Analyzing GrayKey Images with AXIOM: New Artifact Parsing Capabilities
With the release of Magnet AXIOM 2.5 and 2.6, we’ve added new artifact parsing capabilities to support exams that utilize GrayKey. Again, GrayKey is a new forensic tool that unlocks iOS devices new and old, giving us access to helpful device information many thought we wouldn’t see again: both user and system data.
In this blog, we’ll talk about a few of the artifacts AXIOM parses that are key in iOS investigations. If you need a refresher on loading GrayKey images into AXIOM, check out our previous blog with video walk-through here.
Geolocation Data
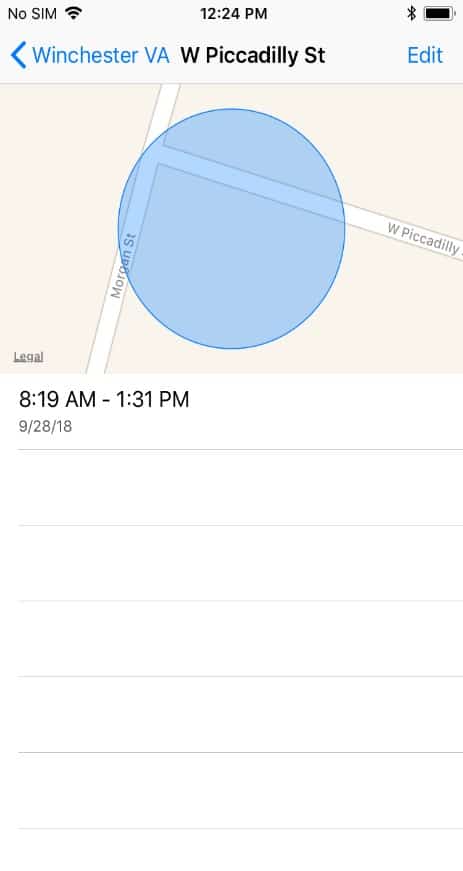
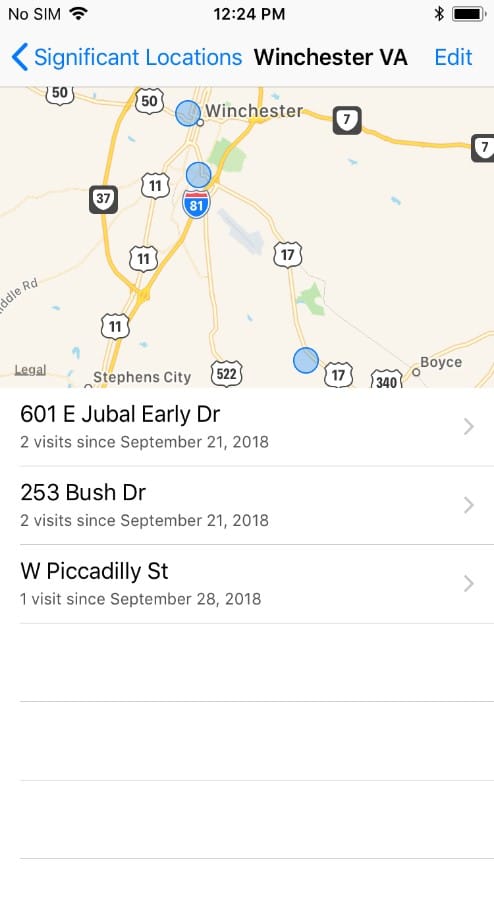
Outside of images and messages, geolocation data is one of the most popular items investigators request information on when submitting a device for forensic analysis. In recent years, if examiners wanted additional GPS information outside of what could be found in apps or embedded in images, we’d turn to reviewing Frequent Locations. This artifact is accessible to the end user, but rarely deleted.
If you’re interested in seeing what location data is available on your own iPhone, navigate to Settings > Privacy > Location Services > System Services > Frequent Locations. Following the artifacts-first philosophy, in AXIOM’s Artifacts Explorer, location evidence such as Frequent Locations and location cache information can be found under the Operating System section. We recommend using the World Map view versus Column or Classic view for viewing this evidence.
iOS Wallet
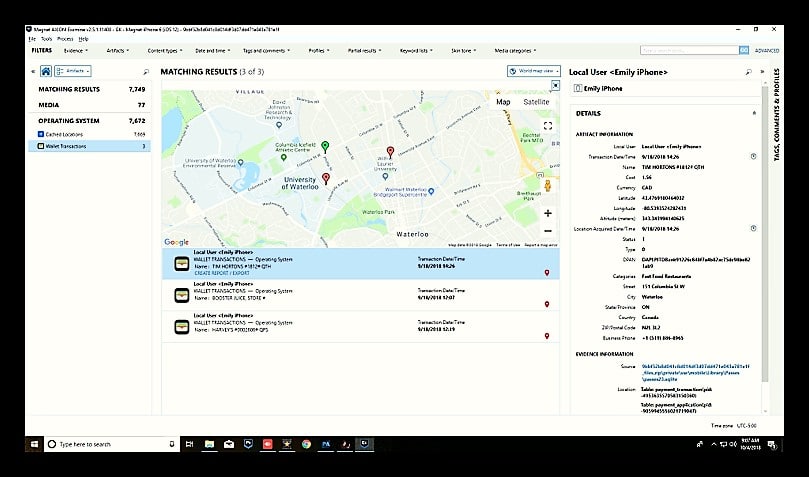
As of AXIOM 2.5, examiners can parse the iOS Wallet. This artifact contains information ranging from saved credit cards and airline tickets, to brand loyalty cards (e.g., Starbucks, United, Delta, and Hilton to name a few).
