Maximizing the Partnership Between GrayKey and Magnet AXIOM
Magnet Forensics and Grayshift have partnered to provide law enforcement the tools they need to acquire and process the most data from iOS devices. This partnership is a result of our joint mission to help our law enforcement customers seek justice and protect the innocent.
For many years law enforcement agencies have struggled to acquire important information from these devices. While GrayKey has allowed us to potentially brute-force the passcodes, it also enables Examiners to acquire more data than any other solution on the market and then review in a tool such as Magnet AXIOM.
There are several different types of images that can be generated by GrayKey, including BFU or Before First Unlock, AFU or After First Unlock, or Full Filesystem images. Regardless of which type of image an examiner can acquire, each type can be ingested into Magnet AXIOM and processed for information.
In order to load the images into Magnet AXIOM, users only need to select “Mobile -> iOS -> Load Evidence -> Images” from the Evidence Sources area of AXIOM Process.
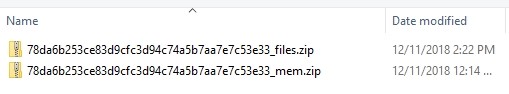
Once the evidence selection screen loads, users can select any of the image format types generated by the GrayKey for processing. These images are stored by the format “<udid>_files_<image type>.zip” which will tie back to the Unique Device Identifier of the iOS device in question. The type of image will reflect if this image is a BFU, AFU, or File System image acquired from the GrayKey device.
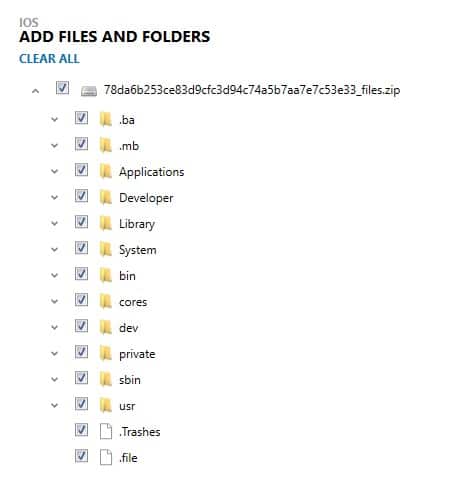
Once a File System image has been selected and loaded, users will be able to selectively pick any or all areas of the file system they want AXIOM to be able to scan for information. This helps users who are low on time or simply looking for very specific artifacts in the file system.
The only difference in loading GrayKey data is around loading the keychain data which will include exportable and non-exportable values for review. In order to load the keychain, users need to follow a similar procedure as the images, but instead of selecting “Images” they will select “Files/Folders” and direct AXIOM to the “udid_keychain.plist”
Once all of your selected GrayKey data is ingested into AXIOM, examiners can then decide which artifacts they wish to scan and even use advanced features such as AXIOM’s Dynamic App Finder or Custom Search by File Type in order to locate additional data with the images to find relevant evidence in.
Once the information has been loaded into Magnet Examine, there is a wealth of artifacts that Magnet has recently added to the product to maximize the information available to users. In this blog, we will detail several important artifact pieces you can expect to find in these images.
Write Ahead Logs
GrayKey can obtain a full-file system image of the device which means that temporary or support files that exist with our standard artifacts are now available for review. A prime example of this is the sms.db-wal file that lives in the same directory as the sms.db. The sms.db allows examiners to recover and parse iMessages, SMS messages, and MMS messages. However, because this database utilizes the “write ahead log” functionality of SQLite, messages are in fact written to the sms.db-wal file before being committed into the main sms.db. This can cause issues in recovering potentially deleted messages depending upon how long the messages were on the device before being deleted. If messages are deleted as soon as they are sent/received it’s much less likely to be able to recover these messages from a standard iTunes style extraction. However, since GrayKey allows us to extract the full file system, we now have access to this file and AXIOM will attempt to carve for any traces of messages left behind in the write ahead log including potentially deleted messages.
