What is MRU (Most Recently Used)?
MRU artifacts, or Most Recently Used are a variety of artifacts tracked by modern Windows operating systems that provide crucial details regarding the user’s interaction with files, folders, and programs that may have been executed using the Windows Run utility. This is fortunate for examiners, because profiling user activity is something digital forensic examiners are often tasked with to corroborate what we believe happened on a computer. It is a method for supporting our theory of the user’s behavior on a system.
Analyzing files and folders which have been opened or browsed using Windows file explorer may help in the quest to determine what occurred on a computer around an important investigative moment in time. A date and time associated with the interaction of a file or folder can help create a timeline of activity on a particular device or serve as a pivot into AXIOM’s Timeline functionality.
This is why MRU artifacts are so valuable to digital forensic examiners.
As with many operating system artifacts, this data is not created for our use in forensic investigations, but they are often useful in supporting our theories surrounding user activity, specifically file and folder knowledge, on a Windows computer.
As with other artifacts featured in this series, it is worth repeating that it often takes more than one artifact to support an investigation.
MRU Data in the Windows Registry
The MRU data that will be covered here is recovered from the Windows Registry.
While the files which comprise the Windows Registry are stored in various locations on disk, think of an individual Registry hive as a logical collection of keys, subkeys, and values—which may be sourced from multiple Registry files—that are collectively loaded into memory when the operating system boots or a specific user logs in (https://docs.microsoft.com/en-us/windows/win32/sysinfo/registry-hives).
Registry data is structured in a tree format and each node within the tree is referred to as a key. These keys can contain data entries, also called values, or may contain subkeys, which in turn may contain data entries. Each key or subkey can have one or more values. (https://docs.microsoft.com/en-us/windows/win32/sysinfo/structure-of-the-registry).
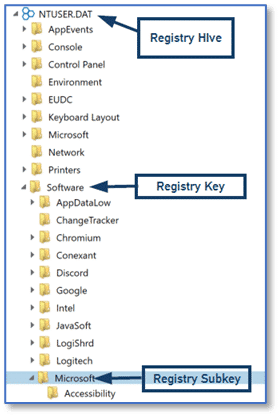
Keys and subkeys within the Registry contain values and there can be one or more values stored. The values may also include data, but in some instances the value itself is the functional part of the entry. Meaning examiners may find instances within the Registry where a value alone exists in the key as well as instances where values contain data. Using the Registry explorer in AXIOM Examine, we can see this relationship showing the Name column which corresponds to the value and the Data column which corresponds to that value’s data.
