What is Infostealer Malware?
What are Infostealer Malware?
Infostealers are a type of malware specifically designed to locate and exfiltrate credentials. Their prevalence and impact were limited pre-COVID-19 as most of the headlines were grabbed by ransomware operations that crippled large organizations. Remote and hybrid working models helped to maintain productivity which put pressure on IT departments to facilitate this by accelerating digital transformation strategies. At the same time, there was a significant uptick in the number of known Malware-as-a-Service (MaaS) operations as well as growth in the number of malware variants seen in the wild.
Now, a complete ecosystem has developed to facilitate the monetization of various aspects of their operations, like how organizations outsource certain tasks so they can focus on their specialty. This has lowered the bar for crime groups to enter the market.
In this blog post, we’ll introduce the top five (as of March 2023) infostealer families, including their capabilities and context to the broader infostealer threat.
The Origins of Infostealers
The origins of infostealers trace back to ransomware which took off in the early 2010s with examples including Reveton and the more well-known CryptoLocker.
Infostealers are not new. Many existing banking trojans and ransomware had similar functionality that you might find in infostealers. One of the major differences is that the business model has evolved from malicious groups requiring expertise in developing malware to being able to acquire it as a service. This has also presented existing developers with another potential revenue stream.
During the first half of 2022, Group-IB identified many Russian-speaking groups distributing infostealer malware that had collectively infected over 890,000 user devices and stolen over 50 million passwords, an increase of 80% over the previous period. Not to mention the over 2 billion cookie files, 100,000+ crypto wallets and 100,000+ credit cards. The FBI estimates that over 50 million unique credentials (email addresses, bank accounts etc.) were stolen using Raccoon Stealer, which targeted millions of potential victims around the world. Groups or individuals who utilize infostealers will typically sell their stash of credentials they have obtained, also known as ‘logs,’ either to automated underground marketplaces or on public forums on the dark web. There is even recent evidence of marketplaces moving to Telegram.
These groups/individuals are known as Initial Access Brokers (IABs), and they sell access to the most high-profile networks to the highest bidder. Many high-profile attacks in recent years have been caused by credential material obtained on these marketplaces. Accounts were compromised at Electronic Arts in June 2021, Uber in Sept 2022, Cisco in August 2022, and Microsoft in March 2022 with stolen credentials.
The largest log markets are Russian-speaking, and growth in these has been significant over the last few years. TwoEasy (2easy) is one of these markets that started in 2019. In July 2020, it offered logs harvested from approximately 28,000 machines, and by 2021 this had grown to 600,000 machines. In Figure 1, we can see the total number of logs across 3 of the biggest Russian-speaking market trending upwards.
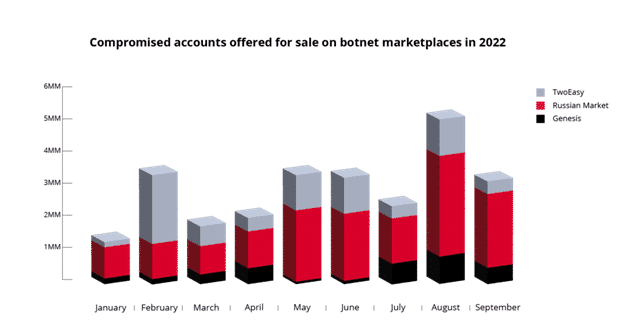
This research from KELA also displayed the relative splits in the type of infostealer malware used to steal the credential material between January and July 2022 on the Russian Market, TwoEast and Genesis.
