST IR framework:
- Detect security incidents
- Contain the incident at the endpoint
- Investigate security incidents
- Provide remediation guidance
Arguably EDR touches each step of the framework with a core competence on the third step: Containment Eradication & Recovery. And while yes, EDR does have a role to play in the Detection & Analysis phase, its capabilities are limited.
EDR only goes so far when it comes to investigation of security incidents. EDR tools provide real-time, continuous monitoring of suspicious incidents on endpoints and let incident handlers know what is happening and when it is happening.
One of the limitations of EDR however, is that it narrowly focuses on endpoint telemetry. This view doesn’t provide visibility into network activity, what may be happening in the cloud, or how data from mobile devices or IoT devices is contributing to the incident.
There is far more to a security incident than just the what and the when on the endpoint. There are other pieces of the puzzle. Other data sources are crucial to understand—not only to ensure the full scope of the security incident at-hand is addressed, but also so that it doesn’t happen again and whoever is responsible is dealt with appropriately.
What is DFIR?
DFIR can be categorized as two things: digital forensics and incident response. Digital forensics is a branch of forensic science that focuses on recovering, investigating, and analyzing digital data. Incident response is a process that is focused on detecting security incidents and remediating them.
While those definitions may sound similar to EDR, the strength of DFIR is in the acquisition of data and the subsequent capability to perform deep dive analysis of that data sometimes from multiple endpoints or data sources.
Imagine an iceberg: EDR is able to investigate the tip of the iceberg, DFIR tools are specially-designed tools to investigate the entire iceberg. If EDR answers the what and when of a security incident, DFIR answers the how and who, and may even get to the why in some cases.
DFIR provides that deeper understanding by performing acquiring and analyzing data at a very granular level from endpoints, network appliances, and other data sources to identify exactly how a security incident happened, what data was compromised, as well as who the bad actor is.
Going back to the NIST IR framework, the final step of the process is Post-Incident Activity which is usually focused on lessons learned that feed into the Preparation stage. Without an intimate understanding of how and who that is best performed by a digital forensics tool, these stages of the IR process are not properly completed.
Additionally, many businesses—specifically those in highly regulated industries like financial services or healthcare—are under increasing pressure and regulatory requirement to report on known data breaches and provide details within a defined timeframe. For example, GDPR mandates that organizations must report a notifiable breach without undue delay within 72 hours of becoming aware of the breach.
Magnet AXIOM Cyber
DFIR tools like Magnet AXIOM Cyber are essential for businesses to acquire data from remote endpoints and analyze data from multiple sources like Windows, Mac, or Linux devices in addition to mobile devices, cloud-based apps or storage services such as AWS or Azure, not to mention the ever-expanding number of IoT devices.
Once analysis is complete, AXIOM Cyber has comprehensive reporting functionality that can produce a range of reports: everything from technical exports for review by other DFIR colleagues or a load file for eDiscovery analysts to easy-to-read and understand reports for non-technical stakeholders such as HR or Legal teams.
A General IR Workflow: EDR Complementing DFIR
Endpoints within enterprise organization are being monitored by the Security Operation Center (SOC) with an EDR platform among others tools such as anti-virus or EPP tools. These SOC tools are generating over one thousand security alerts each day. Although this is an overwhelming amount of volume, advancements in technology and automation alleviate some of the workflow and many alerts don’t require investigation.
SIEM and SOAR tools interact with EDR tools and can help identify when a security event needs to be escalated and therefore investigated. Processes can be defined that invoke DFIR tools to acquire data from compromised endpoints and processed so a DFIR examiner or analyst can then perform analysis of the data.
Performing a deep dive analysis of a security event using specialized DFIR tools, such as Magnet AXIOM Cyber, uncovers not only the what and when, but also the how, who, and sometimes why. Findings from DFIR analysis are shared with SOC teams so they perform comprehensive threat containment and eradication, often using an EDR tool or custom scripting.
In short, DFIR tools get the depth of evidence needed to move forward in an incident response process that EDR tools aren’t designed to obtain. Without a root cause understanding of a security event, organizations are incapable of effectively learning from it and will not be prepared to handle a similar attack in the future.
What About XDR?
XDR (Extended Detection and Response) is the evolution of EDR and addresses some of the shortcomings of EDR. Although EDR has been valuable, EDR is restricted because it can only detect and respond to threats inside managed endpoints.
While XDR addresses the narrow focus that EDR has, it still doesn’t solve the deep dive analysis that DFIR performs. Therefore, XDR and DFIR are complementary to each other as well. DFIR tools like Magnet AXIOM Cyber are still best positioned to get the whole picture of a security incident.
DFIR Solutions for Enterprise Businesses
Learn more about how Magnet Forensics solutions for enterprise organizations can complement EDR tooling and help you respond to security incidents faster.