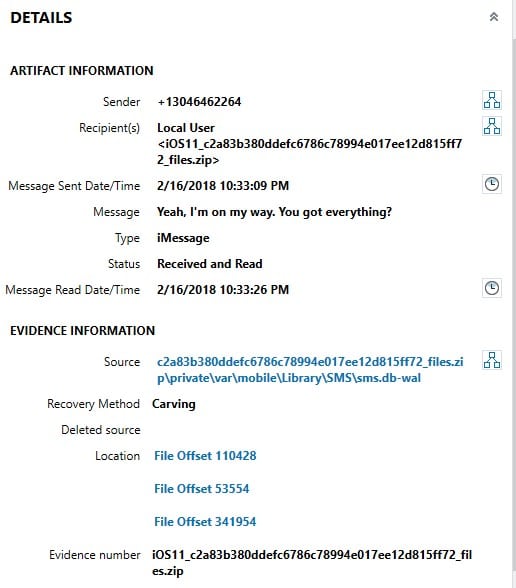
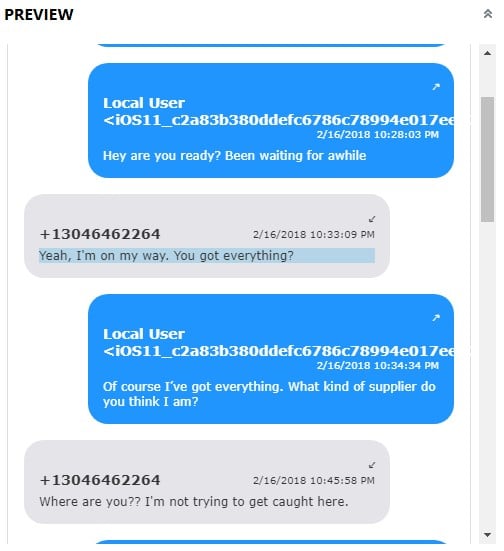
In the above examples, you can see some examples of a message that have been recovered from the write ahead log of a sms.db and how AXIOM can still link much of the information back together including timestamps, directionality, and use Connections to map communications between users. The write ahead log recovered messages are also still part of the chat threading options in AXIOM so users can see these data points threaded out in a chronological view for reviewing.
Third-Party Application Data
In standard iTunes-style backup images developers can be very selective about what from their applications they want to include. Prime examples of this include Facebook, Instagram, and Twitter who don’t include key files into these backups. Since AXIOM gets access to the full file system from GrayKey images, this third-party application data is available to us again. Some brief examples in AXIOM are Facebook Messenger messages, Instagram Direct Messages, and Twitter Tweets.

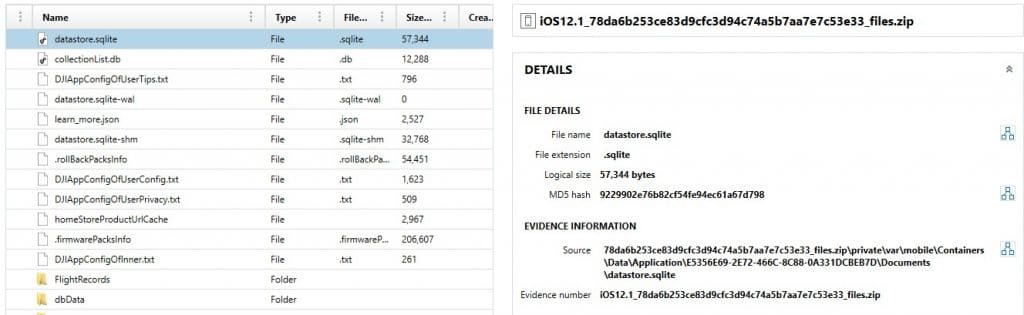
This also gives the examiner a chance to dig deeper into applications that aren’t normally processed by artifacts such as this example showing the recovery of data for the DJI Go application.
Apple Mail
The Apple Mail application (Mail.app) has been frustrating many forensic examiners since the days of the iPhone 4 as it’s information has not been available since then. Apple protects the Mail.app data at some of the highest levels of the file system, therefore this information will only be available in a Full File System image once the passcode has been determined.
Once found, AXIOM Examine will display the saved to/from, subject, date sent, date received, summary, and read status of emails that are recovered from this application. These mails can provide valuable communication points but can also inform an examiner about other services that they may need to look for.
