Making a Case (Portable Case)
This course is specifically designed to introduce stakeholders, such as investigators, attorneys, and subject matter experts, to the utilization and review of digital forensics case data provided in the form of a Magnet Forensics Portable Case.
In this introductory course you will learn and develop skills related to a Portable Case, including investigating a subset of data, Portable Case navigation, searching and filtering data, analyzing and understanding artifacts, and distributing findings in the form of a report.
Module 1: Introduction and overview
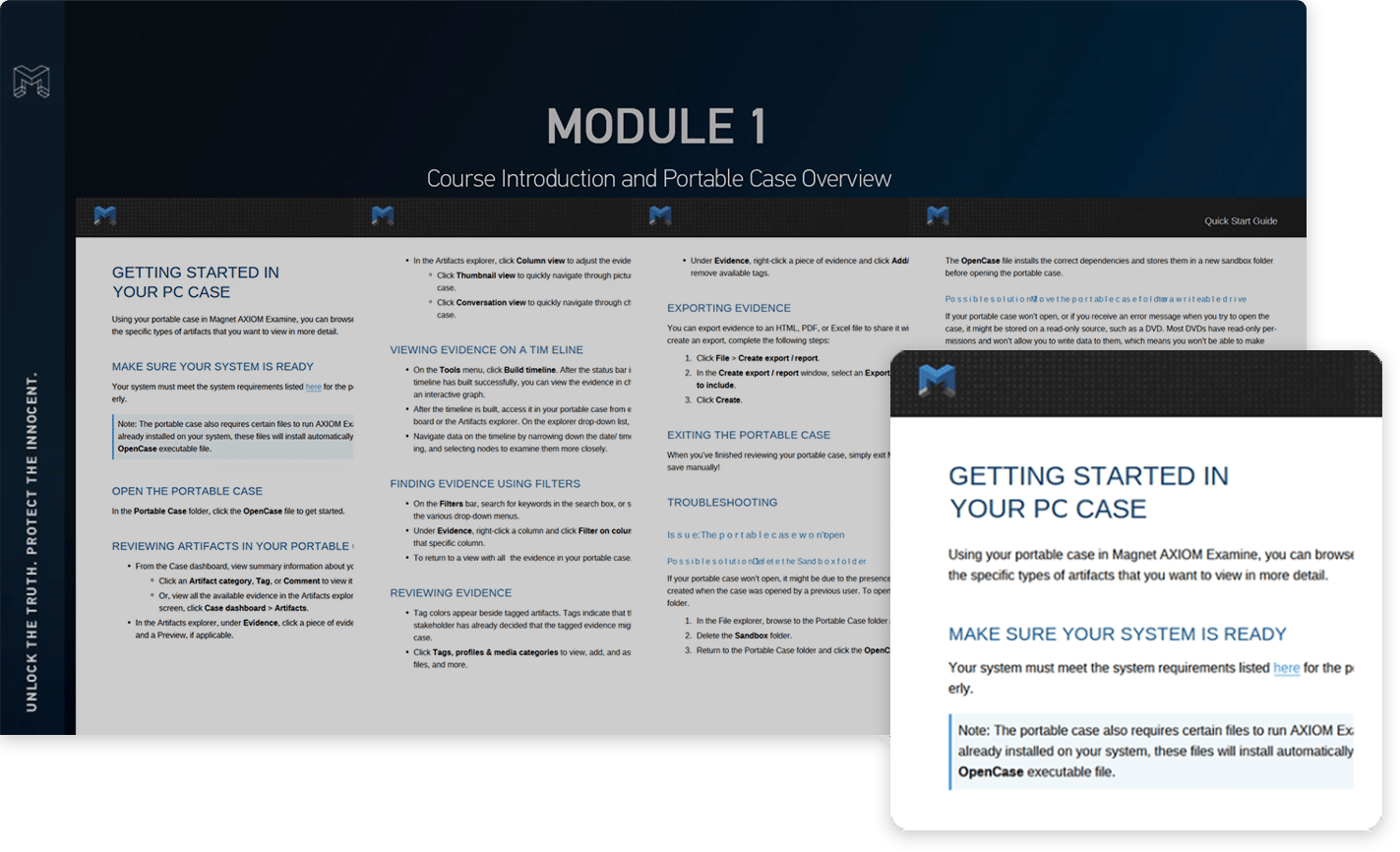
An introduction to this course and Portable Cases, along with system requirements and how to get started.