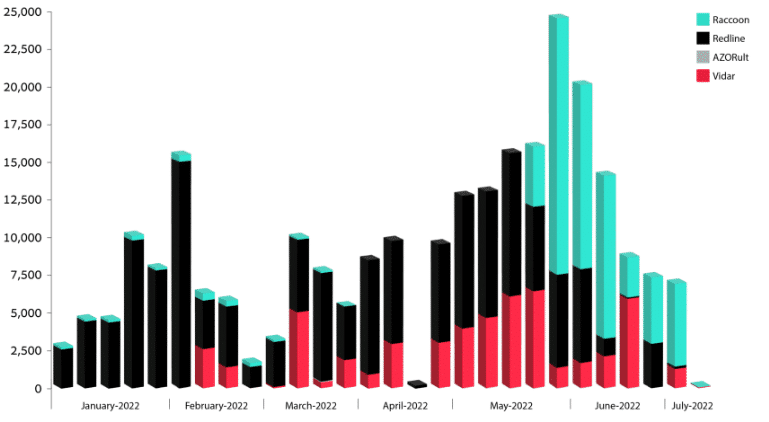
On the detection side, Elastic’s Global Threat Report showed a significant increase in the proportion of infostealer malware detected on its Windows endpoints. Both AgentTesla and Redline show significant increases in detections.
Top 5 Families of Infostealers
The top 5 families of Infostealers detected most frequently across a wide range of security vendors are:
- Raccoon (v1 and v2)
- RedLine
- AgentTesla
- Vidar
- AZOrult
Their main capabilities and a brief overview of each are highlighted in the next section, however more detail can be found in the references. While most infostealers have a wide range of capabilities to utilise for credential theft, most of them can also be used as Remote Access Trojans (RAT) and provide follow-on deployment opportunities for other malware. Conversely, other types of malware like banking trojans can also go on to deploy infostealers on to the machine.
Raccoon
Raccoon v1 was released early 2019 with support stopping March 2022, with the group stating it was due to the invasion of Ukraine by Russia. In June 2022 v2 was released by the developers that steals the following:
- Information stored in browsers (passwords / cookies / autofill information and credit cards)
- System information
- Telegram Desktop application
- Take a screenshot
- Drop and execute a file
- Steal desktop crypto wallets
- Screenshots
- File grabber
RedLine
First spotted in March 2020 and still under active development, the latest detailed analysis of a RedLine sample established that it steals the following:
- Information stored in browsers (passwords / cookies / autofill information and credit cards)
- System information
- Telegram Desktop application
- Take a screenshot
- Drop and execute a file
- Steal desktop crypto wallets
- Screenshots
- File grabber
AgentTesla
Commonly referred to as a Remote Access Trojan (RAT), AgentTesla has been around since 2014 and has a lot of functionality that is commonly associated with infostealers:
- System information
- Information stored in browsers (passwords / cookies / autofill information and credit cards)
- Keylogging
- Steals clipboard data
- Screenshots
- VPN Credentials
- FTP Credentials
- Email client credentials
Vidar
Vidar is an evolved version of the Arkei infostealer and has been around since around 2018. Initially it used gaming platforms for distribution of C2 IP addresses and configurations but has since moved to social media platforms. It steals the following:
- Information stored in browsers (passwords / cookies / autofill information and credit cards)
- Tor Browser Information
- Email clients
- Crypto wallets
- FTP clients
- 2FA software
- Messenger Apps (Telegram/Thunderbird/Pidgin/Bat!)
- Crypto Wallets
- File grabber
- Screenshots
- Installed software
- Download and execute payload
One interesting difference between Vidar and existing infostealers, is that Vidar erases itself once it has collected the required information. Others typically hang around awaiting commands from the operator.
AZOrult
Operating since 2016 AZOrult is another common commodity infostealer, development stopped in 2018 and it was released as a free product. Infostealers exist that utilise portions of AZOrult currently and it steals:
- Information stored in browsers (passwords / cookies / autofill information and credit cards)
- Email client information
- Crypto wallets
- FTP clients
- Steam
- Desktop messaging clients (Telegram and Skype)
- Download and execute payload
The lists of functionalities for all infostealers here should be treated as snapshots of the infostealers capabilities as developers may add/remove functionalities and only certain samples will be analysed.
