83% of companies have a BYOD policy
Accessing business-critical communications and data on mobile devices is crucial to protecting your organization and employees. However, the complexity and ever-growing diversity of mobile devices can present challenges for digital forensic investigators when investigating IP theft, insider threats, fraud, and other internal investigations.
Missing data
If your organization has a BYOD or corporate-owned device policy and you’re unable to recover mobile data or only limited data, you’re potentially missing critical evidence.
Disconnected tools waste time
Manually moving mobile data from an acquisition tool, such as Cellebrite UFED4PC, to Axiom Cyber for processing and analysis wastes valuable time and can result in inconsistencies in the data.

More vendors = more admin
Purchasing tools from multiple vendors means you’re managing more communications, invoices, security audits, and contracts when you could be resolving cases.

MDMs not fit for forensics
MDM platforms collect minimal data from mobile devices. Analyzing data from MDM is challenging as you can’t view it alongside other sources, like computer and cloud data.
Magnet Verakey and Magnet Axiom Cyber
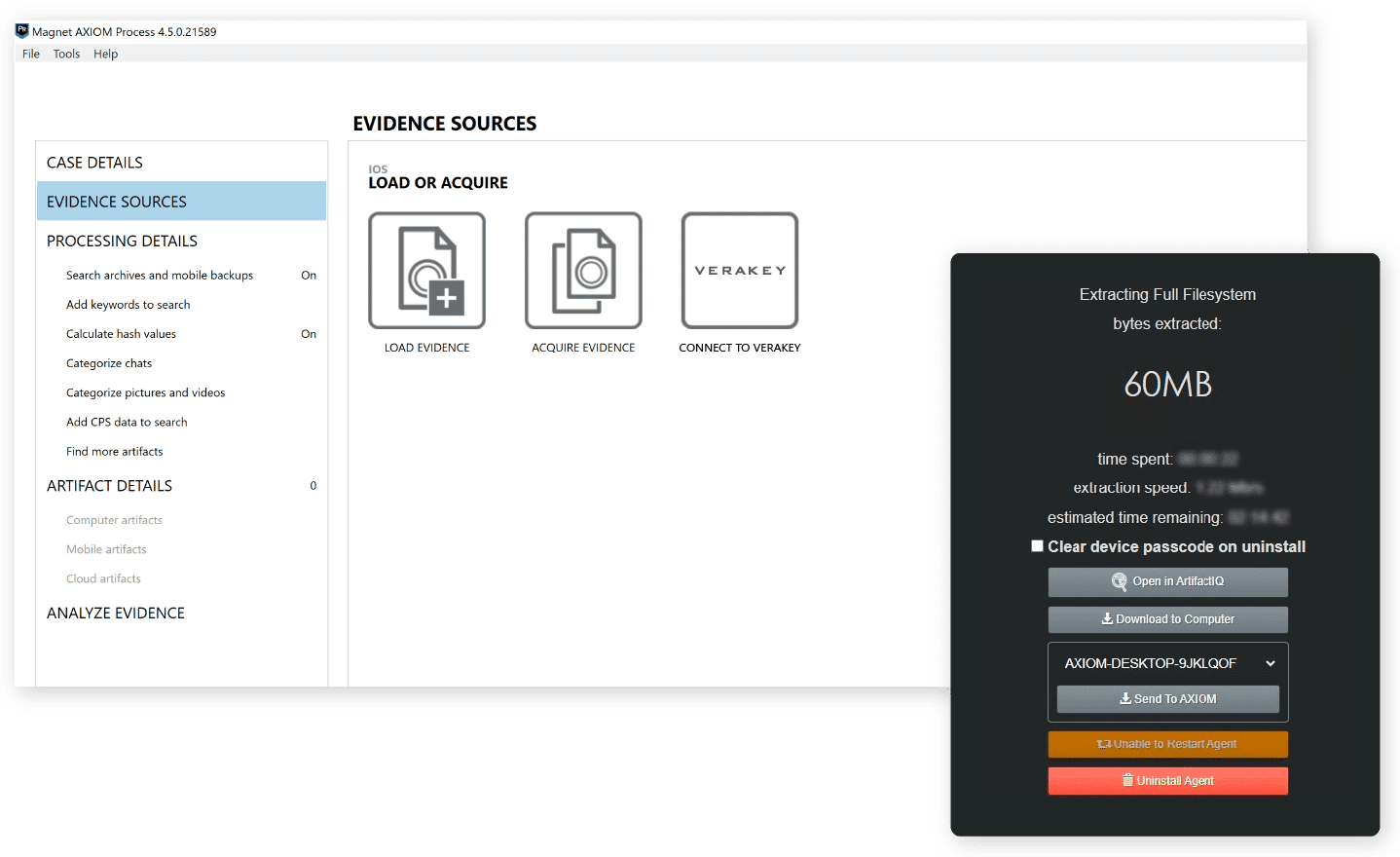
Streamline processing workflows
Stop interrupting your flow to load 3rd party mobile images into Axiom Cyber.
Maximize your productivity with the integration of Verakey and Axiom Cyber. Automatically push Verakey mobile images to Axiom Cyber for processing and analysis.