Module 2: Case Dashboard
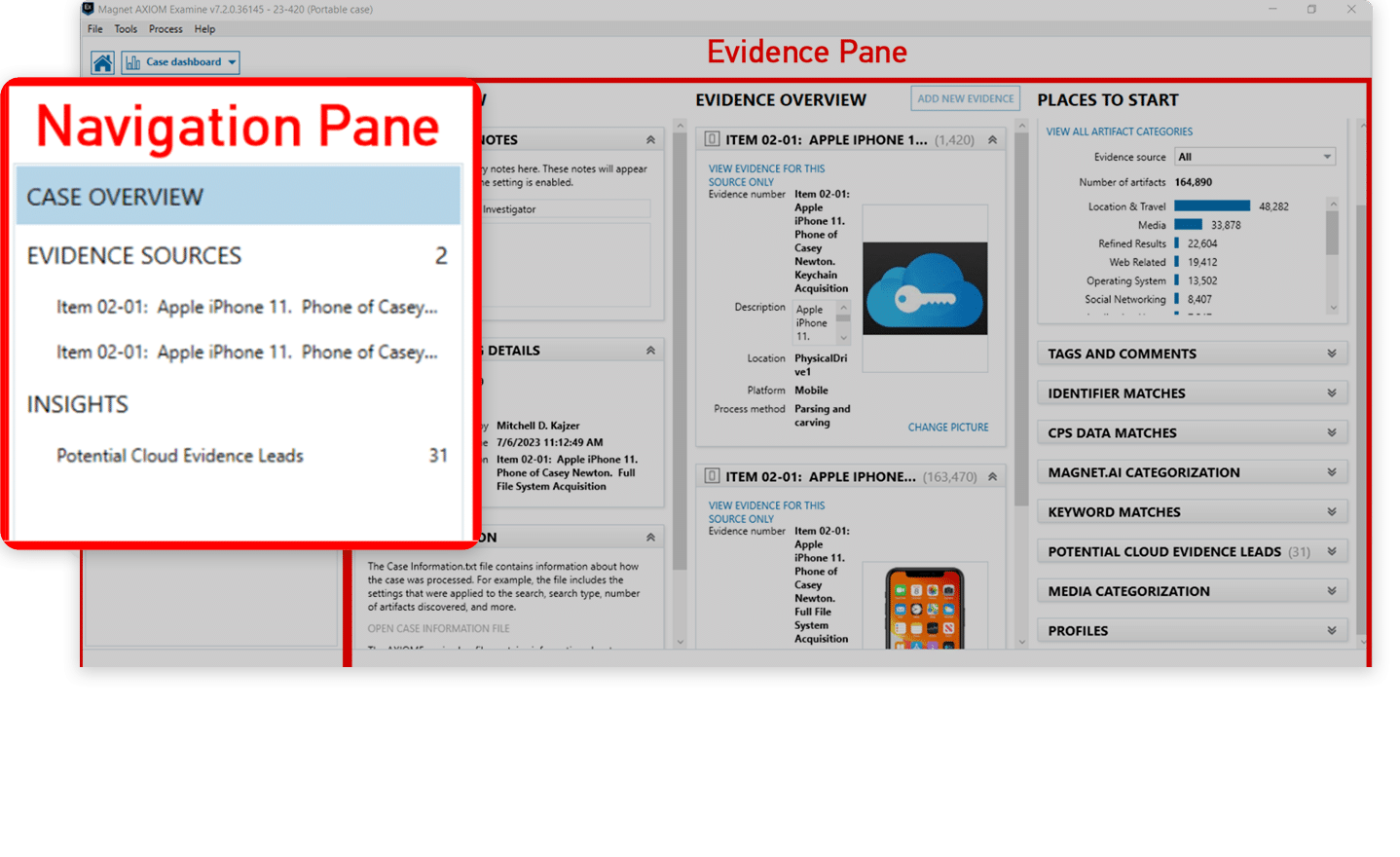
This module sets out key places to start in navigating the Portable Case.