While not every investigation will need these artifacts, information available to the examiner includes store information, transaction history time stamps, and geolocation data. If your investigation hinges on providing a timeline of events for an individual, this data could be invaluable in helping to tell the story.
iOS Cloud Tabs
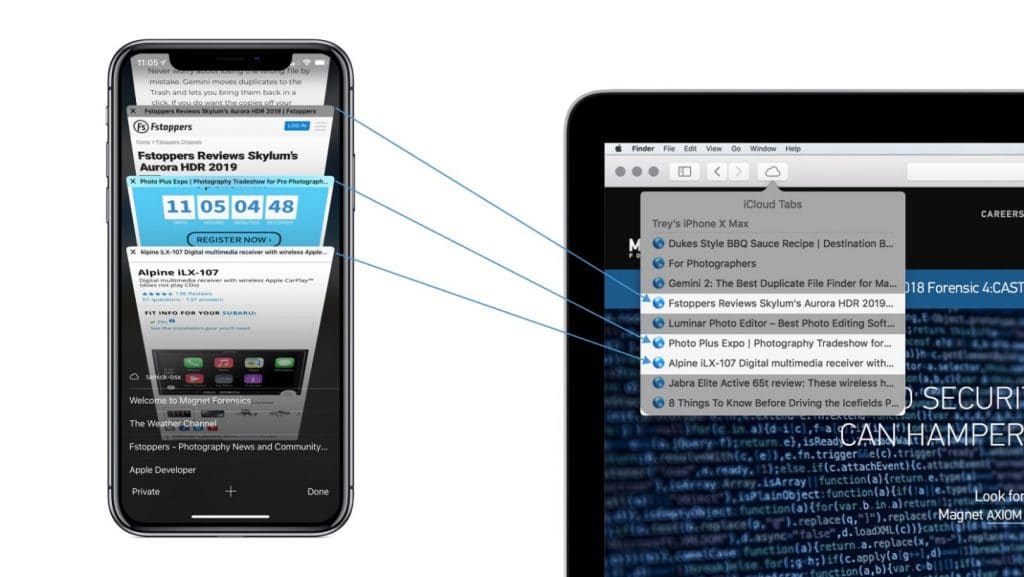
AXIOM also parses Safari iCloud Tabs (CloudTabs.db), located under the Web Related Artifacts section. As the name implies, the Safari iCloud Tabs artifact provides insight into web pages that are open on other Mac devices (OS X 10.8.2 or later) and iOS devices (iOS 6 or later).
This artifact is particularly interesting when you start an investigation. It provides insight as to other devices that may need to be seized. It also offers more web history, which could hold potential evidence.
In the images below, you can see iCloud Tabs in action. If an investigator only has access to a mobile device during an investigation, using AXIOM’s iCloud Tabs artifact, additional evidence of what websites were being browsed and still open on a separate devices could be viewed.
How AXIOM Reports GrayKey Image Data
Apart from the above artifacts, GrayKey images result in a lot of unstructured raw data. This can result in potential discrepancies between multiple forensic suites’ dashboard views, so it’s important to understand how your forensic tools report the data.
In contrast to the traditional file system approach of manually searching through gigabytes or even more commonly, terabytes of data per case, AXIOM’s artifacts-first approach allows examiners to home in on a device’s most important recovered app and browser data.
As a result, AXIOM doesn’t count files such as configuration, or 0-1KB, files as “hits” since the majority of these are not actionable evidence. AXIOM allows you to examine these files inside the File System Explorer, but doesn’t typically show these files in the Artifacts Explorer. This is in contrast to other tools, which may count every single file as a “hit” when presenting the evidence, but end up only adding time and effort to your overall examination.
Recap
The amount of evidence that GrayKey acquires is substantial. Using AXIOM to parse out artifacts such as the Wallet, geolocation data, and iOS iCloud Tabs allows you to complete forensic investigations that are both faster and more thorough, recovering data you might not have otherwise thought relevant to a particular case.
Stay tuned, Magnet Forensics will be adding new artifacts found in GrayKey images soon! If there are artifacts you’d like to see supported in AXIOM or if you have any questions, please don’t hesitate to reach out to me at trey.amick@magnetforensics.com.