Most examiners are familiar with the NTUSER.DAT Registry hive that is created in the root of each Windows user account profile folder. Many operating system artifacts are sourced from the Windows Registry and items recovered from the NTUSER.DAT Registry hive may be particularly useful as they are associated with a specific Windows user account, potentially helping to provide attribution in a forensic investigation.
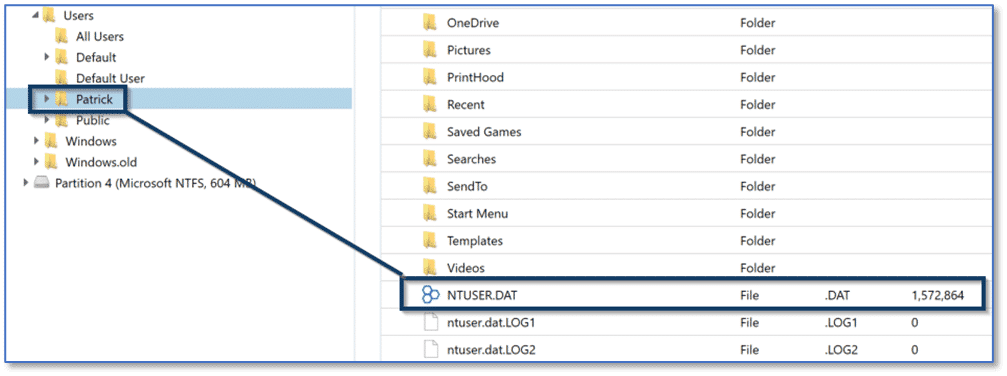
Within each user’s NTUSER.DAT Registry hive there are several items of interest related to MRU data that are sourced from different subkeys and manually examining this data requires multiple steps. One location of interest is a key labeled RecentDocs which potentially contains a tremendous amount of data useful for corroborating the files and folders a Windows user account interacted with. The RecentDocs key is found at:
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
Other items of interest are related to folders that are accessed by a Windows application using the common Open / Save dialog which are found at:
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32
or files that are accessed by a Windows application using the common Open File or Save File dialog found at:
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU
And finally, items of interest regarding commands a user runs via the Windows Run utility are found at:
NTUSER.DAT\ Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
RecentDocs – Manual Examination
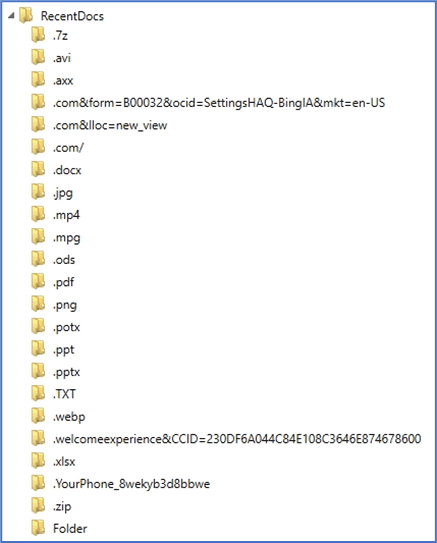
The RecentDocs key is tracking recent file and folder access and is populated via Windows file explorer when a user opens folders or opens or saves files. Simultaneously, within the RecentDocs key, examiners will find subkeys for the different file extensions which have been accessed using File Explorer to open or save files or open a folder.
We can walk through some examples to see how this looks using the Registry explorer in AXIOM Examine. First, we can navigate to the NTUSER.DAT Registry hive and select the RecentDocs key for a user account labeled Patrick. Notice at the top of the graphic, AXIOM’s Registry explorer displays the path of key—subkey entries necessary to arrive at the RecentDocs location. This is particularly useful as the very nature of Registry hives results in a hierarchy which can be confusing to navigate and easy to become disoriented. This can be made worse by the fact there are multiple locations in the Registry where subkey paths are similar to other locations.
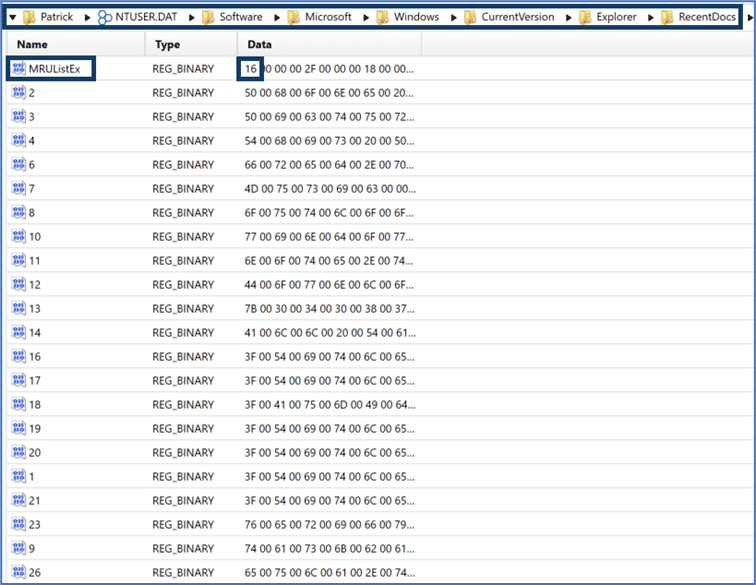
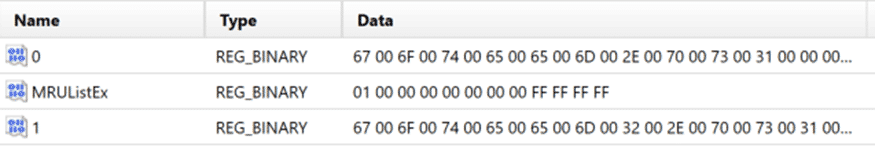
Within the RecentDocs key examiners will find value entries including MRUListEX and numeric values. Microsoft takes an interesting approach to the way the MRUListEx data entry is populated which can lead to some confusion during manual analysis. In the RecentDocs Key graphic above, we can see the first entry is 16. First, the MRUListEx data entry tracks an ordered list of files or folders accessed, with the first item listed in the value data being the most recently accessed and the last entry being the oldest.
