Connections in Magnet AXIOM Q&A Part 2
This is the second part in a two-part series. You can read Part 1 here.
In our short series on AXIOM Connections, we’ve given an overview of what Connections is (a fast, easy way to visualize how different artifacts are related to one another across devices) and how it works (automatically, with minimal time and effort on your part).
We’re also answering the most popular questions about Connections. In our last blog, we covered AXIOM Connections basics, including how connections are established, how to run Connections on newly added evidence, and reporting, among other aspects. In this blog, we talk about processing time and storage, as well as more in-depth questions about working with the connected artifact fragments.
Connections Processing Time and Storage
What is the typical processing time for AXIOM to parse all the artifacts of a standard size hard drive?
Because AXIOM processes both artifacts and the file system, processing time is based on the number of artifacts (and in turn, what’s parsed from them) rather than hard drive size. Artifacts can number into the hundreds of thousands, so it may take up to 8 hours to build. However, not only can you work a case while it’s processing; you can also, as many examiners do, leave a case to process overnight.
Will Connections process user folders and other likely evidence locations first for speed?
You can choose whether to run Connections automatically after processing is complete or manually when you choose. This processing is done in the background. Connections are mapped all at one time and are not available until all connections are complete.
To improve speed as new artifacts are added, Connections continues to undergo optimization.
For a typical image, what is the estimated size of additional storage of AXIOM-generated files?
Again, because AXIOM processes artifacts in addition to file systems, database storage size depends on the density of data—the types and quantity of artifacts on the acquired images.
Can AXIOM run on a server to handle large cases?
While it can be run on a larger system, AXIOM is designed to be optimized on a system with 16 logical cores and 32GB RAM. Adding additional cores does not improve performance in a linear way. For example, increasing the number of cores from 4 to 8 will yield huge improvements, while increasing from 16-32 cores yields almost no improvements. AXIOM can handle multiple pieces of evidence, but neither AXIOM nor the Connections feature are designed for large-scale, cross-collection analysis.
Is there any restriction on the number of cases that can be ingested into the software?
Most cases involve multiple pieces of digital evidence within cases. Typically, Connections can handle artifacts from one computer and multiple USB drives, phones etc. Because it isn’t designed for cross-collection analysis, however, we don’t advise correlating (for example) four 2TB drives.
This is an intentional design for our customers who frequently bring laptops into the field and need to be able to correlate artifacts during search warrant service or during an ongoing situation.
Working with Artifacts within Connections
Can Connections correlate artifacts with information from file or memory slack space, or unstructured data sets such as raw memory dump, hiberfil, pagefile?
Yes. Connections are rule-based relationships for both parsed and carved data. However, sometimes files in slack space don’t have the same attributes as those that still exist in the file system. Therefore, it may not be possible to get correlations on metadata that was lost when you carved a file from slack space. Still, even without a file path, you can tie together fragments such as hash values, URLs, or filenames available from memory, hiberfil, pagefile, unallocated space, etc.
Does Connections define whether data downloaded from a website was requested, or pushed by the site?
It can, but this depends on the artifact fragment and whether a rules-based correlation can be built from it. If the browser offers the metadata that differentiates between a download requested and data pushed by the site—and if the appropriate fragment is recovered—then yes, Connections can differentiate downloads.
If a file is downloaded directly onto some external device, or the file destination is changed after downloading, and there is no cloud service active on the system, how would that affect the information?
It depends. Files can be downloaded from any number of sources, so again, the data you get from an instance like this depends on the metadata—and therefore the artifact—available from the download source.
For example, Chrome offers a file download path and the “saved to” path, as well as download completion time and start/end time. To correlate a file saved under a different name, you would connect from the file’s download path to its hash, then pivot from source to hash to new file name and finally, the path in which that filename has existed.
Are there ways to filter data to see potential data exfiltration?
It depends on the artifacts recovered from the evidence. Connections provides relations between attributes such as File Path, Source, URL, etc. You’ll be able to see all the connecting artifacts with a common attribute. You can also start with a file system artifact and backtrack it to see where else on the system it was accessed, to and from whom, etc.
Filters such as the Timeline view enable you to see when a particular user viewed the file as well as when it was moved off a system. Whether data was emailed, uploaded to a cloud service such as Dropbox, transferred to a USB drive, etc., you can see this activity provided that artifacts related to the activity were recovered.
