How to Acquire and Analyze Cloud Data with Magnet AXIOM Cloud
With Magnet AXIOM, users can acquire data from multiple cloud sources, such as Apple, Google, Facebook, Microsoft, Dropbox, Twitter, WhatsApp and more. AXIOM supports multiple acquisition and account sign-in methods, including username and password, external browser authentication, and account tokens from mobile extractions.
Within each of these sources there may be several services, apps, or data types for each of them. For example, for Microsoft, AXIOM can acquire data from OneDrive, Microsoft Mail, and Office365 mail. For Google, AXIOM can acquire data from a user’s Google Account, Google Drive, and Google Apps, such as Google Photos, Google Calendar, Gmail, and Google Hangouts.
The cloud capabilities of AXIOM are integrated alongside Computer, Mobile, and Vehicle as another evidence source and you can process computer, mobile, vehicle , and cloud data all in one case so that your analysis will span across all sources of evidence for a given case, not in a separate tool or product.
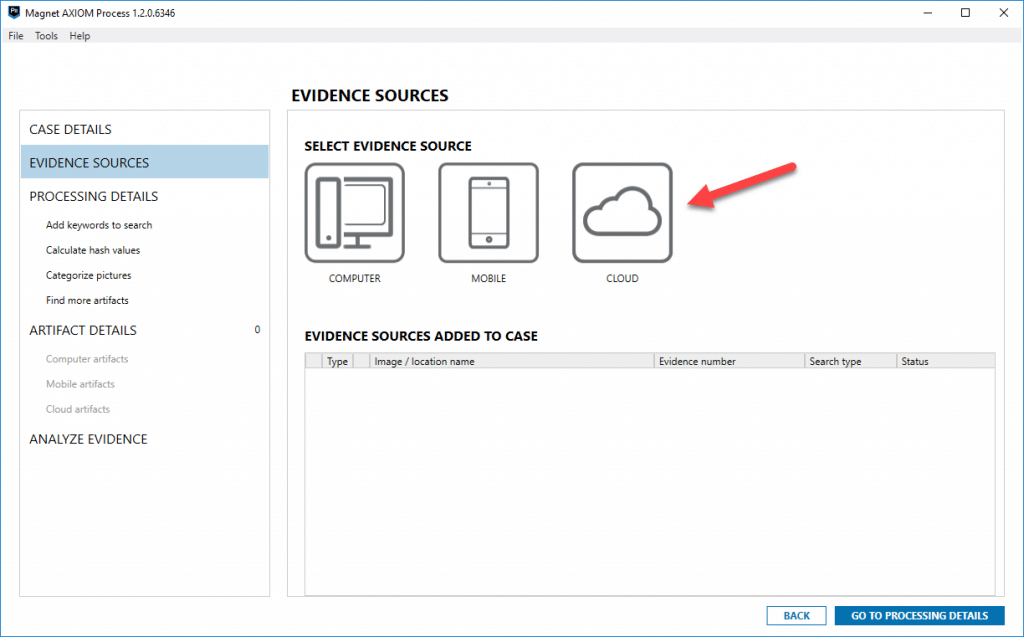
To acquire cloud data, simply click cloud as an evidence source, select acquire evidence, then you will be presented with a message confirming that you have proper search authorization to access and acquire the cloud data in question. This prompt and acknowledgment is here to notify you that you’re going out to acquire data from another source other than what’s found on the phone or computer. Once the box is accepted, you’ll be presented with all of the platforms supported and available.

You can select any of the sources that you would like to acquire cloud data from, so long as you have proper legal authority. From here, if Google cloud acquisition is used as an example, once you select Google, AXIOM will prompt you to select the appropriate sign-in process.
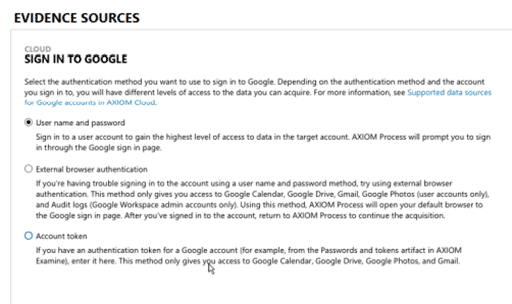
Once you have signed into the specific users account, each cloud source will provide different data source options, so for Google, that would be the Google Account, Google Drive, and Google Apps.

Some platforms will allow you to see the last activity on that account or an estimate on the amount of data that will be acquired for each. This isn’t available for all services, but it will be displayed when available in AXIOM.