Initially, it would appear we could reference the data item “16” from the MRUListEx entry and then select the corresponding value from the Name column in AXIOM’s Registry explorer for additional information. However, the MRUListEx data is stored in hexadecimal and the values in the Name column are stored in decimal, so we must first convert the hexadecimal value to decimal to locate the correct value in RecentDocs.
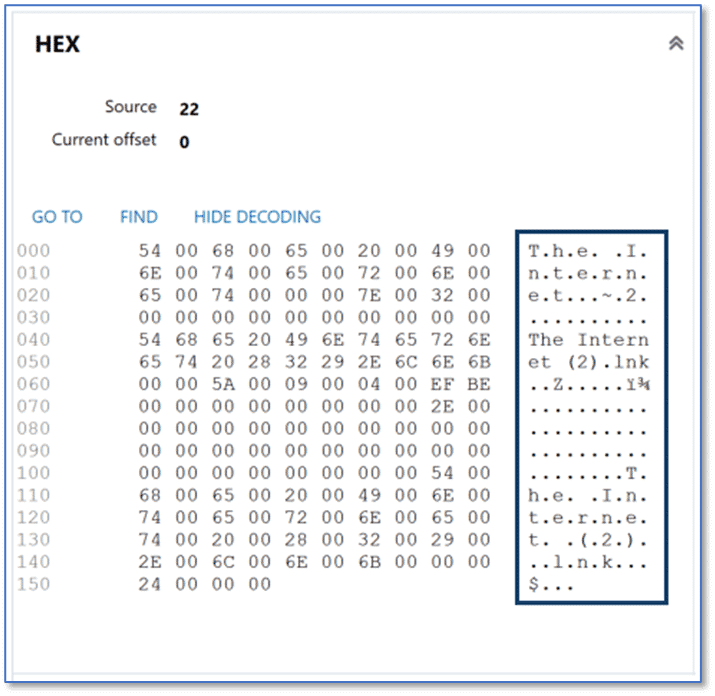
For our example above, the first entry of 0x16 converts to decimal 22. Scrolling down in the Registry Explorer within AXIOM Examine we find the entry with a Name value of 22. The Details Pane of the Registry explorer shows the content stored within the Data section for this entry. The Data field contains a string of numeric values, in this case beginning with “0x54006800650020”. These characters are hexadecimal values which can be mapped to ASCII characters using an online resource like RapidTables (https://www.rapidtables.com/convert/number/hex-to-ascii.html).
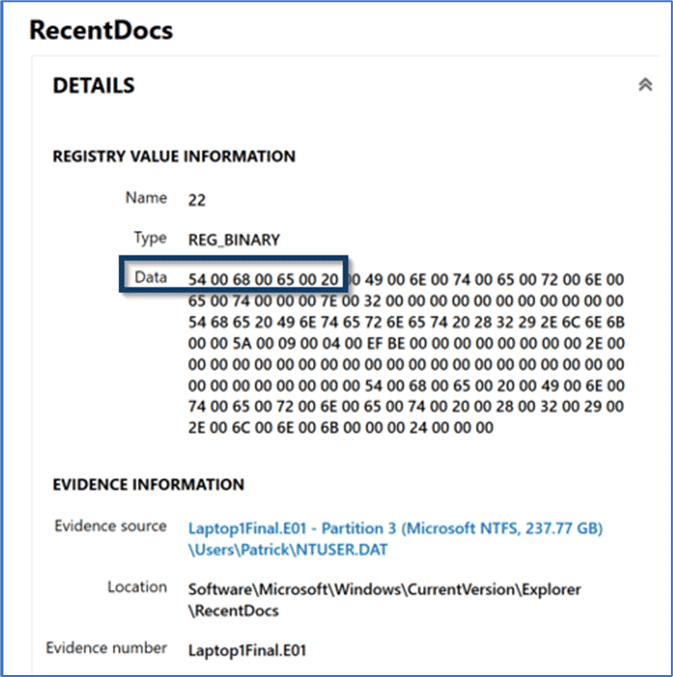
Or by consulting the Hex card shown in the Details pane of the Registry explorer view in AXIOM Examine which provides the conversion for us, making this process even easier.
