
Enhancing Your Incident Response Playbook With Magnet AXIOM Cyber
With the range of cybersecurity threats targeting government agencies, it’s not a matter of if a cyberattack will occur, it’s a matter of when. With that in mind, cybersecurity teams need to prioritize developing, implementing, and updating their incident response playbook to help reduce the impact and recovery time of a cybersecurity incident.
A key step in developing a successful incident response playbook is the post-incident review and analysis. Effective prevention of future events needs to be informed by the post-incident analysis. Understanding vulnerabilities in a network is imperative to being prepared to prevent future incidents and strengthening your agency’s security posture.
The Framework for an Incident Response Playbook
The National Institute of Standards and Technology (NIST) provides one of the most commonly adopted frameworks for incident response. The NIST framework outlines four key phases of IR: Preparation, Detection & Analysis, Containment, Eradication, & Recovery, and Post-Incident Activity.
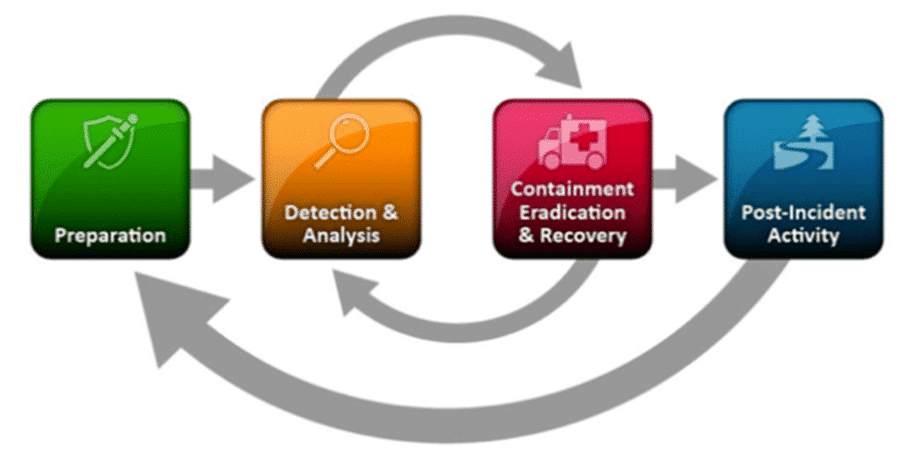
The final step of the process, Post-Incident Activity, focuses on lessons learned which are used to inform continued Preparation. However, this can also be the most easily overlooked or abbreviated stage of the process. Once the incident is contained, recovery is underway and high-level questions have been answered, it can be tempting to shift focus to the many other competing priorities and new potential threats. But without a comprehensive understanding of the root cause—to identify exactly how the incident occurred—this stage is not fully completed, leaving important lessons unlearned that could prevent or mitigate the next cyber incident.
Getting to the Root Cause of a Cybersecurity Incident With AXIOM Cyber
One of the reasons that post-incident activity may not be fully optimized is that EDR and IR-specific tools simply aren’t designed to provide a holistic picture across mobile, cloud and network activity related to a security event.
These important insights can only be acquired through specialized digital forensic tools, like Magnet AXIOM Cyber, that provide a deeper understanding of the incident by acquiring and analyzing data at a very granular level. Only with this deep analysis are you able to understand exactly how a security incident happened, what data was compromised, as well as who the bad actor was.
Magnet AXIOM Cyber helps you acquire and analyze artifacts from multiple data sources like Windows, Mac, or Linux, mobile devices, cloud-based apps, storage services such as AWS or Azure, and IoT devices. To help manage the volume of artifacts available from these data sources, there are several features and capabilities that have been incorporated into AXIOM Cyber to help accelerate IR investigations and get you the insights that you need to protect your agency and sensitive data from future attacks.
Incident Response Workflow in AXIOM Cyber
Magnet AXIOM Cyber’s powerful toolset lets you understand how an incident occurred so you can prevent it in the future. Let’s look at how the incident response features of AXIOM Cyber can be used at the different stages of an investigation: collecting, analyzing, and reporting on cybersecurity incidents.
1. Collecting All of the Necessary Data
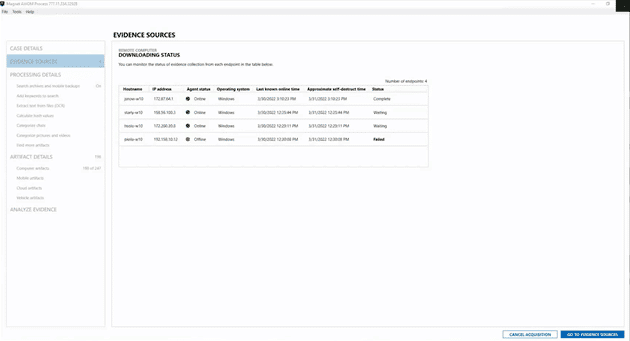
AXIOM Cyber enables the remote collection of artifacts even if the endpoint is in a different geographic region or off the corporate network. With AXIOM Cyber you can quickly create a remote agent to gather the necessary data and even covertly deploy the agent if there is concern that a bad actor might be monitoring your activity.
