
Pontificating on the Perplexing Preferences Proliferated by Safari
Within the macOS operating system, Safari is the built-in web browser that drives user’s interactions with the web. Surprisingly to many, Safari is often seen as the second most used browser as collected by report user agents behind Google’s Chrome. Safari has some very interesting behaviors when it comes to the macOS platform. While many users may keep the default options, it’s the default options which can cause a lot of problems for the forensic examiner.
First, let’s start by examining the default preferences within the Safari browser. From a live-running system, users can access this by pressing Command+, while the Safari browser is in focus. With mac 10.15, the following screenshot details some of the default preferences set by the operating system:
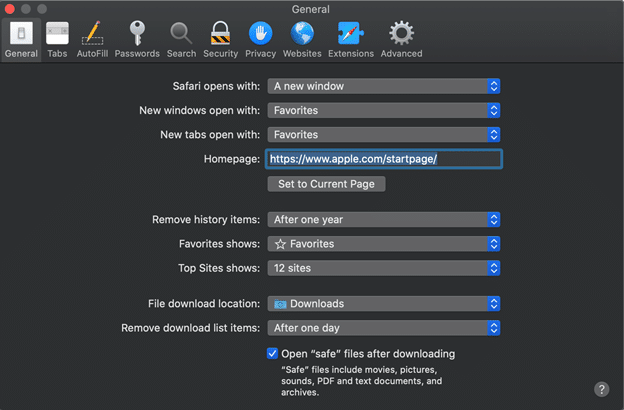
Two of these in particular can vex an examiner during an investigation. First, the “Remove download list items” is set to ‘After one day.’ As if the Downloads.plist file wasn’t difficult enough keeping only the past 20 downloads, it seems that after one day, the downloads list will also be cleared as well. While there are other ways to track files that were downloaded by Safari (here’s looking at you Quarantine Events and Extended Attributes), that’s a topic for another blog post.
The second vexing listing in the screenshot shows that the checkbox for ‘Open “safe” files after downloading’ is checked by default. This makes tracking attribution of a file difficult for an examiner as a user could claim “Hey, I never opened that file” even though attributes show a different story. Maybe the user didn’t open the file, the system actually triggered it for them after considering the picture, PDF, archive, etc. is considered “safe.”
Other settings of note are that Safari will automatically remove the history after one year, point the downloads to the ~/Downloads directory of the logged-in user, and will have the default home page be set to Apple’s own. The most interesting thing is that the file that tracks these preferences actually won’t store records about many of these preferences if the defaults are still set!
Speaking of the file that contains them, users can find this file in the “com.apple.Safari.plist” file found within the ~/Library/Application Support/Containers/com.apple.Safari/Library/Preferences folder. This plist will contain several important records for the user’s preferences but it’s actually the absence of some listings that are telling in itself.
AXIOM will automatically parse this property list file to recover the system or user-set preferences under the Safari Preferences artifact.
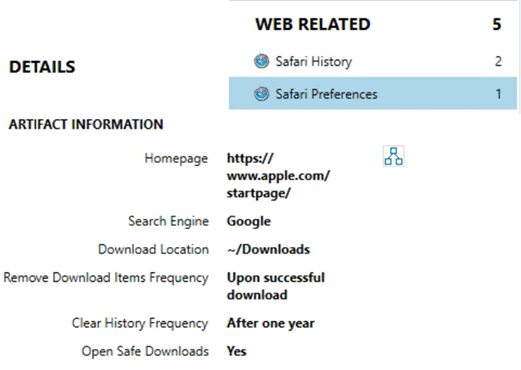
Because some of the keys such as the default search engine, download location, remove download frequency, and clear history are actually not present in the property list file unless they have been changed by the user, AXIOM will detect the missing keys and populate the artifact with the default values.
There are additional preferences that may be of interest to the examiner than what are stored within just this file. Because Apple couldn’t make it easy for us, right?
There are several preferences which can be found within the “Websites” section of the Safari Preferences that could pose importance to the examiner. For one, when discussing downloading a file from a website, a pop up box will first prompt the user to either Allow or Deny that specific website permission.
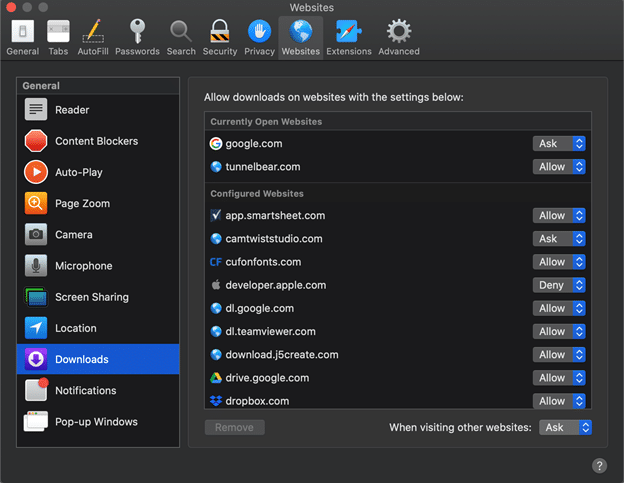
By default, users will be asked on each website. There is however a global preference that the user can set and change it. Some (but not all) of these preferences can be tracked by a database within a different area of the Safari structure. Under the PerSitePreferences.db file which can be found in the ~/Library/Safari directory, examiners can track information on whether or not a file has prompted and has been allowed or denied the ability to download a file.
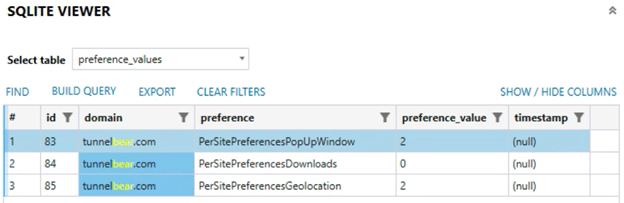
The ability to track if a site is allowed to display pop-up windows, can download files, or can use geolocation are set within this database. The numbers are tracked back to the following values:
| Listed Preference in Safari | Listed in Database |
| ALLOW | 0 |
| ASK | 1 |
| DENY | 2 |
While these are some of the more important preferences to the examiner, others such as if a site is allowed to display notifications in the notification center can be tracked in yet a DIFFERENT file. In the ~/Library/Safari directory, a UserNotificationPermissions.plist can show if a user has accepted that preference or denied it for a specific site.
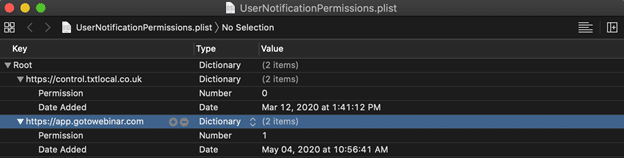
As more preferences raise more questions, these above mentioned locations should be a good jumping off point for most investigators. Until this, we’ll keep searching for more information to find these preference values and their meaning!