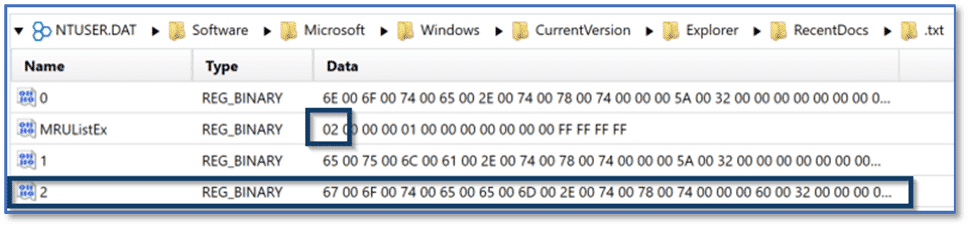
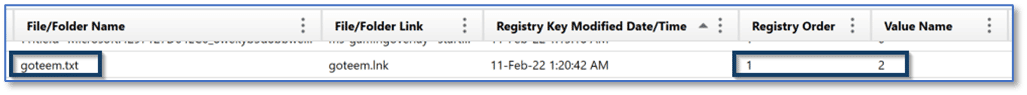
As mentioned previously, there are subkeys within RecentDocs for Folder along with the different file extensions a user account has interacted with. These subkeys will each contain an MRUListEx entry with hexadecimal values and data entries with decimal values for the individual items accessed which are populated the same as the RecentDocs key. As an example, below is the subkey entry for the TXT file extension. The MRUListEx entry indicates the most recently accessed file as 0x02 or decimal two (2).
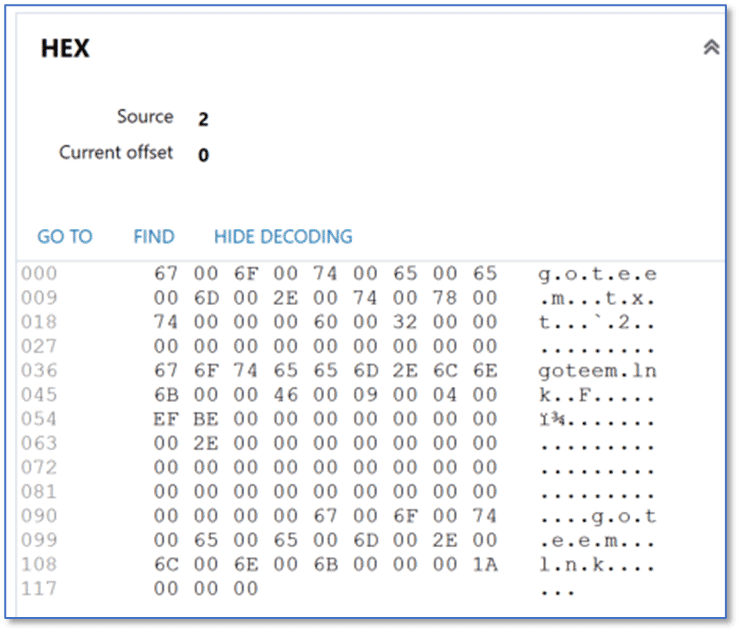
The corresponding entry for item two shows that a file named “goteem.txt” was the most recently accessed file with the TXT extension associated with the Patrick user account on the computer.
RecentDocs – Not-So-Manual Examination
Fortunately, this data is presented to us in an even easier to understand way using the Artifact explorer of AXIOM Examine. Depending on user activity on a Windows computer, we may be able to find artifacts within four different artifact categories in AXIOM Examine: MRU Folder Access, MRU Opened-Saved Files, MRU Recent Files and Folders, and MRU Run Commands. Our examples above focused on the RecentDocs entries, which are displayed in the Artifact explorer within the artifact category for MRU Recent Files & Folders.