Module 3: Artifacts Explorer
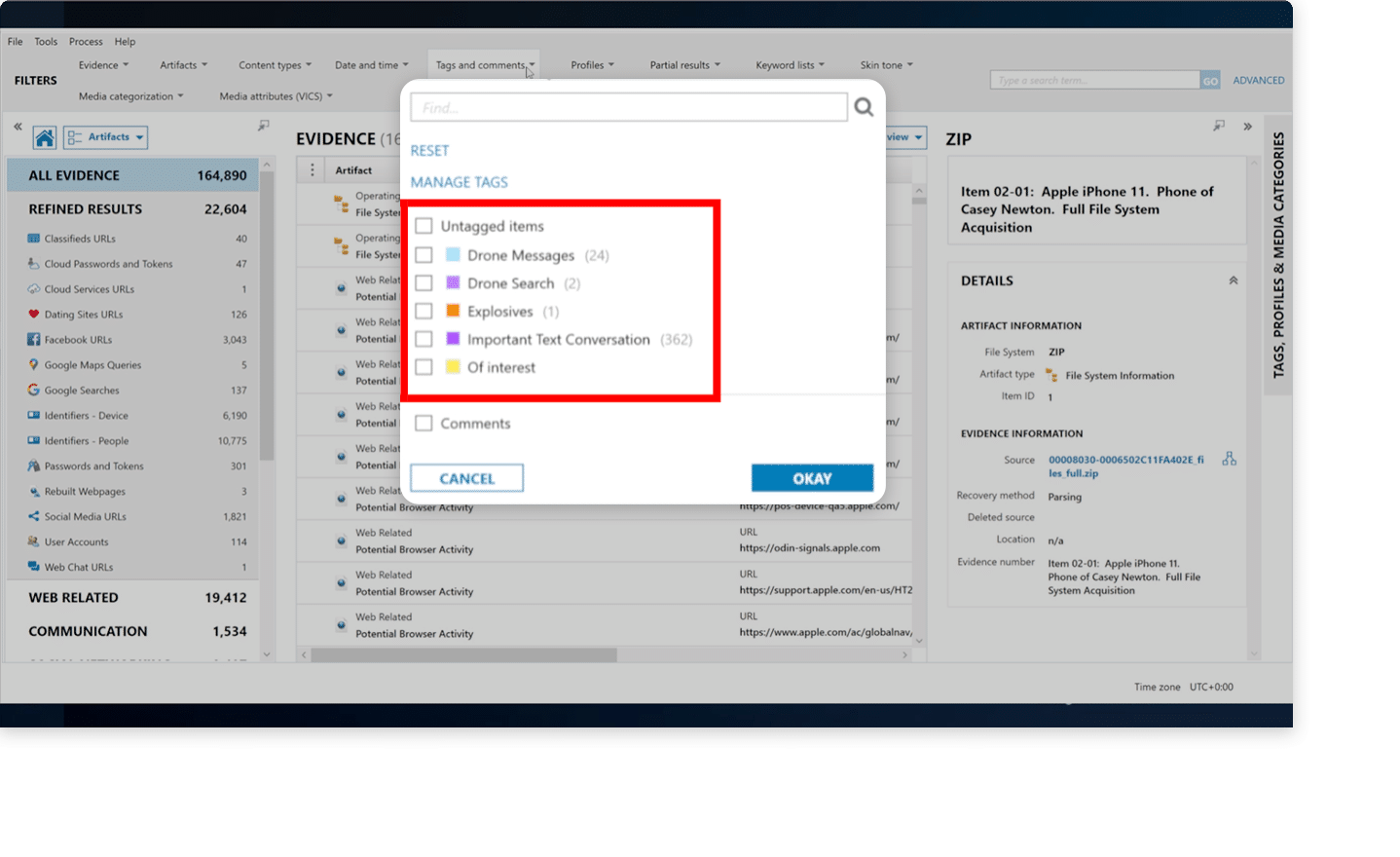
The core of the Portable Case – the artifacts – are examined in this module, demonstrating the use of Conversation View and World Map View to provide more comprehensive analytical features.