You can even see whether a file exists under a different name in another location, such as a USB drive, through using file hashes. Even if you don’t have the media where a file path was connected, artifacts such as LNK files from the system may still provide additional information.
Can you pivot from an external E drive to USB registry key? From active files to VSS?
Yes, though it depends on what pieces of evidence you have. This correlation is straightforward if you have both the USB and the computer; using the file path, you can pivot from a LNK file on the E drive to the registry key based on the volume serial number.
However, if you couldn’t seize the USB, while there may be circumstantial evidence of the connection, you couldn’t correlate from the specific file based on a file path. You may have the LNK file as well as evidence of a drive mounted to the USB with the same serial number. In this instance, timeline analysis will be valuable.
You could also correlate the file name to the volume shadow copy, provided you have volume shadow copy as evidence, because the file name still exists there.
Can you view connections for a user to see with whom the individual is collaborating?
Connections wasn’t built for traditional link analysis. However, traditional communication, such as calls, emails, and messaging are viewable in Connections. By correlating artifacts such as shared files, peer-to-peer sharing, etc., you can see user connections, especially if processing images from two or more users’ devices.
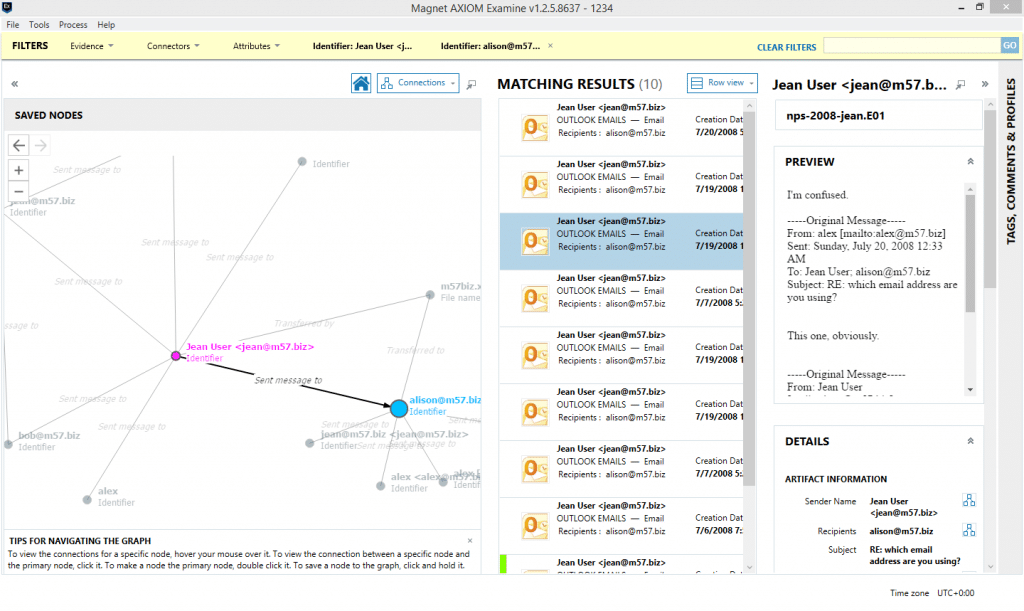
You can see all communications between two people by selecting a primary and secondary node. Figure 1 demonstrates how Matching Results shows all emails sent from jean@m57.biz (primary node) to allison@m57.biz (secondary node).
Does Connections correlate call detail / cellular tower with geolocation data?
AXIOM currently doesn’t ingest external call detail records, so it isn’t possible to bring this data into Connections.
Does Connections have a global date filter?
No. We intentionally do not limit connections based on time, as correlations would be missed. However, if you tag artifacts in Connections view, then return to artifacts view, you can apply a time filter there or view in a timeline view.
If you’ve conducted image and video review in another program like Griffeye Analyze DI and exported a JSON of a small selection of notable image/video files, can you then do Connection analysis on only those files?
When you import JSON files back in from Griffeye, AXIOM builds connections on everything you have. As the examiner you could filter down to the files with a particular category or to a particular evidence and then look at the connections related to that evidence. However, Connections will still correlate those to the other evidence in your case.
Can Connections link thumbnails to original photos using PhotoDNA?
Currently, hash matches have to be exact. Percent matches haven’t yet been added.