Delivery Methods
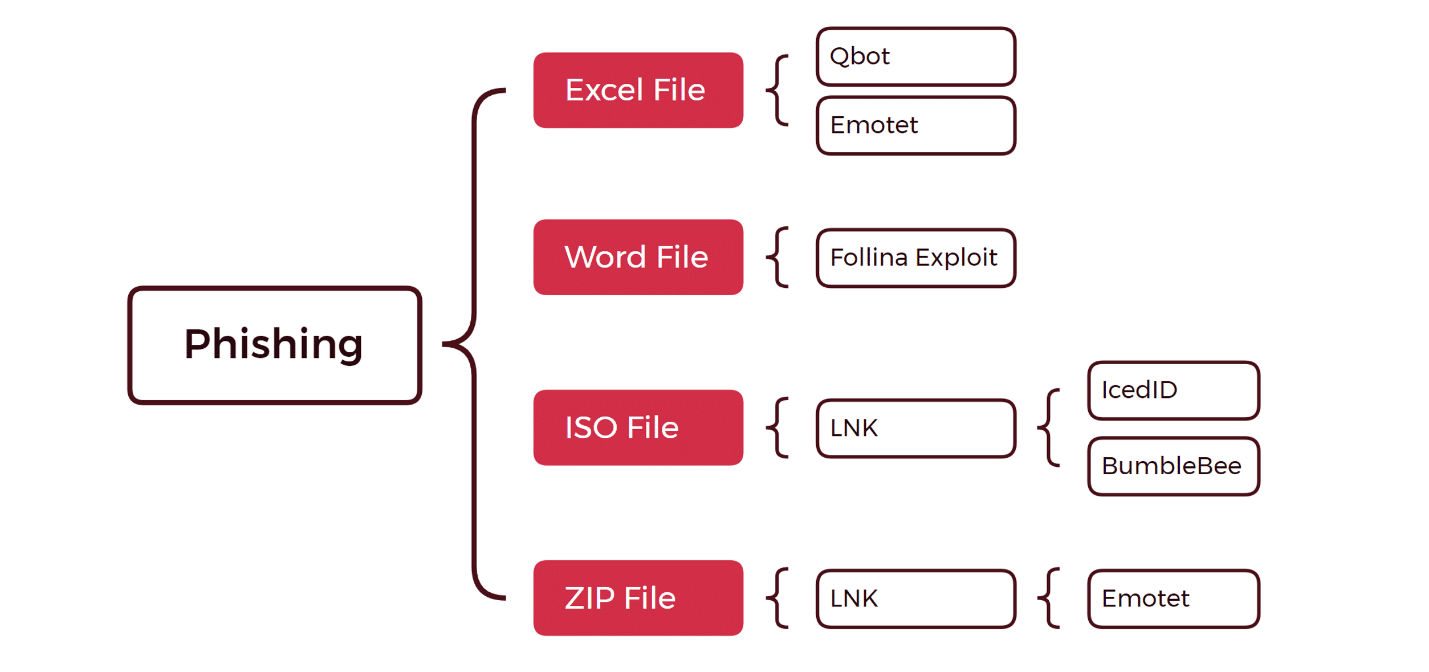
There are two main delivery methods used for infostealer malware that can be broadly grouped in to phishing and non-phishing methods. Both are then further divided in sub-methods – note that the phishing diagram only represents email attachments as a tactic and does not include phishing emails that link to a malicious site (Figure 4 and Figure 5).