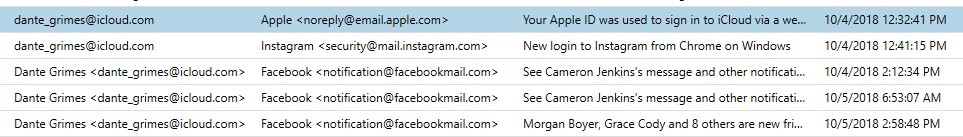
In addition to the data found within the Mail application, AXIOM Examine may also recover artifacts known as Apple Mail Fragments from different sources even if a full filesystem isn’t available. These fragments can help examiners key in on email addresses being used on a device in order to launch investigations from the service provider’s end while waiting for the device password to be recovered in order to obtain all of the data from the device. For example, these email fragments may be recoverable from a process memory image generated by GrayKey from a device in the After First Unlock (AFU) state.
Web Cache and App Cache
In addition to recovering standard Safari data, these file system images allow us to recover additional web data such as Safari App Cache information. Since the web cache can give us some context as to what users are viewing on URLs, this information can become very valuable in certain case types where users are viewing illicit material online.
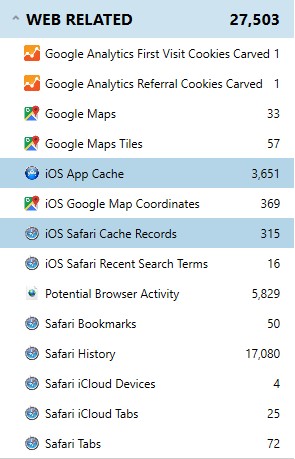
The App Cache artifact can allow examiners to see what is being stored within the cache for specific artifacts. Since applications typically have built-in browsers but don’t store many logs of web history for those browsers, this may give an examiner a chance to recover information that was found when clicking on a link inside a third-party application.
Operating System Data – KnowledgeC
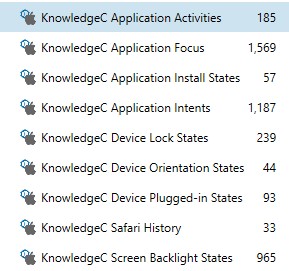
The Operating System category within AXIOM Examine has many artifacts available exclusively to these file system images. One such great example is the KnowledgeC artifact set. These artifacts can help to determine a pattern of usage of an application or a user in general by looking at multiple artifacts to map out such activity.
Operating System Data – Network Usage
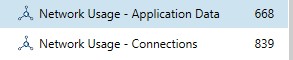
The Network Usage artifacts under the Operating System category allows examiners to see Wireless access points the users have communicated on as well as cellular towers users have sent data to. The Network usage – Connections artifact will display the Cell ID or MAC Address depending on the type.
The Network Usage – Application Data artifact works a lot like Windows SRUM. This artifact allows examiners to see which processes have used data, how much data, and over what connection types including WiFi, Cellular, and Wired. If a user claims they have never used an application, searching for the application ID can help to prove or disprove this and show exactly how much data has been sent across the networks. Note: this information can be reset by a user clearing their Usage statistics on their settings so it’s not a complete history since the device was first powered on.
Operating System Data – Screen Time
New to iOS 12, the Screen Time data that is generated by iOS allows examiners to track within 1-hour intervals how much an application was used, how many notifications it generated, and how many times the device was picked up due to this application. This information can be incredibly valuable but is a key reason why devices must be acquired immediately upon seizure.
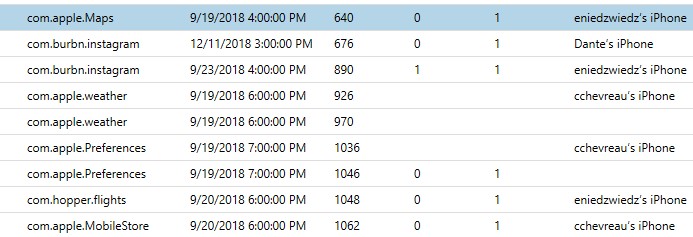
Location Data
There are multiple points of location data storage within modern iOS devices. Cached locations and Frequent Locations can be incredibly relevant in helping to determine a location or region that a user has visited. Other information such as Apple Pay transaction data can also be viewed within AXIOM Examine’s World Map View in order to map out these location points to make sense of a user’s activities.
