
Expanded Office 365 Unified Audit Log Capabilities with Magnet AXIOM Cyber
Users can ingest Office 365 unified audit logs that are manually exported from Microsoft’s Security & Compliance Center into their casefiles for analysis in Magnet AXIOM Cyber. In earlier releases of AXIOM Cyber, examiners could collect directly from O365 environments via live acquisition, however we understand data is sometimes provided to investigators, versus them having the ability to acquire directly. Unified audit logs are invaluable when it comes to tracing user actions within the Microsoft O365 environment. Employee actions ranging from logins, files being copied, deleted, edited, or shared are easily identified with the use of these logs. In this blog we’ll walk through exporting the audit logs out of the Security & Compliance Center, and review what the data looks like once parsed by AXIOM.
If you haven’t had the opportunity to try AXIOM Cyber yet, make sure to request a free trial here, and for those who already have Cyber, make sure to head over to the Magnet Customer Portal to update today!
Loading O365 Audit Logs
To start, let’s head over to protection.office.com, where you’ll need to login to access the Office 365 Security & Compliance center. If you login and don’t have sufficient permissions, you’ll be prompted that you need to elevate your permissions before moving forward with a similar message as to what’s below.
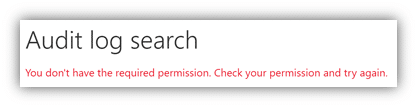
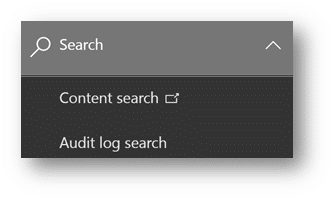
However, if you have the correct permissions on your account, you’ll navigate down the left-hand menu bar to “Search” and select “Audit Log Search” as we can see here. You can also utilize protection.office.com/unifiedauditlog if you prefer not having to navigate using the menu bar.
Now we simply need to configure our search to filter through our organization’s users. For this investigation, we are interested in what the one associate, Dante Grimes has been doing within his O365 environment over the last week. It’s important to remember what the scope of your investigation entails. Did the stakeholder only request information around when a user logged into Microsoft Teams, or perhaps did they want to know any file a user has accessed within a given time frame? We can filter on this data before we run our search within the Audit Log Search. The Activities dropdown includes a vast array of different activities users can perform while operating in an O365, however for investigations where you need as much information as possible on what a specific user is doing, leave the default option “Show results for all activities” selected.
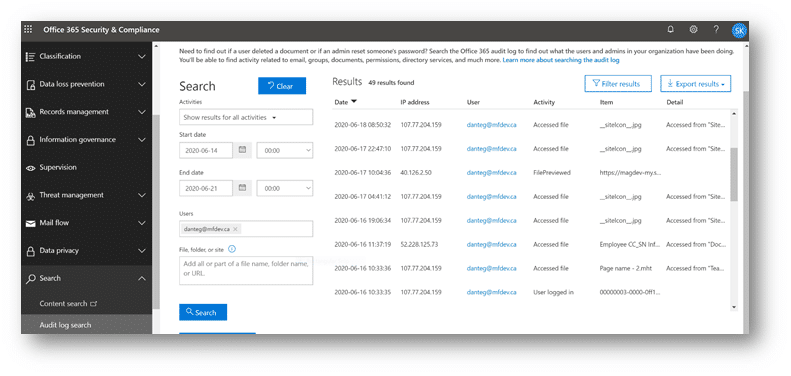
Once you’ve successfully queried your data, simply select the “Export results” box in the top right corner of your search window and select “Download all results”. This will generate an auditlog_[date].csv file of your data.
Now that we have our unified audit log CSV, we’ll launch AXIOM Cyber Process, and load our evidence in for processing and analysis.
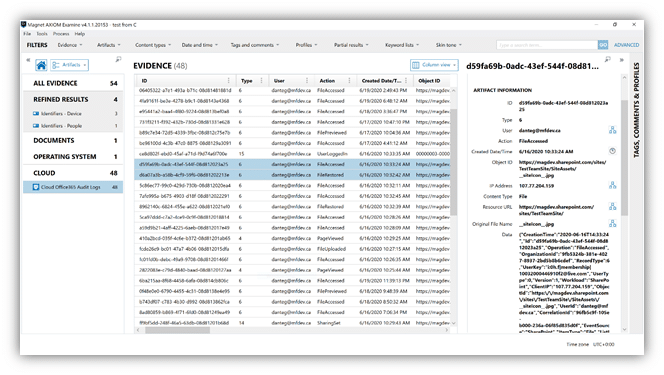
Once complete, examiners can make quick work of reviewing the audit logs processed with AXIOM Cyber. As you can see below, we can sort the logs based on action to narrow our focus. We can also utilize AXIOM’s relative time filter to get a better understanding over all the changes that occurred to our evidence within a given time frame as well. Under the Details Panel, we see information such as the IP Address of the user, Object ID for the file in question, Original File Name, and the raw data from the Log for reference as well.
If you have any questions or have ideas on new artifacts you’d like to see supported with AXIOM Cyber, don’t hesitate to reach out at trey.amick@magnetforensics.com.