Module 4: Timeline Explorer
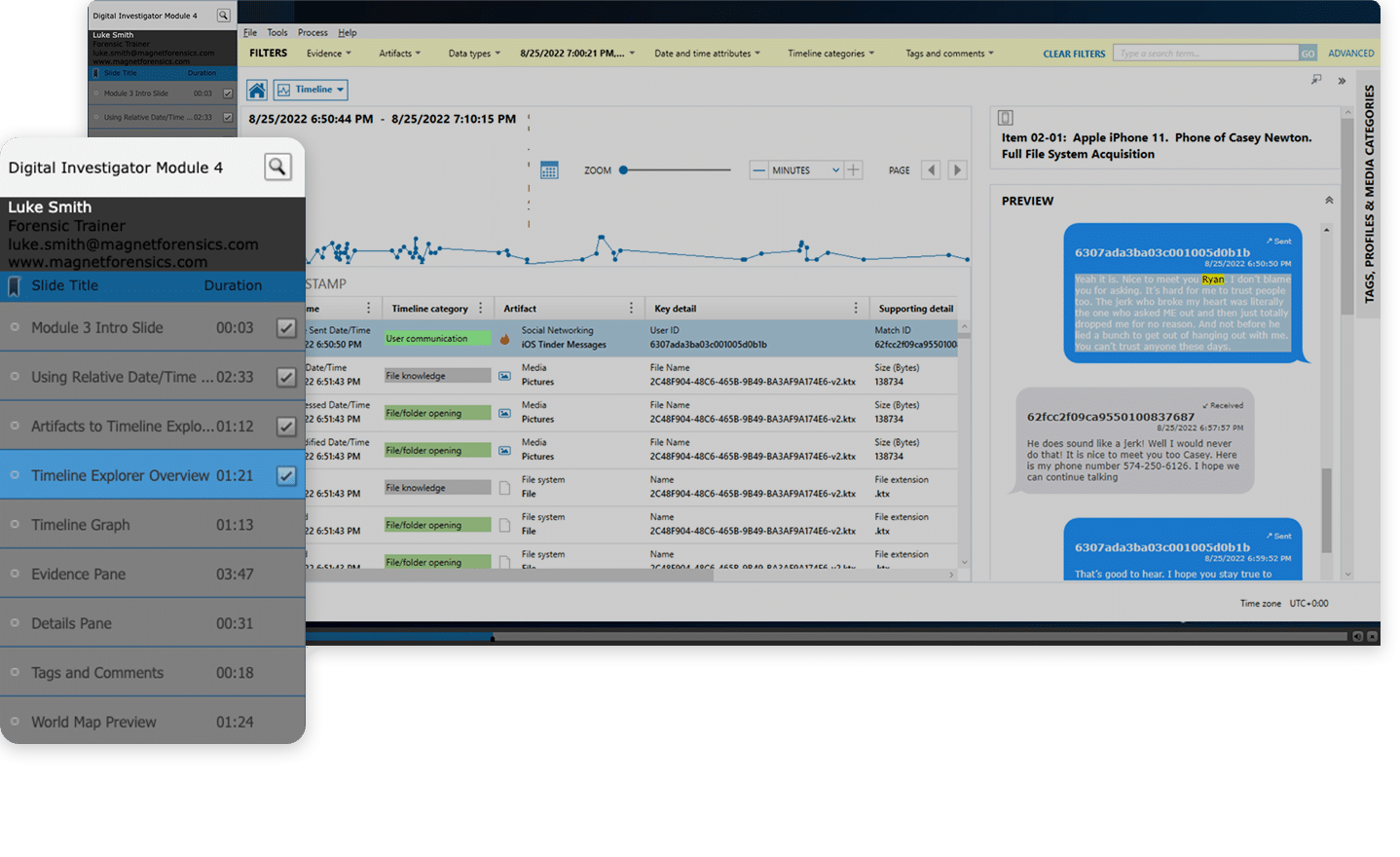
Examining your case using date and time filters can really help you hone your view of key evidence, allowing you to quickly identify spikes in activity to establish behavioral patterns.