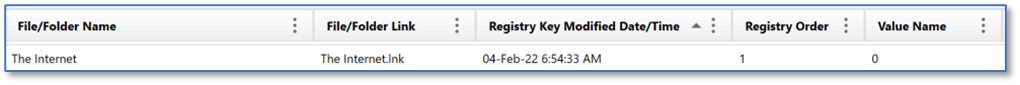
Using the same examples from earlier, selecting the MRU Recent Files & Folders artifact category in AXIOM Examine, we can again see that a LNK file named The Internet was the most recently accessed file, according to the RecentDocs key. Also note that AXIOM is displaying the Value Name of 0, as seen in the Registry explorer view, and showing the Registry Order value of 1, indicating this is the first item from the MRUListEx entry from the RecentDocs key, just as we saw previously. AXIOM parses the hexadecimal data within all of the MRUListEX entries in RecentDocs and its associated subkeys, and then uses the corresponding decimal values from the Name column to present this information to examiners.
Because the MRU Recent Files & Folders artifact category is presenting both the content of the RecentDocs key and the subkeys for individual file extensions and folders, examiners are likely to find instances where there are multiple items listed in the evidence pane with the same Registry Order value. This is simply because we would expect to find an item with a Registry Order value of 1 for RecentDocs, and item with a Registry Order value of 1 for Folder, and item(s) with a Registry Order value of 1 for each of the file extensions parsed from the RecentDocs subkeys. Using AXIOM Examine’s filtering and sorting capabilities can make review of this data much easier for forensic examiners.
Similarly, we can apply a column filter to the File/Folder Name column within the MRU Recent Files & Folders artifact for “TXT” and again see that a file named goteem.txt was the most recently accessed text file. Also note that AXIOM is displaying the Value Name of 2, as seen in the Registry explorer view, and showing the Registry Order value of 1, indicating this is the first item from the MRUListEx entry for the TXT subkey.
Other MRU Artifacts in AXIOM
Depending on user activity on a Windows computer, we may be able to find artifacts within four different artifact categories in AXIOM Examine: MRU Folder Access, MRU Opened-Saved Files, MRU Recent Files and Folders, and MRU Run Commands. Our examples above focused on the RecentDocs entries, which are displayed in the Artifact explorer within the artifact category for MRU Recent Files & Folders. The other potential MRU artifact categories are:
MRU Folder Access
The MRU Folder Access artifact category details information concerning folders accessed by a Windows application using the Open / Save file dialog. This functionality is often accessed by third-party applications which means as an examiner, you may find evidence of access to folders which were browsed during file open or save operations associated with a variety of programs on the system. Windows Vista and later may include entries that reference a PIDL path, which contain GUID values, instead of relative path strings.
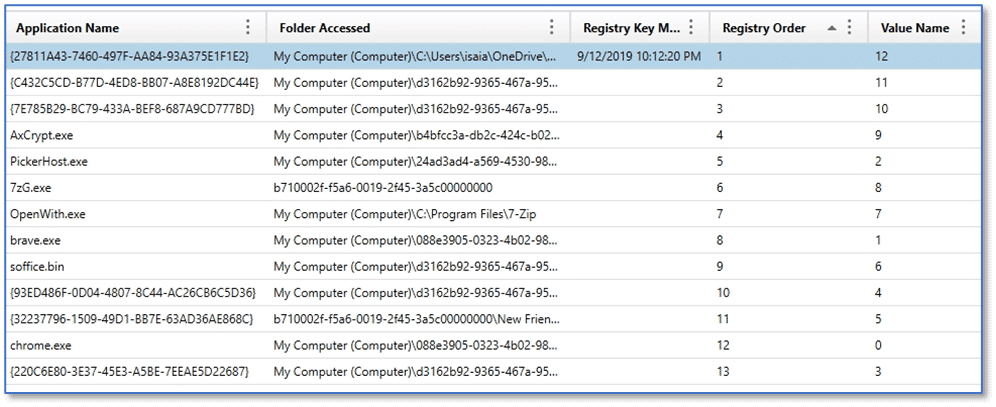
For Windows Vista and later, this data is stored at:
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32
MRU Opened-Saved Files
The MRU Opened/Saved Files artifact category details information about the last files accessed by an application using the Open File or Save File dialog window. As with the MRU Folder Access artifact category, Windows Vista and later may include entries that reference a PIDL path, which contain GUID values, instead of relative path strings.