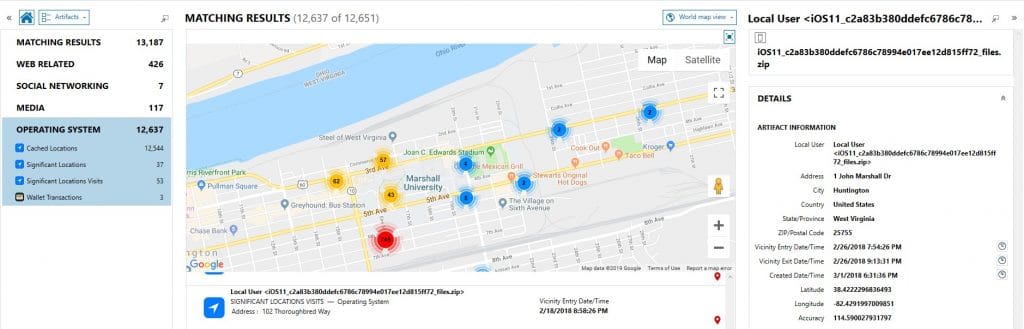
Keychain Data
The data stored within the keychain files generated by the GrayKey will store both exportable and non-exportable values. This means that there will be data within the GrayKey generated keychains that will not be available from keychain entries from encrypted iOS backups. These can include Wireless Access Points stored as “AirPort” entries with their SSIDs and passcodes, Backup passwords for encrypted backups, and tokens for multiple services the user has interacted with on this device. The Internet Passwords artifact will store information passed into the Keychain from using the Safari browser and can even pass information from one iOS device to another or to a MacOS device. This can allow users to recover usernames and passwords for cloud-based sources and with proper legal authority acquire them using a service such as AXIOM Cloud.
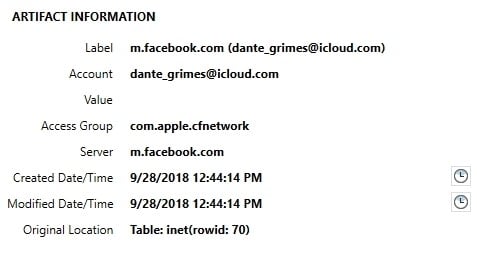
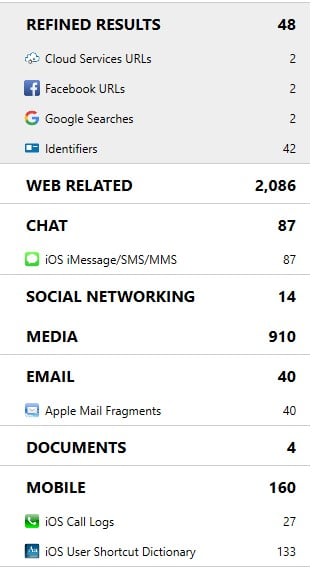
Process Memory Image Analysis
By processing the images of Process Memory generated by GrayKey, AXIOM will be able to carve information stored within the process memory of AFU (after first unlock) devices. This can include information that may have been deleted from the file system. These images are acquired from the GrayKey device and will be named “<udid>_mem.zip” and can be loaded into AXIOM Process the same way as any other image. Once loaded, AXIOM will automatically attempt to carve for records including web related, chat, email, media, and more. The below example shows some of the information that was carved from a process memory image including iMessage/SMS messages, mail fragments, call logs, and refined results such as Google Searches that were performed.
Wrap-Up
The team at Magnet Forensics has spent a lot of time recently diving deep into the images provided by the team at Grayshift. We have taken this research very seriously and have been working hard in order to provide new and exciting artifacts to the forensic community to make parsing through the massive amounts of data available easier. With this new partnership, Magnet Forensics and Grayshift are dedicated to helping our customers have the easiest and most powerful tools at their disposal when dealing with iOS devices.
Stay tuned for some additional exciting artifacts coming your way very soon!