Module 5: Overview of artifacts
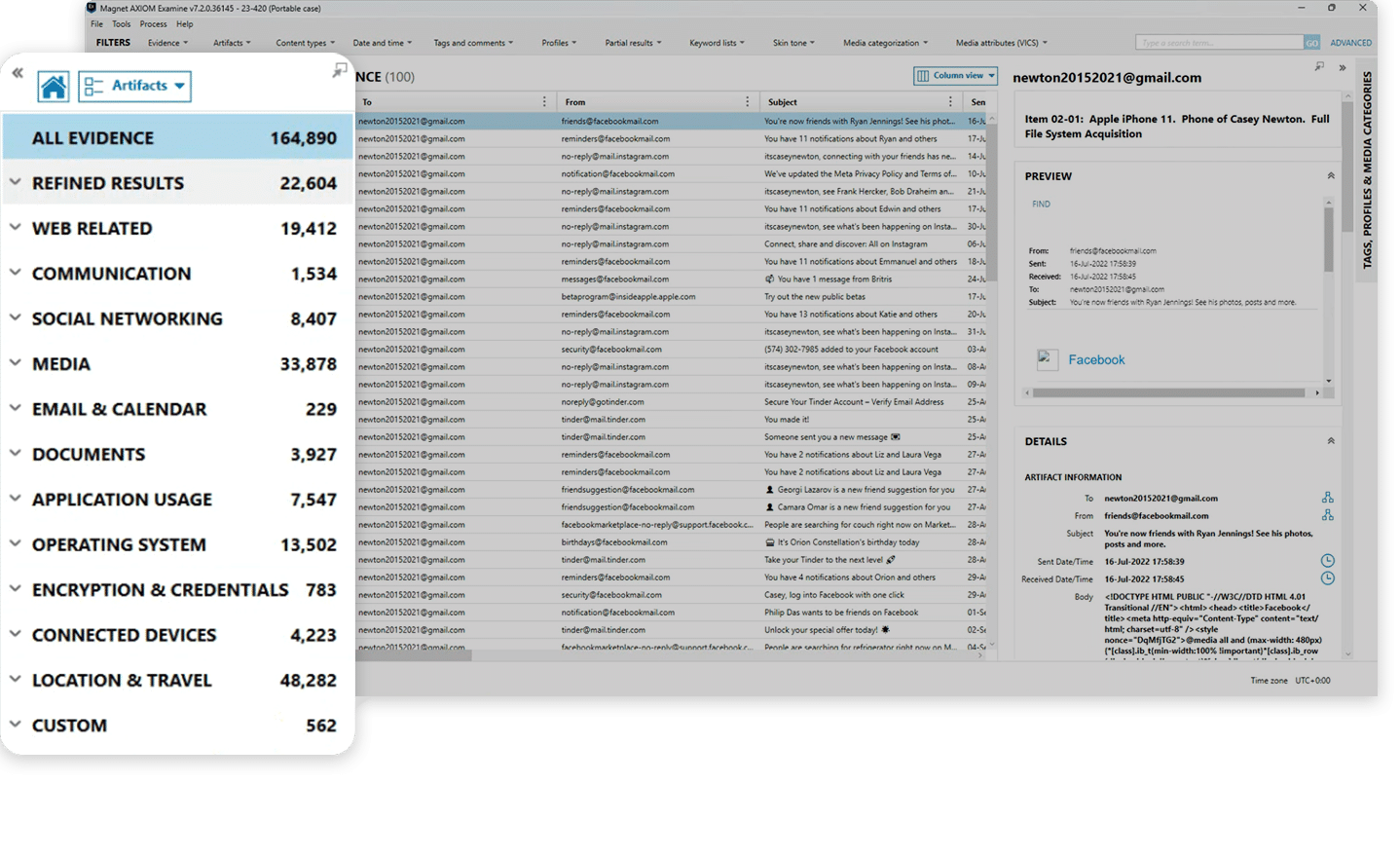
- Refined results and web related: Learn how key artifacts are summarized in Refined Results, and how internet activity is catalogued and displayed in the Portable Case. Start learning >
- Communication and social networking: The analysis of call records and messaging is discussed in this module, along with such social media networks as Facebook, Instagram, and TikTok. Start learning >
- Media: Reviewing media items allows the investigator to see photos taken or sync’d with the device, and pictures generated automatically as evidence of applications used. Start learning >
- Email and documents: Examine how emails are stored and best practices for sorting and filtering. Understand how metadata in documents can be incredibly useful in your investigation. Start learning >
