
iOS 17 Forensics: Another Year, Another Byte of the Apple
With another year gone by, it’s time for another version of iOS to hit the market to coincide with the release of the iPhone 15 series and Apple’s first inclusion of the USB-C port to its iPhone line. While the USB-C port is old-hat for macOS devices and even several years old for iPadOS devices, bringing it to Apple’s mainstream mobile device will certainly bring some changes for forensic professionals. Let’s take a look at both the changes and features of iOS 17 as well as some forensic impacts going forward!
Acquiring iOS 17 Devices
On the surface there have been no detected changes with imaging iOS 17 with AXIOM. While I haven’t gotten my hands on an iPhone 15 series device yet, previous USB-C iPads running iOS 17 have also been put through the paces and work as expected with AXIOM.
Encrypting quick images is still the way to go, with several artifacts still locked behind the backup encryption function. So, what will you get by encrypting the backup versus not encrypting?
- Call Logs
- Safari History *
- Safari Last Session
- Safari Tab Data
- InteractionC
- Keychain
- Apple Health Data
- Private Wi-Fi Profiles
Safari History is a bit of an “it depends” scenario because as of the time of this writing, any of the Safari “Profile” history data is available within an unencrypted backup. Speaking of, let’s talk about the new feature changes to iOS 17.
iOS 17 New Features and Artifact Support
Before we dive into the new features the latest version of iOS brings us, let’s talk about the elephant in the room. What broke? Well, good news! Initial tests and reviews show that the standard artifacts parsed by AXIOM are already working with iOS 17 images. There have been very few changes to the basic artifacts such as iMessage/SMS/MMS, Call Logs, Contacts, Notes, and the like.
But little doesn’t mean none. For example, within the sms.db we have a new way to recover audio messages! Audio messages sent via iMessage are designed to self-detonate two minutes after being played which makes recovering them difficult. Enter the new audio message transcription that was added by Apple for these voice files.
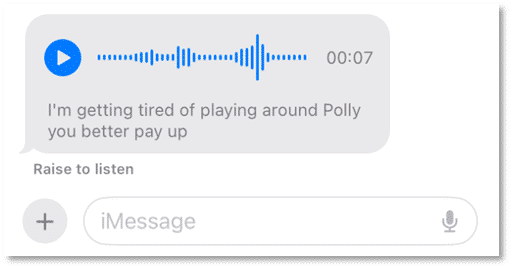
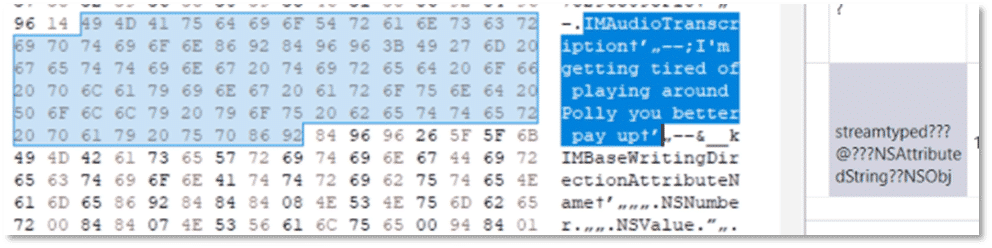
Unlike other transcriptions these are easily recovered by browsing through the attributedBody BLOB for the audio message record. When opening this in pure hex/text examiners can review the transcription of the message. With any transcription, it’s worth noting they’re not going to be perfect but gives you a general understanding of what it was about.
Safari is where thing start to get interesting. One of the features announced for Safari in the new OS was the inclusion of “Profiles” to segment the browsing history of its users on the device. This allows a user to separate their work from personal, or even to group their information under a specific profile for maybe their schoolwork or second job. It builds upon the features of Tab Groups released in a previous release of iOS.
What Apple hasn’t been entirely clear of, is how the data is segmented. This is where it gets a bit messy. The user’s actual browser history is segmented into each of the separate profiles. Anything that is done under the base or default profile is still stored in the same old location within the History.db file. Additional profiles have their own segmented History.db within a Profiles folder. These files are not in the standard Library/Safari path but instead in the application directory.
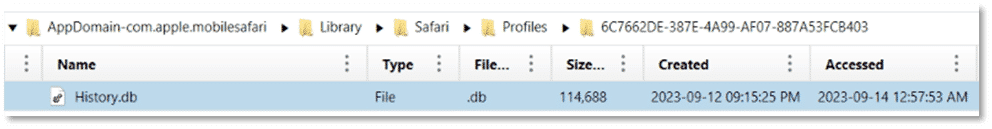
The good news for examiners is that AXIOM is already parsing and carving these additional History.db files to recover all of the profiled history.
As it stands at the time of this article’s writing, this is really the only data that is getting segmented. The rest of the Safari data including the Session, Tabs, and even Private Tabs are getting intermingled within the main Library/Safari directory. Private browsing data is still recoverable as long as the tabs are still open (or carvable) regardless of whether they’re using the biometric/passcode lock to hide Private Browsing.
Bookmarks are all stored within the same database, and users CAN choose to segment them, but it only extends to what folder they may choose. Users can still simply store them in any bookmark folder they wish.
One thing to consider is that the “Recent Search Terms” stored within the Safari plist files are only going to track the searches which occur under the base profile.