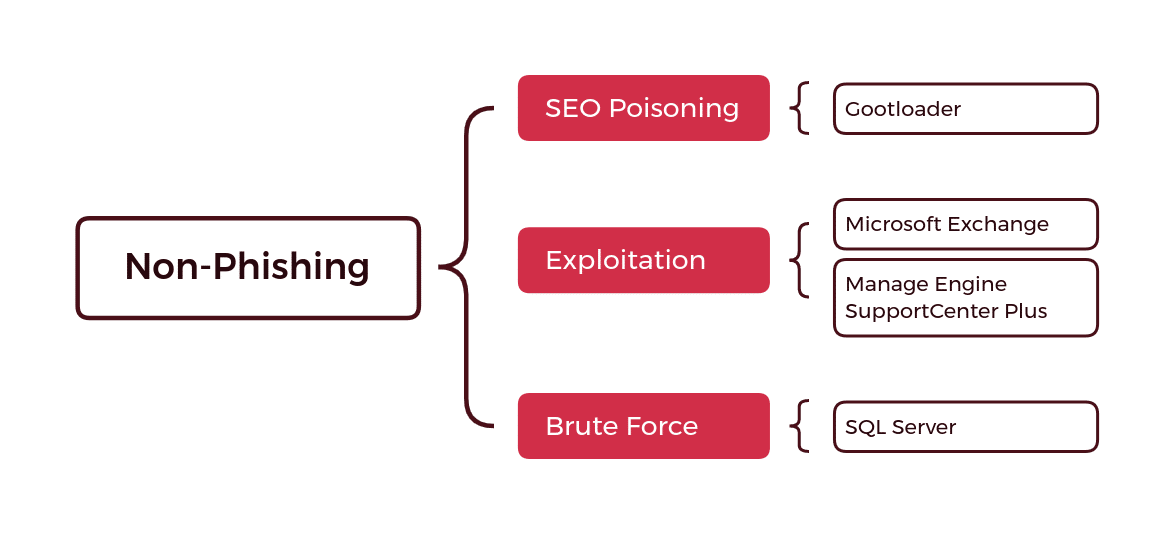
Malvertising as a New Non-Phishing Delivery Method
More recently, the non-phishing approach has utilised malvertising and compromised accounts on social media platforms to push content that contains links to malicious websites. Reputable social media accounts (e.g., Facebook or YouTube) post material that leads users to a malicious website with a legitimate looking domain, mimicking a legitimate one. The malware is then downloaded from the site and executed by the user unwittingly. These methods are typically not circulated in online user security literature. It uses the reputation of the compromised account to increase the likelihood that the user visits the malicious site.
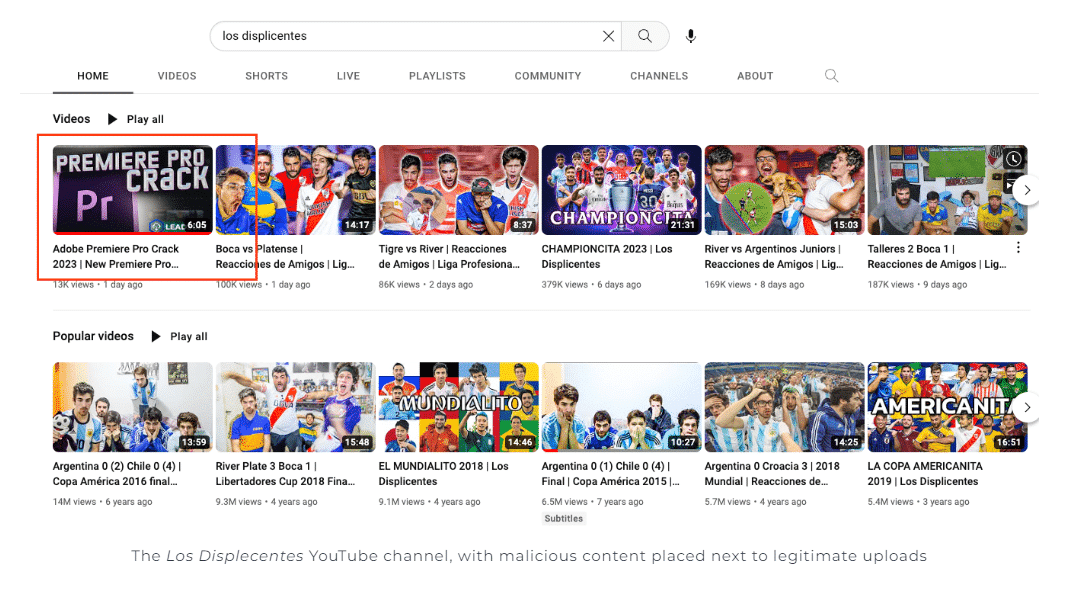
Advertising networks are complex and deal with large quantities of data making validation of submitted ads difficult. Malicious actors submit legitimate looking ads that are then displayed on reputable websites. Users click on them believing that because they are shown on a reputable site they must be trustworthy too. Once clicked, they then lead to a website masquerading as legitimate software when in fact it is malware.