- Application usage: Advanced filtering can be used to filter through the thousands of artifacts showing a pattern of usage on a mobile device. Start learning >
- Operating system: The core of the device records its state as it is being used, including cell tower locations, screen activation, and device accounts stored. Start learning >
- Encryption & credentials and connected devices: Learn how to uncover encryption recovery keys, cloud account passwords, and devices that have been connected – including Apple Health, Fitbits and other Bluetooth devices. Start learning >
- Location and travel: These artifacts store locations from Wi-Fi profiles, Google Maps locations and more, and you can learn how to plot these locations on a map – automatically. Start learning >
Module 6: Reporting
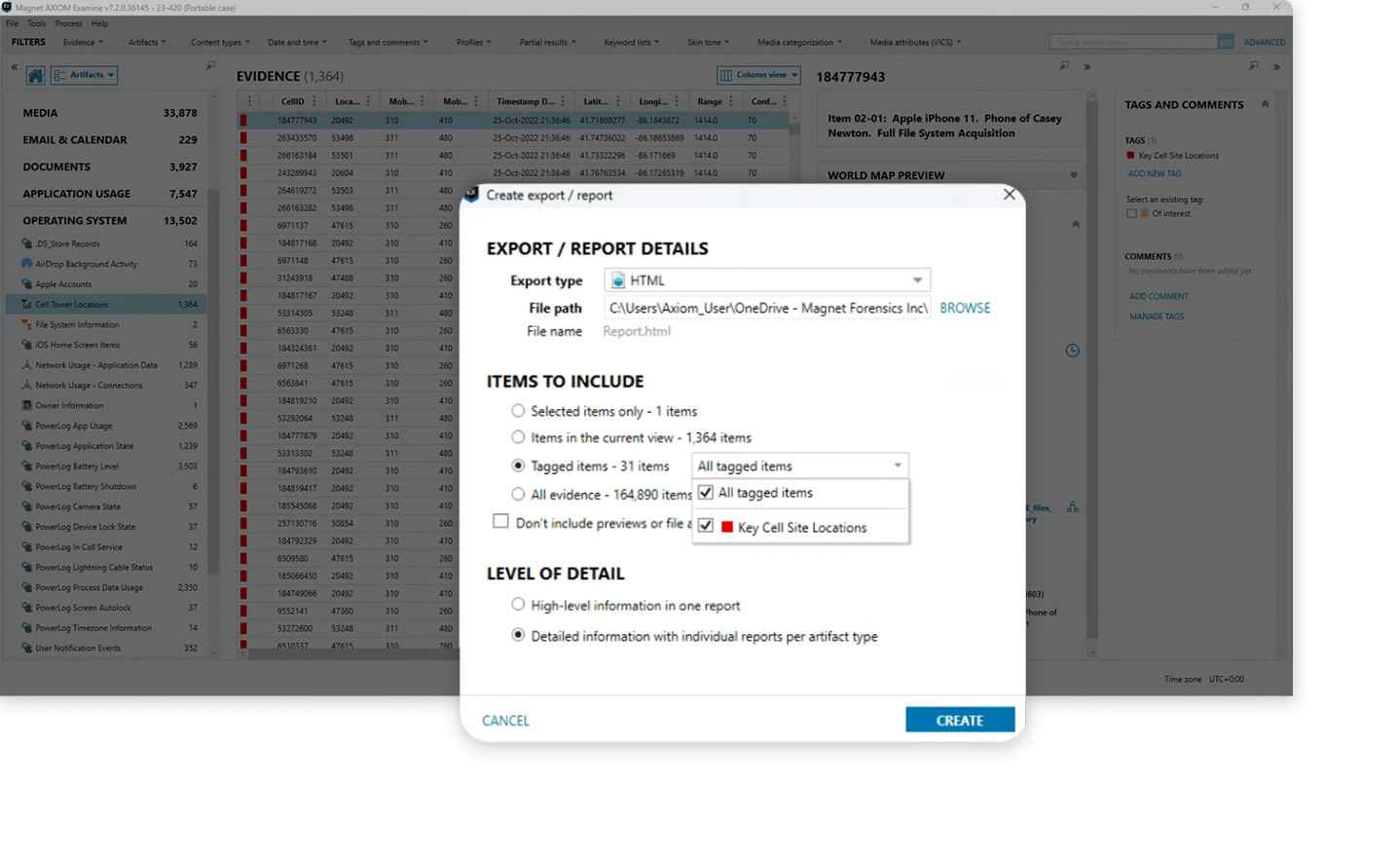
Learn how the crucial tagged artifacts discovered so far can be grouped and output into a single PDF, Excel or HTML report for stakeholders to review.