Another feature added to iOS 17 was a visual representation of voicemails that get streamed to the lock screen while they are being left. These are true for both regular calls as well as FaceTime times, marking the first time you can leave voicemails for FaceTime.
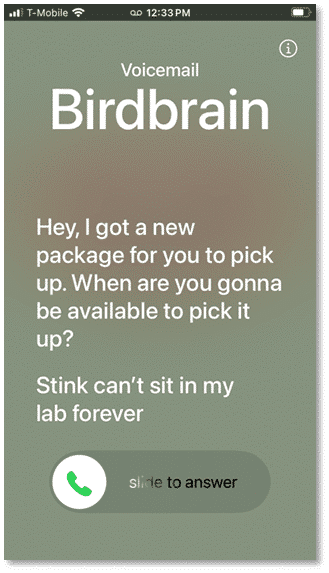
Currently, these textual recordings don’t seem to be available within the backup-style images, but we’ll keep diving in to find them as we unlock access to the file system. The voicemail greeting replaces the standard carrier one (or allows you to use your custom pre-set) and sounds like Siri’s voice.
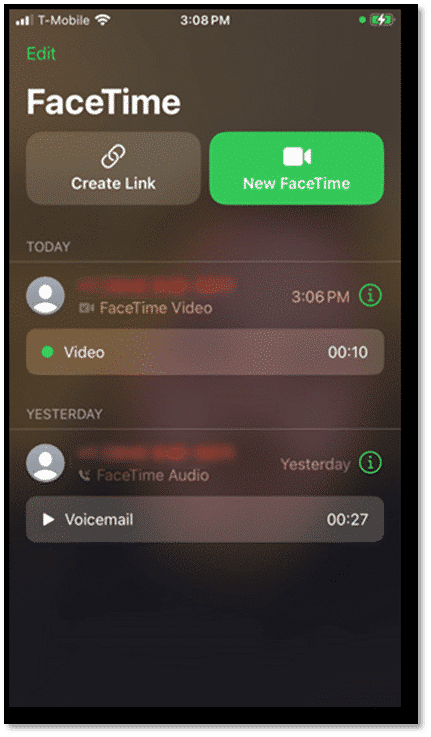
Speaking of FaceTime, iOS 17 has given users the ability to leave both audio and video recordings as voicemails. Audio voicemails will be visibly available within the same area as regular call voicemails, but FaceTime Video voicemails are going to be in a different area. Unfortunately, none of these files seemed available within the backup-style images.
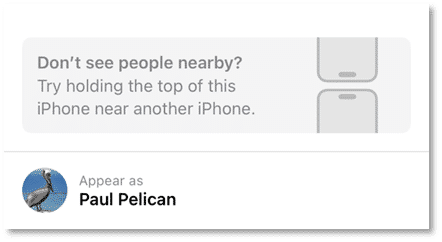
Apple has added the ability to share contacts quickly with another individual you’re in close proximity with using the new feature “NameDrop.” To use this, both devices need to be unlocked and the tops of the devices brought together. After a visual effect and a vibration, the contact poster you have created will appear on your phone and allow you to exchange it with the other device.

Now, while this may not be the most forensically relevant feature, this introduces what Apple seems to refer to as the “boop” service. No, I’m not kidding, yes, that’s really what they called it when reviewing internal information. This “boop” allows for the users to transfer more than just their contact information. It’s now possible to AirDrop files with individuals you’re not contacts with by bringing the tops of two phones together.
So, AirDrop will now work in multiple ways, the newer “boop” transfer which allows you to quickly send a file to someone without them being a contact (or being discoverable), or the standard proximity method which scans the area using the same previous technology of AirDrop. It also seems that Apple has removed the ability to let your AirDrop remain completely open indefinitely, reducing it now to allowing you to setting it to “Everyone for 10 minutes” which was previously only offered in other countries such as China. As a note, this change was rolled in 16.2, not 17 specifically, but the “boop” feature seems to be the fix to allowing you to trade files with someone you’re not a contact of without constantly changing the setting.
There are still some features that need to be tested as we continue to unlock access to file system extractions. Messages received an upgrade on location sharing opting for a live location share over just the older ‘Send Location’ that would just drop a vCard file containing an Apple Maps URL with a latitude/longitude. Additional safety features were added including a ‘Check In’ feature that can be used to share your location with trusted contacts at specific times when traveling somewhere.
On the location front, iOS 17 added the ability to share AirTags with individuals and as a lover and avid user of AirTags I can’t wait to dive into those features myself. Since Apple is so protective of their location data behind the largest of their protected walls, we’ll have to wait just a bit longer to start tearing apart all of those new details.
Apple didn’t give us ALL of the features they’re adding on day one. There are still several very relevant forensic features that are slated to arrive later this year according to the Apple website. These features will be continued to be examined as they release and include AirDrops that start within proximity and finish via iCloud, the Journal application and enhancements coming to the Files application. Be sure to keep a watch here on the Magnet Forensics website as well as we continue to share all of the latest, greatest information with the community!
Christopher Vance is a Senior Technical Forensics Specialist with Magnet Forensics specializing in mobile and macOS research. You can find more of his work being shared with the community on Magnet’s monthly web series “Mobile Unpacked with Chris Vance” as well as on his personal blog http://d204n6.com.