How to Connect Magnet AXIOM Cyber Directly to VeraKey for Mobile Device Investigations
Organizations leveraging VeraKey for their consent-based mobile device extractions are provided access to full file system acquisitions of both iOS and Android devices. These full file system images contain additional data points that would otherwise not be available with only logical extractions.
With the integration of these tools, connecting Magnet AXIOM Cyber to VeraKey directly can streamline your acquisition and analysis workflow. By launching AXIOM Process, and then connecting to your VeraKey, you can transfer acquired images directly into AXIOM Cyber for processing.
Connecting Magnet AXIOM Cyber to VeraKey
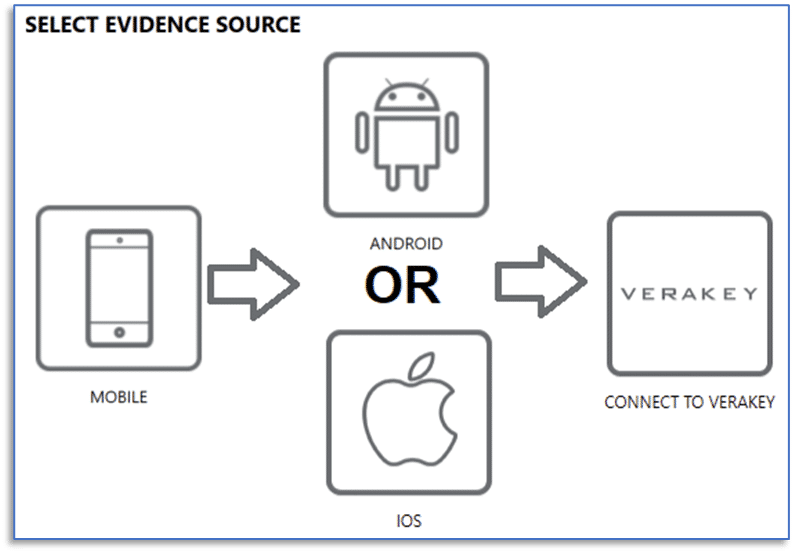
First, launch AXIOM Process and proceed to choose your evidence source by selecting:
Mobile -> Android or iOS -> Connect to VeraKey
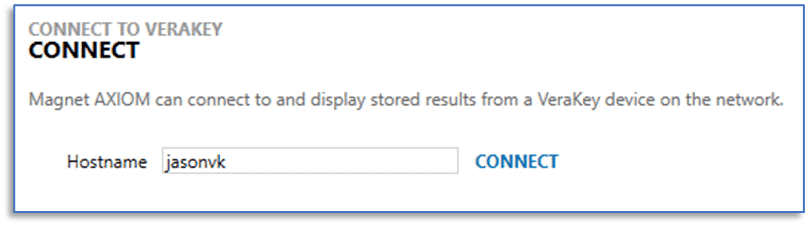
You will then need to provide the hostname or internet protocol (IP) address of the VeraKey device that you want to connect to. The VeraKey will need to be on the same network as your examination computer. If an examiner has previously completed this step within this installation of AXIOM Cyber, you will not see this dialog window.
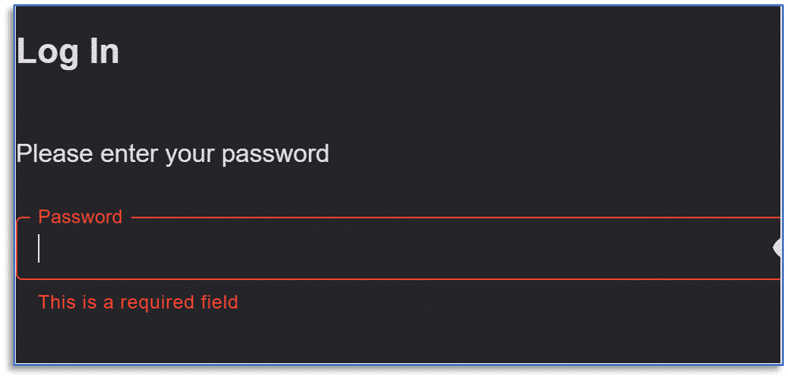
Once connected to the VeraKey, you will be prompted for a password. If this is the first time you’re connecting, you will also be prompted to allow access, authorizing AXIOM Cyber access to the VeraKey.
After completing authentication, examiners can designate a location to store VeraKey extractions. This will vary depending on your environment, but a dedicated storage device for evidence files generally provides the best performance during case processing; options are available to suit most workflows. You will then see a listing of extractions currently available on the VeraKey. This list will include the name, UUID, iOS version, and evidence ID (as entered during device acquisition) making it easy to determine which acquisition you would like to transfer.