To further accelerate the speed of your IR investigations, you can build out Targeted Location Profiles which allow you to define multiple locations on an endpoint, including folders, browser activity and system files that will be consistently collected. These profiles can also include volatile artifacts to capture live system processes and insights into malware behavior and malicious activities that don’t leave easily detectable evidence trails.
When there are multiple endpoints impacted by malicious activity, you can easily set up a Queued Remote Collection of up to 15 endpoints that AXIOM Cyber will automatically progress through. The result is that your time isn’t spent manually initiating collections and monitoring the connection status, freeing you up to focus on other priorities while AXIOM Cyber takes care of collecting the data.
2. Analyzing Data to Determine the Root Cause of the Incident
AXIOM Cyber enables you to review consolidated evidence from all of the sources in one case, while the powerful analytical capabilities automatically surface actionable insights that enable you to focus on the most relevant data.
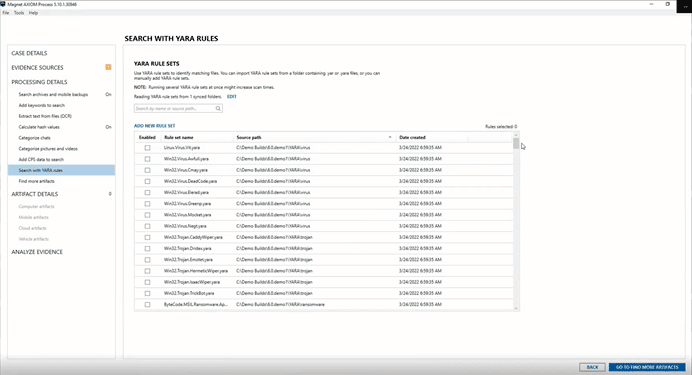
The collected data can be run against the included, or custom, YARA rules in AXIOM Cyber to identify known instances of malware. Malicious files can be further examined with a quick right-click to access the VirusTotal integration in AXIOM Cyber, providing insights into the history and behavior of a threat to inform your response and mitigation plans.
The Email Explorer interface in AXIOM Cyber helps manage email evidence in IR cases by presenting them in an intuitive format that mirrors the appearance and functionality of common email platforms. Search and filter capabilities can be used to quickly surface messages containing suspected malware and link attributes or wording that may be related to phishing attempts.
3. Reporting on the Incident
Once your analysis is complete, AXIOM Cyber has comprehensive reporting functionality that can produce a range of reports: everything from technical exports for review by DFIR colleagues to easy-to-read and understand reports for non-technical stakeholders.
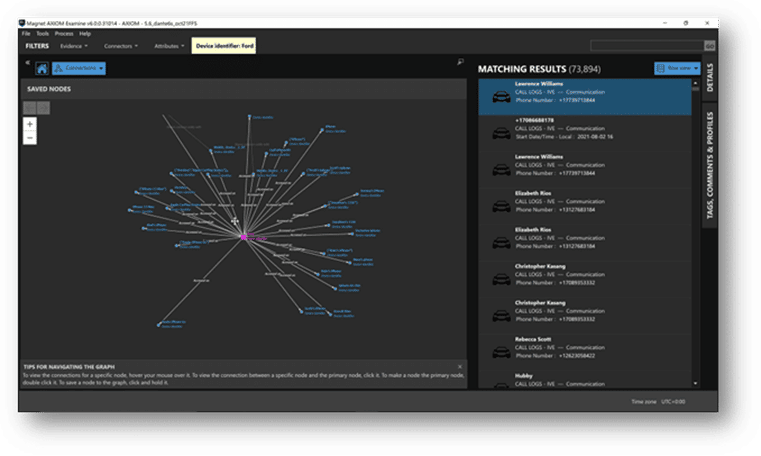
The powerful analytical capabilities and data visualizations in AXIOM Cyber, such as Timeline and Connections, can also be applied to reports. Providing connections between artifacts from different sources to present a clear picture of the events related to an incident.
The Importance of Lessons Learned
Cyberattacks are only increasing in their sophistication and persistence, employing new, malicious tools and services to increase the odds of gaining access to sensitive data. As cyberattacks targeting government agencies continue to adapt and evolve you need to prioritize updating and refining your incident response playbook to reduce the damage, recovery time, and impact of cybersecurity incidents.
“Ransomware, along with business email compromise (BEC), will likely remain the primary cyber threats. However, we have seen first-hand that when organizations have the tools and planning in place to respond quickly and efficiently, they can minimize both the cost and the disruption to their business.”
Mark Greisiger President NetDiligence
Using AXIOM Cyber to gain a detailed understanding of cyber incidents, an Incident Response playbook can be refined and improved to address threats before they become attacks, hardening your agency’s security posture, and protecting its important data.
Take Your Incident Response Playbook to the Next Level With Magnet Forensics and AXIOM Cyber
To learn more about the IR capabilities of AXIOM Cyber visit our Incident Response hub to review blogs, how-to videos, and webinars on each of the features outlined above.