From here, you can choose to acquire all the cloud data available from that account or limit it based on date/time. For example, you could choose to only acquire the last month’s worth of messages or data from a given account if that is a limitation of your authorization or you may want to limit the amount of data being acquired to streamline the focus of your investigation.
Next, the selected data is added to your case ready for processing. At this point you can continue to add additional evidence items such as a computer or phone or continue with the other processing options. In the screenshot below, I’ve added an additional computer E01 image and physical image of a Samsung Galaxy S3.
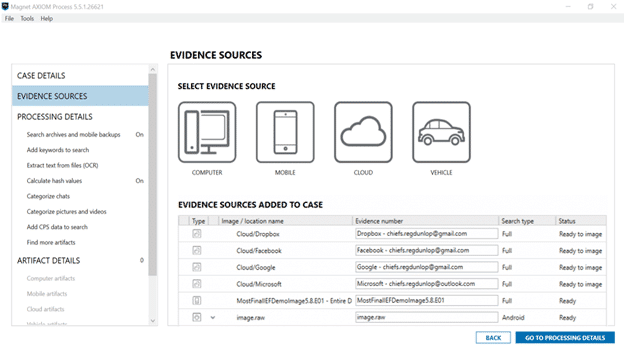
You can also continue to add additional processing options such as keywords, hashsets, etc., just like you would in any other case in AXIOM. Once your additional processing options and artifacts are selected, you’re ready to acquire and process the cloud data.
Depending on your network speed and the amount of cloud data being acquired, your acquisition times may vary. You can expect it to take quite a bit longer if, for example, the user has a lot of storage in their Dropbox, OneDrive, or Google Drive as these can be several hundred gigabytes in size.
Once the processing is complete, you’re presented with the results in AXIOM with the new cloud data found at the bottom under “Cloud”:
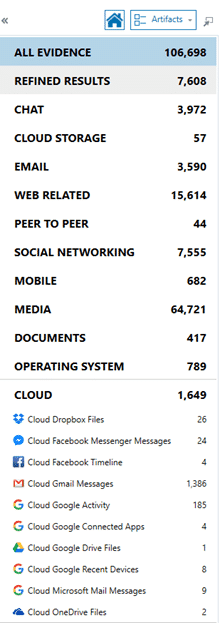
You may also see a category for “Cloud Storage.” The difference between these two categories is that Cloud Storage describes cloud artifacts that were found on the device whereas those artifacts accounted for in the “Cloud” category specifically describe those artifacts acquired from the cloud. For example, if you found Dropbox data on a user’s computer referencing files and accounts tied to Dropbox, they would fall under “Cloud Storage,” but if I authenticated and acquired data from a user’s Dropbox account online, they would be found under the “Cloud” category.
In the example below, there is a good amount of data across each of the accounts and now this data is integrated right into AXIOM along with the computer and phone evidence that was recovered as well. Here’s a quick look at what Gmail email looks like in AXIOM when pulled from the cloud:
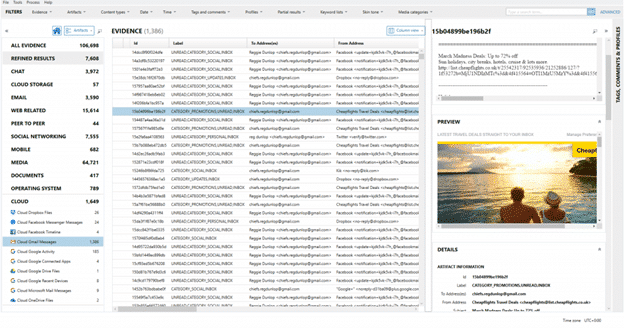
You can see the columns in the middle will list all the relevant details such as To/From/CC/BCC, Subject, Message, timestamps, email headers, etc., and along the right you will get those details listed along the bottom as well as two previews for the message: one is text only, automatically indexed, and searchable, whereas the other will render the email in its native format as the user might see it.
From here you can continue your examination just like any other making use of the sorting, filtering on any of the columns available to help narrow down the number of emails to be searched. If any of the artifacts contain timestamps or geolocation data (which many of them do), the data can be viewed in AXIOM’s Timeline or World Map views as well. Watch the video below for a guided walk through with Kim Bradley, highlighting how to acquire data from Google cloud accounts, which is just one of the examples of the cloud capabilities of Magnet AXIOM.