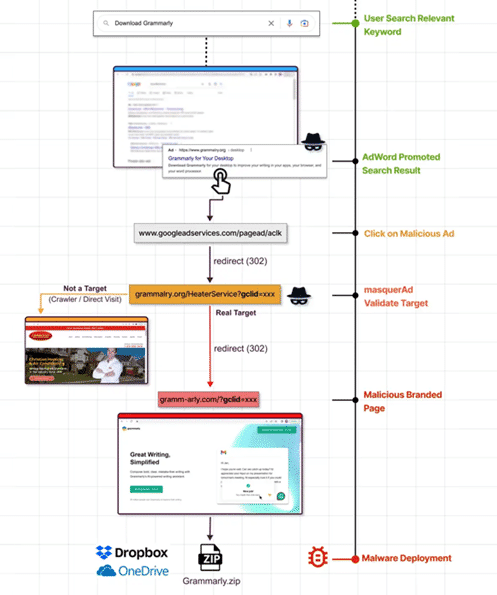
Another form of malvertising abuses paid-for search results by inserting links to malicious sites at the top of the search engine results as paid ads. An example flow of actions is in the next diagram (Figure 7).
Both tactics phish users interested in legitimate software that focuses on business-critical functions, common examples include Slack and Adobe Photoshop.
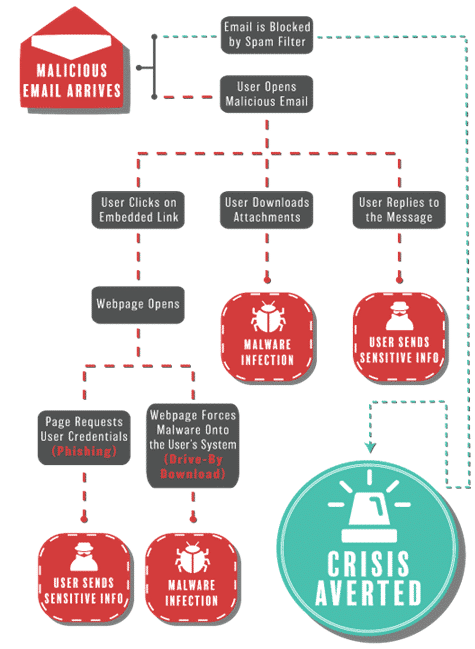
Phishing email campaigns have also diversified their delivery methods by not only using malicious attachments but also creating emails that contain links to these legitimate-looking software sites, resulting in credential loss or installation of malware. An overview of the various attack flows using phishing emails is shown below.
Conclusion
Infostealers have proven to be an effective method to compromise both corporate and non-corporate machines lowering the bar to entry for criminal individuals or groups. The diversification in the delivery methods has also led to an increase in compromised credential material. Detections of infostealer malware and the increase in the amount of material for sale on underground forums has increased over the last few years and shows no sign of slowing down. While ransomware is still a significant concern to businesses, infostealers are providing more opportunities for less technically savvy criminals to impact individual users and large corporations. As more businesses lean-in to hybrid working and find new ways of conducting business electronically, infostealers will present a significant and increasing risk going forward.
Investigating a Malware Attack with Magnet AXIOM Cyber
It’s not a question of if a cyber attack will happen, but when.
Magnet AXIOM Cyber is a robust digital forensics and incident response solution for businesses that need to perform remote acquisitions and collect & analyze evidence from computers, the cloud, and mobile devices.
To learn more about the incident response capabilities of AXIOM Cyber visit our Incident Response hub to review blogs, how-to videos, and webinars on each of the features outlined above. Or check out our webinar: A Walk-Through of Investigating a Malware Attack: An Introduction to AXIOM Cyber.
This is a post authored by Ivan King (Security Research Engineer) with contributions by Matt Suiche (Director, Memory, IR & R&D).