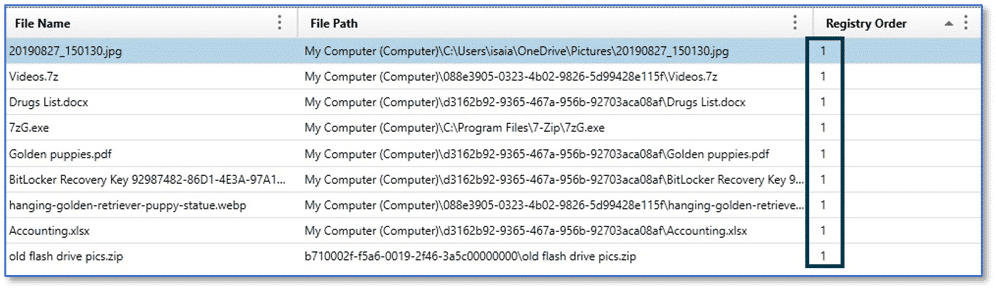
For Windows Vista and later, this data is stored at:
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU
Note in the graphic above, each of the items listed is showing a Registry Order value of “1”, but as examiners we know they cannot all have been the most recently opened or saved file. Reviewing the File Name column with this artifact category shows us that each of the files listed is a different type. We have a JPG image, 7z archive, docx document file, and so on. The OpenSavePidMRU uses a similar mechanism to the RecentDocs key where there is an overarching list of file access, regardless of file extension, along with subkeys for individual file extensions.
MRU Run Commands
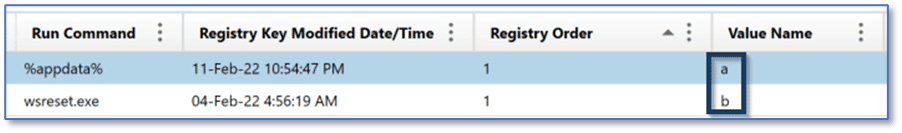
The MRU Run Commands artifact category details information about commands a user executed from the Run utility for Windows. The Run utility can be accessed several ways, such as right-clicking on the Start icon and selecting Run from the menu, or the keyboard shortcut Windows+R. The Run utility can be used to launch applications or executables on Windows system and can even be used to access Windows operating system components such as Control Panel. The data contained in the MRU Run Commands artifact category is sourced from:
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
RunMRU stores data in a similar fashion to what we have seen with other MRU artifacts, but with a variation on the naming convention. The RunMRU subkey contains an MRUList value, as opposed to MRUListEx, with a Data column using the characters of the English alphabet tracking the order items were launched using the Run utility, as opposed to hexadecimal values.
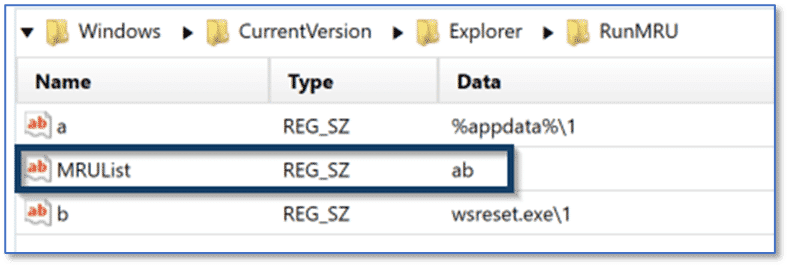
As with the other MRU artifacts, AXIOM parses the data contained within the MRUList value and presents the data to examiners in the appropriate order.
Let Us Know Your Thoughts
I hope this post regarding Windows MRU artifacts has been useful. I welcome any questions or feedback, including suggestions for other artifacts you would like to see featured in upcoming posts (kim.bradley@magnetforensics.com).