Extracting Data from a Samsung Device Using Advanced MTP
Samsung devices are one of the most popular device types on the most popular mobile operating system, Android. In the case of a recent examination, a Samsung was giving me a lot of trouble. It was a Verizon Samsung Galaxy S7, SM-G930V. This phone was released running Android version 6, or Marshmallow, and upgradable to version 7, Nougat. This tells us almost immediately that encryption is in play. Unfortunately, it gets worse in this case because the phone is damaged. The phone will boot, we can hear it turn on, but nothing on the screen. This means that even if we knew the passcode, we can’t enter it in. That also means we can’t turn on USB debugging either.
So, to review, the device is encrypted (no chip-off or ISP options), it’s a Verizon phone so the bootloader is locked (no recovery extraction), and the screen is busted (no input for passcode or ADB). Hmmm. So at this point, there’s not a lot we can do with this device without repairing the screen. We could attempt MTP (Media Transfer Protocol) which has sometimes been found to get around passcodes and authorization, but, since this is Android version 6, MTP is going to be disabled by default. In version 6, Android has changed the default connection type to “Charge Only” when it is plugged into a computer, so we would have to enable MTP which isn’t going to be possible without our screen.
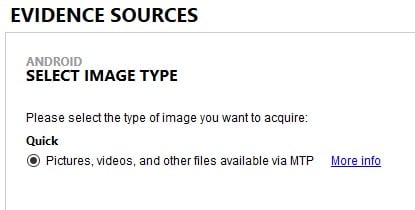
Enter in Magnet AXIOM’s new Advanced MTP bypass method. This new option will allow us to grab a quick image of the /media/ partition on the device for Samsung devices that have not received either the SMR-OCT-2017 or SMR-NOV-2017 security update (the exact update in which this was patched depends on the device model). Even if this device doesn’t have MTP enabled or is even locked with a passcode, this option will allow us to extract some of the data for analysis.
In order to select this new option from the AXIOM workflow, we need to connect the device we’d like to acquire, and then select: Mobile ⇒ Android ⇒ Acquire Evidence ⇒ Advanced ⇒ Samsung ⇒ MTP. At this stage, we simply follow the instructions provided and, when finished, AXIOM will present us to our device ready to acquire.
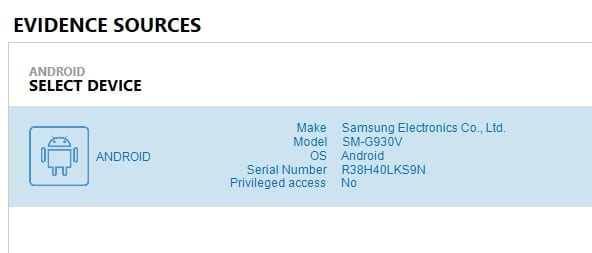
Yes! Now that we’ve gained connection, we can confirm this is our correct phone thanks to the Serial Number of Model being displayed and extract our data.
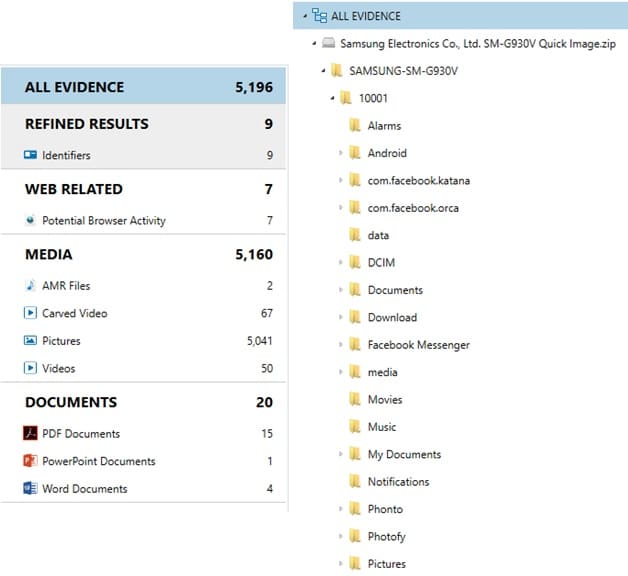
Because this is an MTP extraction, we’re only going to be able to grab what’s in the /media/ directory in the /data/ or /userdata/ partition. This is going to be mostly pictures and video files. However, the /media/ directory can hold more than that. It can also include documents, downloads from web browsers, WhatsApp chat backups, and third party application data that developers choose to store here.
Once the data was pulled, we were left with a .zip file over 4GB in size. After processing with artifacts in AXIOM we were able to recover over 5,000 artifact hits.
Again, because this is a full pull of the /media/ directory, we could be looking lots of third-party data as seen above from things like Facebook, Snapchat, WhatsApp, and more. In media-heavy cases such as solicitation, CSAM, or terroristic threats, this new option for passcode bypass could be a huge win in many investigations. This new acquisition method should work on many Samsung devices from 2012 to 2017 running OSes from 4.0.3 all the way up to 7 (Nougat). So, go grab that previously inaccessible device out of evidence and let’s try again!
To learn more about acquiring a physical image of LG devices without knowing the user’s passcode, watch this video:
If you have any questions or comments, feel free to reach out to christopher.vance@magnetforensics.com.