A Deeper Look at Magnet AXIOM’s Improved Hashing
One of the most obvious benefits of Magnet AXIOM is the access to the entire file system, as well as the hundreds of artifact types that the Magnet parsing and carving engine finds. To accommodate the larger data set and expanded access, we’ve improved the hashing functionality as well.
If you are more familiar with IEF, then you know there are a few options to hash pictures or whitelist non-relevant files. However, since IEF only reports on the artifacts it finds, some features like hashing were limited to artifacts and any file that was not an artifact wouldn’t be included.
To get started using AXIOM’s advanced hashing functionality, the first thing you’ll want to do is to load your hash lists into AXIOM and, depending on the type of hash list you’re loading, you’ll have a few options available.
Adding hash lists is easy, the examples below show how to load these lists prior to processing your evidence. Upon loading each set, AXIOM will build a database from your hash list, which can take a bit of time. AXIOM should go through your hash set at about a pace of 5000-10000 hashes per second depending on your system — which is much improved over the speeds in IEF. Once the database is built, those hash sets will be persistent across cases and will be available to include or exclude in every subsequent case thereafter.
Let’s take a look at the different hashing options in Magnet AXIOM:
Setting Up Your Hash Lists in AXIOM Process
Calculate Hash Values
In AXIOM Process, under Processing Options, you will find two pages that specifically apply to hashing: “Calculate hash values” and “Categorize pictures.” The first one starts with some basic hashing options, giving you the ability to hash every file on the system and provide either an MD5, SHA1, or both values. These hashes will be available as a column in the File System Explorer for AXIOM Examine.
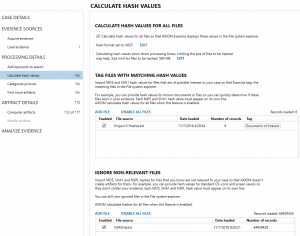
The next option under “Calculate hash values” is to tag files with matching hash values. Here examiners can load a list of hashes of known files they wish to identify in the file system. This works well if you have a list of files you wish to match and look for, such as known malware or intellectual property. To load the list, simply use a line separated text file of MD5 or SHA1 hashes, select “Add File”, and then choose a tag name to label any matches. Any files in the file system that match the hash from the list added will automatically be tagged as the name the list was given.
The last option under “Calculate hash values” works as a whitelist of known, non-relevant files. Often Windows and other applications come pre-installed on a fresh, clean system that have files that were never touched by the user. These files are usually system files, icons, dlls, etc. that have no bearing on your investigation but add to the data that must be examined — and that can be time consuming. By identifying known, non-relevant files, we can exclude these files from your case so they don’t need to be reviewed by the examiner.
Examiners can build their own whitelists (this is common in enterprise settings where all employee computers run from a standard image deployed by IT) or use pre-built lists such as the NSRL list by NIST. The NSRL hash list is a massive file of known non-relevant hashes maintained by NIST and available free from their website (http://www.nsrl.nist.gov/). There are three sets available (full, reduced, and minimal.) I usually recommend AXIOM users download and use either the reduced or minimal set as the full set contains duplicates and is unnecessary when used with AXIOM.
Categorize Pictures
The next page details hash sets used to categorize pictures in Magnet AXIOM. These features are often used by law enforcement agencies to identify known illicit images. There are two methods to load hash sets here depending on the type of data set being used.
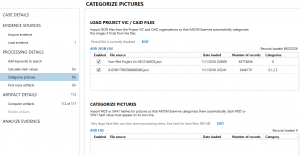
The first set is used if examiners are utilizing either the Project VIC or CAID hash sets. This data is stored in .JSON files and contains not only hashes but additional metadata about the associated file — including category, original path, timestamps, etc. We do not provide these hash sets but they are available for law enforcement agencies through your local ICAC group.
The other method to categorize pictures is to load in your own custom hash set if you’re not using Project VIC/CAID. Line-separated text files of MD5 or SHA1 hashes can be loaded here and the examiner can choose a category that these hashes represent.
PhotoDNA
In addition to the ability to hash MD5 or SHA1 hashes, AXIOM can also calculate PhotoDNA hashes. This feature is off by default and only available to law enforcement examiners so it must be unlocked prior to using it.
To enable PhotoDNA, follow the link in the software to our website and fill out the form using your agency email address (this is required to verify that you are LE.) You will be provided an unlock code to enable the feature. Once unlocked, PhotoDNA hashes will be created for all pictures being processed and will make use of the PhotoDNA hash values in your Project VIC/CAID hash sets as well.
For more information on PhotoDNA, visit: https://news.microsoft.com/features/microsofts-photodna-protecting-children-and-businesses-in-the-cloud/
Hopefully this helps explain how to use the various hashing options in Magnet AXIOM since hashing is an excellent way to help reduce the amount of data that needs to be examined by either identifying known files of interest or whitelisting/ignoring non-relevant files.
If you have any follow up questions or comments, feel free to reach out.