Using F-Response and Magnet AXIOM: Use Case 1 – Targeted Acquisition
In our first F-Response and Magnet AXIOM blog post (Using F-Response and Magnet AXIOM to Conduct Enterprise Investigations), we discussed set up and acquisition methods. Here we will discuss a specific use case: Targeted Acquisition.
Even with decent network infrastructure, the bottleneck for a proper forensic investigation on a remote host will always be the network. I’ve worked in environments where the infrastructure was outstanding with dedicated pipes between offices, but the moment you hit a remote worker over VPN, it’s nearly impossible to remotely acquire a full physical disk in a reasonable amount of time and quite often it’s not necessary.
Conducting a targeted acquisition of just the files or data of interest will not only save time in your acquisition but also during your analysis because you will have less information to review. The key is to target the most common areas on a computer that is useful to an investigation.
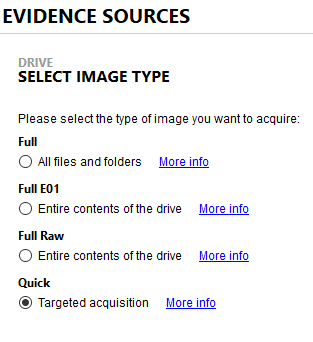
If we use F-Response in a similar fashion to our previous blog (Using F-Response and Magnet AXIOM to Conduct Enterprise Investigations) by remotely mounting the physical drive of the target computer, we can then load it into Magnet AXIOM and it will appear as a local drive on your forensics machine. From there we can choose to acquire the computer and then select a targeted acquisition in AXIOM to limit the amount of data that needs to be transferred over the network.
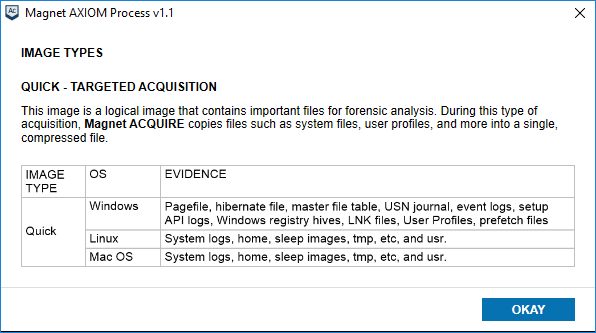
A targeted acquisition will do a logical extraction of the most common areas of a hard drive useful to forensic examiners. It won’t include everything on the disk but typically we don’t need an entire physical image to conduct most investigations. Each investigation will vary on what is needed. On a Windows system, we target the user profiles, pagefile, hiberfil.sys, registry hives, MFT, USN Journal, event logs, LNK files, prefetch files, etc.
User Profiles
If you’re conducting an investigation on a user’s activity, the user profiles will contain the majority of the information that you need. Depending on how many profiles there are or the size of them, it can still take some time to pull this data, but it’s certainly going to be much faster than a full physical image or a logical dump of the file system. This will also help minimize the amount of non-user data that gets included in your case as well saving even more time in the end.
Depending on the objectives of your investigation, this is just another way to utilize the features of both F-Response and Magnet AXIOM when conducting remote enterprise investigations. Both tools are very flexible in the implementation allowing for a multitude of options and avenues to conduct your examination the best way you see fit.
Any questions? Send an email to Jamie at jamie.mcquaid@magnetforensics.com.