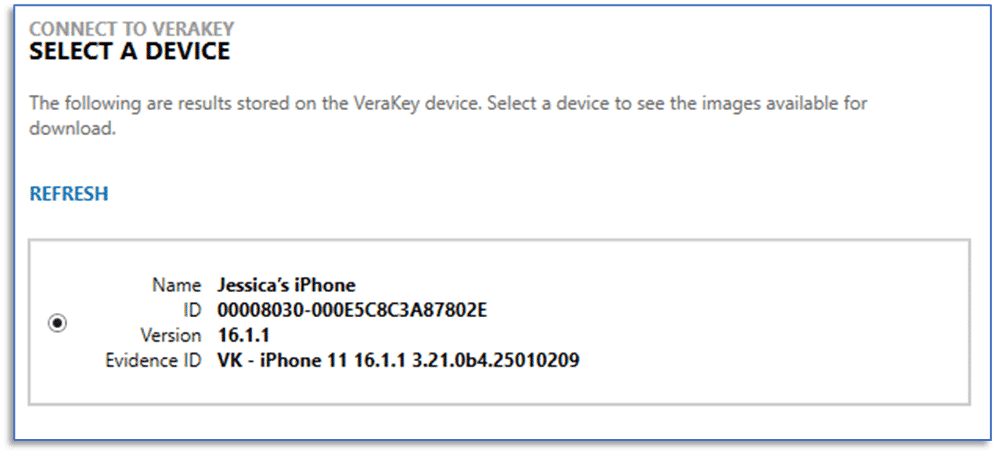
After selecting a device acquisition from the list, you can then select which of the available items you would like to include in your AXIOM Cyber case for processing. These options will vary depending on the type of device acquired and acquisition performed. As an example, for iOS Devices, options typically include the file system acquisition, keychain data, and process memory. There is also an option to pre-process the keychain from VeraKey iOS extractions, learn more here.
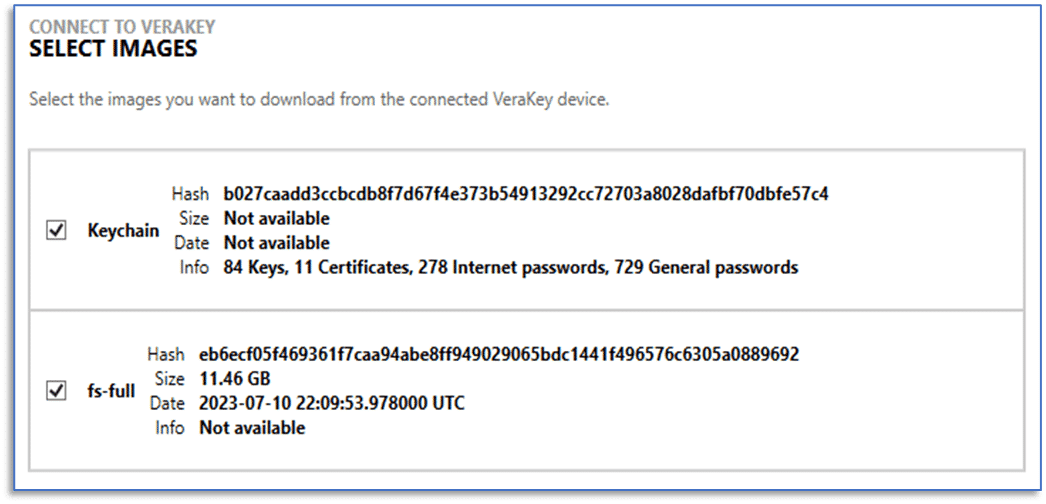
Once you have chosen the acquisition items for transfer, selecting the NEXT button will begin download data from the VeraKay. Once the transfer is complete, AXIOM Cyber will perform hash verification to ensure the downloads was successful. If either the download or hash verification fail, examiners are presented with an option to retry the download.
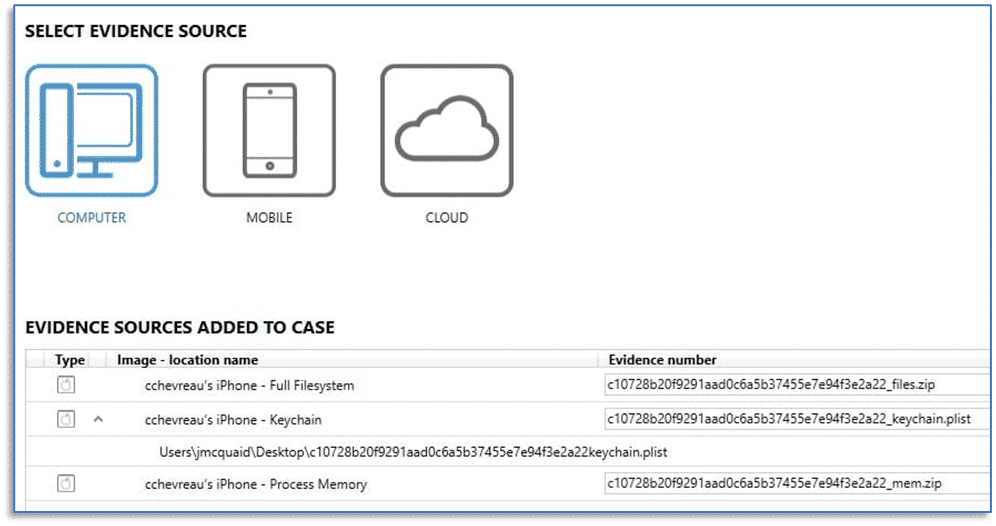
Once the download and hash verification completes, the selected evidence items will be added to your AXIOM case. The remaining case processing options in AXIOM Cyber, including things like keyword searching, using hash lists, or media categorization are available for you to utilize while processing the evidence. The integration of AXIOM Cyber and VeraKey is a timesaving feature allowing examiners to streamline their workflows for mobile device investigations.