
Yep, Magnet AXIOM Cyber Supports Slack!
As many of us know, Slack has become a dominant collaboration and chat platform used in environments around the globe since its inception in 2009. With over 10 million daily active users and 85,000 paying customers, examiners are frequently facing casework where Slack data plays a pivotal part in the investigation.
In this blog, we’ll discuss the different options examiners have when investigating Slack with Magnet AXIOM Cyber. If you haven’t already, make sure to download the latest version of AXIOM Cyber!
Where to Find the Data
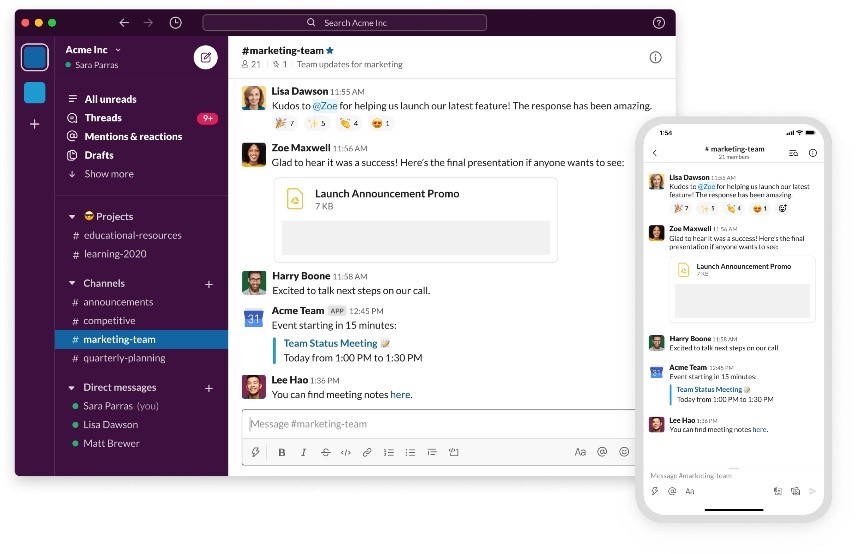
AXIOM Cyber supports multiple ways of ingesting Slack evidence. The first decision for examiners when loading Slack evidence into AXIOM Cyber is whether they would like to:
- Collect Slack data with AXIOM Cyber’s live acquisition capabilities, or
- Load the Slack compliance exports into AXIOM Cyber for processing.
For option 1, we’ve made acquiring data directly from Slack into AXIOM Cyber a quick three-step process. Before casework can commence, coordinate with your IT/SOC to make sure AXIOM is whitelisted for apps that can access Slack. You’ll only need to whitelist AXIOM once. Next, simply enter the account information and credentials of the account that is under investigation into AXIOM Cyber and select Analyze Evidence.
With the second option, loading the Slack Standard or Corporate Compliance Exports for processing into AXIOM Cyber is straightforward — point AXIOM Cyber to the .zip you’ve received from Slack.
Now if you are wondering where you can find these exports, we’ll walk through obtaining access to those now. Once again, you may need to work with your Cloud Ops/IT team so they can coordinate getting you access to the compliance exports. To access direct messages, channel information, and attachments without user credentials you’ll need the workspace owner to apply for the corporate export via ‘Settings & Administration’ from the menu in Slack (that’s right, Slack makes you apply to access your own information.)
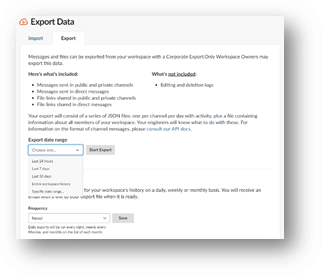
Once Slack has granted access to your workspace owner to export data, they’ll need to set the date range for the export which consist of a series of JSON files that are archived together. One option for the export is ‘entire workspace history’, for large organizations. I would not recommend this option due to the sheer size that export would make. Many organizations who already have compliance exports being generated select 30 days at a time for their archives.
Once exports are generated and after the initial download, they will remain on the account for 10 days before being deleted by Slack. It’s important to note the attachments that are shared in the workspace are not included in the export file. Slack provides a URL and token to retrieve the attachments, however if the token has been revoked the attachments cannot be retrieved.
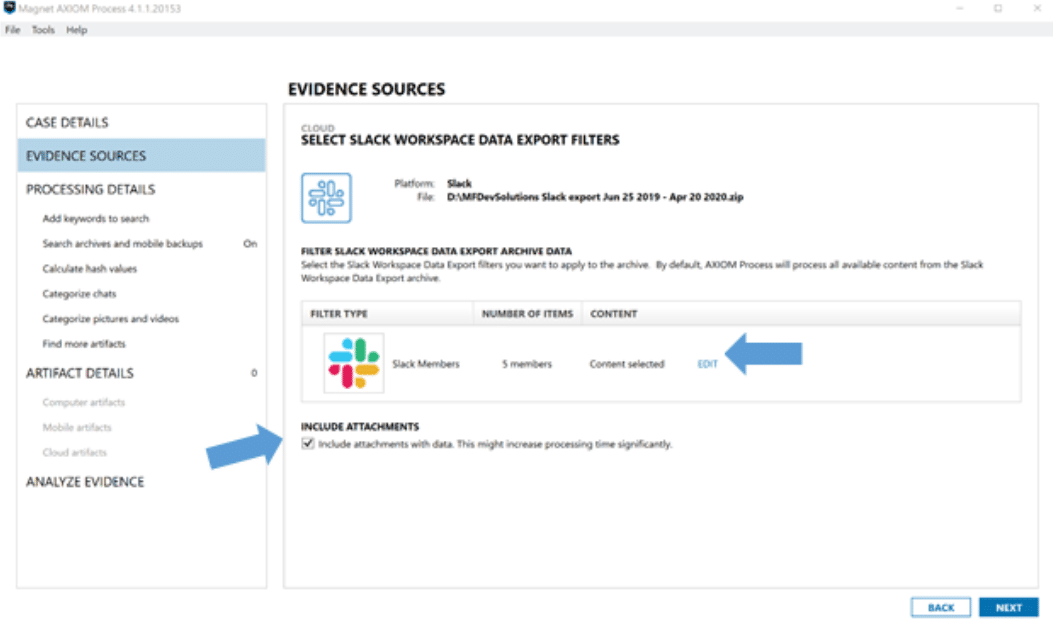
You will not need to decompress the archive file from Slack, keep it as is when loading into AXIOM Cyber. Once loaded, you’ll want to filter your data to expediate processing in AXIOM. As you can see in the image below, you can select “edit” to identify what users you want process data for as well as whether or not you want AXIOM Cyber to include the attachments data, which can increase processing time due to AXIOM Cyber downloading each attachment.
Once your evidence is analyzed by either use of the .zip export Slack provides or AXIOM Cyber’s live acquisition, you’ll be able to continue building your case with additional evidence sources within one case file as well as utilize analytical features like Connections and Timeline to complete the story of your investigation for stakeholders.
Differences between live acquisition and compliance exports with AXIOM Cyber can be seen below:
| Live Acquisition | Standard or Corporate Export Processing |
| Leverage user credentials to live acquire: – Channel messages (public and private) – Private chats – Group chats – Attachments (optional) | Process data packages exported from your slack environment. Supports: – Multiple user content – Channel Messages – Private Messages (Corporate export only) – Attachments (optional) |
If there are other cloud sources you’d like to see AXIOM Cyber acquire and process from please don’t hesitate to reach out to me at trey.amick@magnetforensics.com.