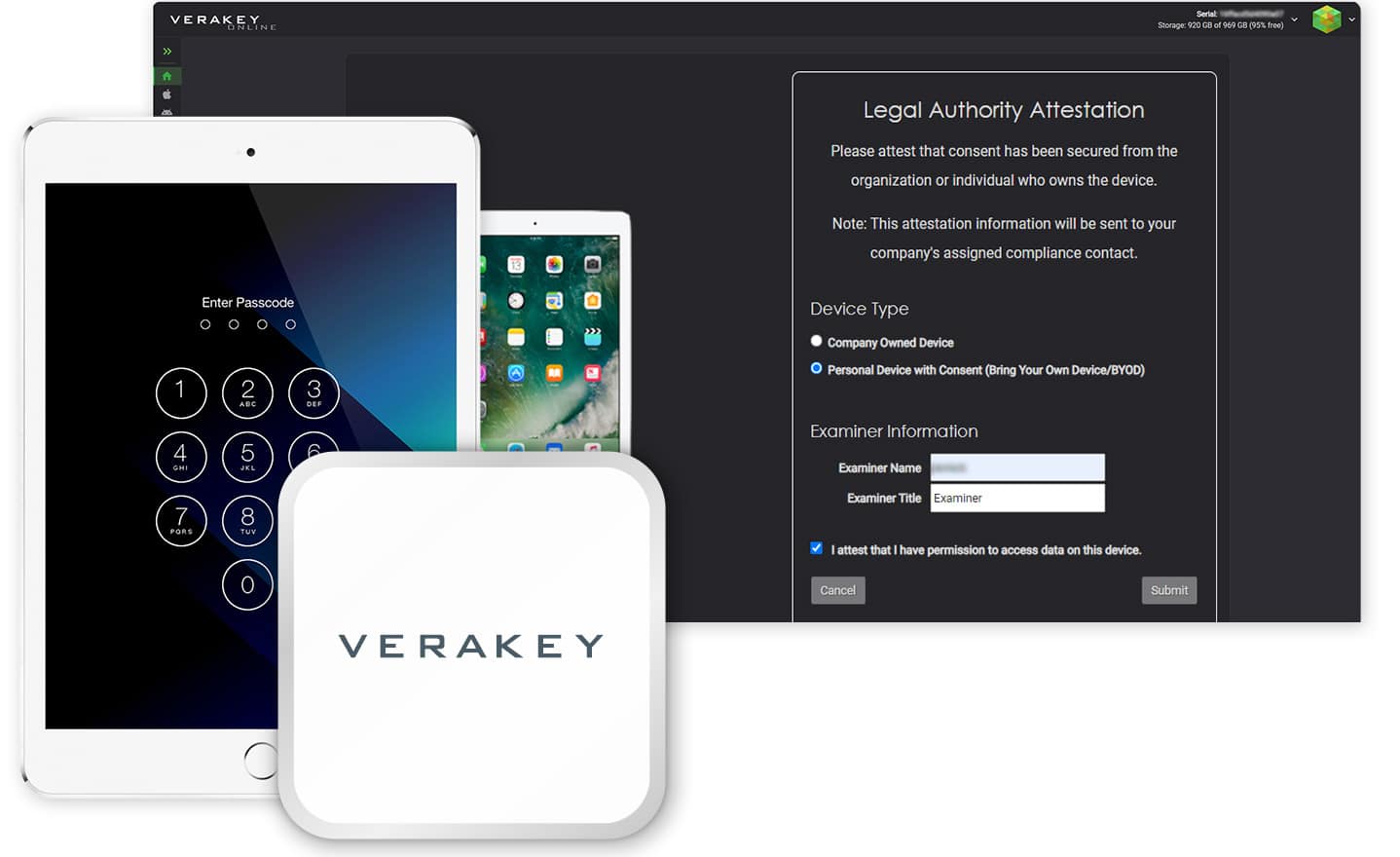
Connect and collect
Tired of tinkering around with various cables and awkward workflows? You’re going to love the simplicity of Verakey.
Verakey’s simple plug-and-play design doesn’t require reskilling, eases adoption, and complements existing solutions. The user-friendly web interface requires no special training.
Find evidence others miss
Verakey collects full file system extractions, including encrypted and inaccessible data, from iOS and leading Android devices.
Analyze the full file system (including iTunes backup-style images), decrypted keychain (iOS), decrypted Keystore data for specific apps (Android) and memory (iOS) from mobile devices and find evidence that other tools miss.
How it works
The complete digital forensics solution you’ve been waiting for
Use Axiom Cyber and Verakey together for the easiest to use end-to-end solution for investigations that involve evidence from mobile data sources:
- Connect the supported mobile device to Verakey.
- Begin the consent-based access and data extraction with the option to automatically push the image to Axiom Cyber by clicking the “Send automatically to Axiom Cyber” button.
- Check on the image processing status through the Integration Status dashboard in Verakey.
- Once processing is complete, jump right into examining the mobile data in Axiom Cyber using the analytics features you love, like Timeline and Connections.
Webinar
Collecting and analyzing mobile evidence in the workplace
Join Trey Amick, Director of Forensic Consultants, as he takes you on an exciting journey into the world of mobile device forensics, where you will discover the combined power of Verakey and Axiom Cyber. Together, these two tools empower users to access and extract full file system data from mobile devices, combine it with data from computer and cloud evidence, and then do a deep dive analysis.
Customer stories
Customer story | Jake Green, Technical Lead of Digital Forensics
Watch The VideoHow Envista Forensics extracts more data and streamlines digital investigation for timely, confident service to clients
Read the case study— Jake Green, Technical Lead of Digital Forensics
Envista Forensics
Request a demo
See Magnet Verakey in action
Talk to an expert and see how Magnet Verakey and Magnet Axiom Cyber work better together to save you time and get you the evidence you need to resolve cases faster.